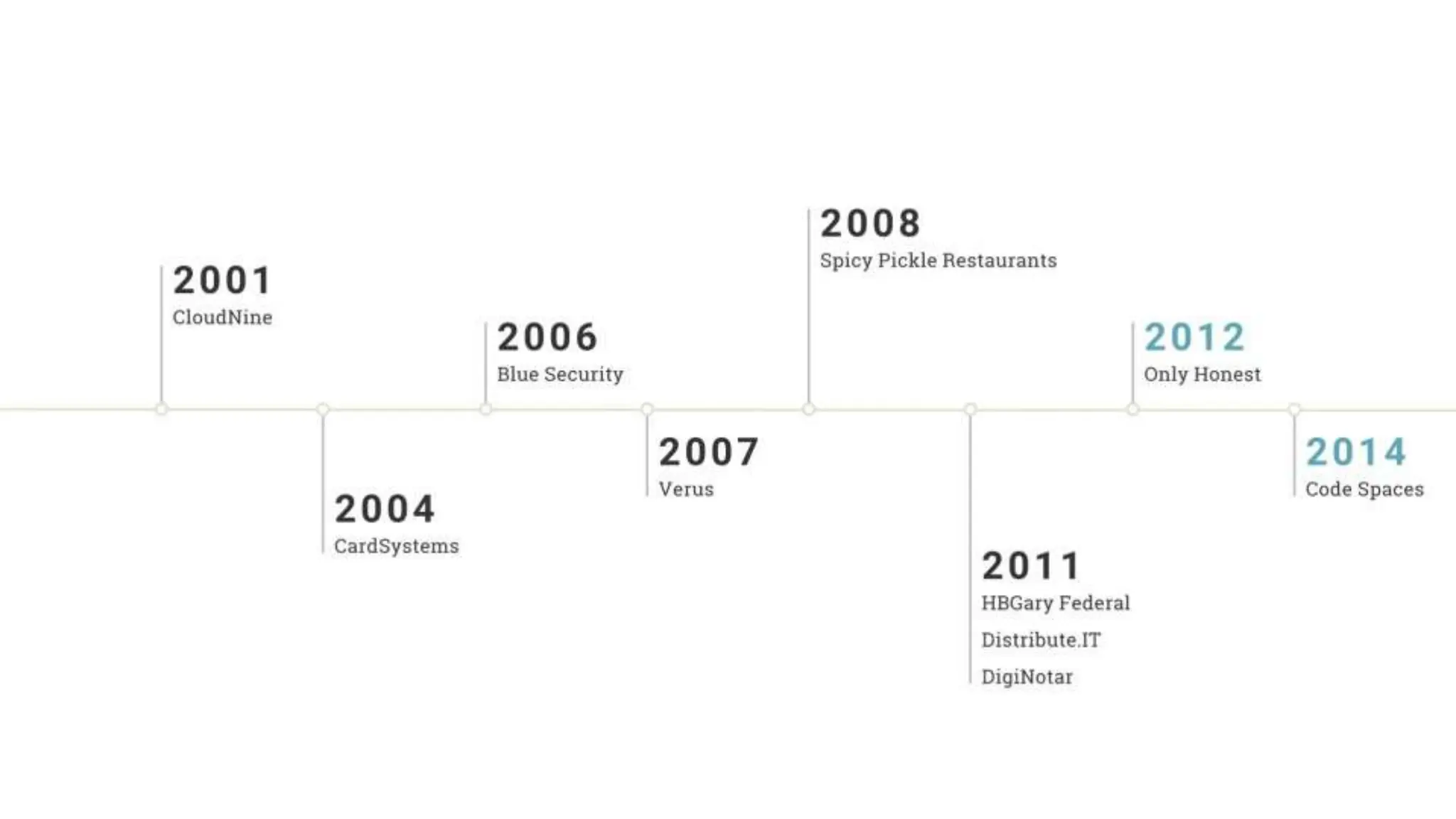
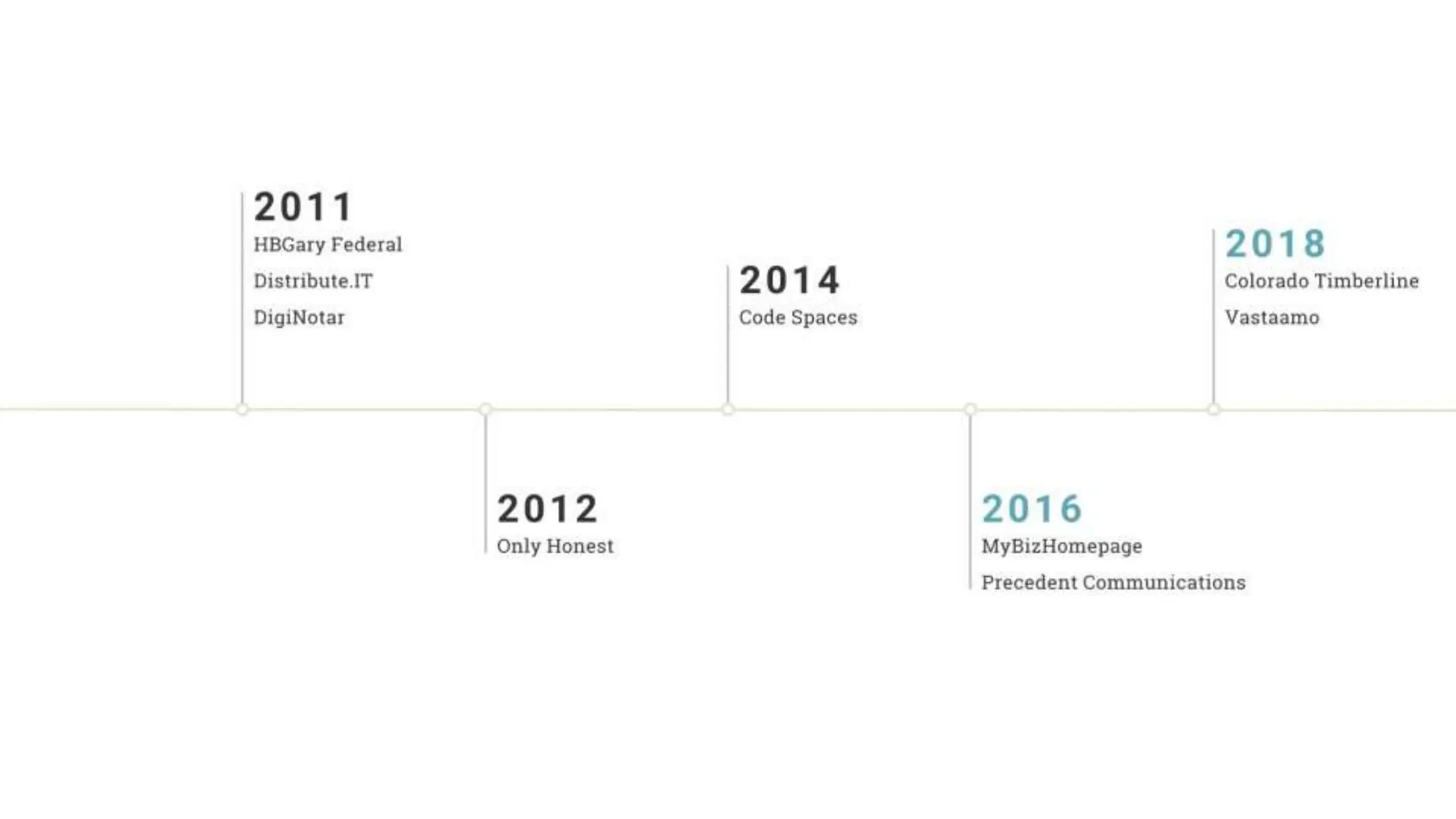
In InfoSec, many closely held beliefs, commonly accepted best practices, and