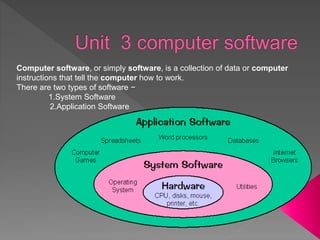
This document discusses two main types of computer software: system software and application software. System software includes operating systems, compilers, and device drivers. It interacts directly with hardware and is often written in low-level languages. Application software satisfies specific user needs and includes programs like word processors, spreadsheets, and games. Common examples of system software are discussed like operating systems, which manage computer resources and act as an interface between users and hardware.