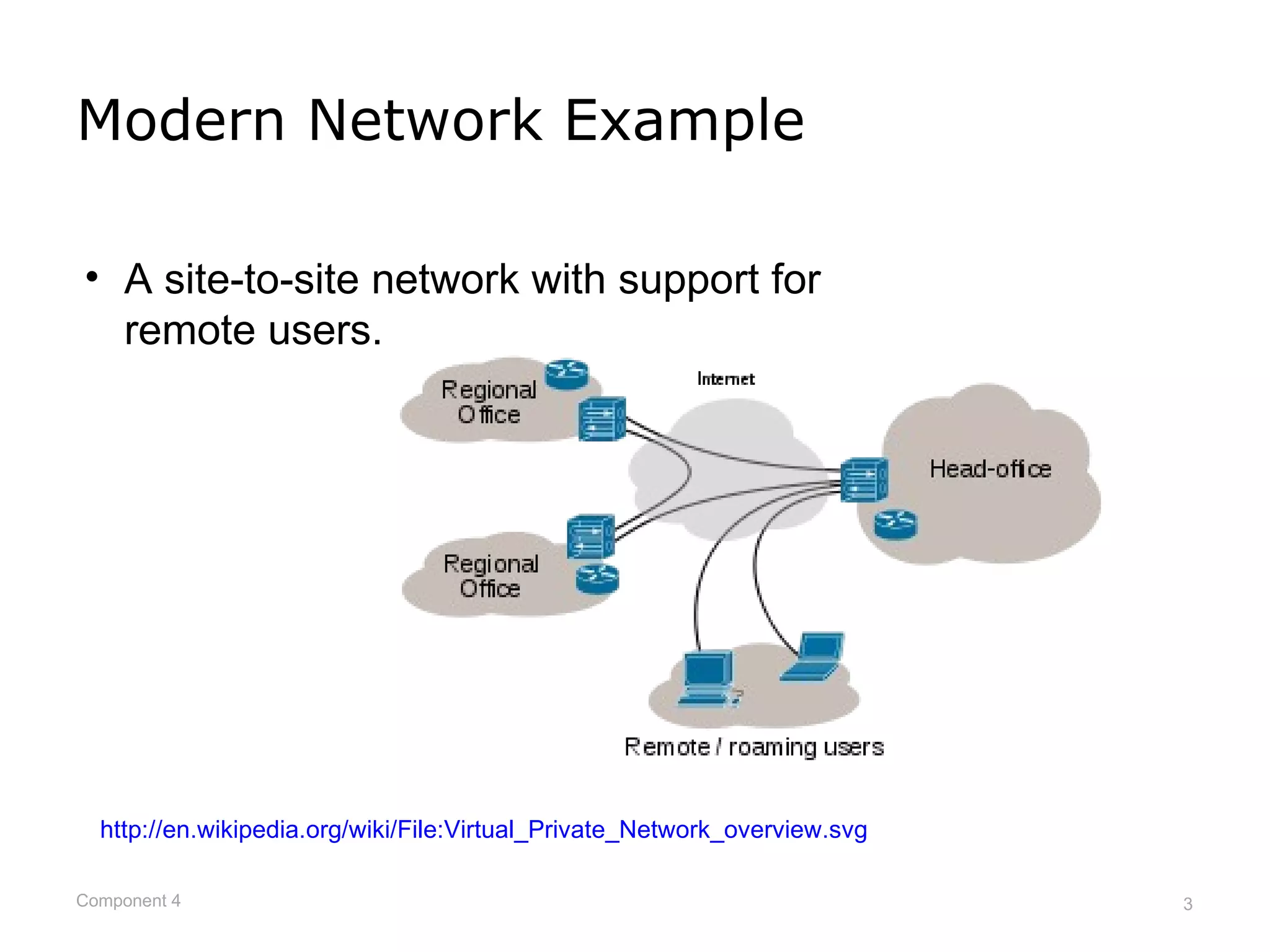
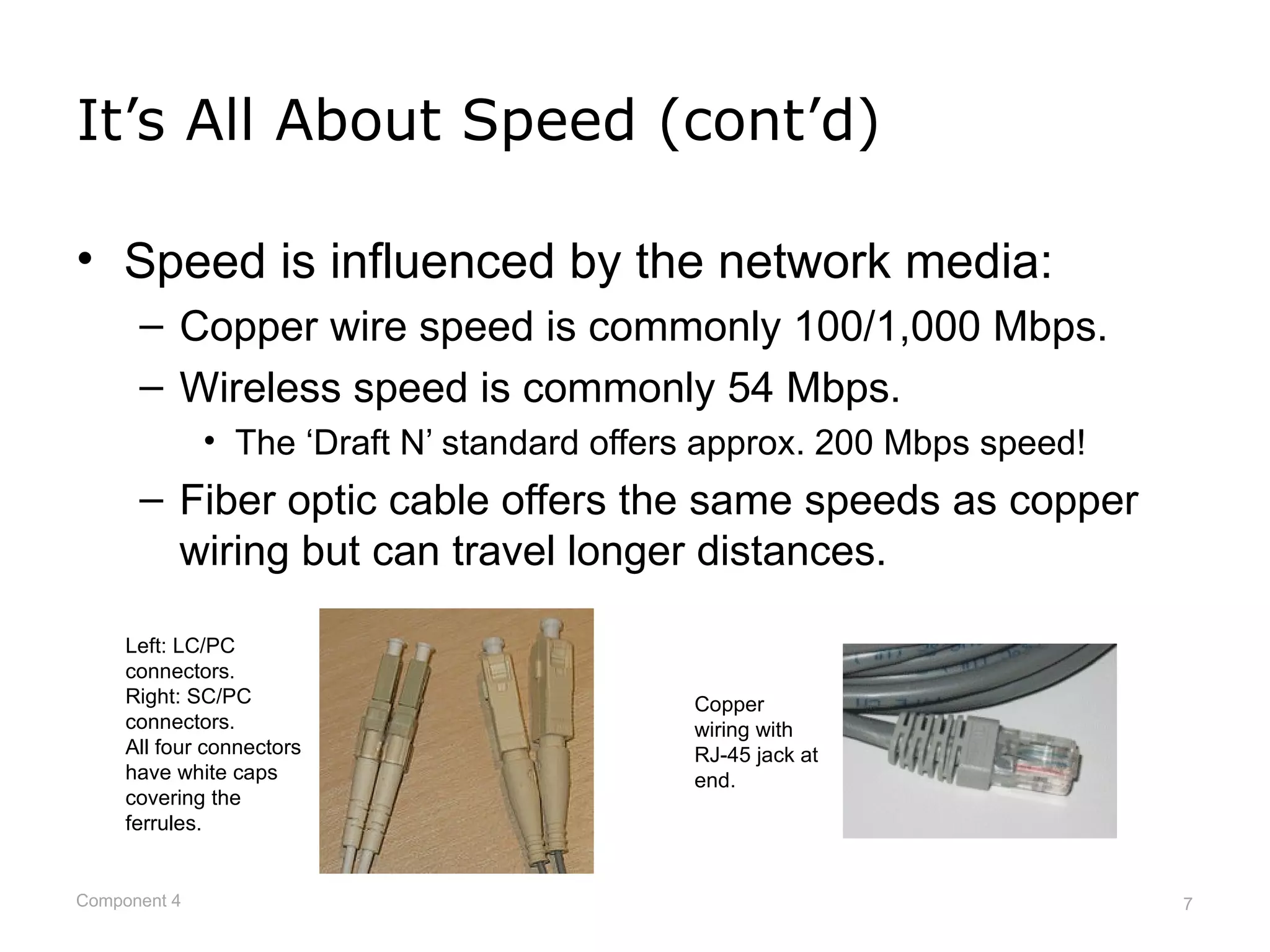
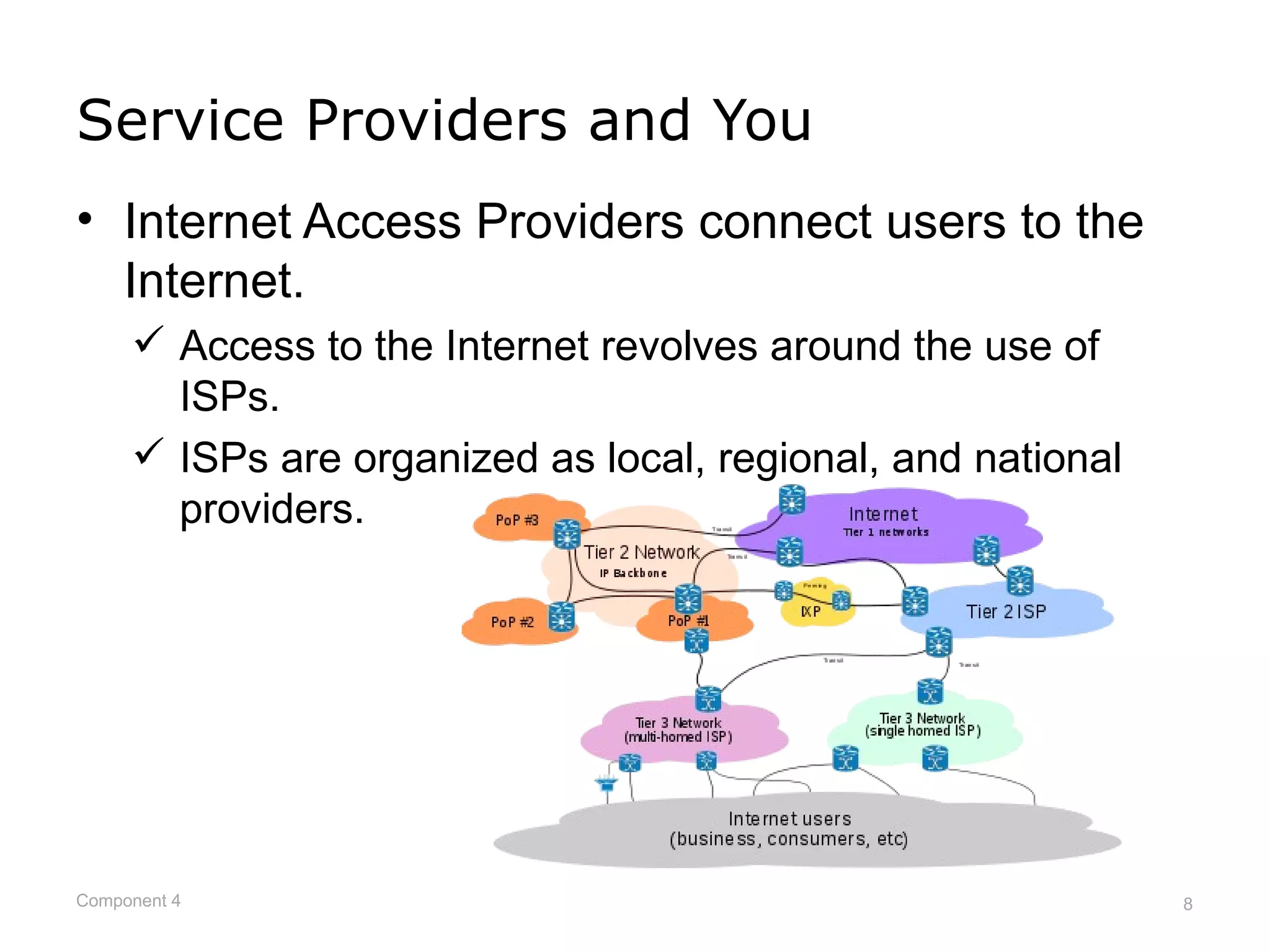
