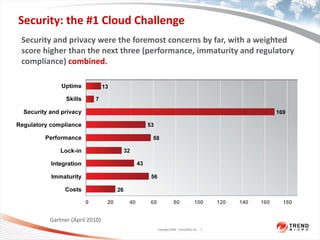
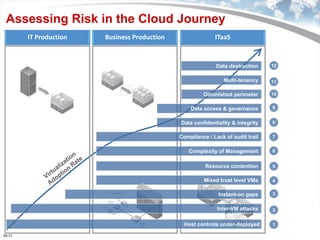
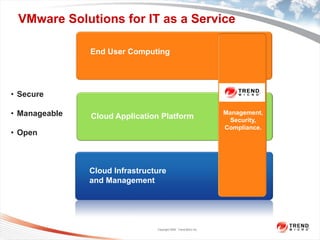
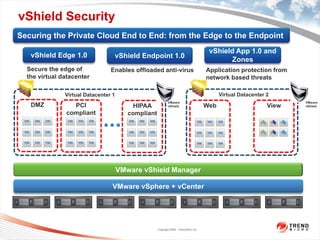
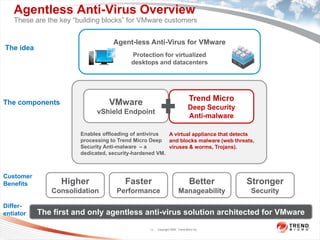
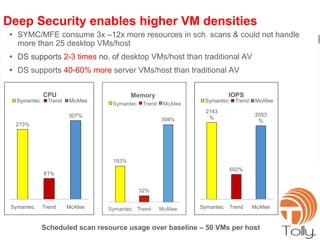
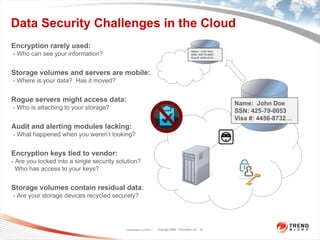
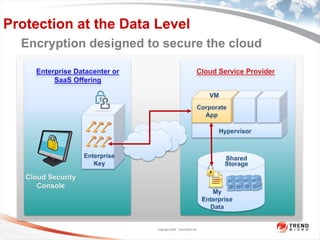
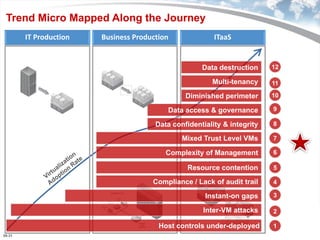
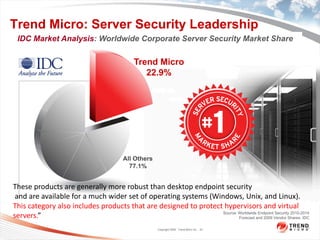
The document discusses the security challenges associated with virtualization and cloud computing, emphasizing the importance of protecting data and virtual environments. It highlights various security risks, such as data access, governance, and compliance, and showcases Trend Micro's solutions, including agentless antivirus technology designed for VMware environments. The need for robust security measures is underscored, as security remains the top concern for organizations transitioning to cloud services.


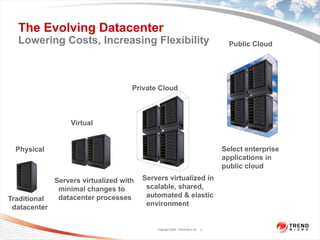


![The Dynamic Datacenter
88% of North American enterprises 2012, 60% of virtualized servers.. less
[no] virtualization security strategy secure than… physical servers….
Forrester Research / Info Week “Addressing the Most Common Security Risks in Data Center
Virtualization Projects” Gartner, 25 January 2010
Physical Virtual Cloud
Technologies and practices for
Number one concern (87.5%)
securing physical servers won’t
about cloud services is security.
provide sufficient protections for VMs. Frank Gens, IDC, Senior VP & Chief Analyst
Neil MacDonald, Gartner, June 2009
Copyright 2009 Trend Micro Inc.](https://image.slidesharecdn.com/deepsecurityvdibeveiligingmaximalebeveiligingenoptimaleperformance-110419040433-phpapp01/85/Deepsecurity-VDI-beveiliging-maximale-beveiliging-en-optimale-performance-6-320.jpg)