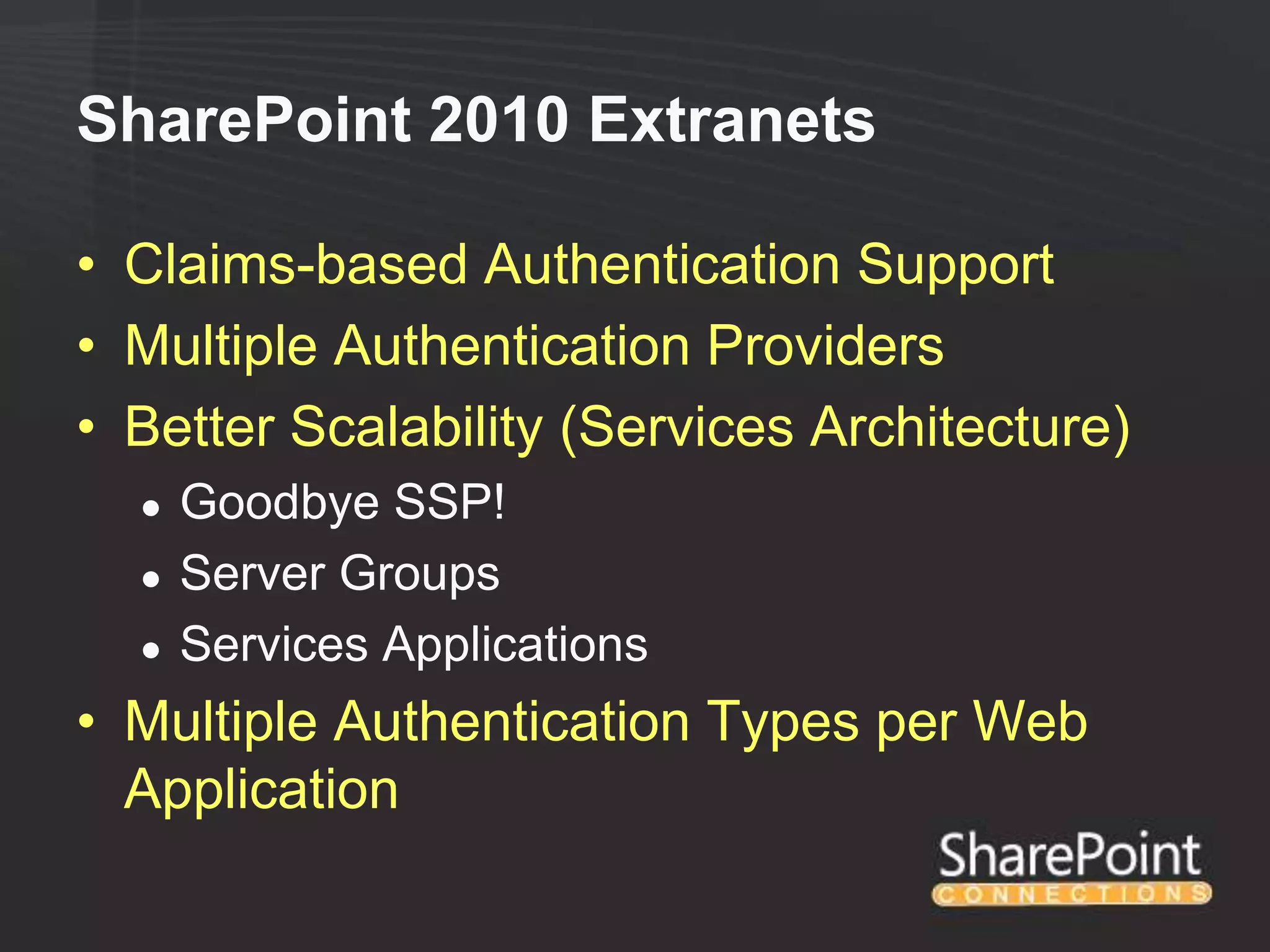
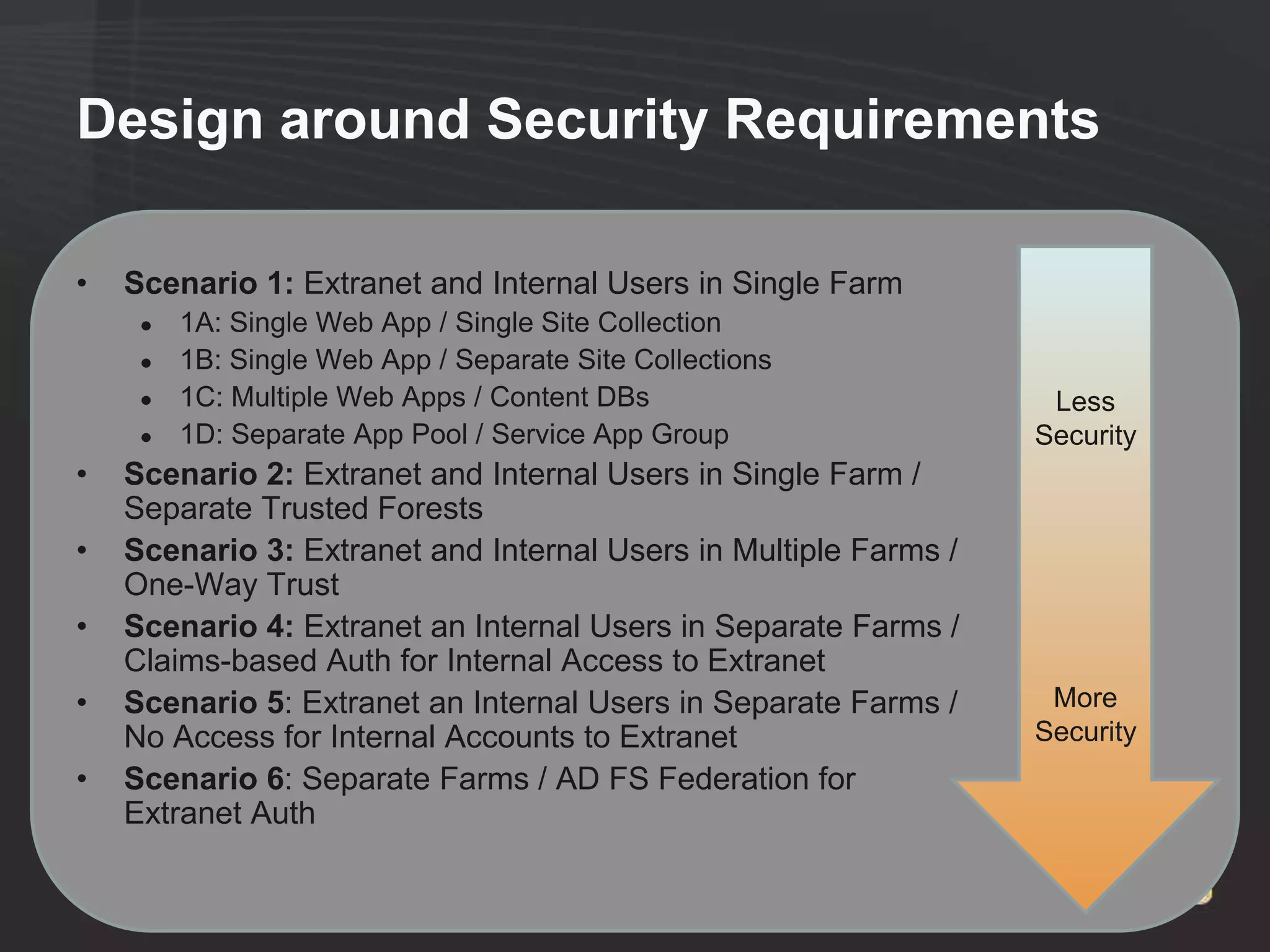
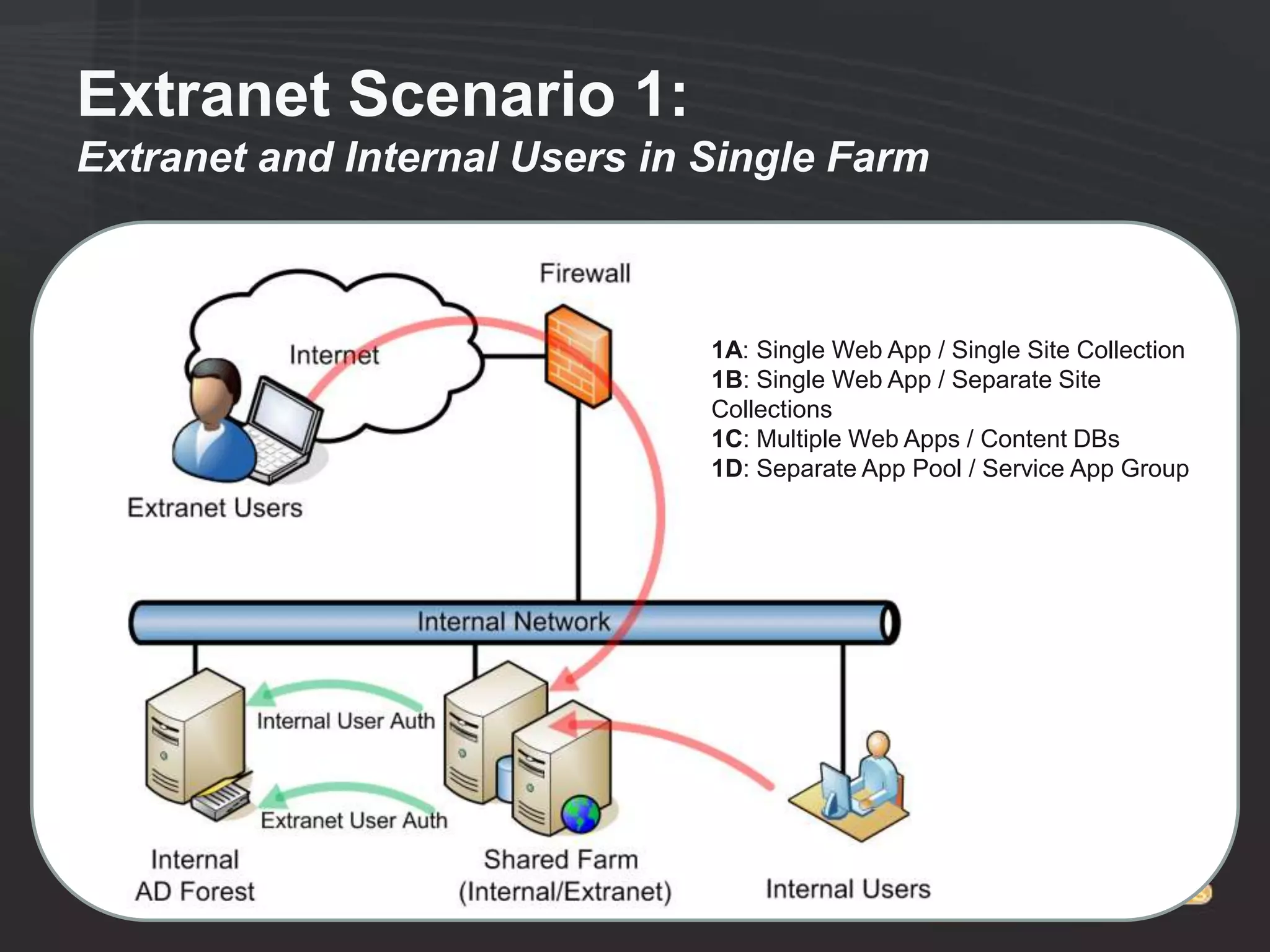
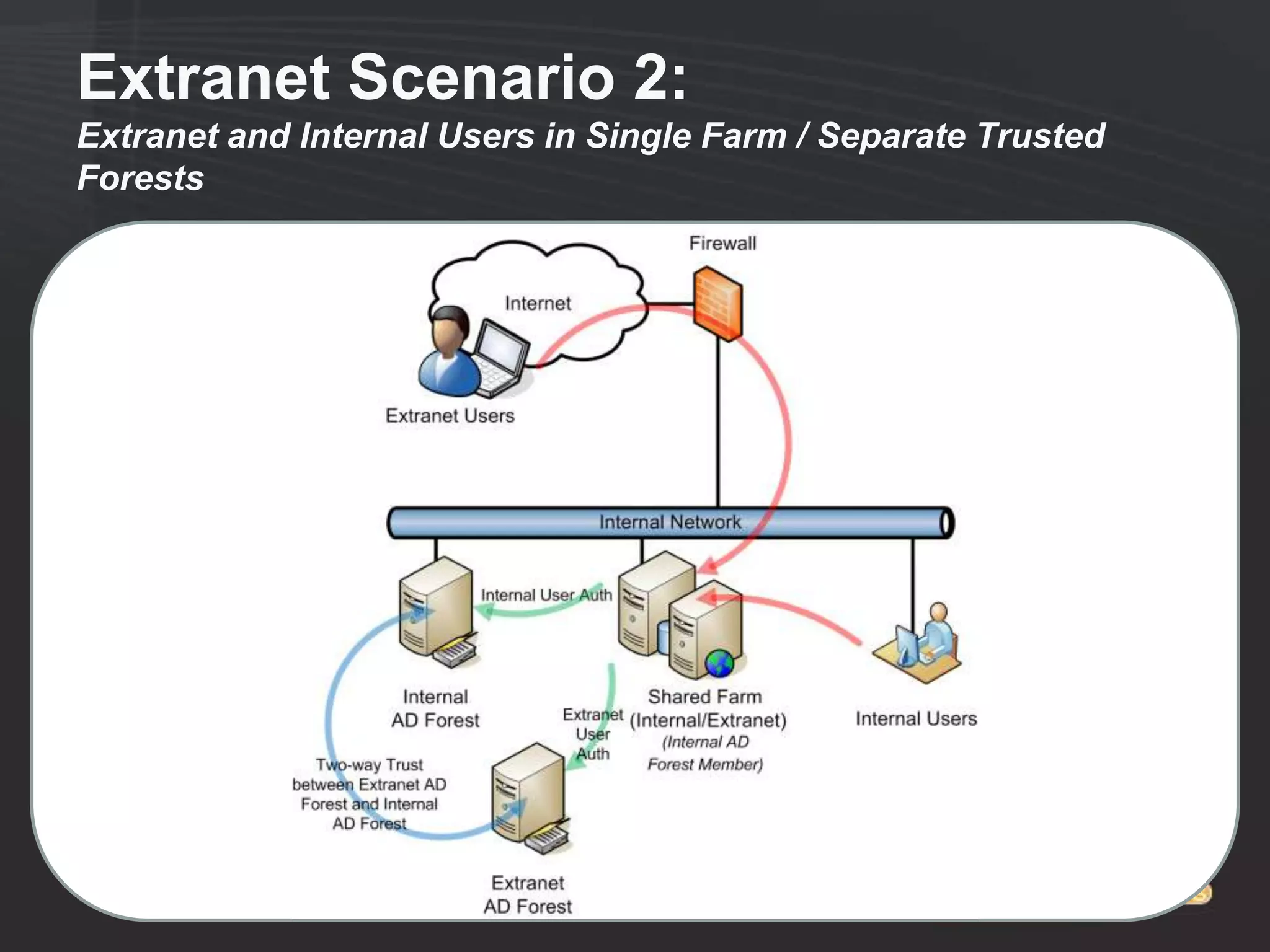
