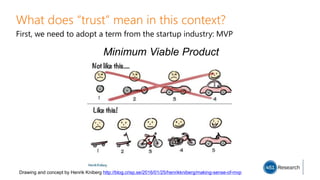
The document critiques the tendency to blame users for security breaches, advocating instead for understanding their needs and behaviors. It discusses the failures of app whitelisting and network access control due to their complexities and user confusion, emphasizing the importance of user-friendly security measures. The key takeaway is that a balance must be struck between security and user autonomy to foster a productive environment.