Embed presentation

















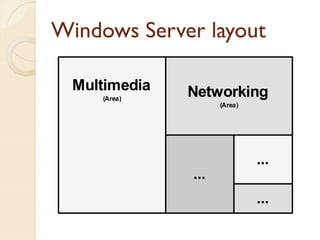
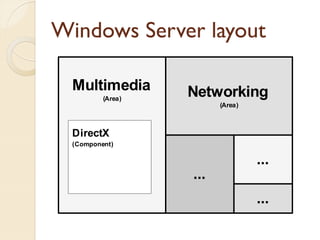
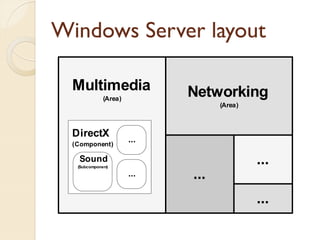
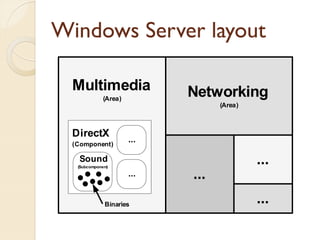
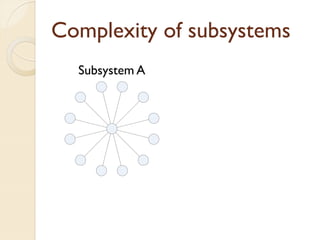
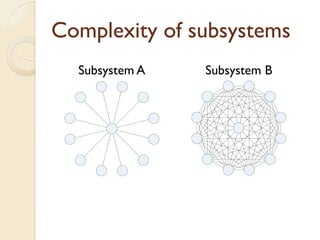
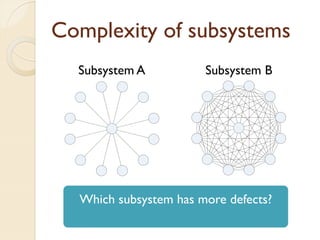
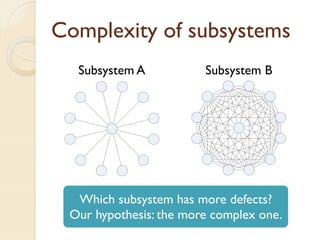
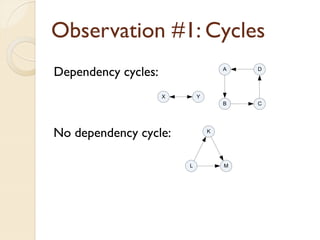
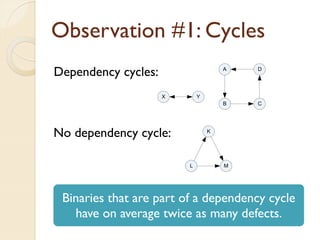

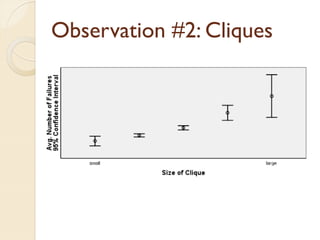
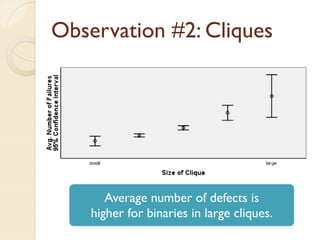
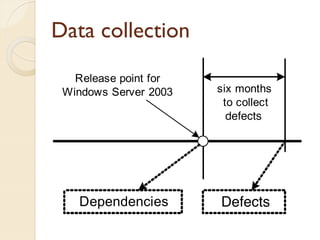
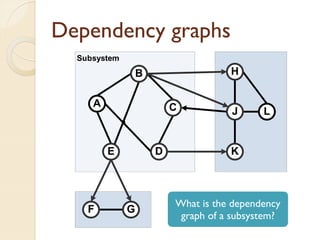
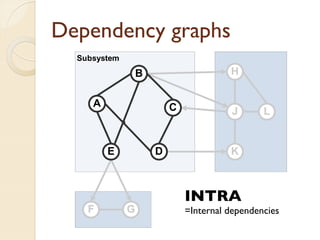
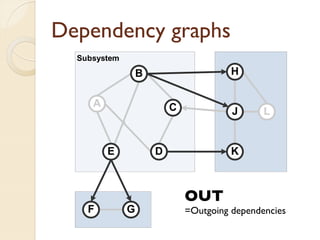
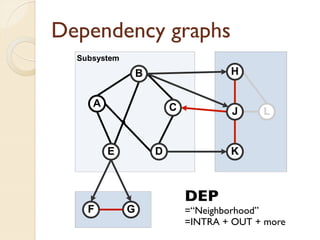
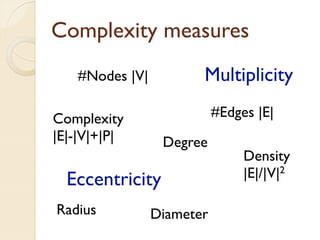