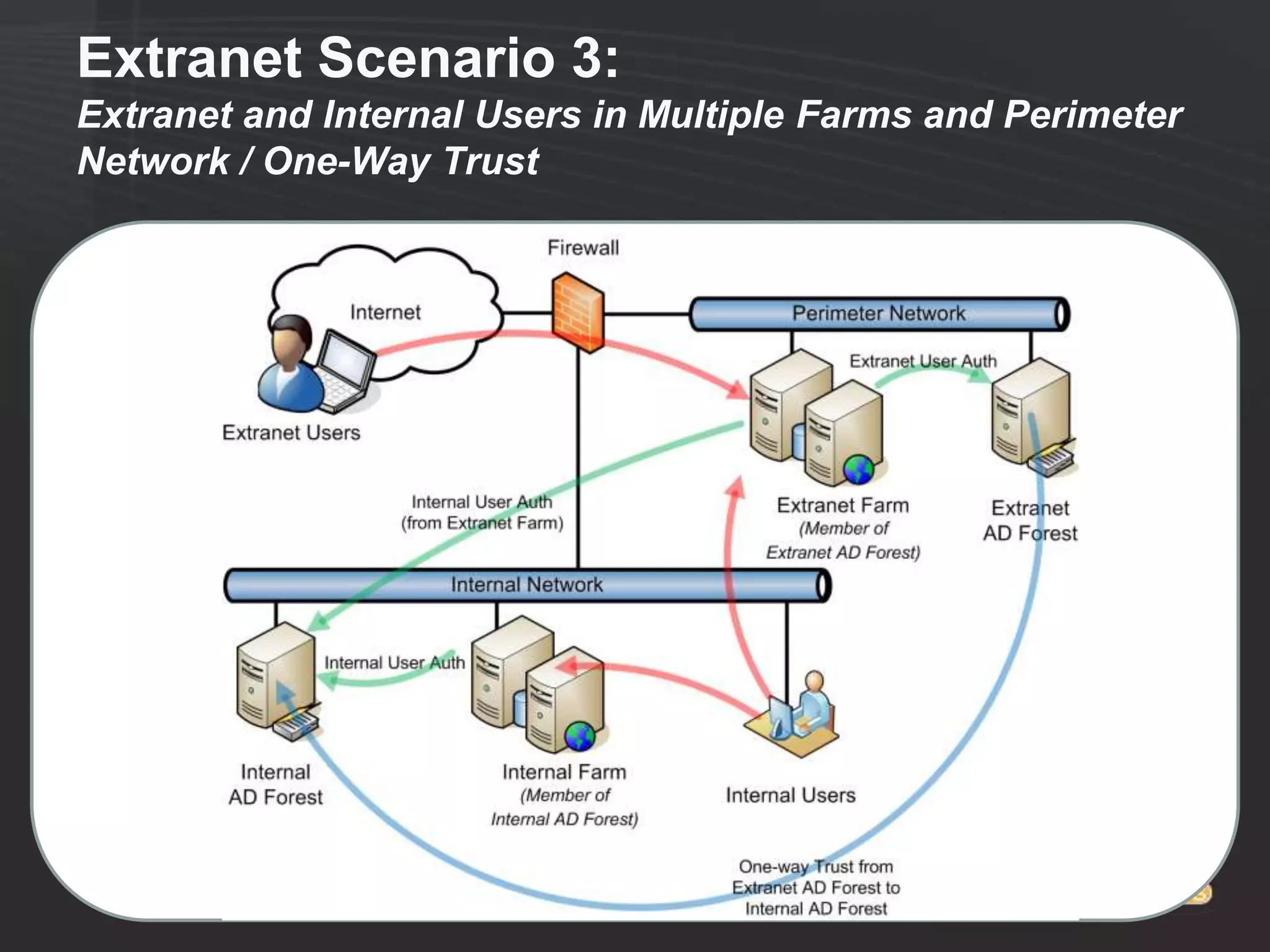
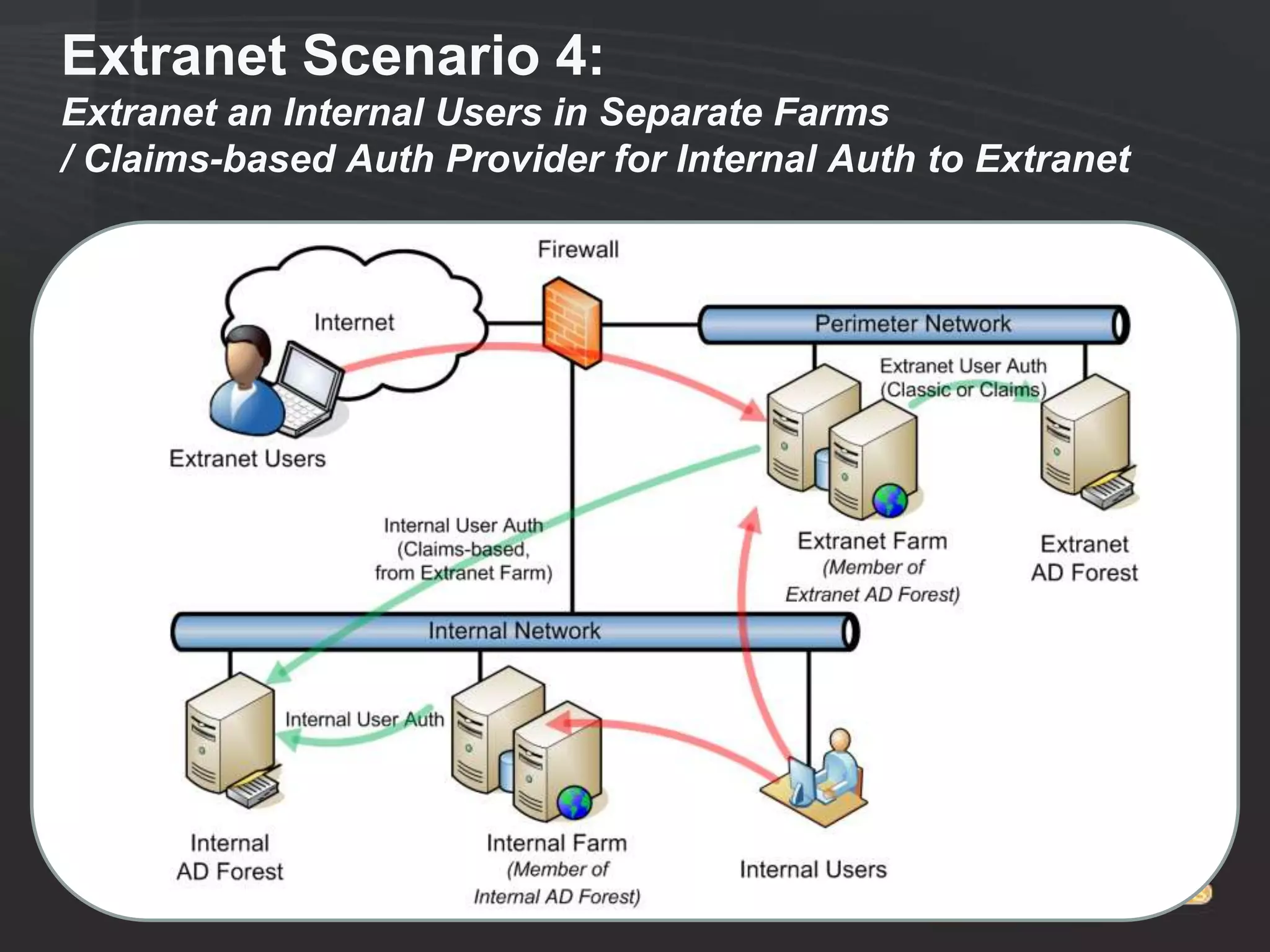
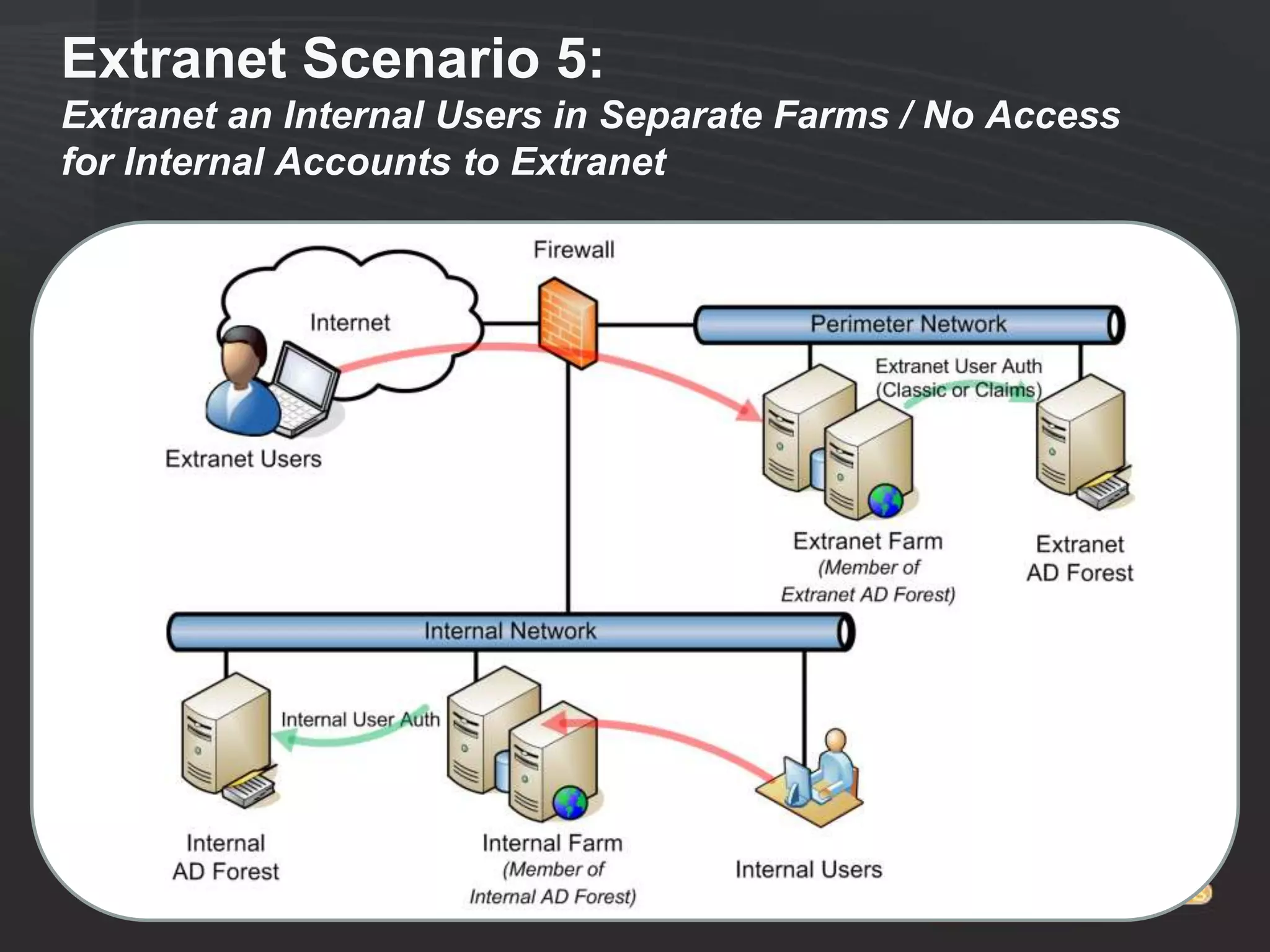
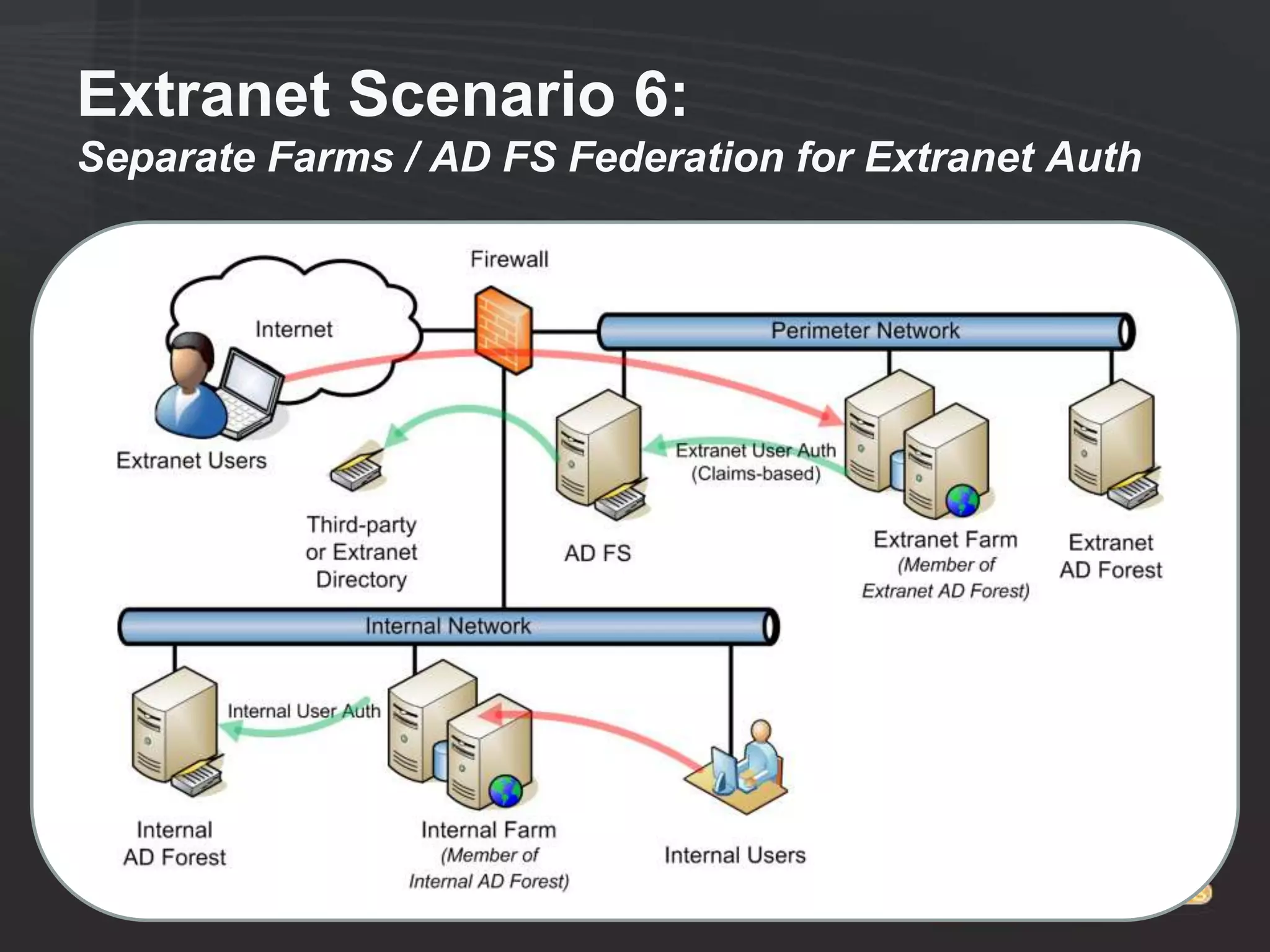
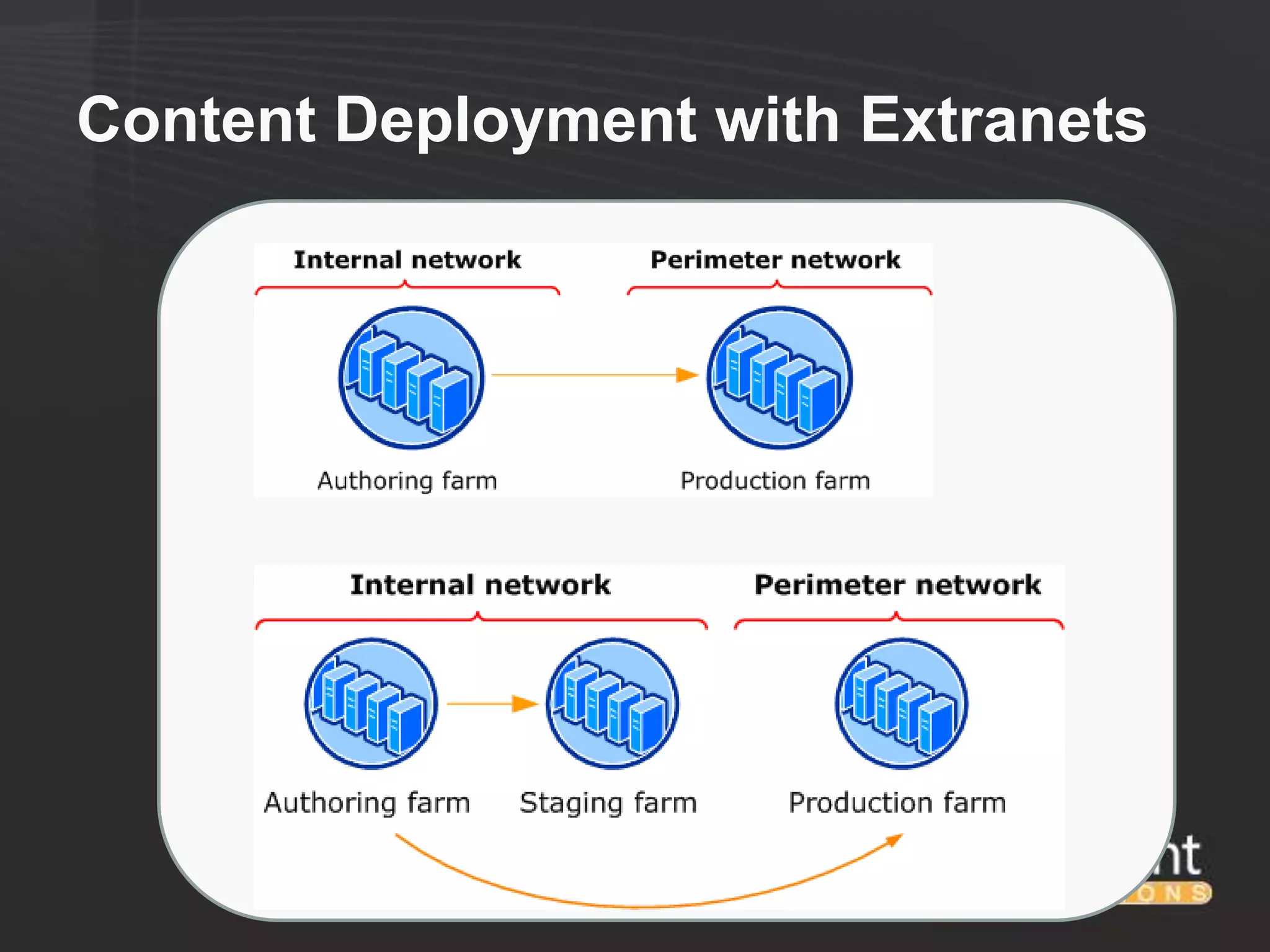
