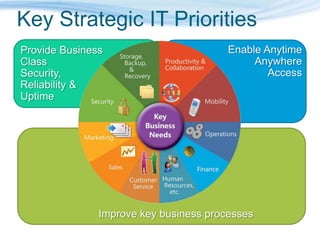
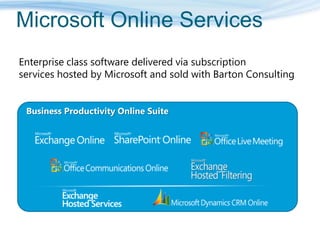
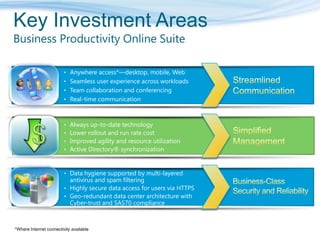
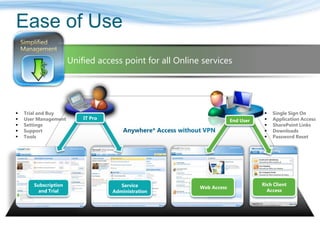
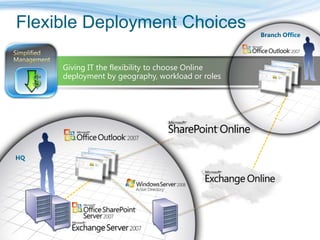
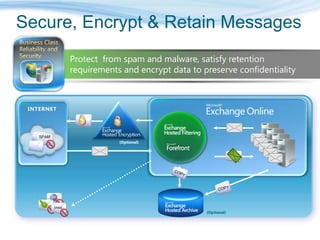
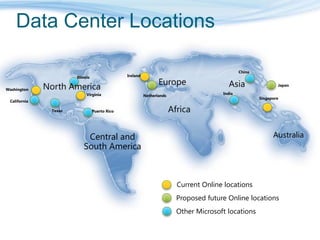
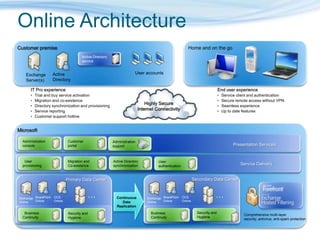
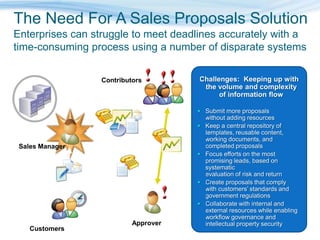
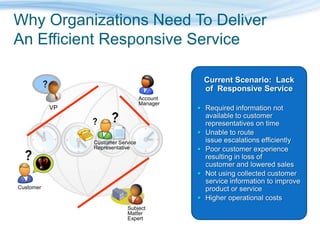
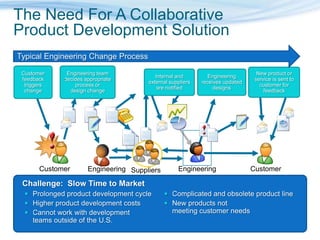
Barton Consulting is a Microsoft consultancy that specializes in online services and unified communications to reduce business IT costs. They provide enterprise-class communication tools like email, team portals, and conferencing through Microsoft Online Services delivered via subscription. The document discusses key considerations for IT investments, Microsoft Online Services offerings like Business Productivity Online Suite, and how Barton Consulting can help customers set up trials and deployments to accelerate speed to value.