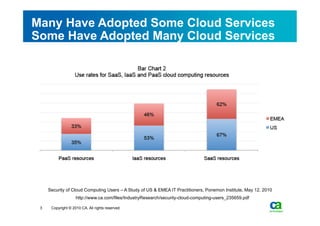
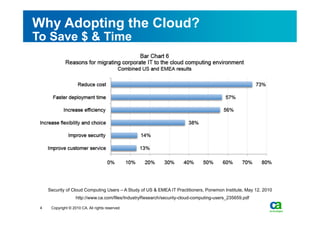
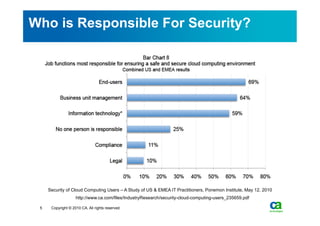
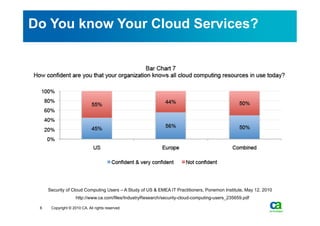
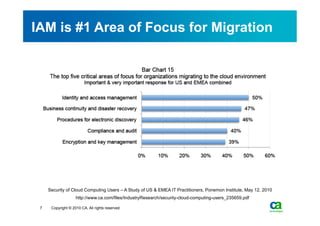
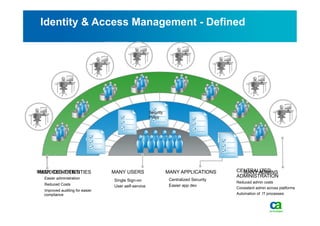
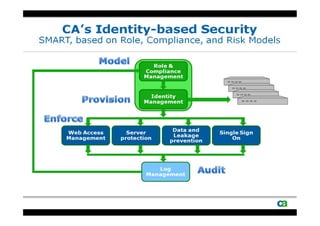
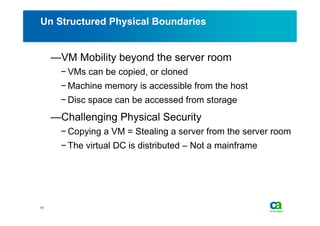
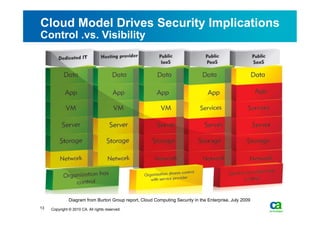
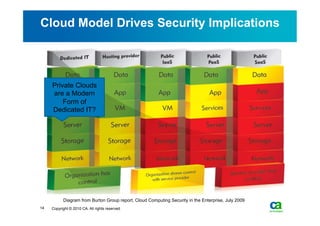
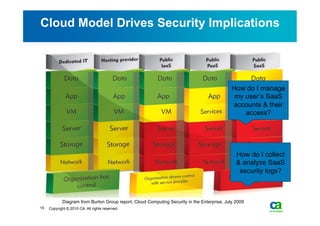
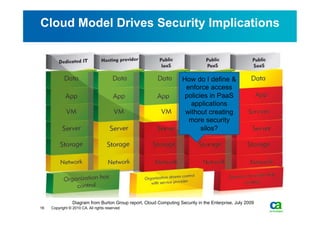
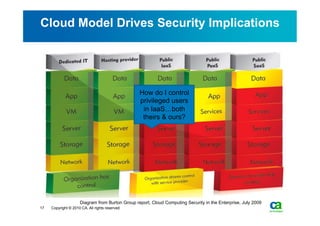
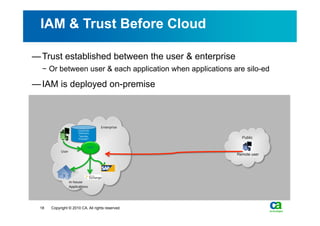
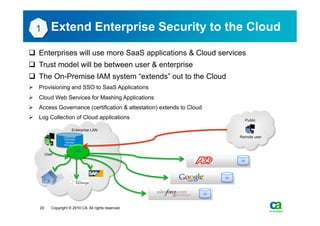
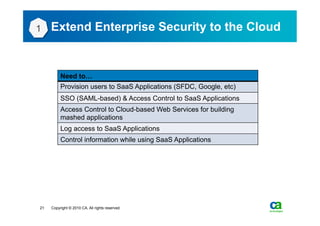
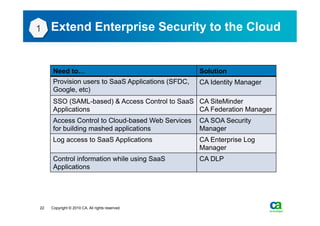
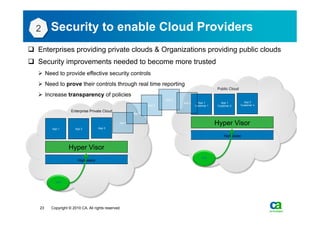
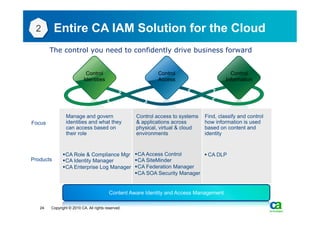
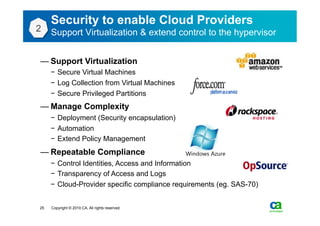
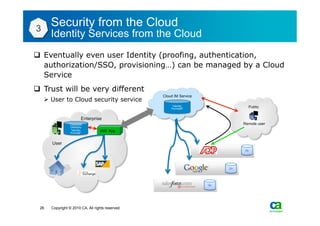
The document discusses security challenges related to cloud computing adoption and identity and access management (IAM). It notes that as organizations increasingly adopt cloud services, the traditional trust model between users and enterprises will need to change. Effective IAM will be crucial to extending enterprise security to the cloud, enabling cloud providers to gain customer trust, and potentially managing user identity from cloud identity services in the future. Key IAM capabilities like access governance, single sign-on, logging and more will need to scale across physical, virtual and cloud environments.