accepted ‘facts’ are just wrong. These myths and lies spread quickly. Collectively, they can point security teams in the wrong direction. They can give rise to ineffective products. They often make their way into legitimate research, clouding results.
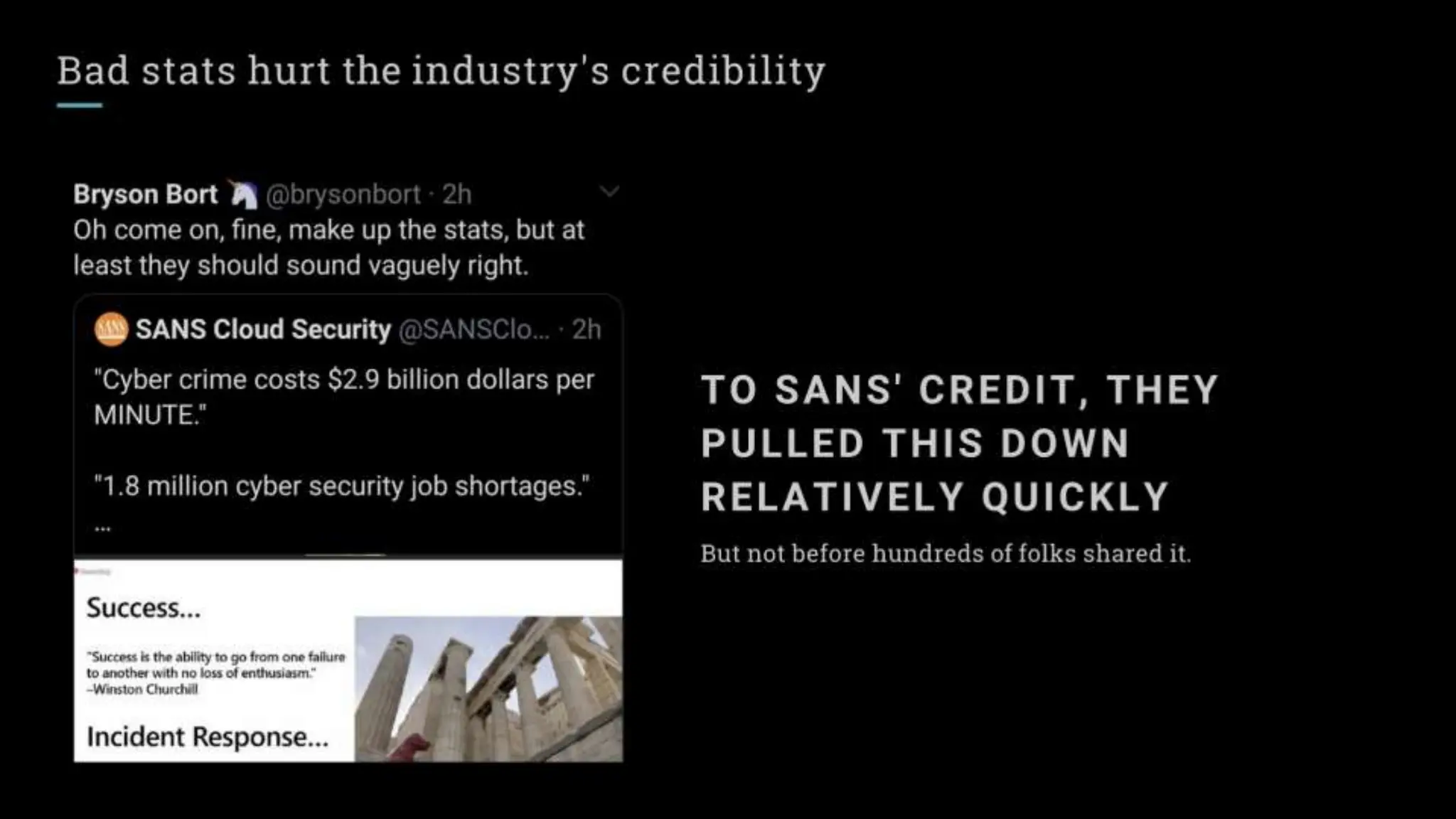
