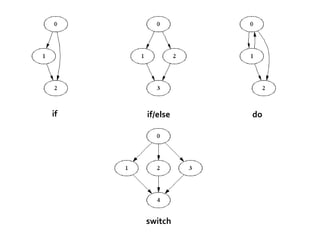
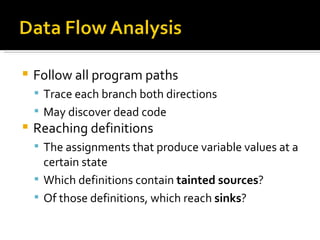
The document discusses various vulnerabilities in software development, focusing on concepts like static and dynamic analysis, code quality issues, and methods for identifying and mitigating vulnerabilities such as SQL injection and cross-site scripting. It emphasizes the importance of both static and dynamic analysis for early detection of potential security risks and outlines techniques such as control flow graphs and data flow analysis for deeper inspection of code. Additionally, it highlights the significance of validating inputs to prevent various types of attacks and the need for tool automation in the development process.





![Cross-site Scripting Response.Write(Request.QueryString[“isbn"]); SQL Injection protected System.Web.UI.WebControls.TextBox Publisher; SqlCommand cmd = new SqlCommand(“SELECT * FROM Books WHERE Publisher = ‘”+Publisher.Text+“’”, conn); HTTP Response Splitting string author = Author.Text; Cookie cookie = new Cookie("author", author); Path Traversal sting fName = Request.Form[“fileName“]; File.Delete("C:\\users\\files\\" + fName); Command Injection string args = “-a -o “+Request.Param[“arg”]; Process.Start(“program.exe“+args);](https://image.slidesharecdn.com/aofwof-090310145240-phpapp01/85/Static-Analysis-The-Art-of-Fighting-without-Fighting-10-320.jpg)
![Cross-site Scripting Response.Write ( Request.QueryString[“isbn"] ); SQL Injection protected System.Web.UI.WebControls.TextBox Publisher; SqlCommand cmd = new SqlCommand (“SELECT * FROM Books WHERE Publisher = ‘”+ Publisher.Text +“’”, conn); HTTP Response Splitting string author = Author.Text ; Cookie cookie = new Cookie ("author", author); Path Traversal sting fName = Request.Form[“fileName“] ; File.Delete ("C:\\users\\files\\" + fName); Command Injection string args = “-a -o “+ Request.Param[“arg”] ; Process.Start (“program.exe“+args);](https://image.slidesharecdn.com/aofwof-090310145240-phpapp01/85/Static-Analysis-The-Art-of-Fighting-without-Fighting-12-320.jpg)

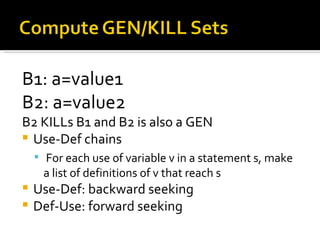
![… if (Page.IsValid()) string pwd = Request.Form[“pwd”]; … string sql = “SELECT …” + pwd + “’”; SqlCommand cmd = new SqlCommand(sql); … If this def doesn’t dominate this use Unvalidated input causes SQL Injection](https://image.slidesharecdn.com/aofwof-090310145240-phpapp01/85/Static-Analysis-The-Art-of-Fighting-without-Fighting-20-320.jpg)
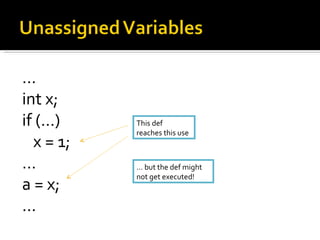
![Formerly called Microsoft Intermediate Language .NET is Stack based (LIFO) Metadata for compiled classes Reflection - the program in the mirror Common Language Runtime .method public static void Main() cil managed { .entrypoint .maxstack 1 ldstr "Hello, world!" call void [mscorlib]System.Console::WriteLine(string) ret }](https://image.slidesharecdn.com/aofwof-090310145240-phpapp01/85/Static-Analysis-The-Art-of-Fighting-without-Fighting-21-320.jpg)