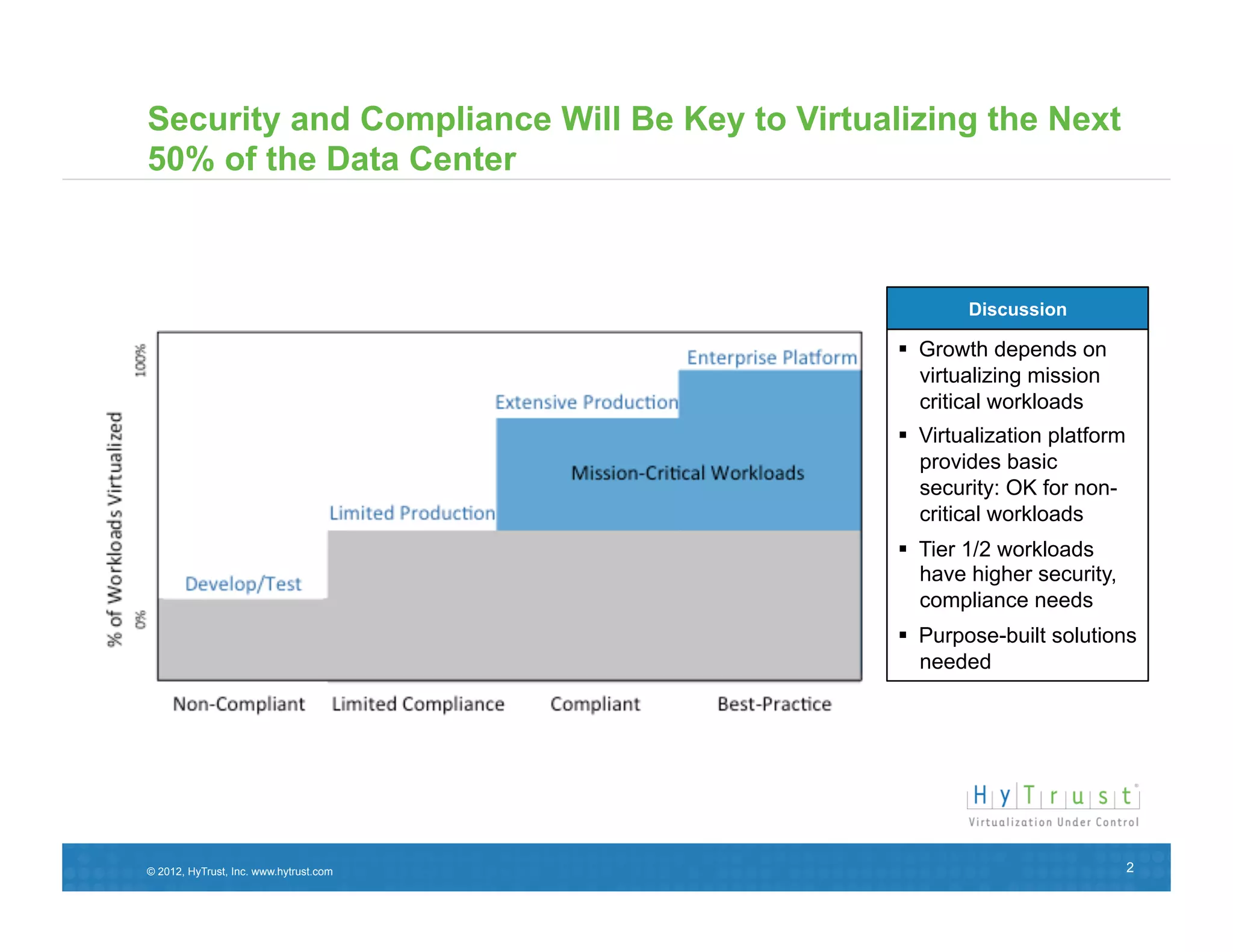
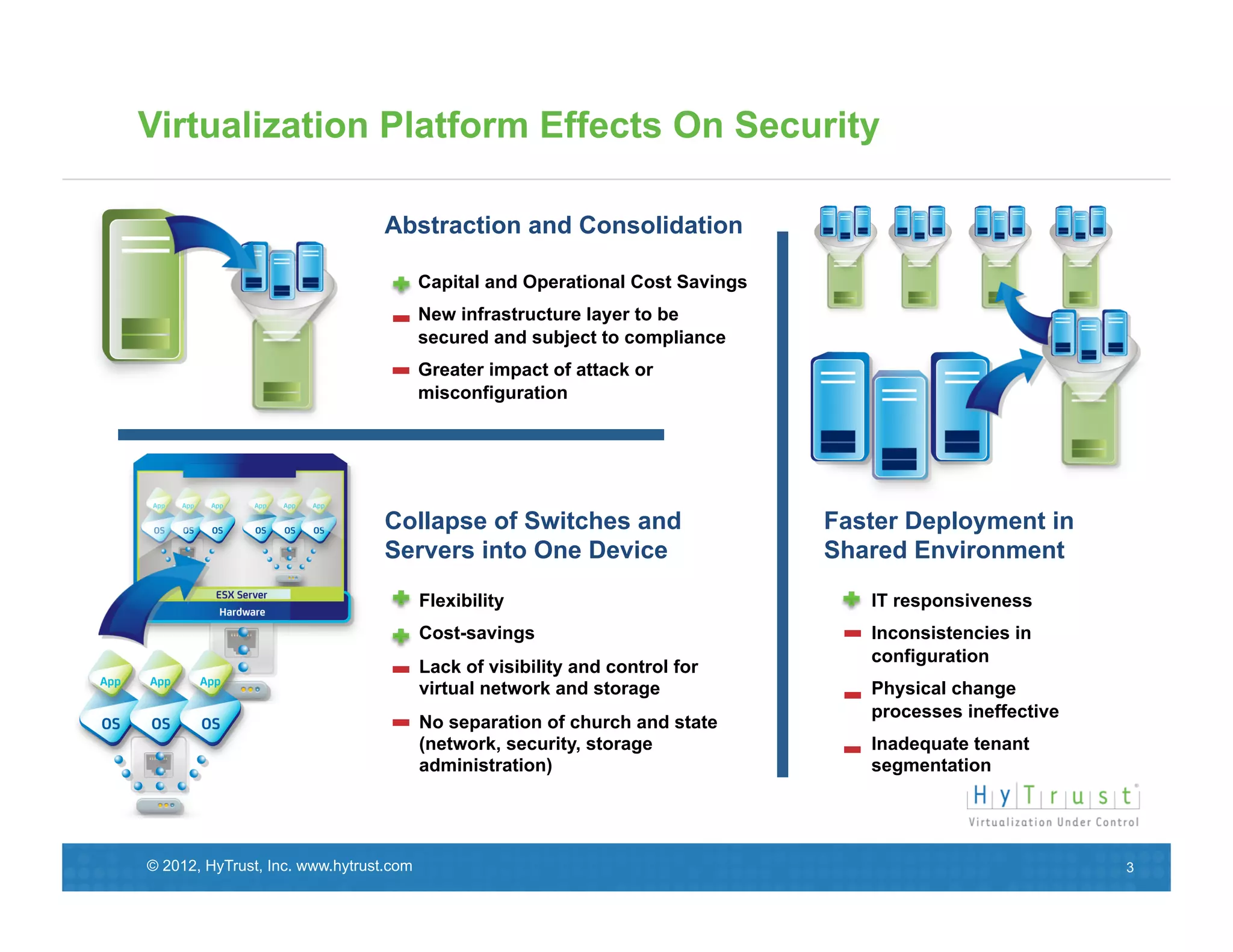
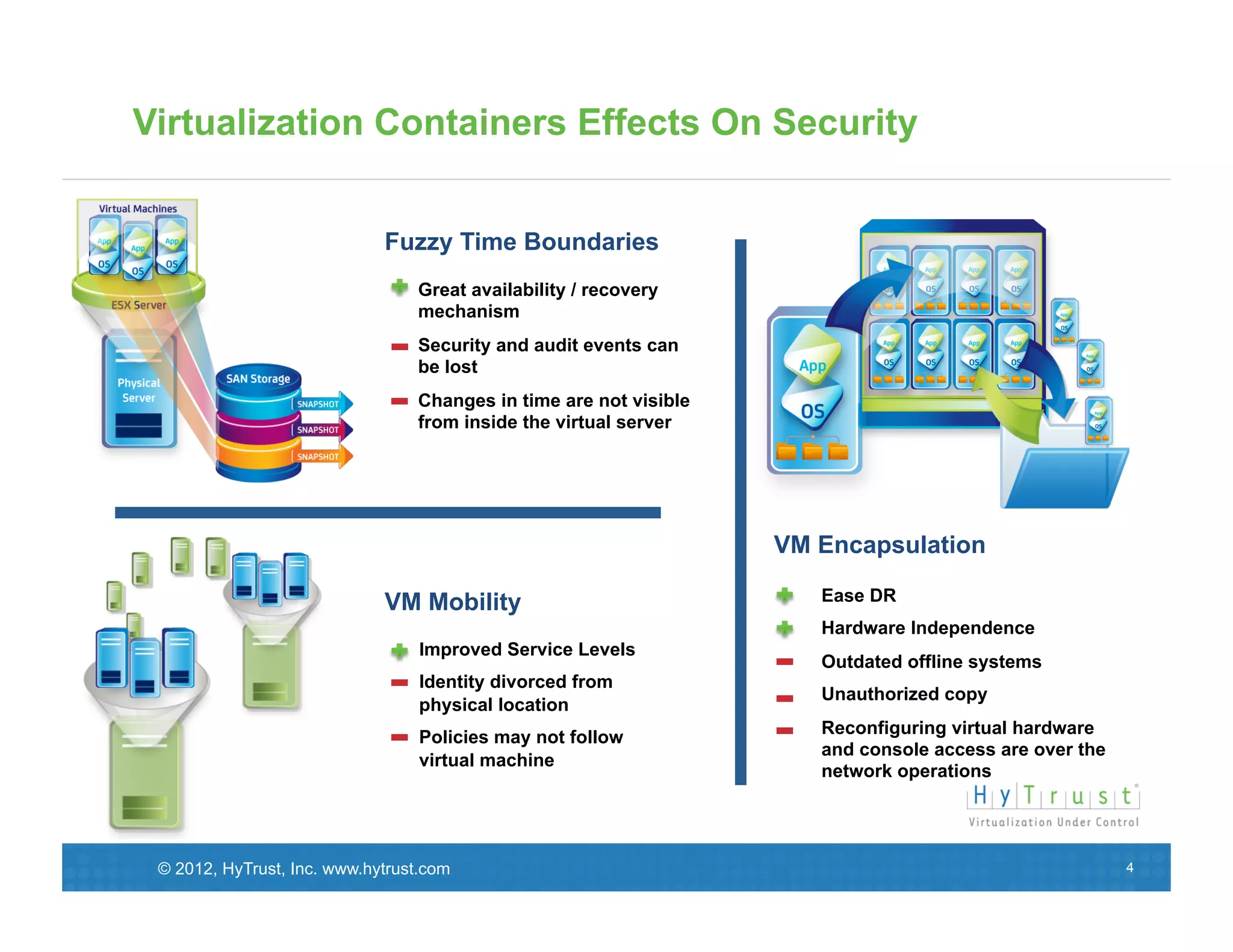
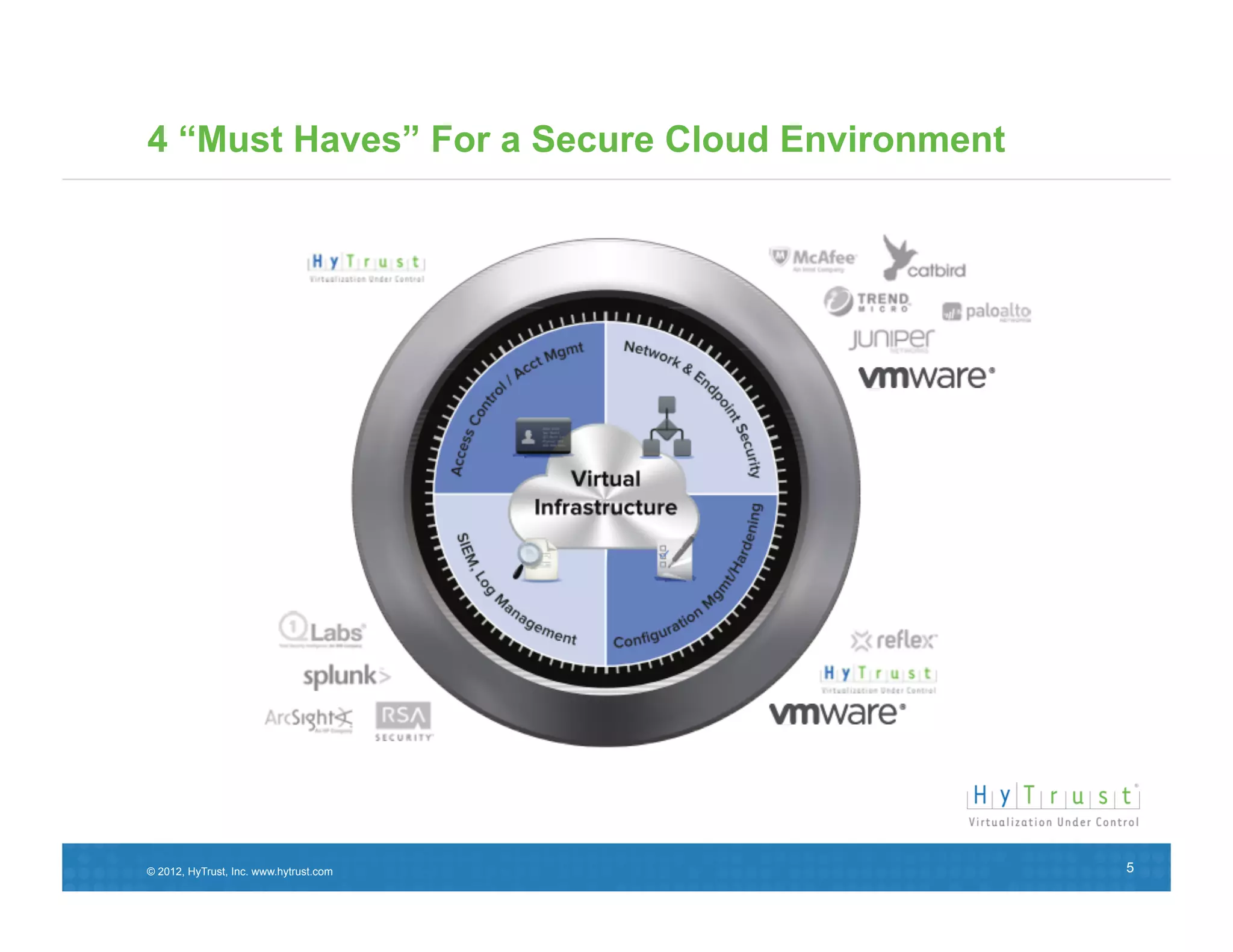