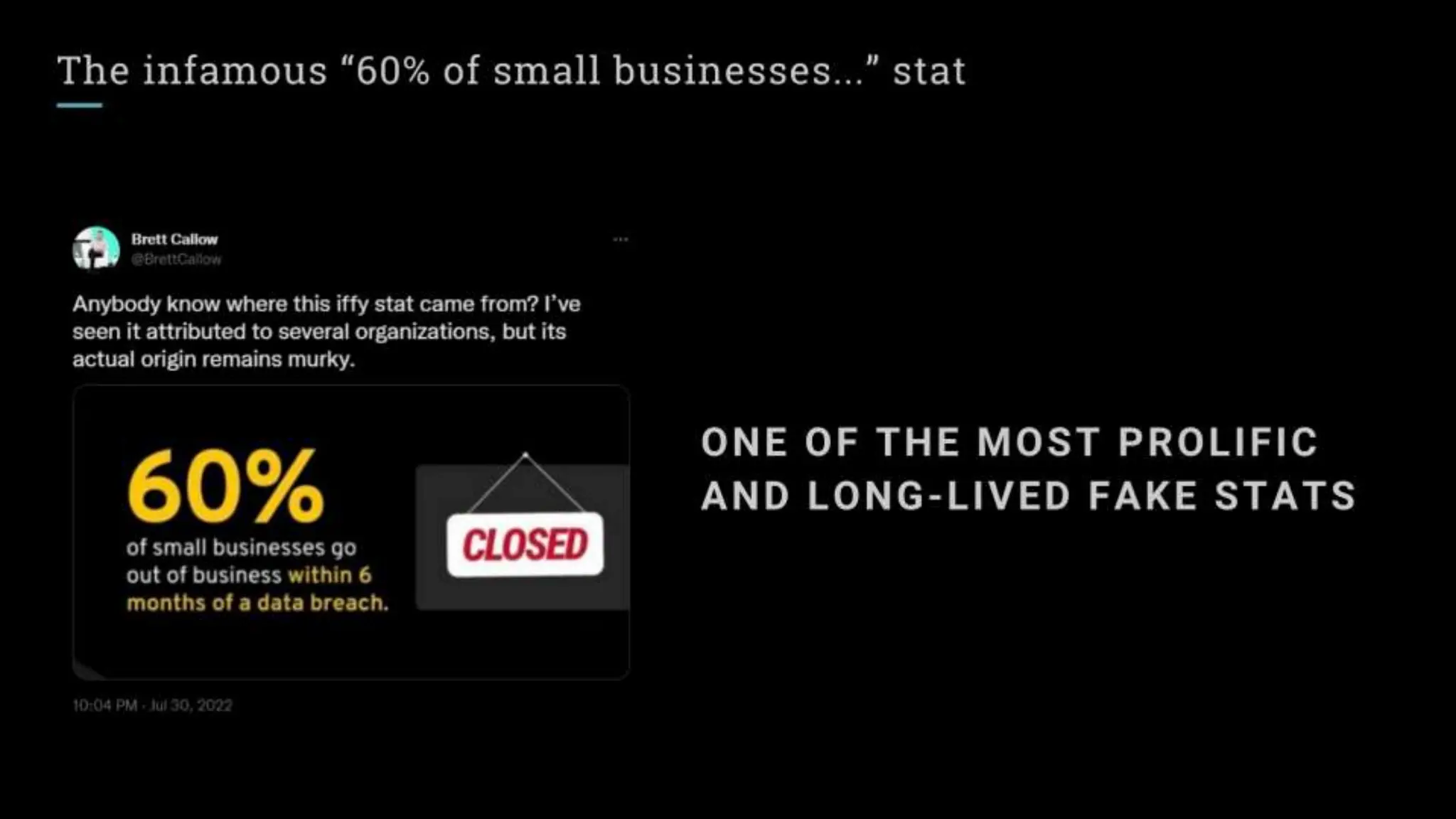
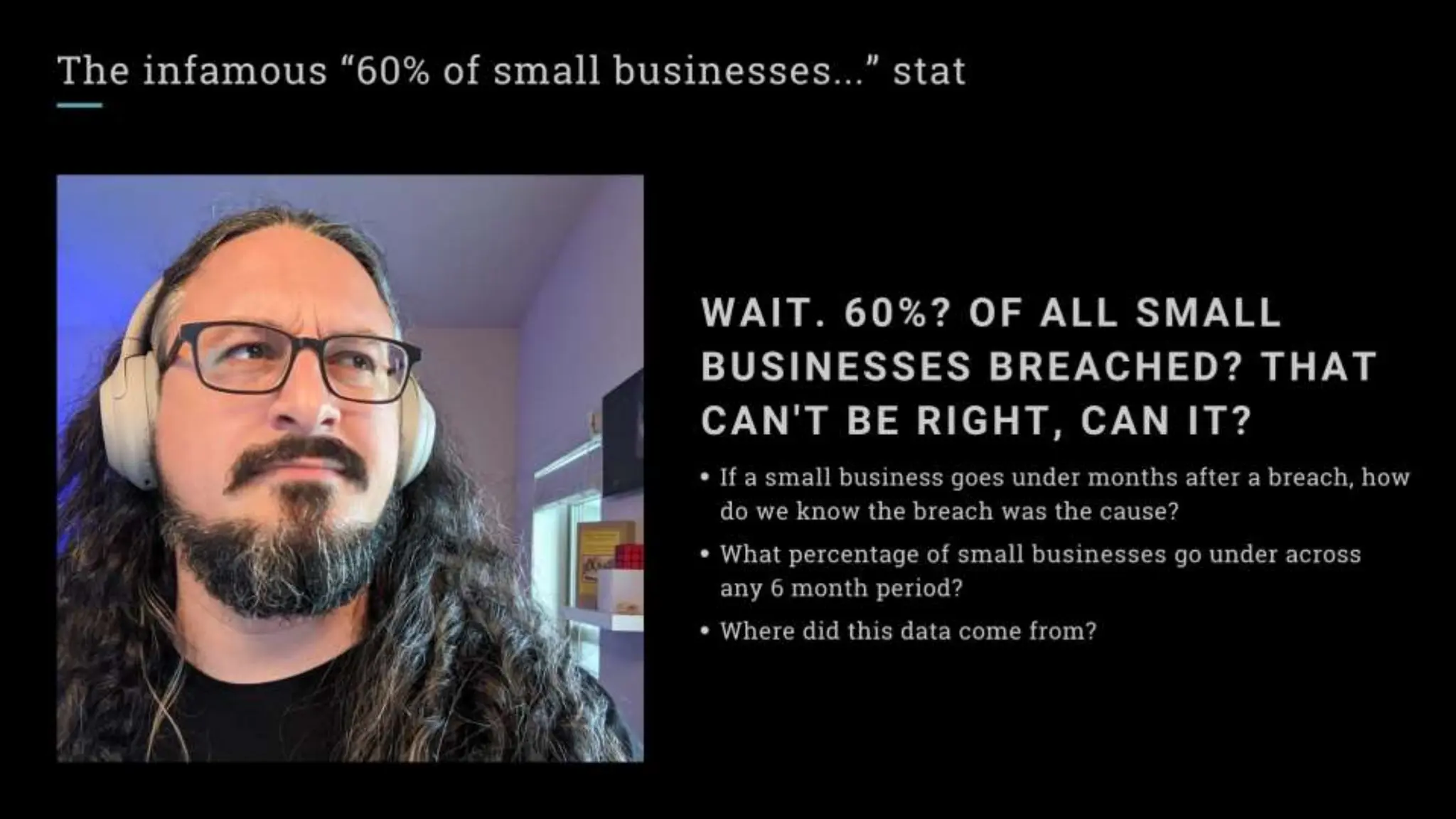
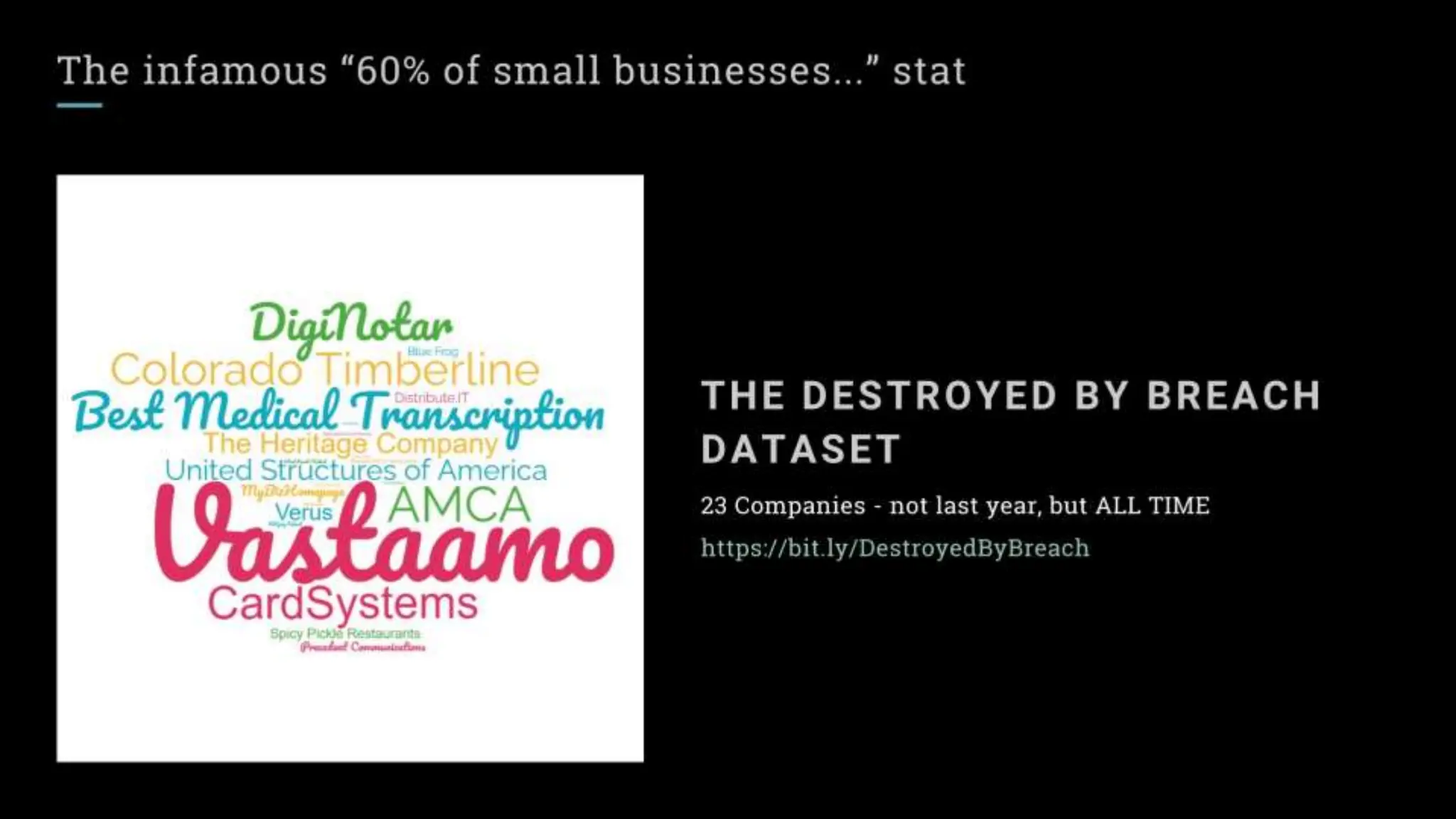
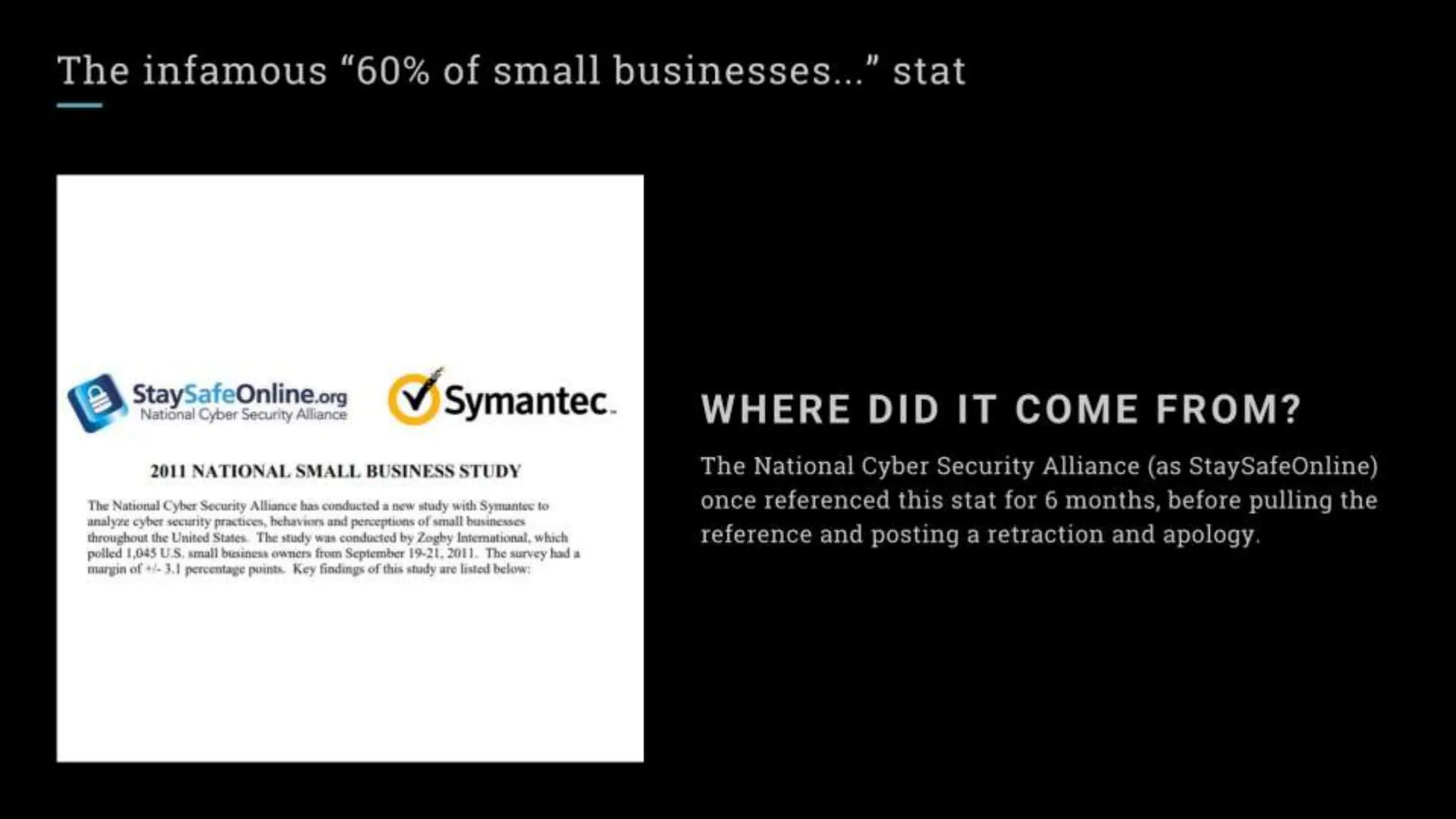