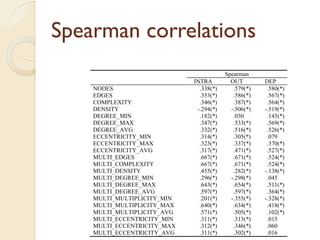
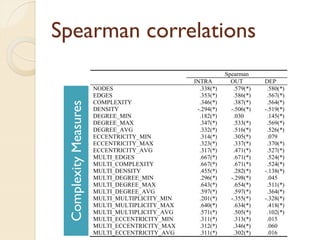
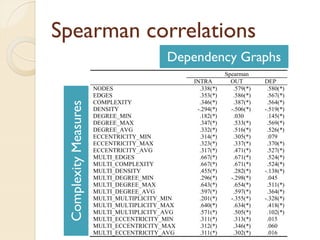
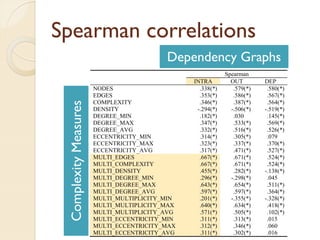
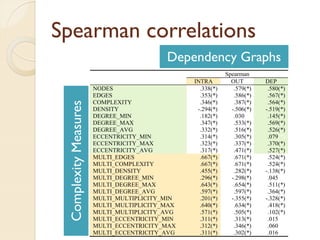
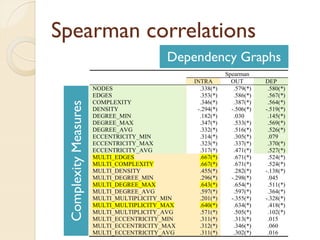
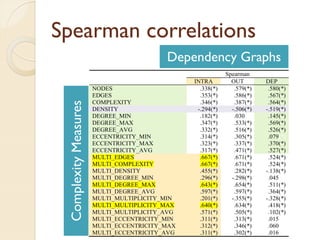
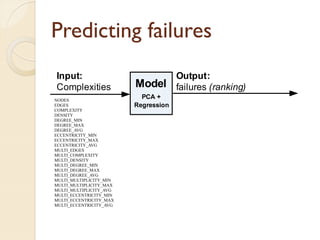
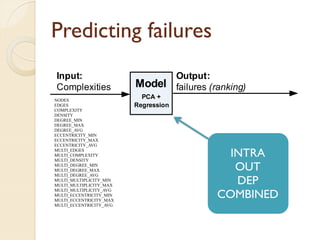

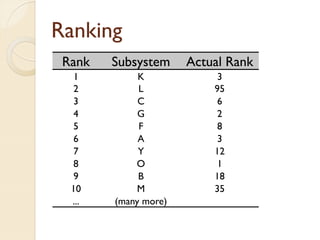
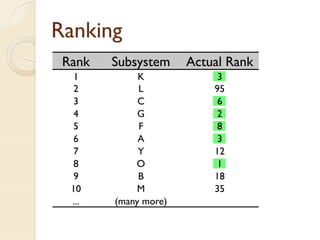
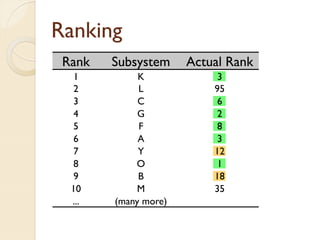
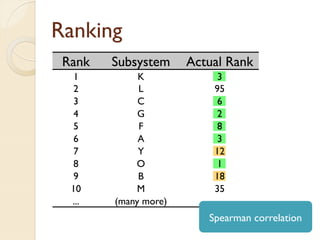
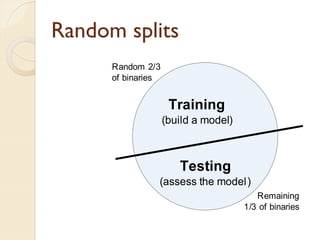
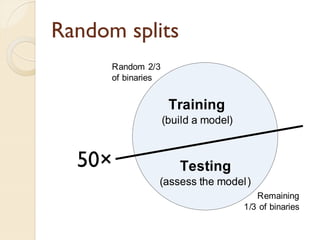
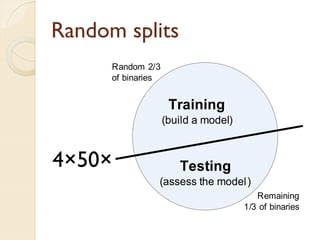
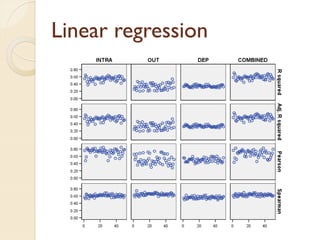
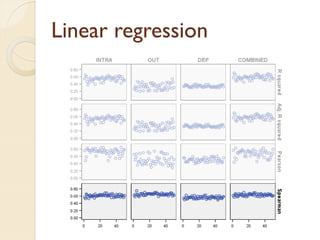
