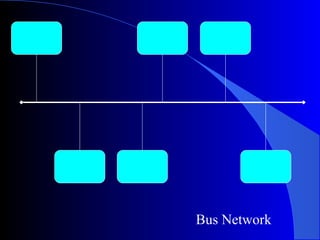
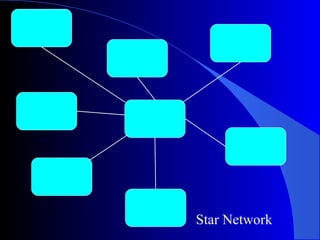
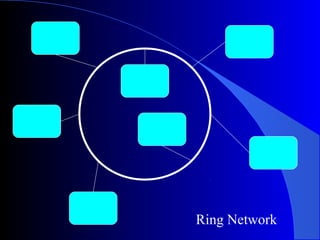
This document discusses various concepts related to transmitting and receiving data over networks. It covers topics such as transmission methods (parallel vs serial), transmission direction (simplex, half-duplex, full-duplex), synchronization techniques, protocols, network topologies, access methods like Ethernet and token ring, transmission media, wireless transmission, and network software. The roles of devices like routers, switches, bridges and servers are also outlined.





![• Asynchronous transmission is sent at
varying rates and the flow is regulated
through the use of start and stop bits.
• One of the protocols agreed upon during
handshaking is how many start and stop bits
will be used.
• [Diagram 3.10, p.88]
• Protocols are a set of rules that govern the
transfer of data between two computers.](https://image.slidesharecdn.com/12ipt0303-transmittingandreceiving-130512204317-phpapp02/85/12-ipt-0303-transmitting-and-receiving-6-320.jpg)
![• They define:
• how a link is established
• how data is transmitted
• how errors are detected and corrected
• Numerous protocols have been developed
for different technologies.
• [Table 3.1, p.89 – Do the following: IPX,
X.25, ATM, Kermit, TCP/IP, HTTP, FTP,
POP, MIME]](https://image.slidesharecdn.com/12ipt0303-transmittingandreceiving-130512204317-phpapp02/85/12-ipt-0303-transmitting-and-receiving-7-320.jpg)