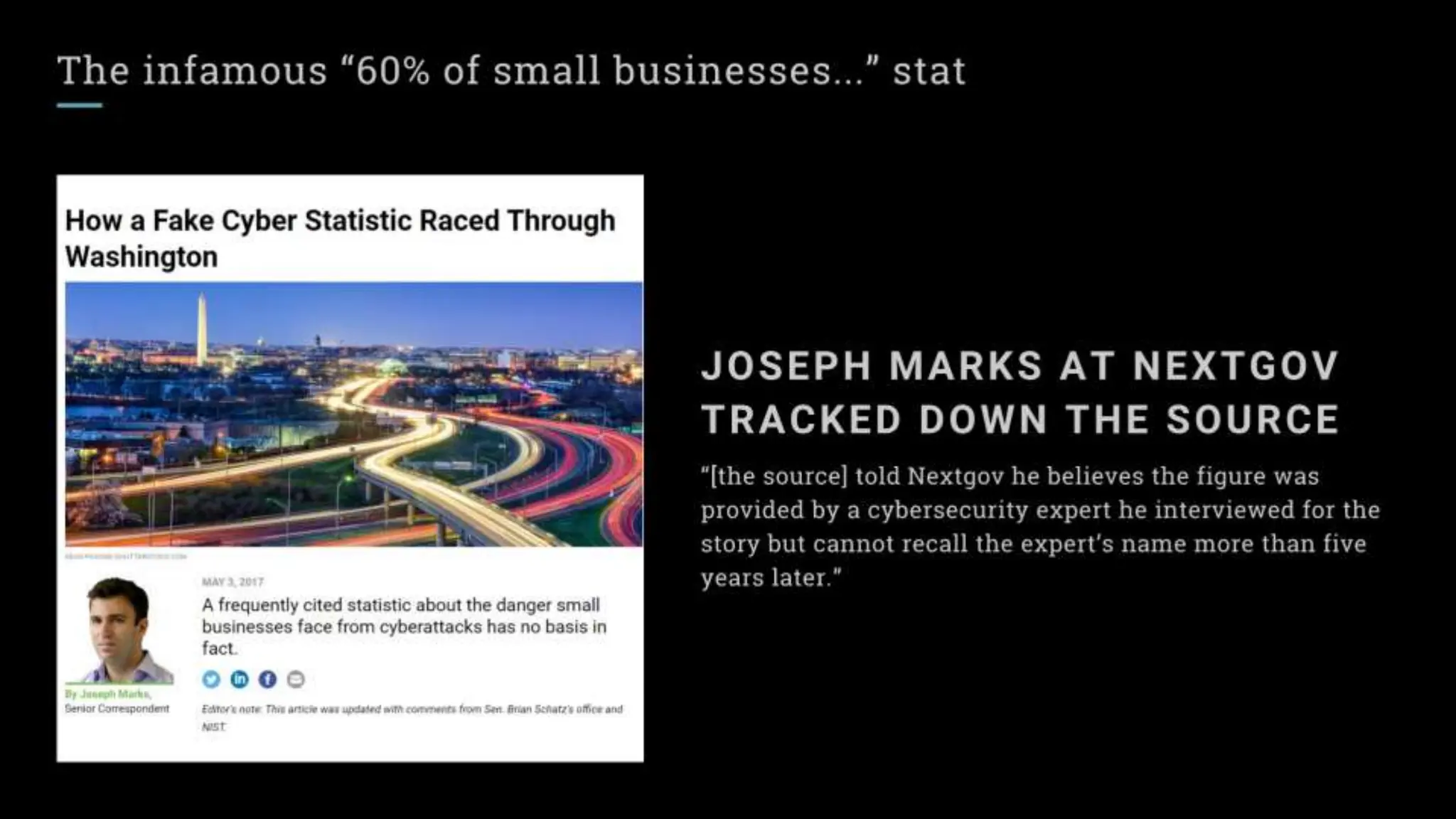
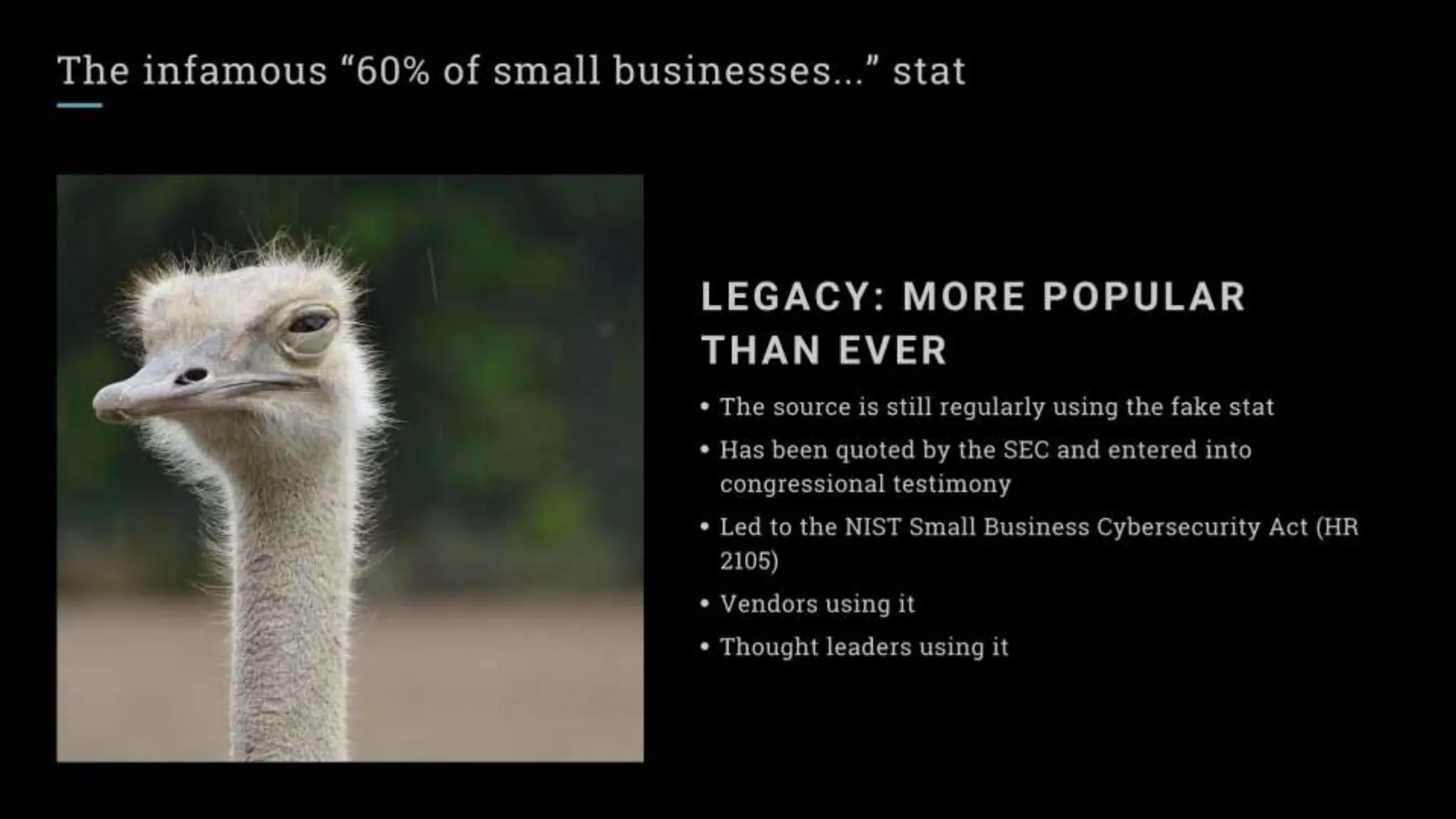
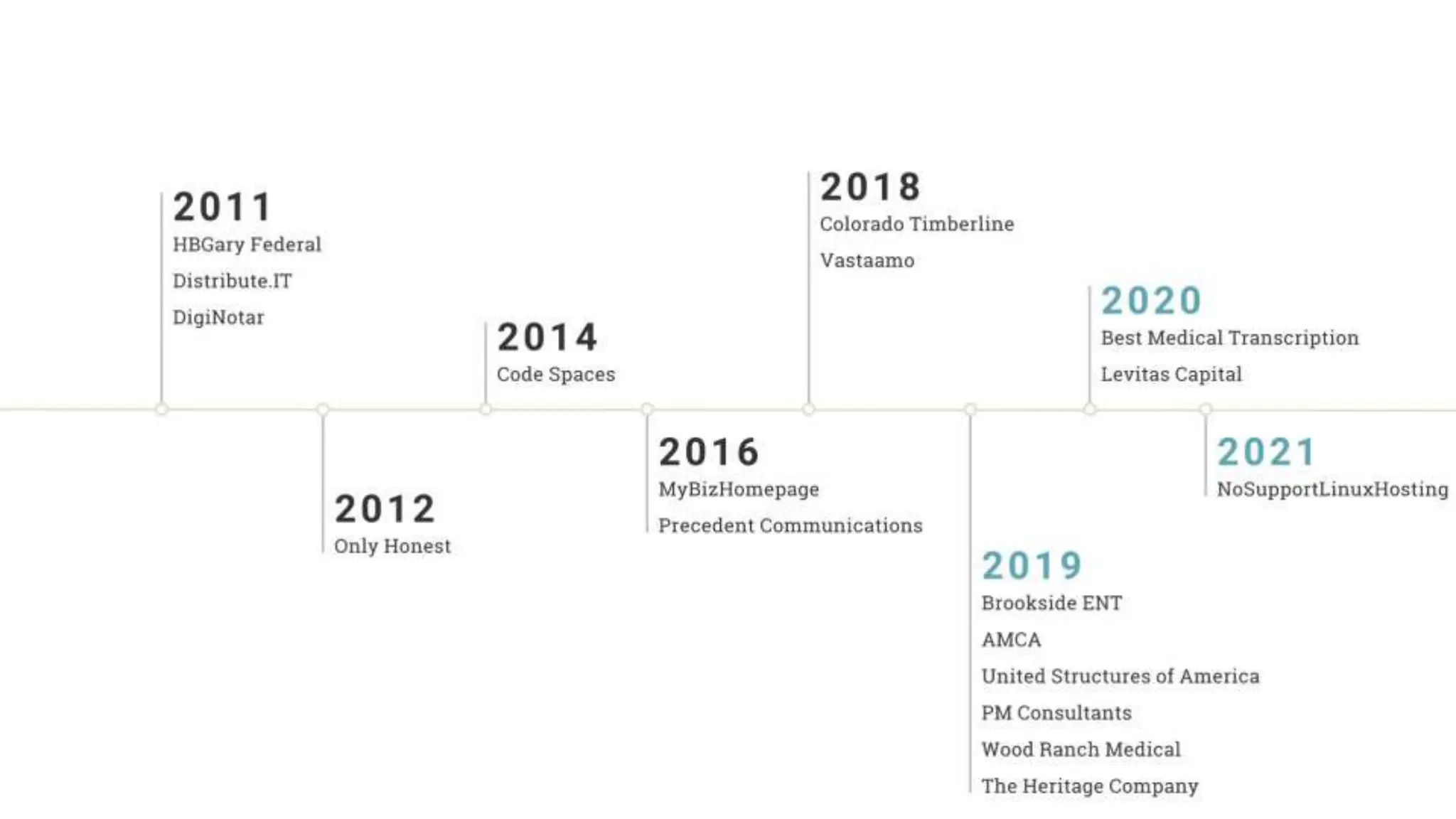
"Sixty percent of small businesses