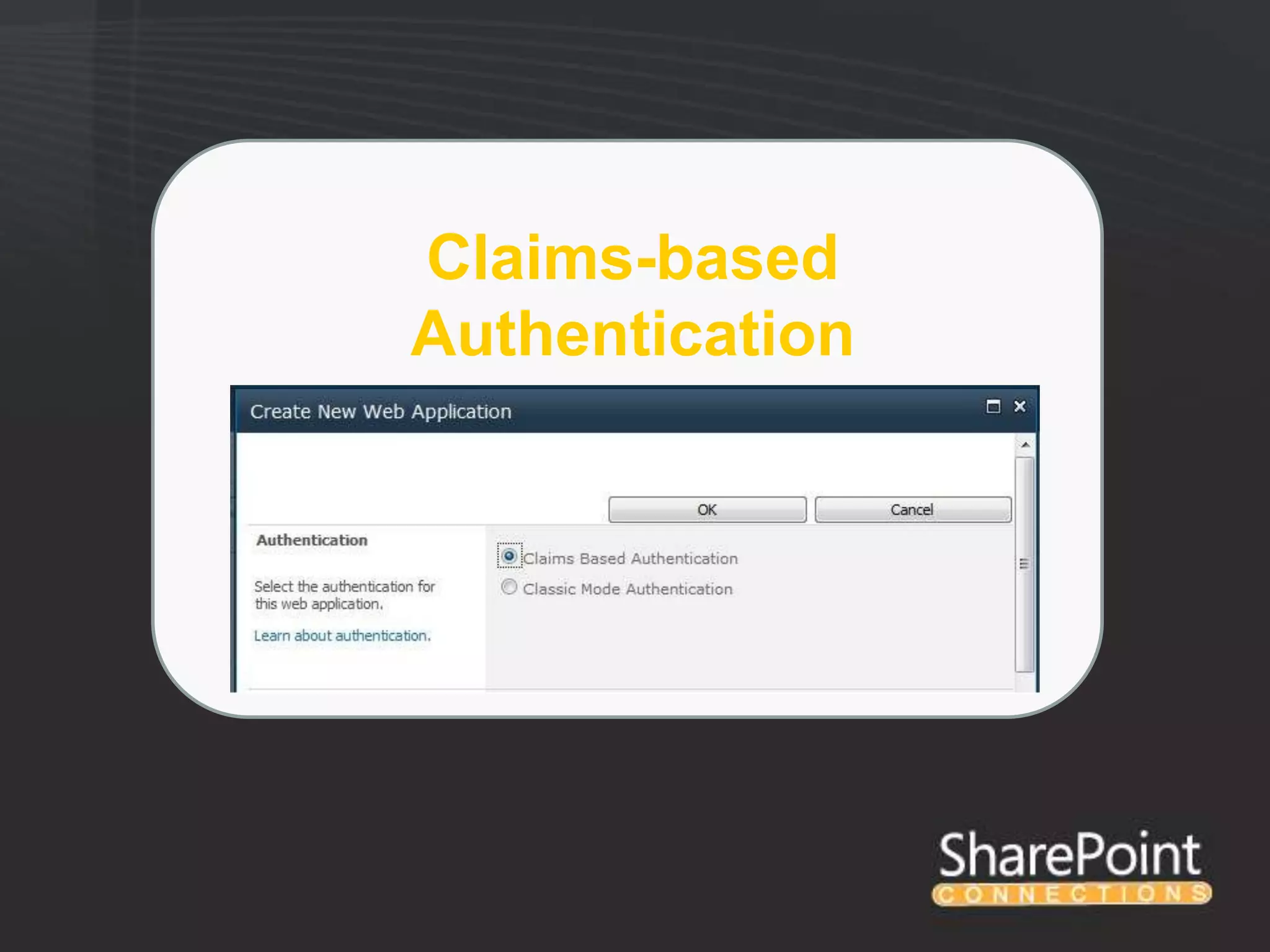
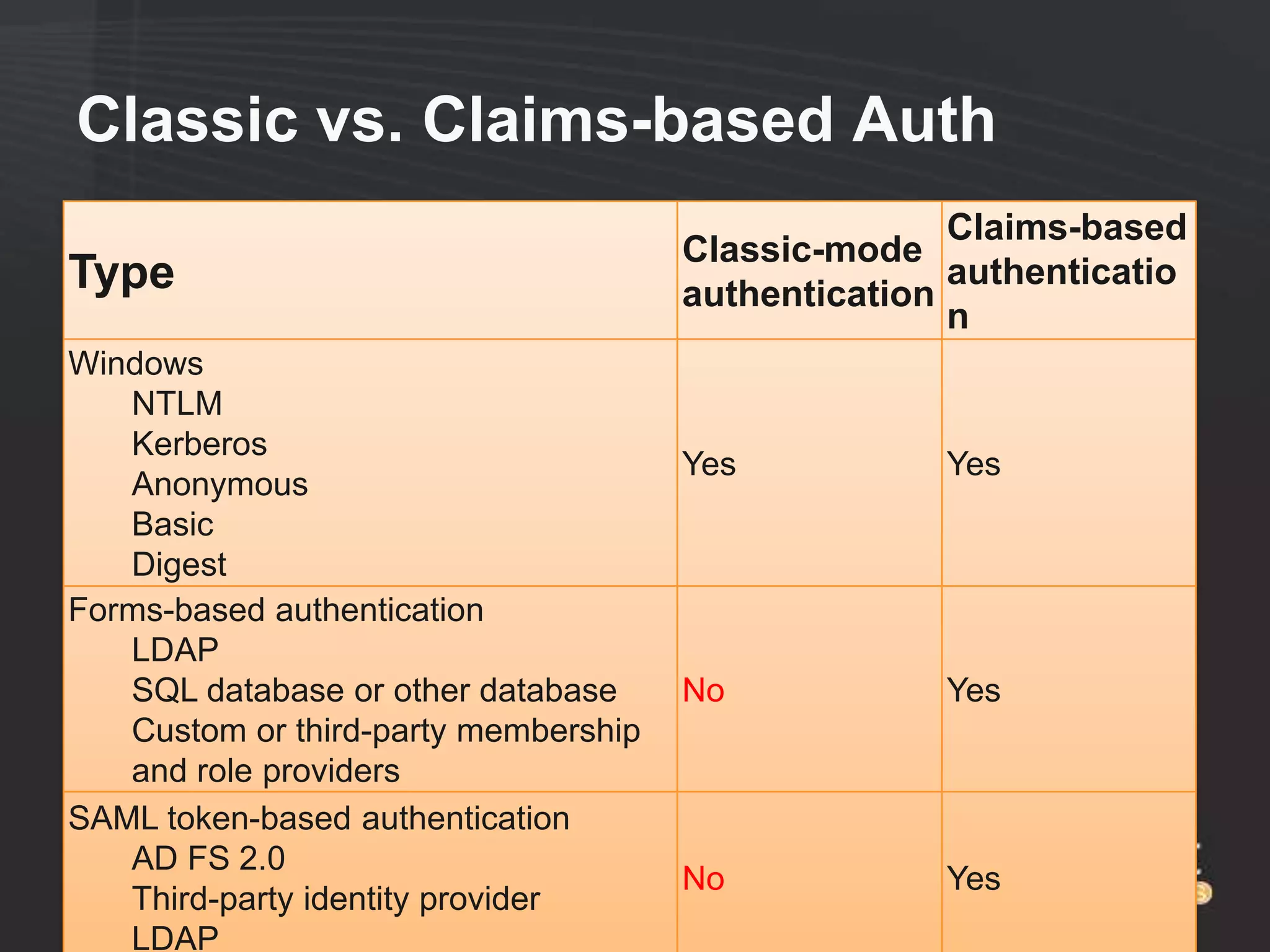
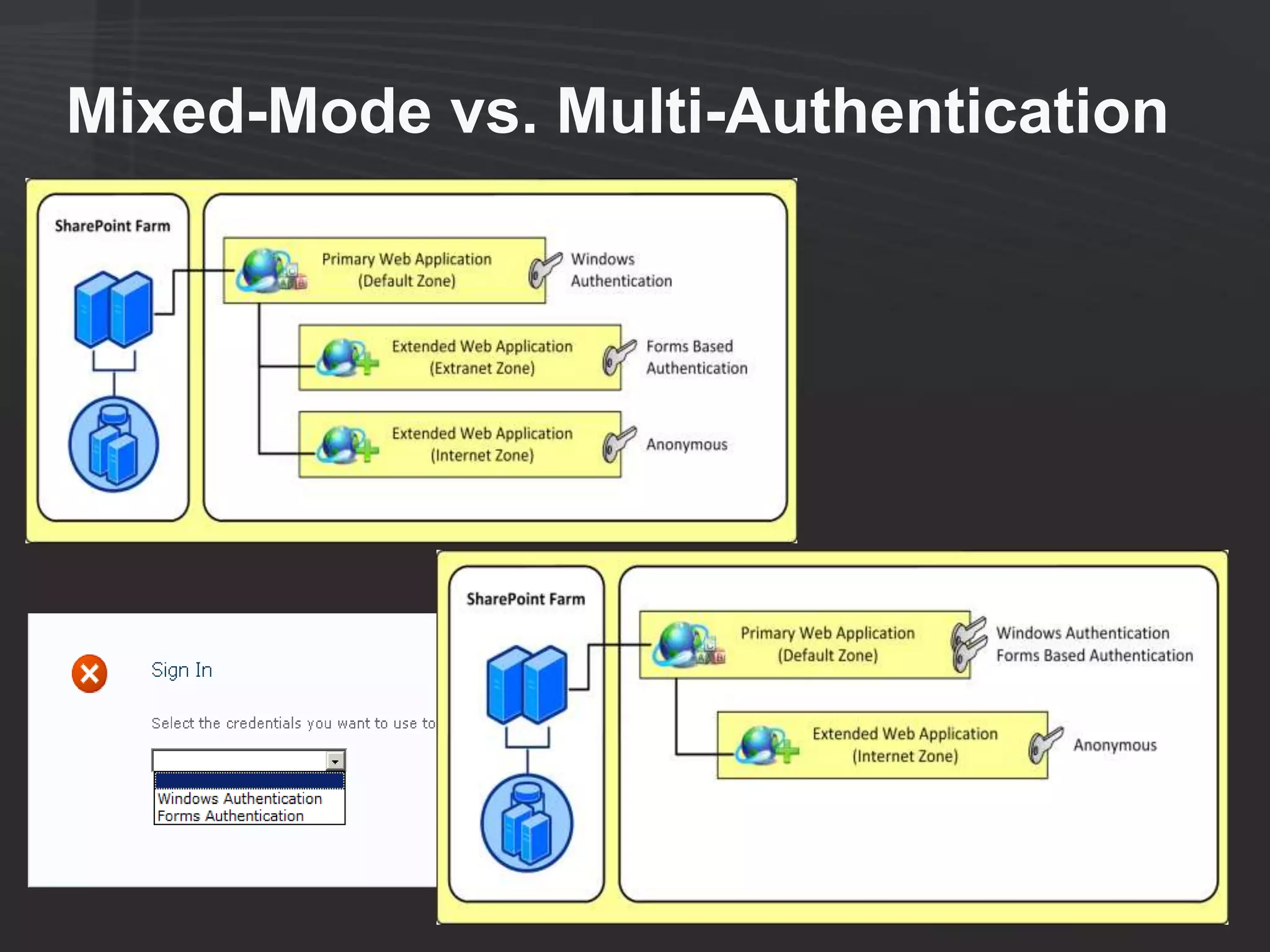
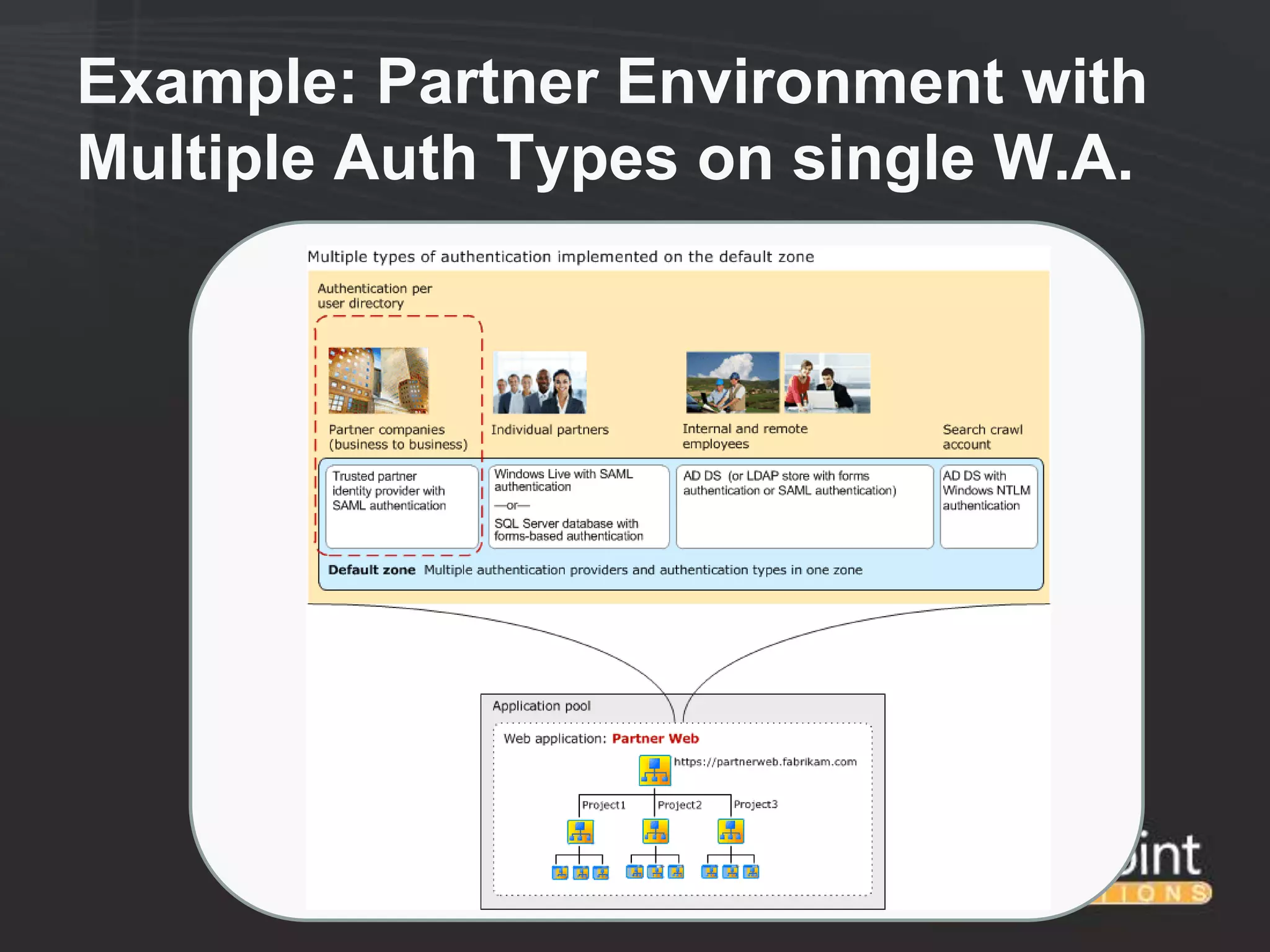
