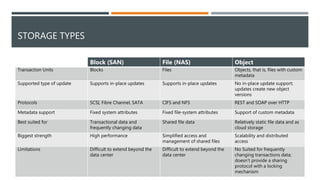
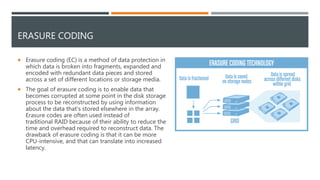
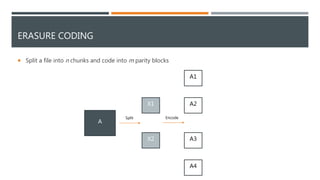
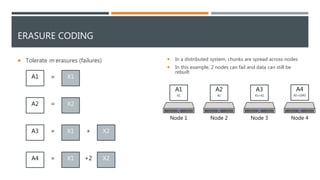
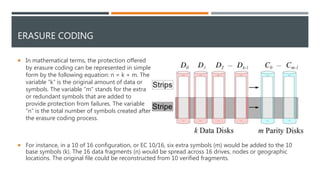
The document provides an overview of different storage types, including block, file, and object storage, detailing their definitions, characteristics, and applications. It emphasizes object storage's advantages like scalability and simplified management while also noting its limitations, such as lack of random access. Additionally, it discusses data protection methods, including RAID and erasure coding, and outlines use cases suited for object storage.