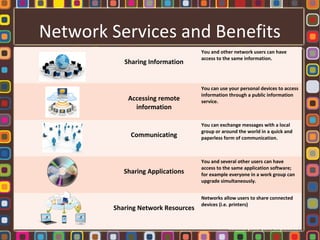
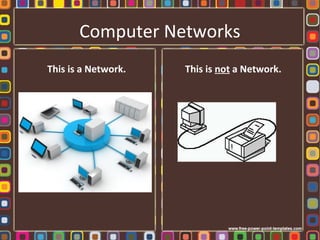
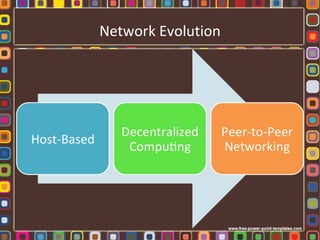
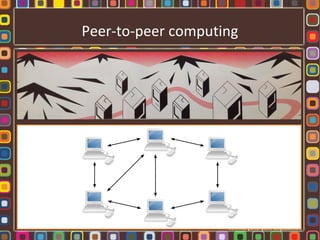
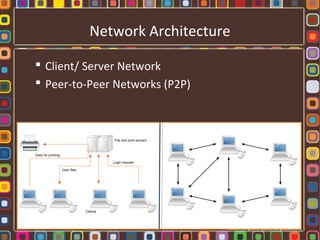
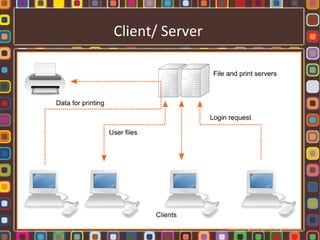
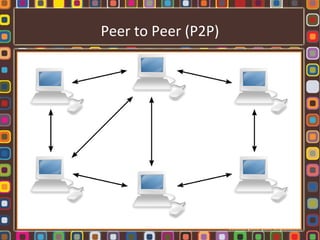
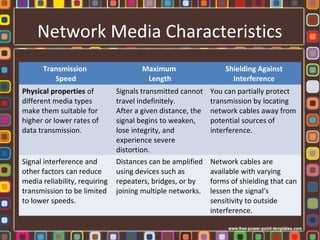
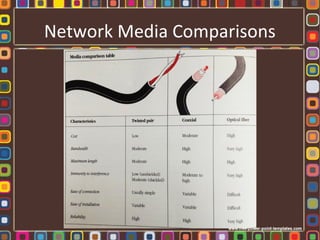
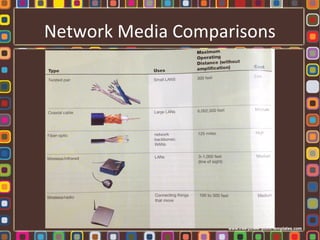
The document discusses the fundamentals of computer networks, including their components, types, and benefits such as information sharing and communication. It explains different network architectures, the roles of clients and servers, and key devices like hubs, switches, and routers. Additionally, it covers the evolution of networking, various connection types, and the importance of protocols and media in transmitting data.