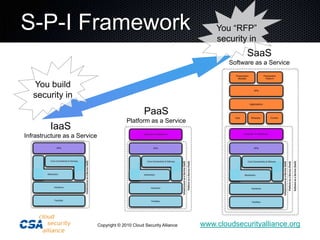
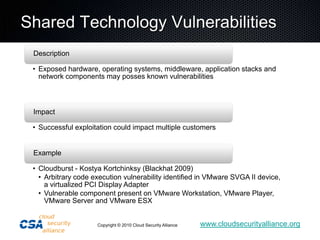
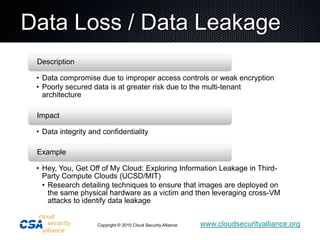
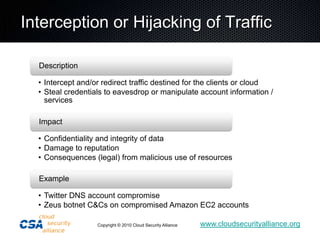
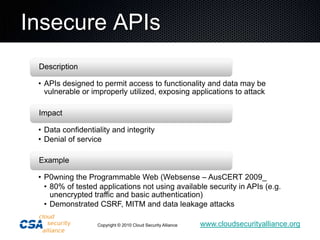
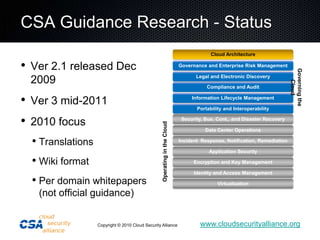
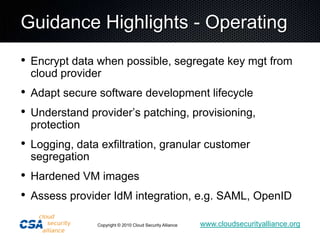
This document summarizes the work of the Cloud Security Alliance (CSA), a global non-profit organization focused on promoting best practices for security in cloud computing. The CSA has over 10,000 individual members from various industries and expertise areas working on cloud security issues. Some of the CSA's key initiatives include developing a Cloud Controls Matrix to help organizations assess security risks in cloud environments, as well as research projects on cloud metrics and the Consensus Assessments Initiative. The document outlines the top threats to cloud computing such as data leakage, malicious insiders, and insecure APIs. It also provides highlights from the CSA's guidance on best practices for governance and operating in the cloud.