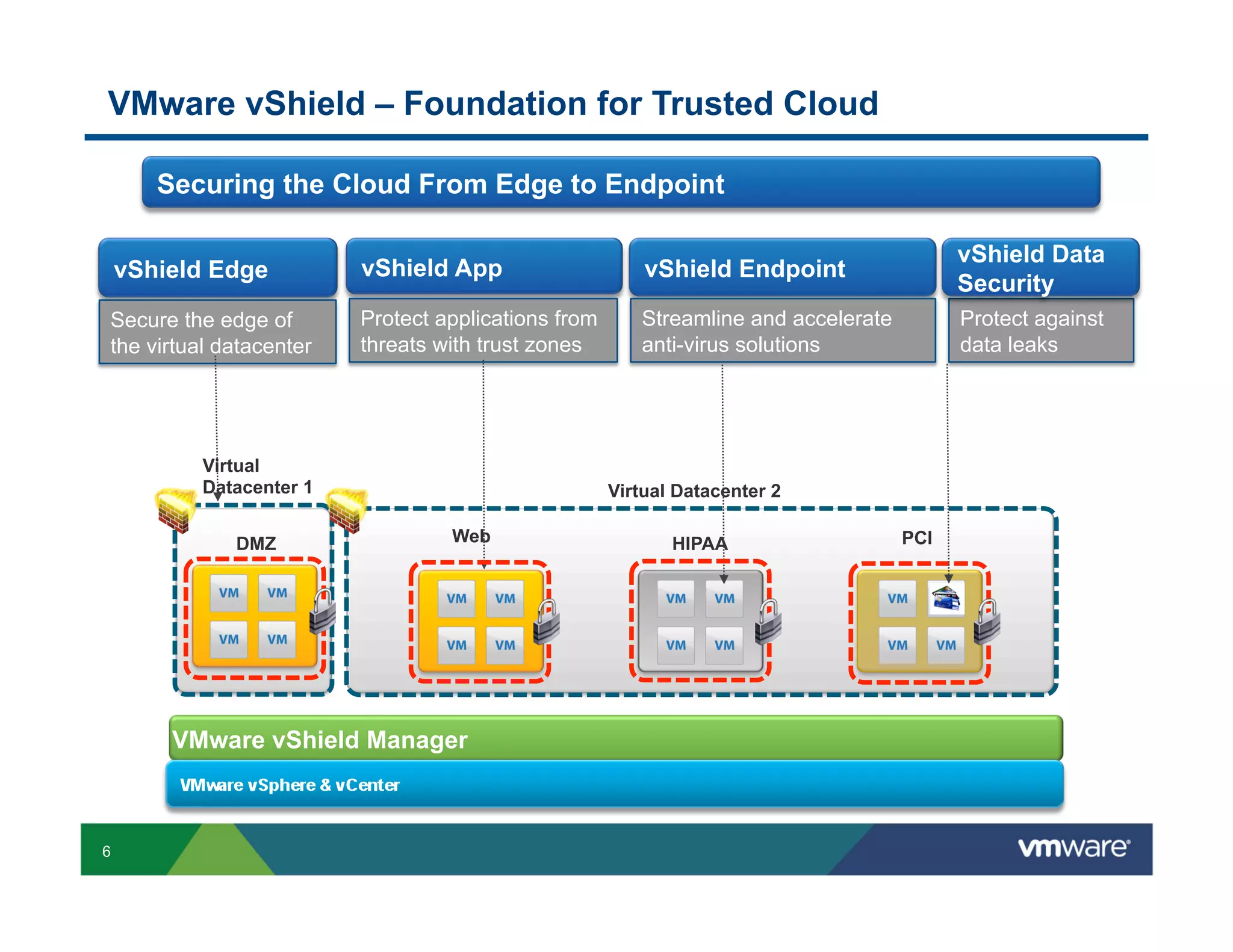
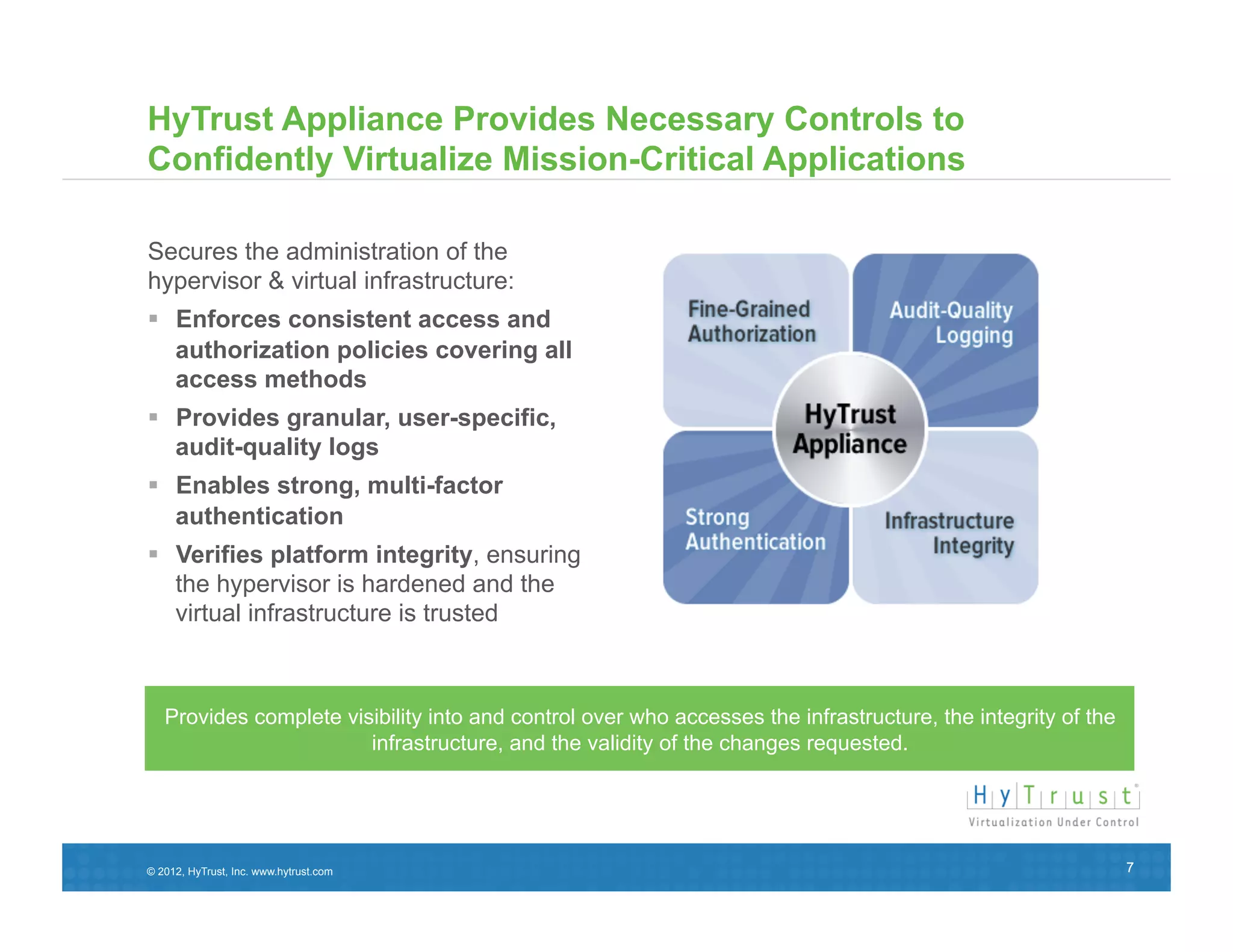
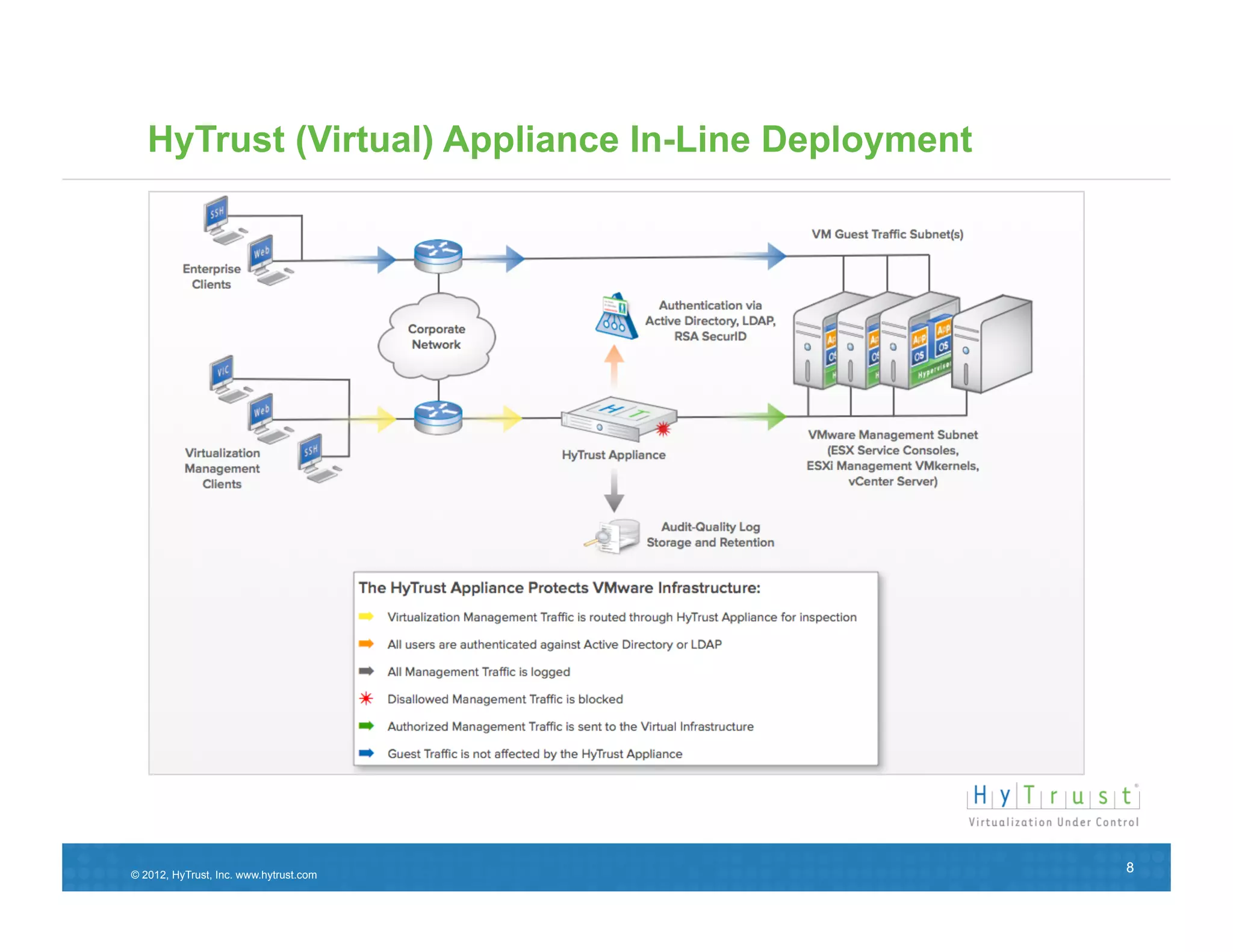
This document discusses the need for secure virtualization solutions as organizations virtualize more mission-critical workloads. It summarizes that while virtualization provides basic security and cost savings, virtual infrastructures require purpose-built security solutions to address issues like lack of visibility, inconsistent configurations, and inadequate tenant segmentation. The document then outlines VMware's virtual security products and how HyTrust provides additional controls like strong authentication, auditing, and integrity monitoring for the virtual infrastructure and hypervisor administration. Major industry partners are also noted as trusting and integrating with HyTrust's virtual security platform.