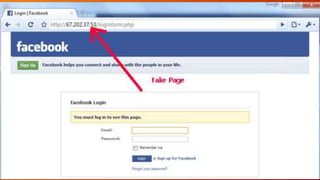
The document explores social engineering, defining it as manipulation used to extract personal and valuable information for malicious purposes like hacking and identity theft. It discusses various techniques such as phishing and pretexting, highlighting the importance of recognizing social engineering threats and protecting oneself through strategies like password management and two-factor authentication. It also contrasts the negative aspects with potential positive applications, emphasizing the need to understand the target audience and their vulnerabilities.