close within 6 months of being hacked."
There's a good chance you've seen this stat before. It has no basis in reality. The available evidence suggests quite the opposite.
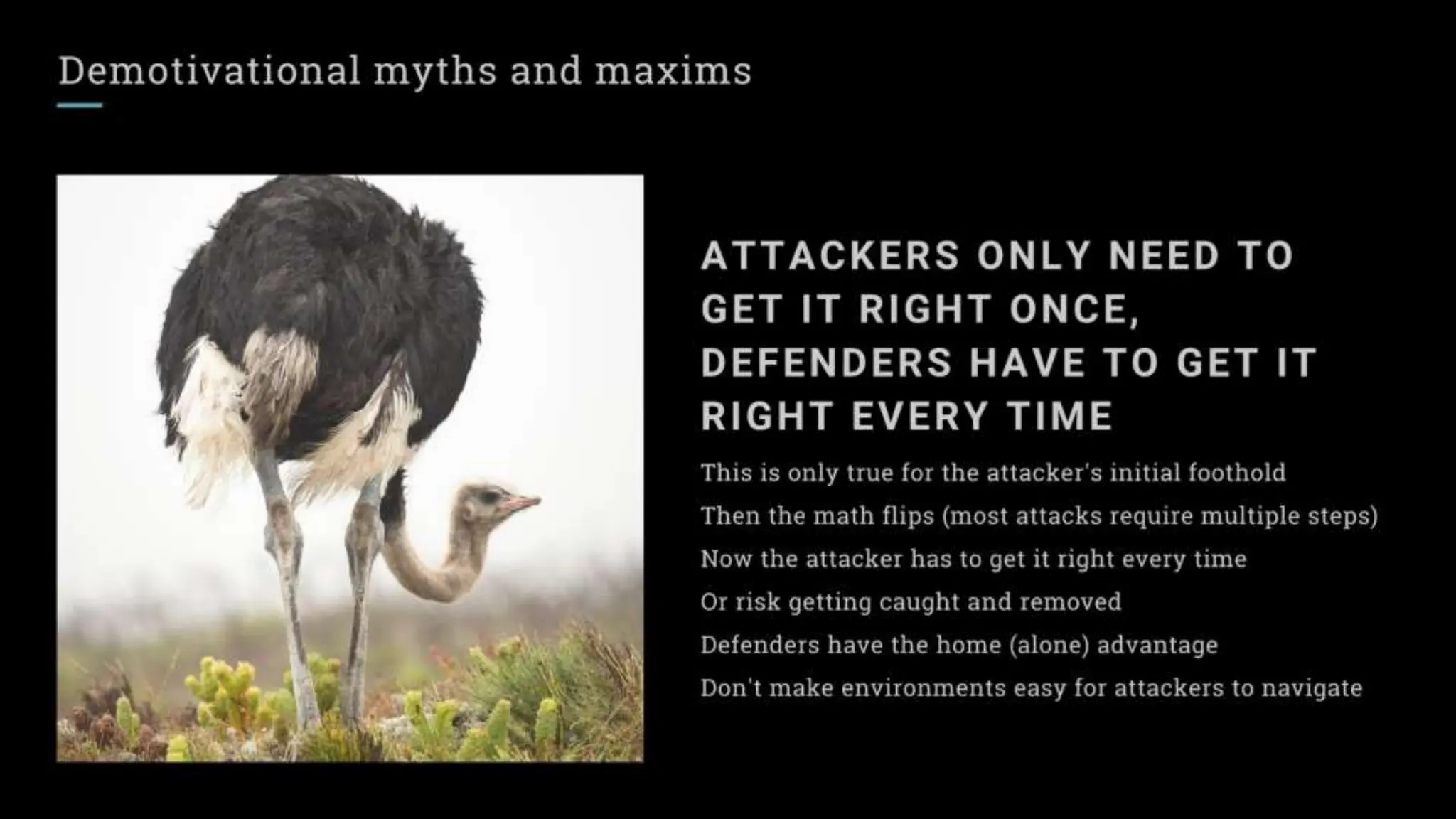
"Attackers only need to get it right once, defenders have to get it right every single time."
