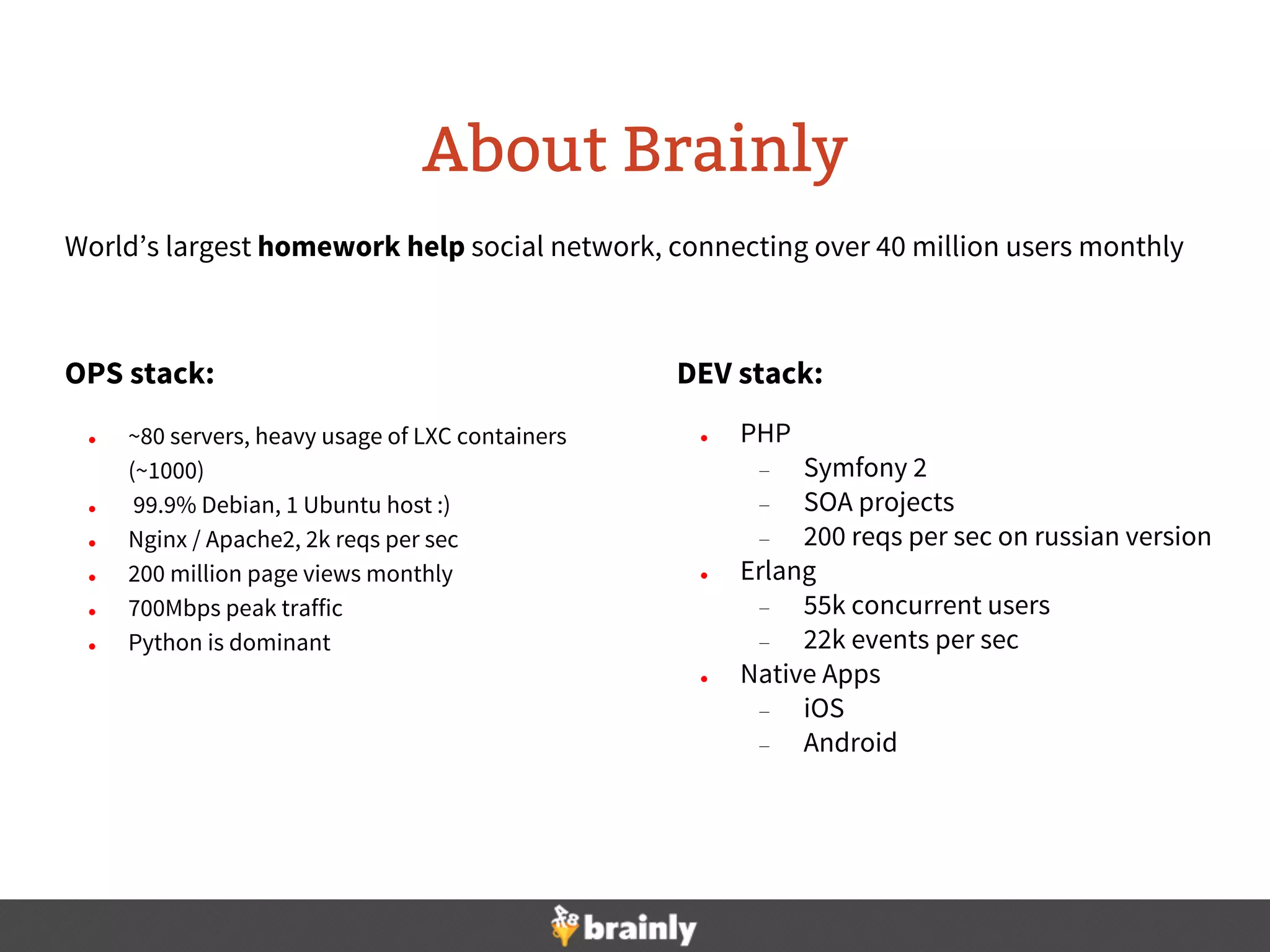
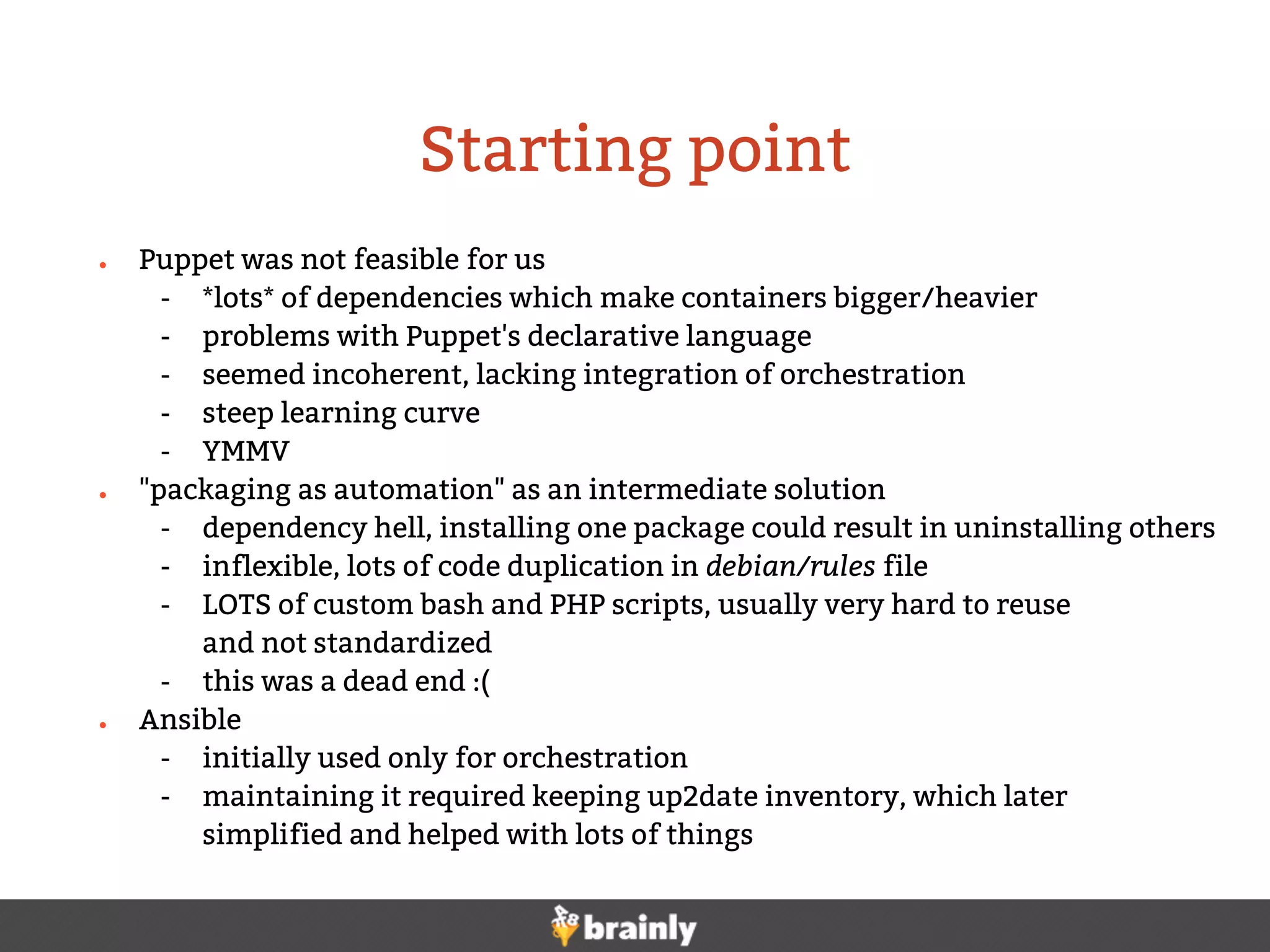
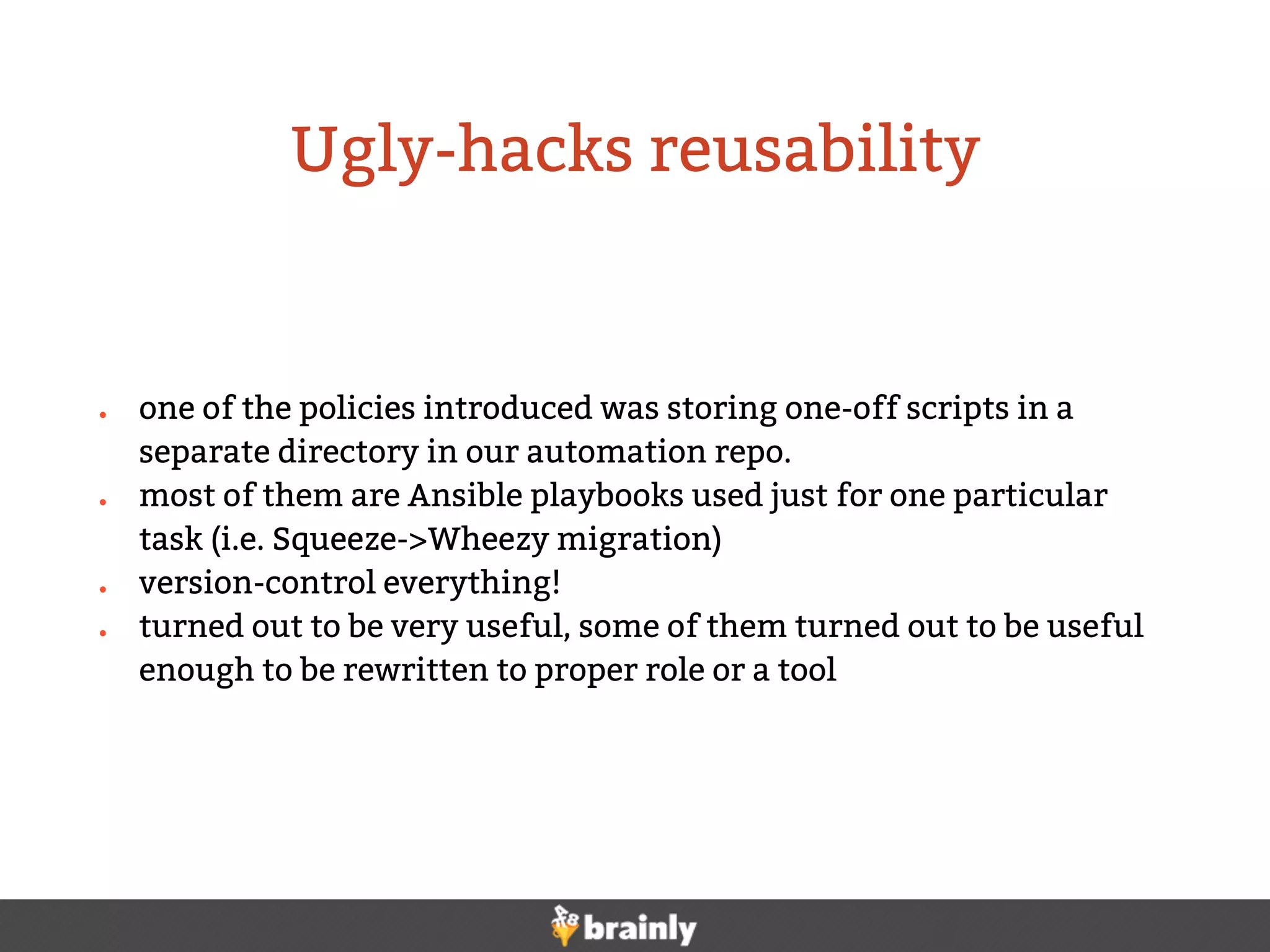
