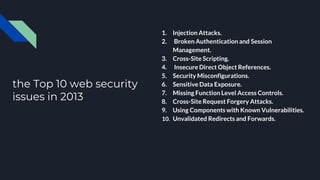
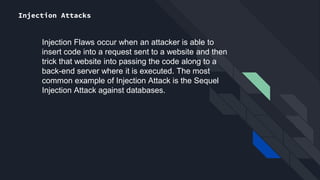
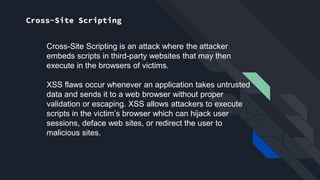
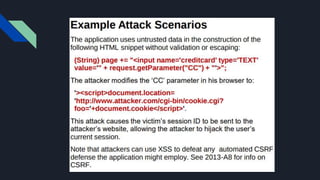
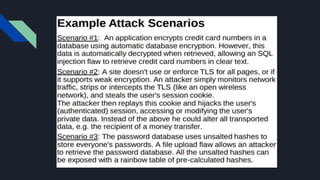
The document discusses the Open Web Application Security Project (OWASP) and its role in improving application security through free resources and tools. It outlines the OWASP Top 10 vulnerabilities, including injection attacks and broken authentication, emphasizing the importance of understanding these threats for secure web services. Additionally, it highlights recent vulnerabilities such as unvalidated redirects and insecure deserialization, and underscores the ongoing need for monitoring and patching to protect applications.