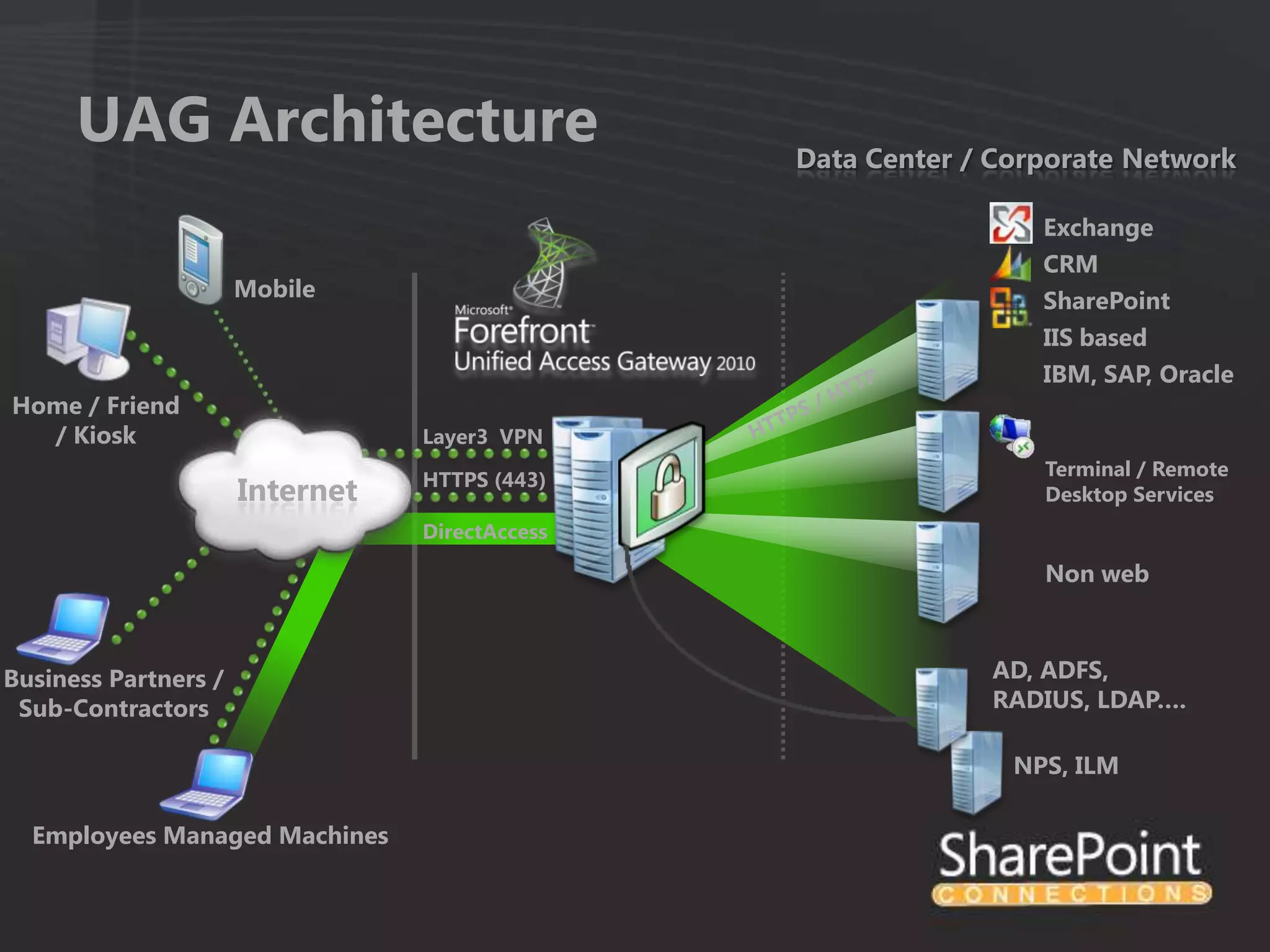
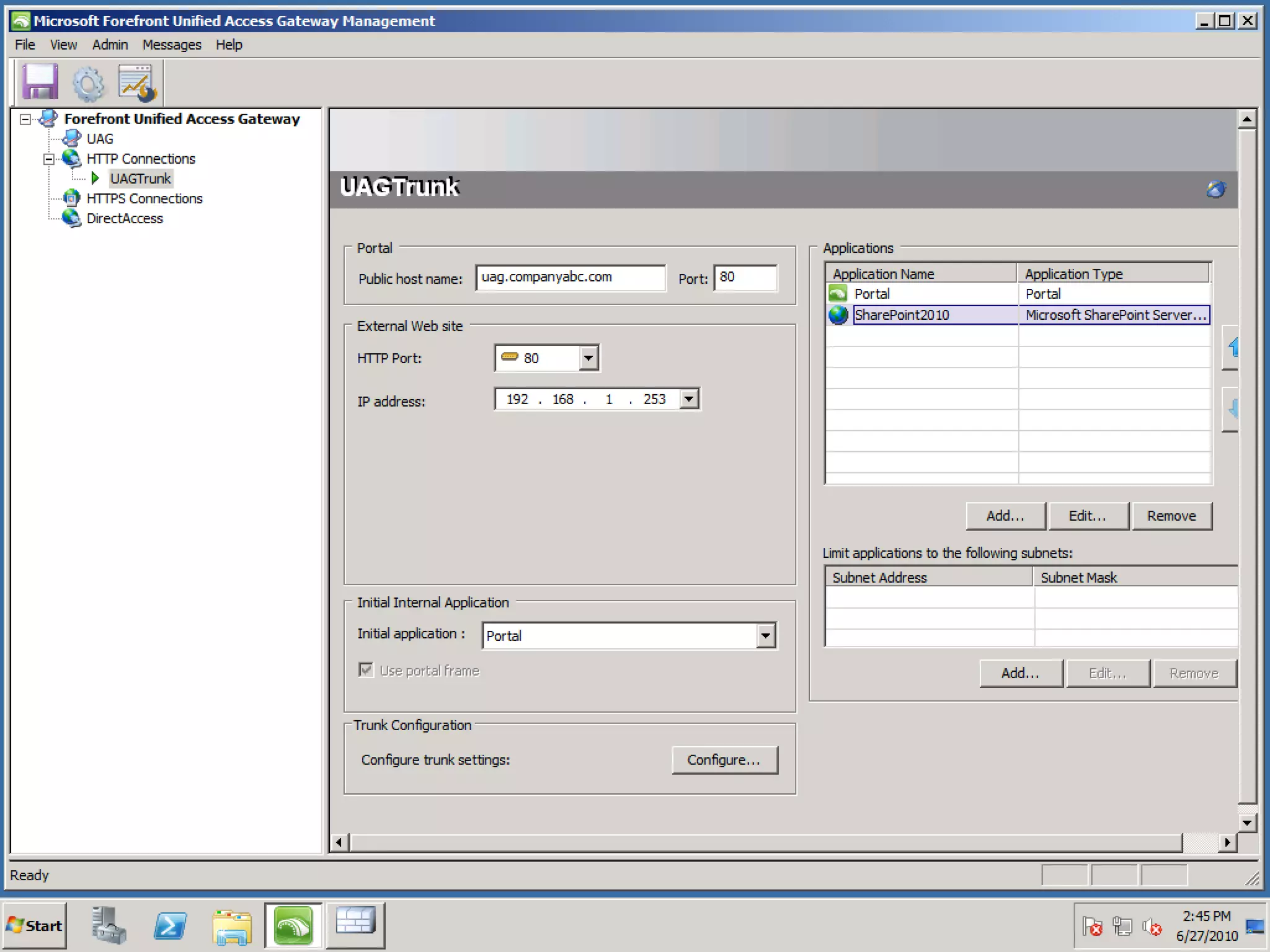
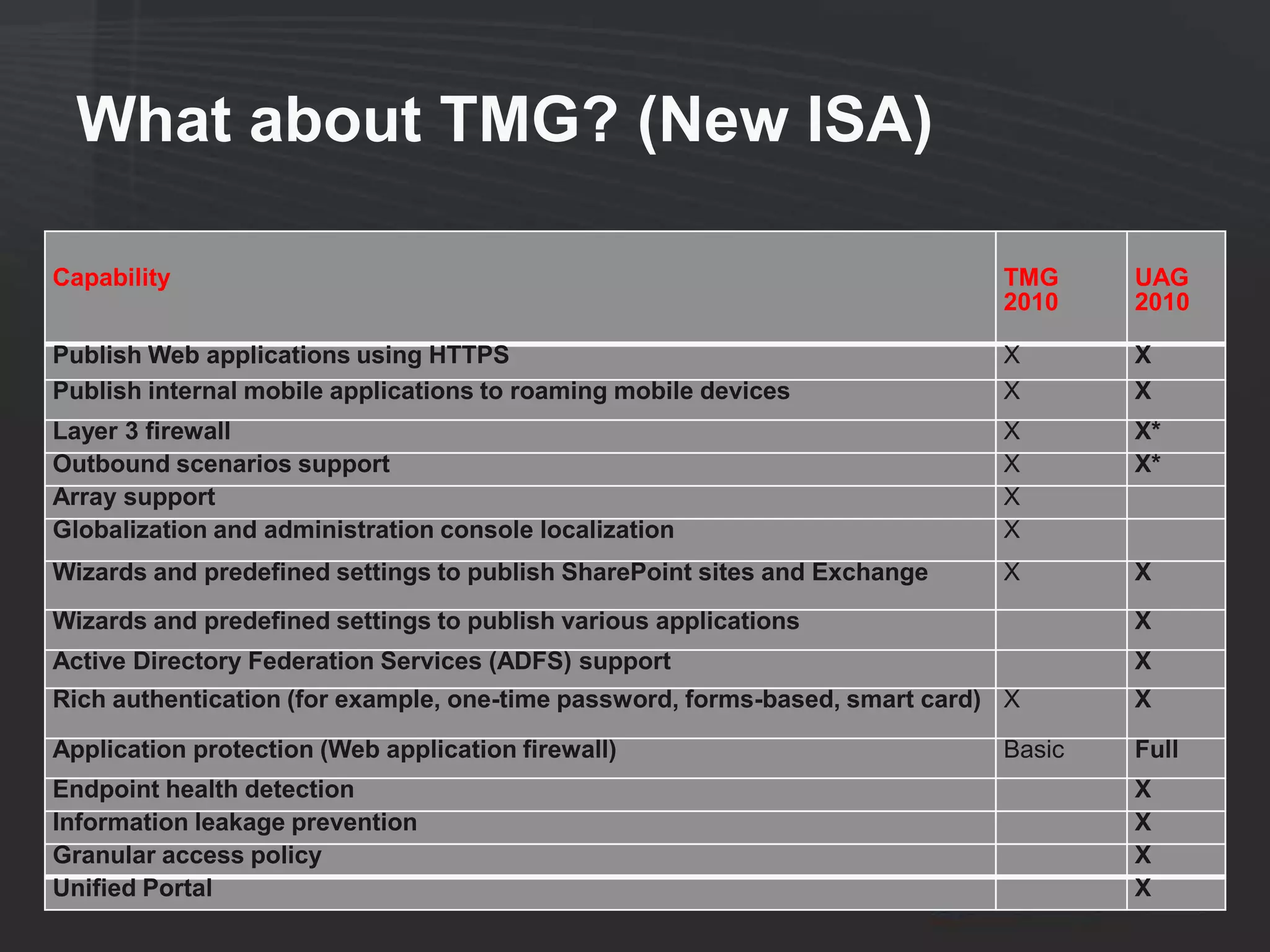
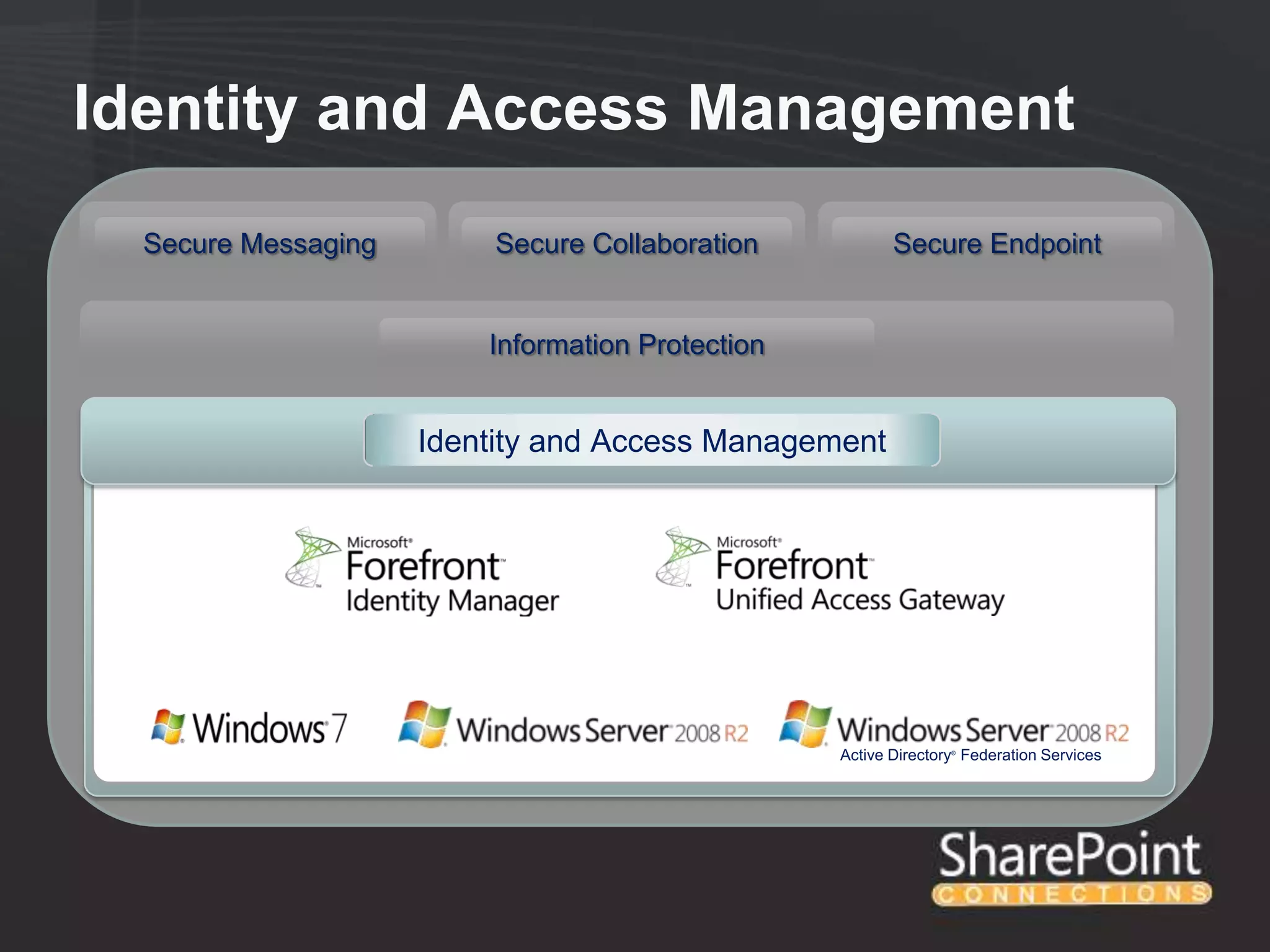
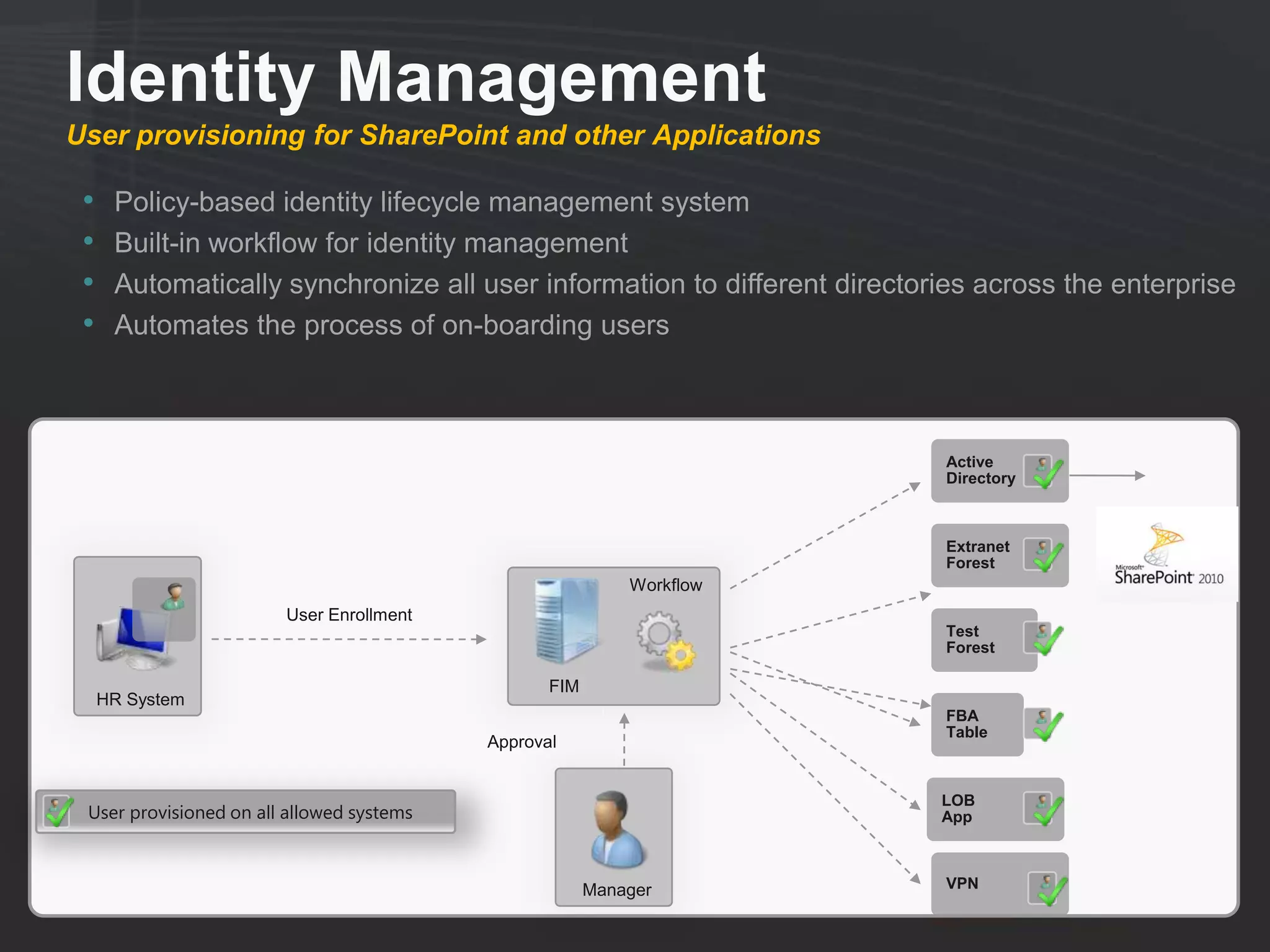
