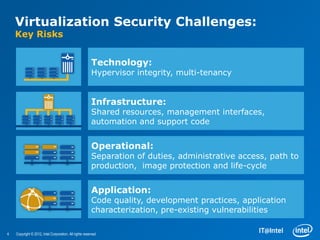
Virtualization and cloud computing provide business benefits like scalability, efficiency and elasticity but also introduce security challenges. Key security risks in virtualized environments include issues with the hypervisor, shared infrastructure vulnerabilities, and operational problems with access controls and application hardening. To balance security and business needs, a "protect to enable" strategy uses granular trust zones like high, medium and low trust environments that apply controls proportionate to asset risk and value. Lessons learned are that a holistic risk view is needed, virtualization security is still maturing, and applications introduced must be hardened.