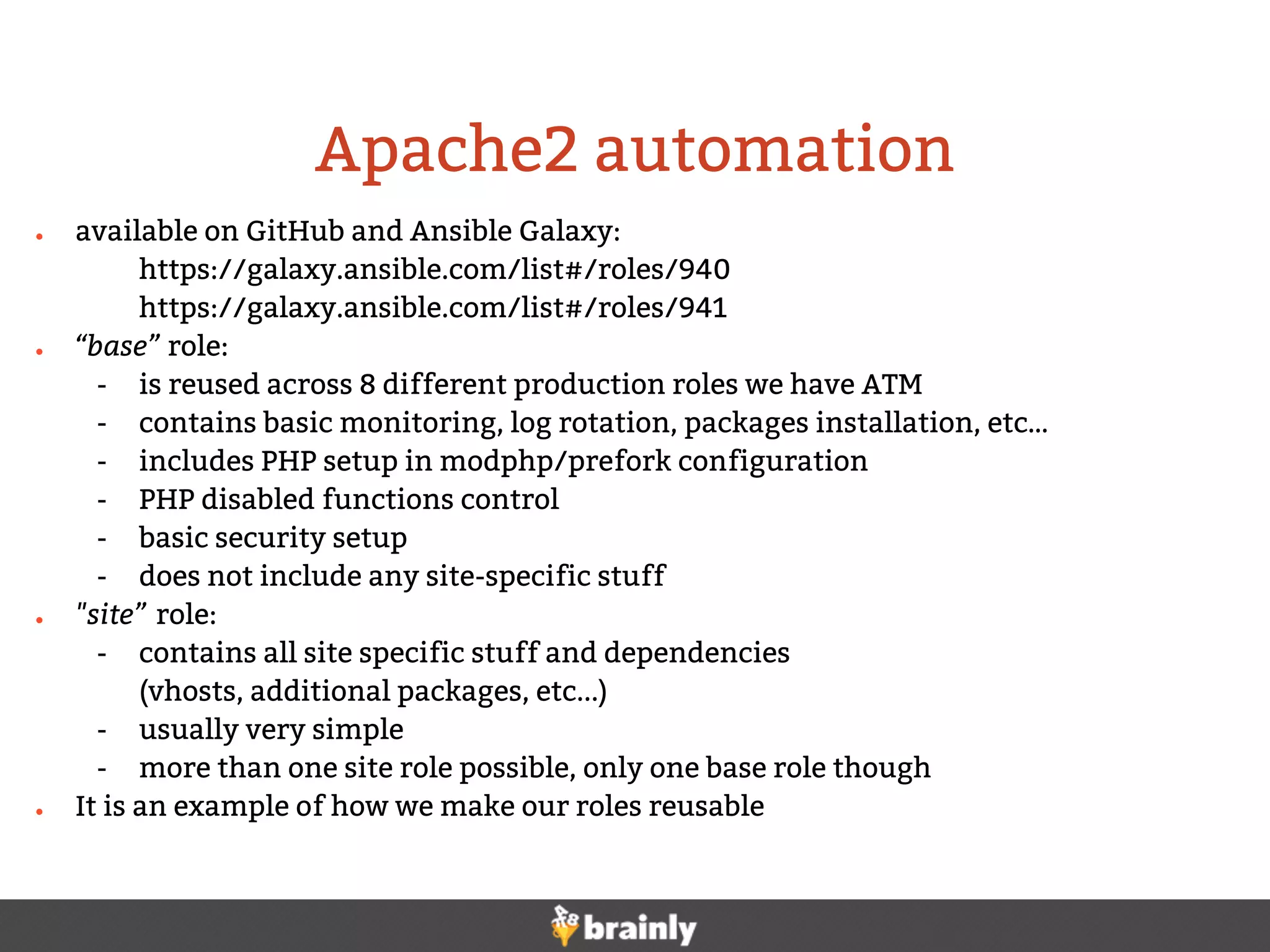
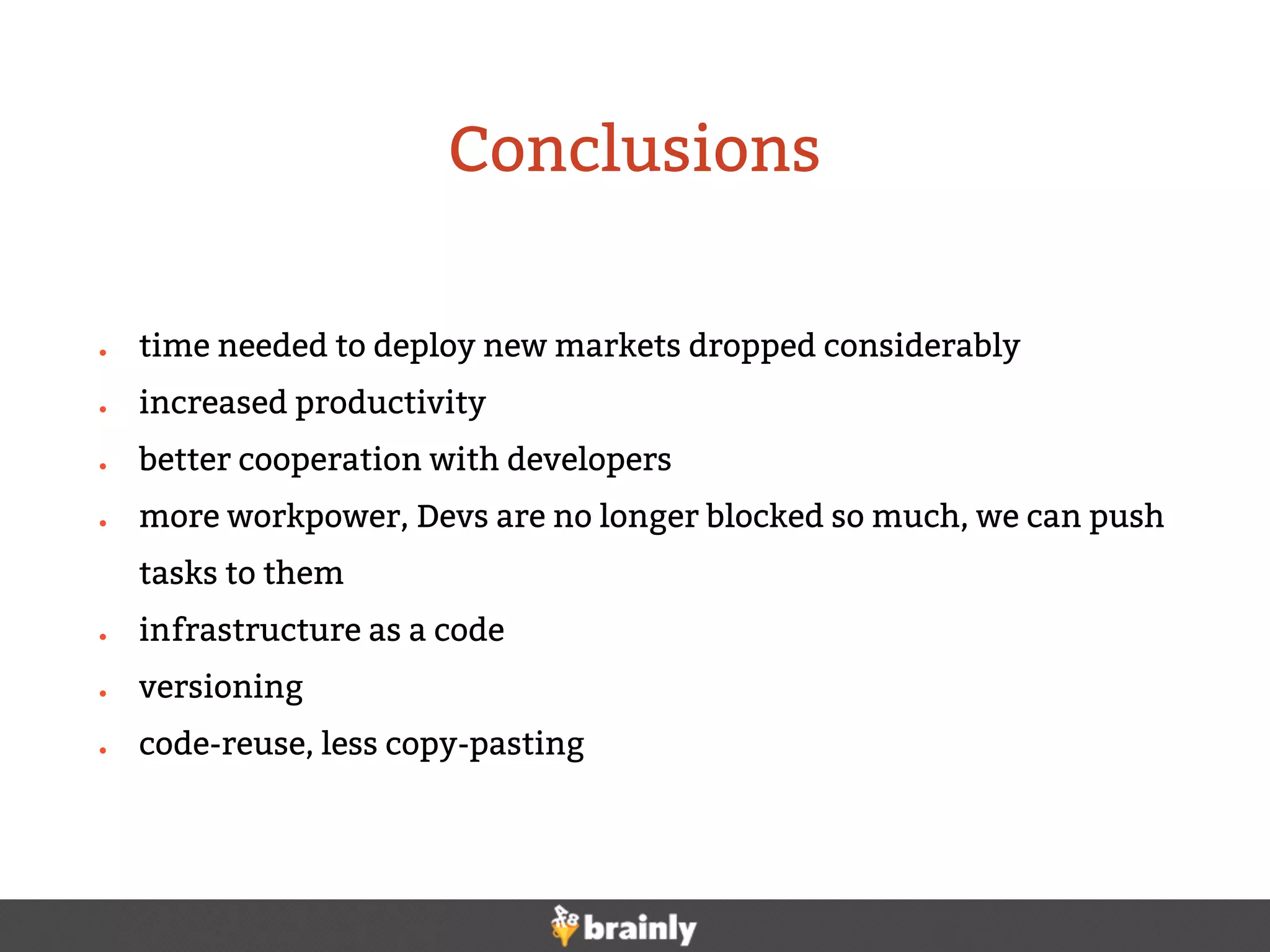
This document summarizes Brainly's use of Ansible for infrastructure automation. Key points include:
- Brainly uses Ansible to configure over 1000 Linux containers running various services.
- Ansible is used to automate setup of services like Nagios monitoring, Apache, DNS, backups, firewalls, and more.
- Custom scripts were integrated with Ansible to improve reusability and standardization.
- Dynamic inventory scripts were developed to simplify host and group management across hundreds of servers.