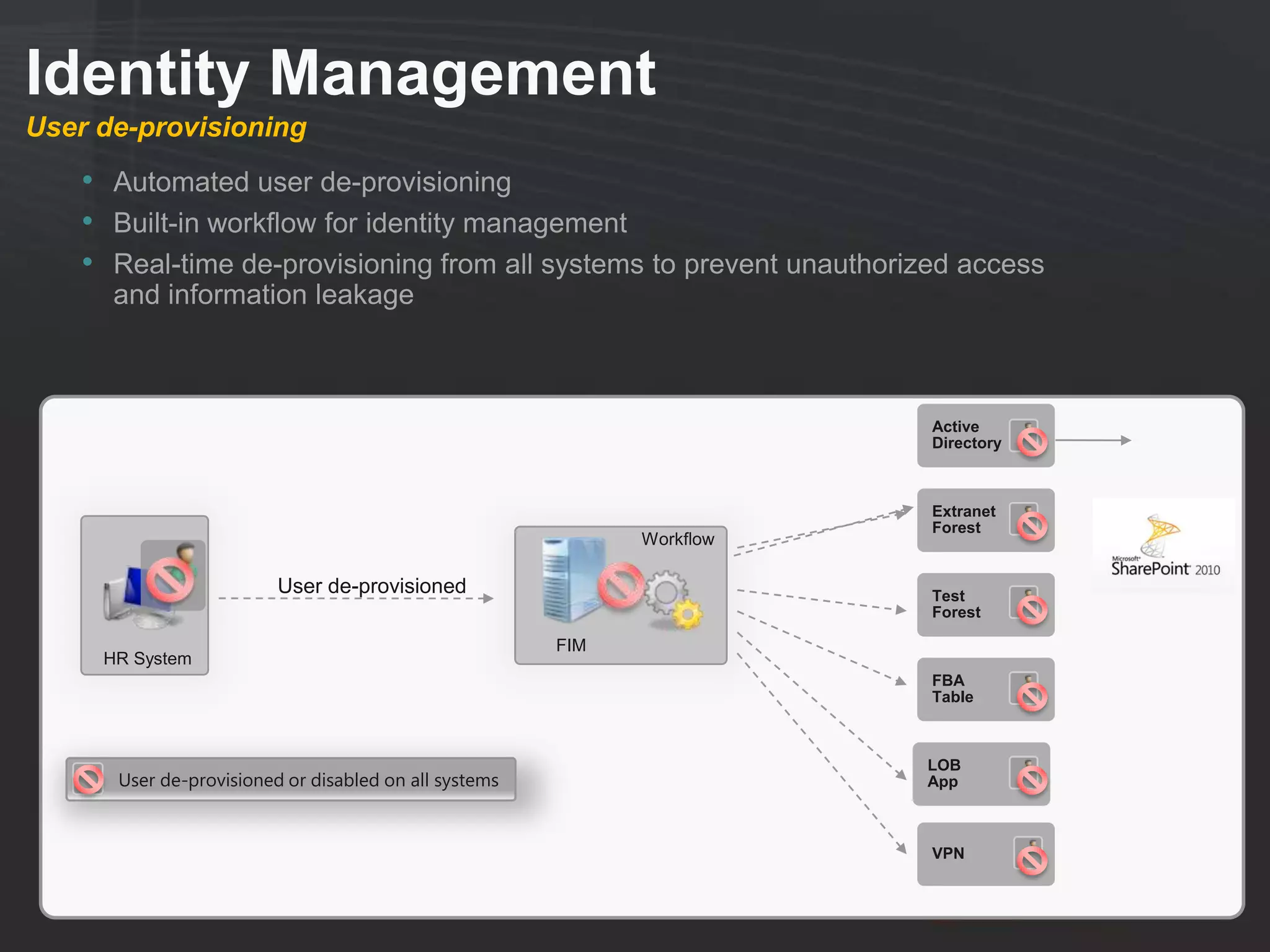
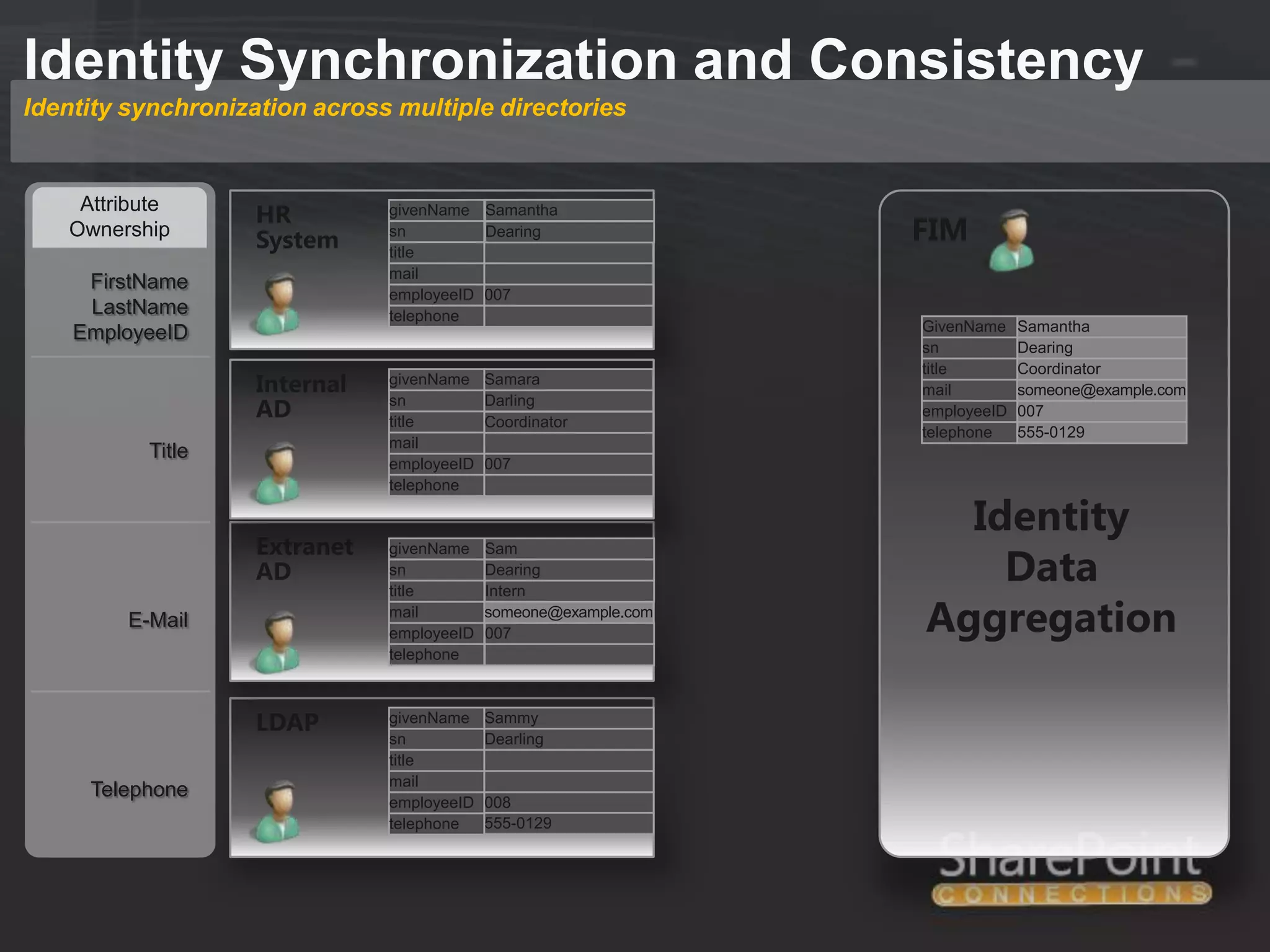
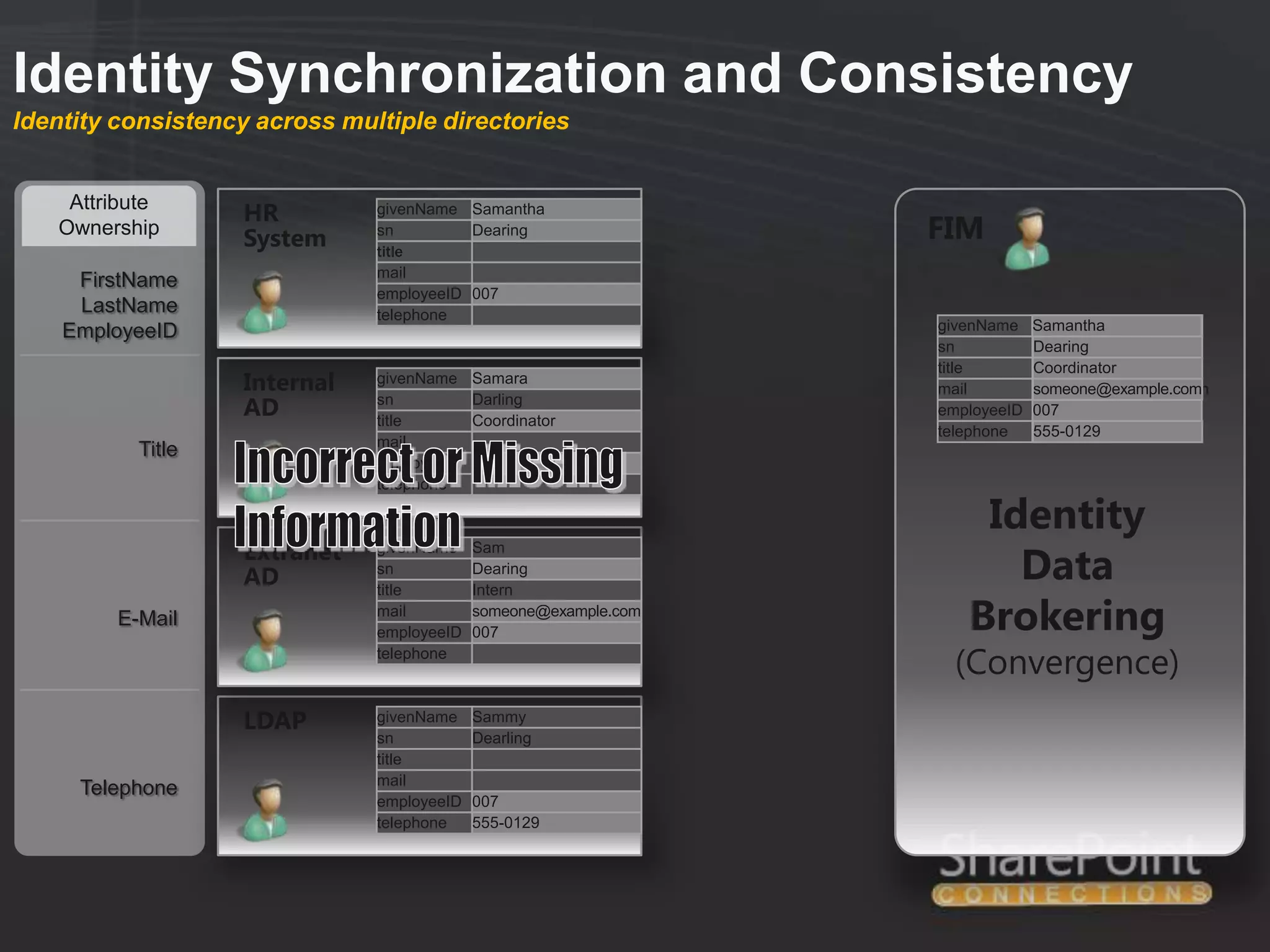
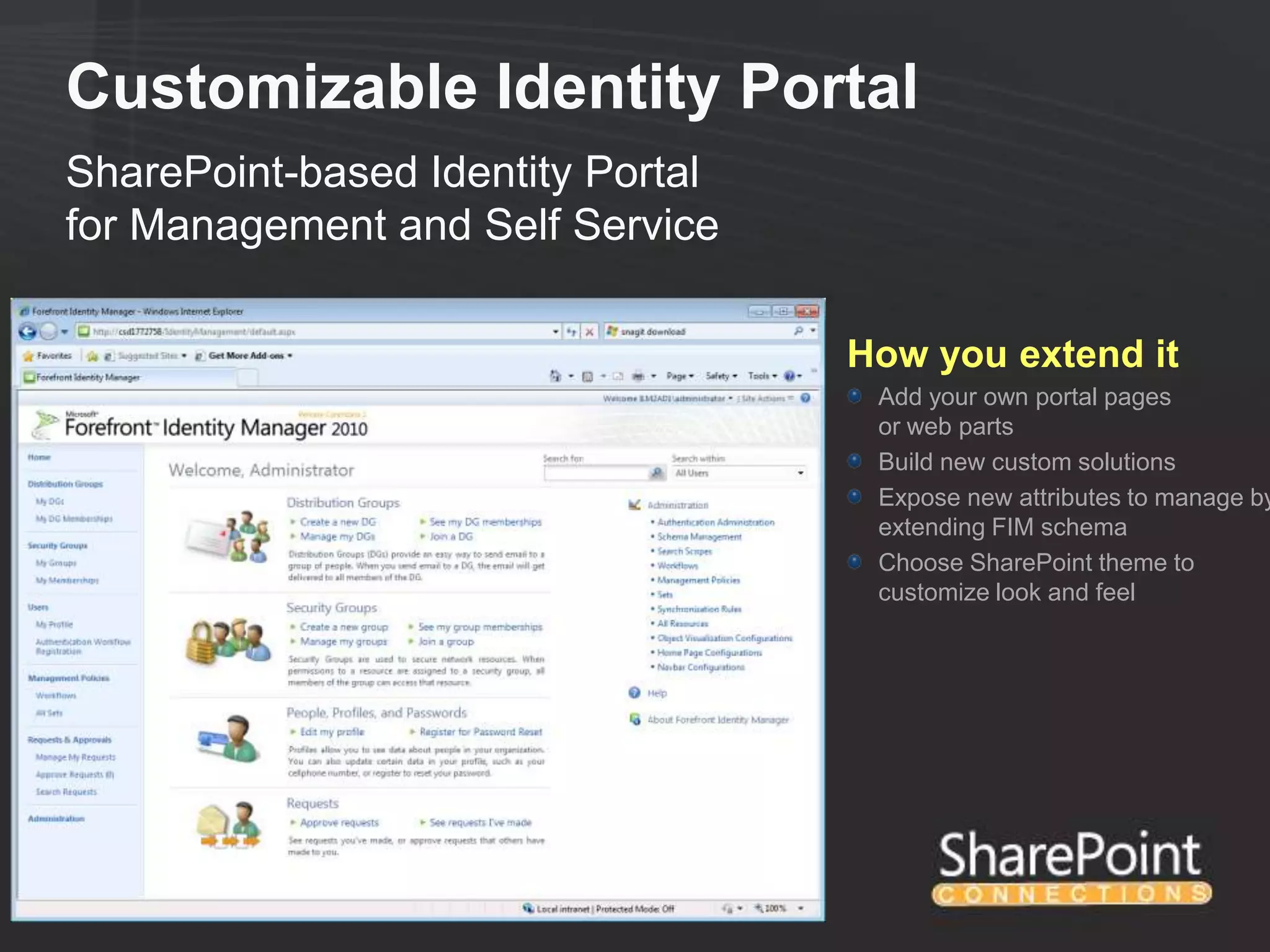