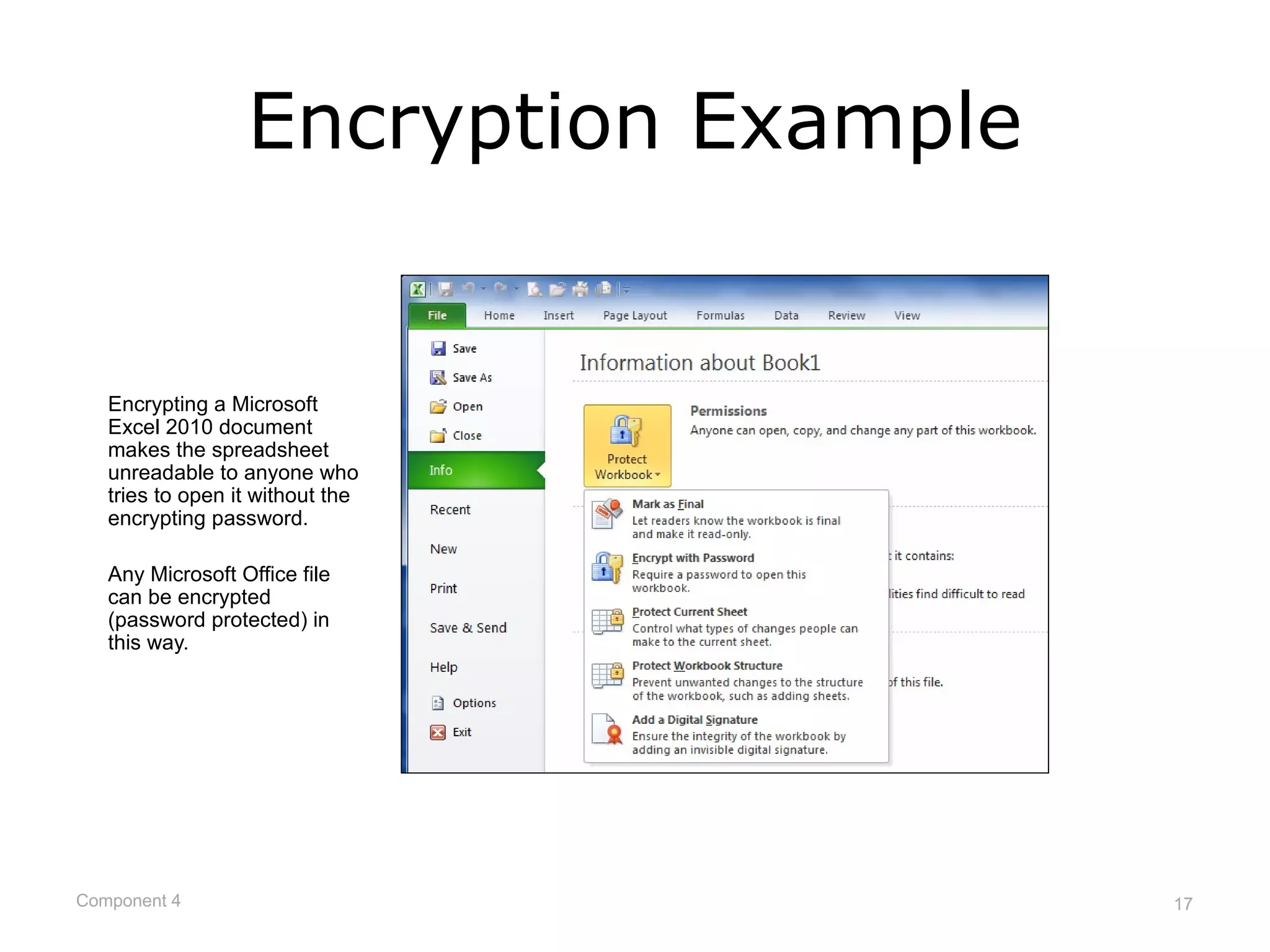
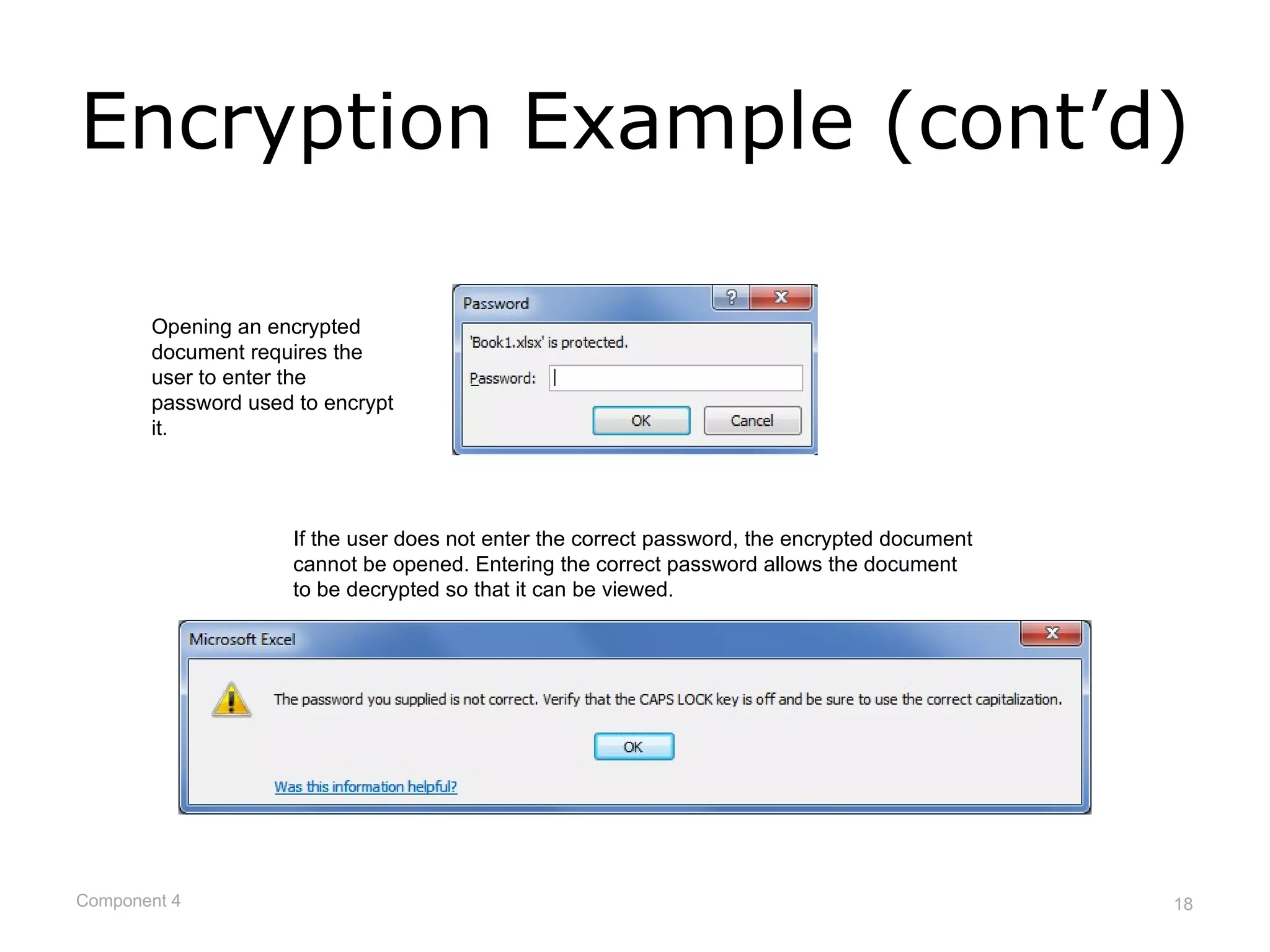
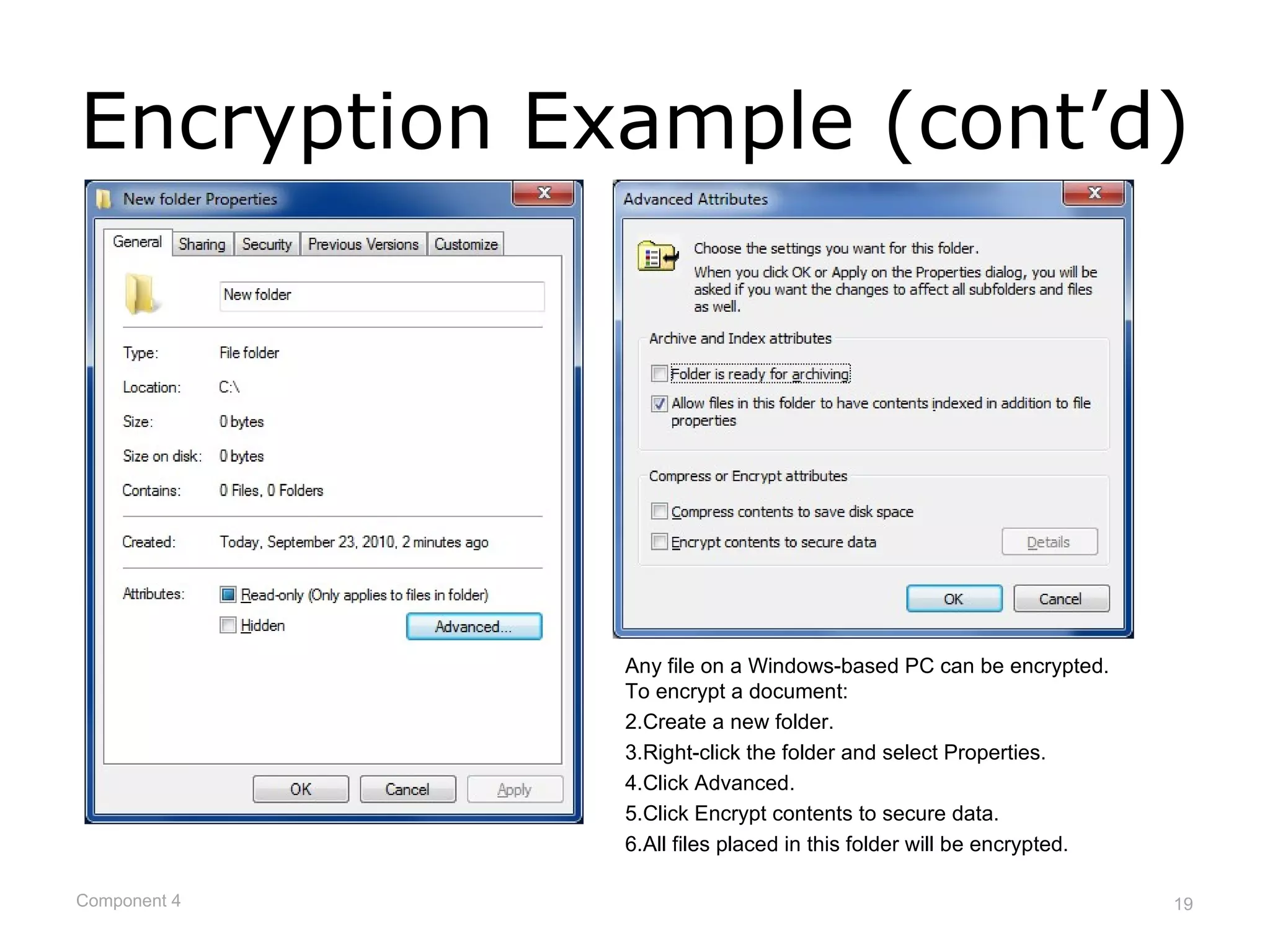
This document provides an overview of networks and network security. It defines what a network is and describes different network types including LANs, WANs, and topologies. It discusses how devices connect to networks, factors that influence connection speed, and examples of internet access providers. The document also summarizes network security measures like encryption, firewalls, and auditing security policies. It provides examples of how encryption works and describes federal regulations around health information privacy and security like HIPAA.