This idea has been repeated so often in InfoSec that it has become generally accepted as a true statement. It isn't just wrong, it's demotivating and encourages defeatist thinking that can sink the morale of a security team.
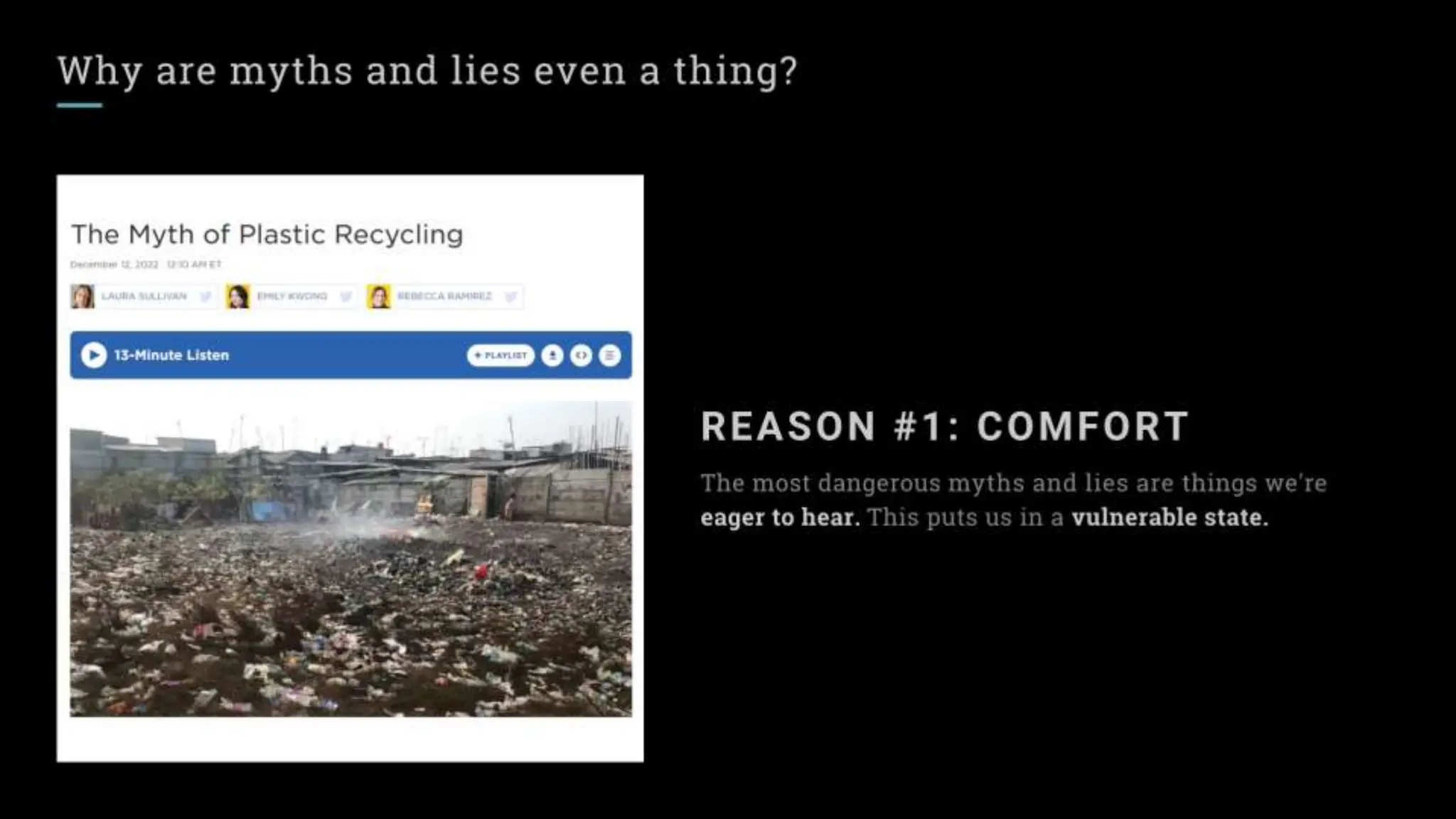
Most of the myths and lies in InfoSec take hold because they seem correct, or sound logical. Similar cognitive biases make it possible for even the most preposterous conspiracy theories to become commonly accepted in some groups.
This is a talk about the importance of critical thinking and checking sources in InfoSec. Our industry is relatively new and constantly changing. Too often, we operate more off faith and hope than fact or results. Exhausted and overworked defenders often don't have the time to seek direct evidence for claims, question sources, or test theories for themselves.
This talk compiles some of the most interesting research I’ve done over the past decade. My goal is to convince you to treat vendor claims, commonly accepted industry statistics, and best practices with healthy skepticism. You don't need to be a data scientist or OSINT expert to test theories and discover the truth - you just need to sacrifice a bit of your time now and then. I'll show you how.