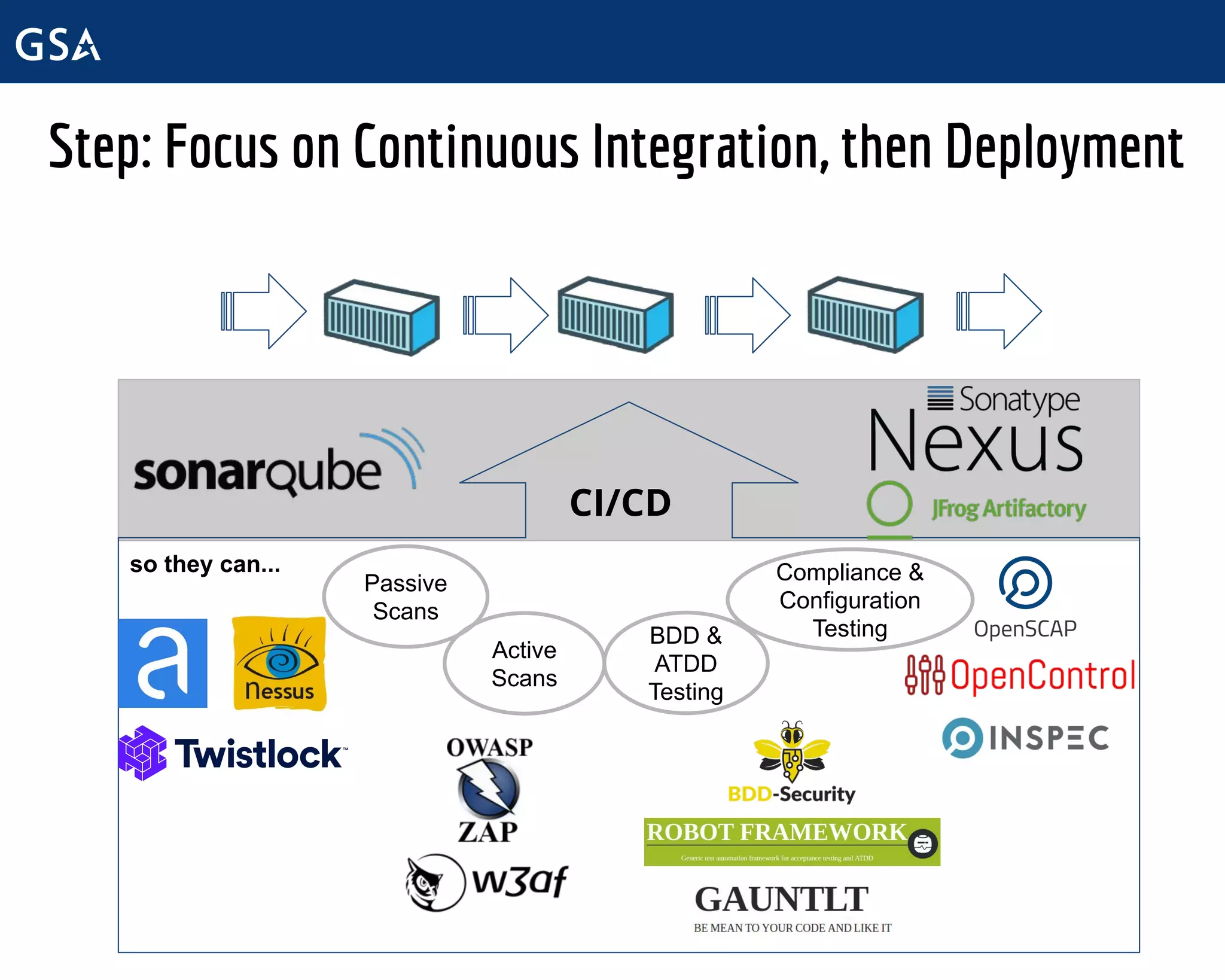
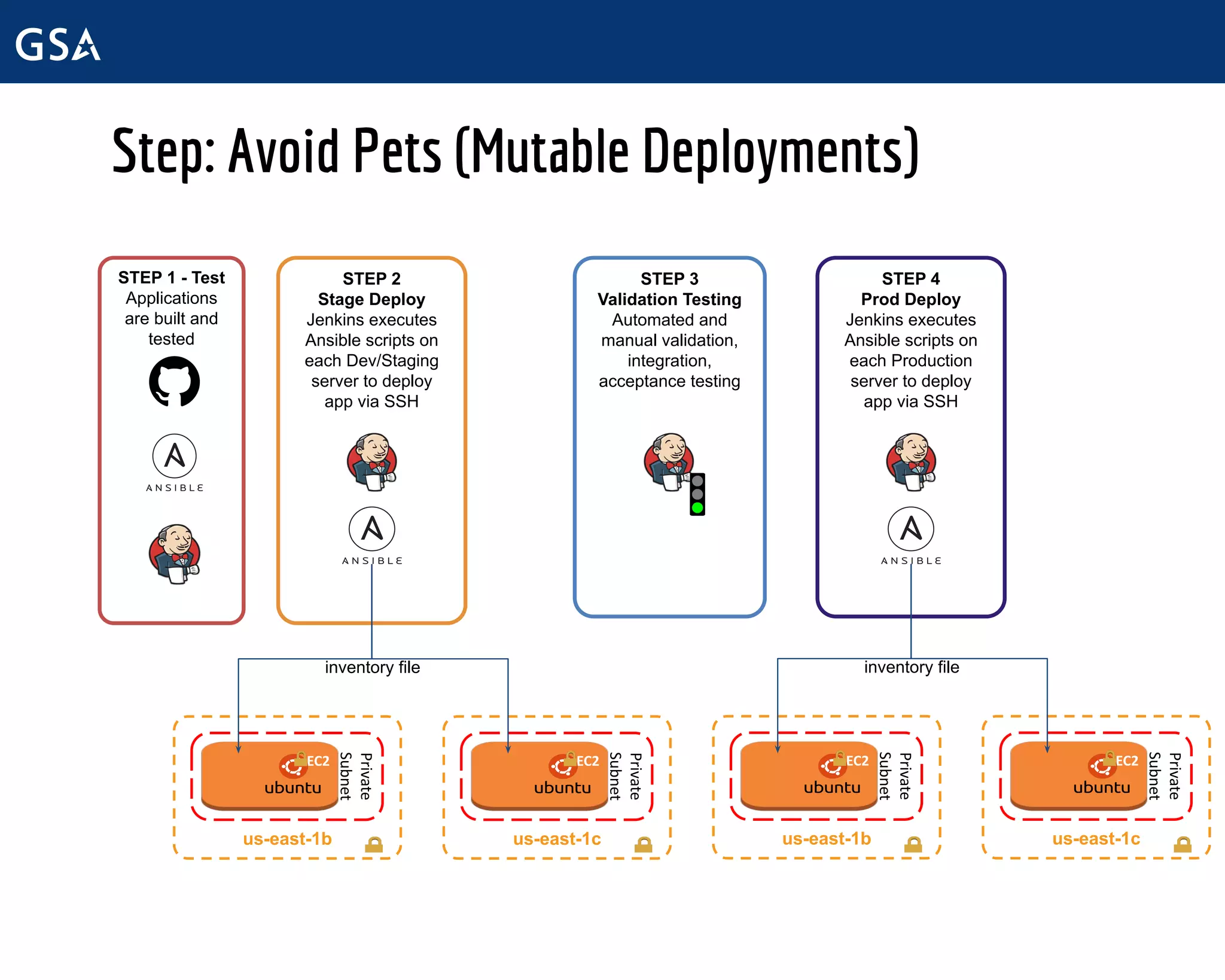
The document outlines the initiatives and challenges faced by the Technology Transformation Service (TTS) at the General Services Administration (GSA) regarding DevSecOps, software management, and infrastructure improvement. It emphasizes the need for centralized processes, enhanced cybersecurity measures, and improving communication to streamline software requests and infrastructure management. The TTS aims to facilitate a DevOps cultural transformation, focusing on automation, security integration, and efficient service delivery across government agencies.