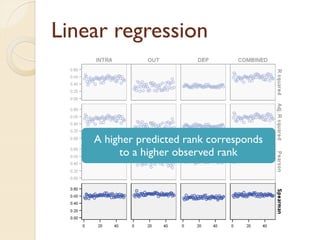
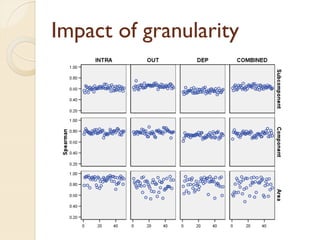
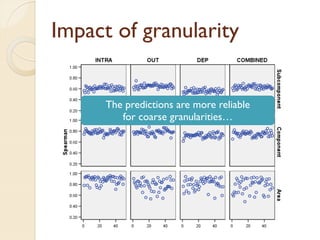
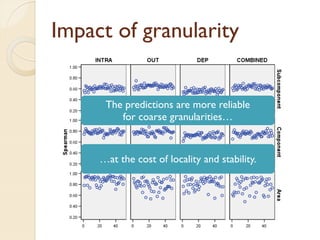





The document presents a method for predicting subsystem failures in software projects using dependency graph complexities. It finds that code dependency cycles and large cliques (fully connected subgraphs) correlate with more defects. It also finds that measures of complexity in a subsystem's dependency graph, such as the number of nodes and edges, can be used to predict the number of defects in the subsystem. Evaluating the method on a large Microsoft software project showed it could effectively rank subsystems by likelihood of failure.


































