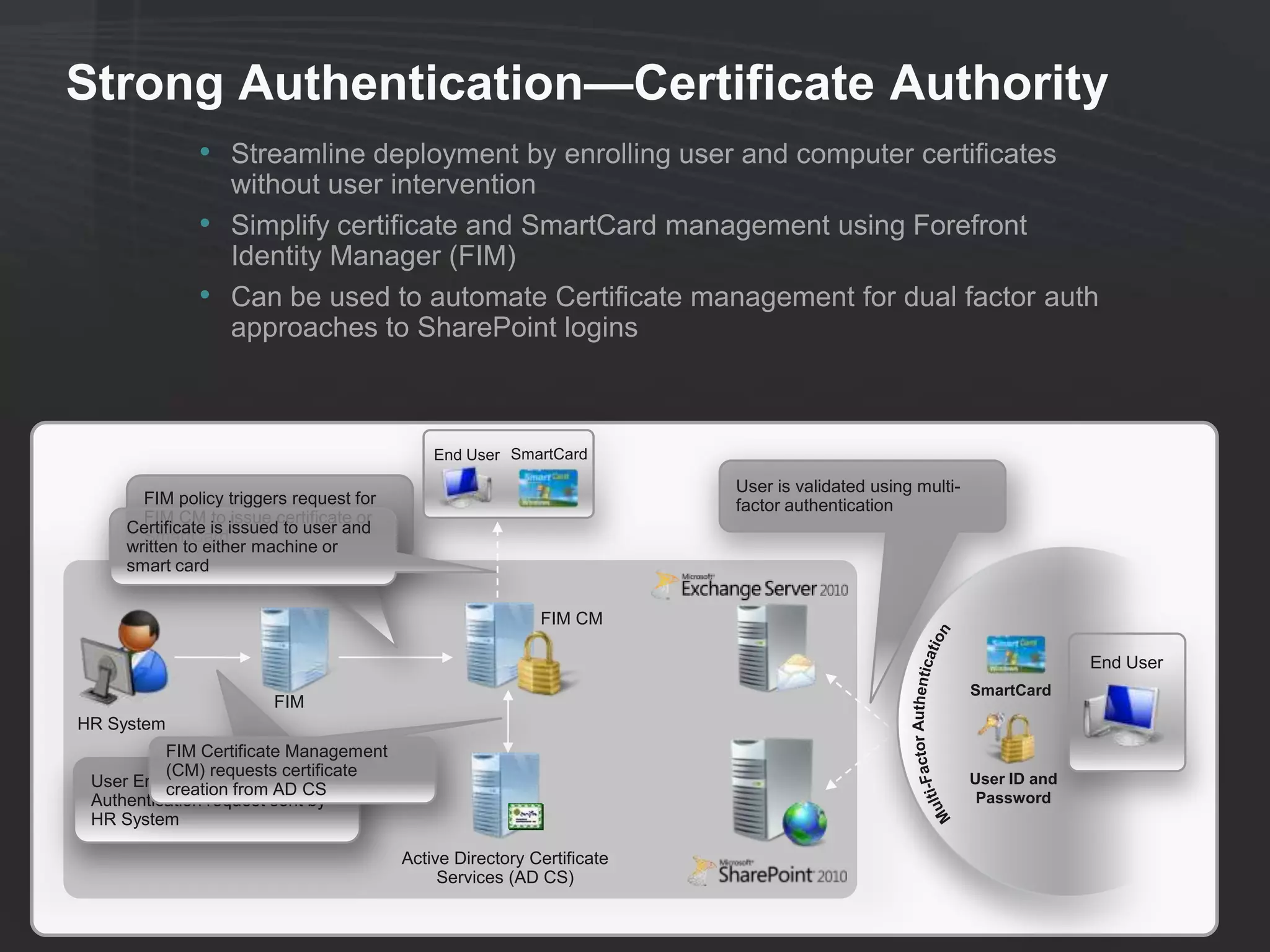
This document discusses collaborating with extranet partners on SharePoint 2010. It begins by covering why organizations implement extranets and the authentication options in SharePoint 2010. It then presents six sample extranet architecture scenarios with varying levels of security isolation between internal and external users. The document also discusses claims-based authentication, the Forefront Unified Access Gateway for external access, and using Forefront Identity Manager for identity management in an extranet.