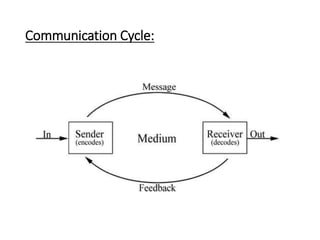
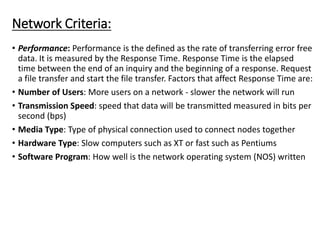
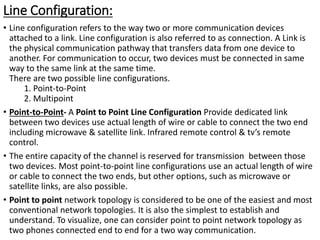
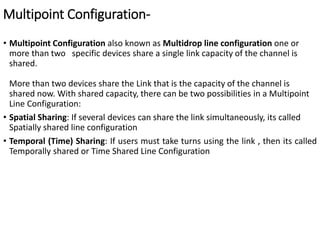
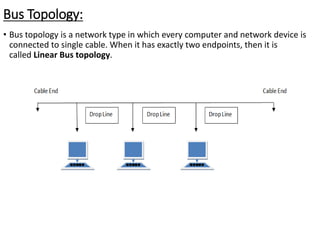
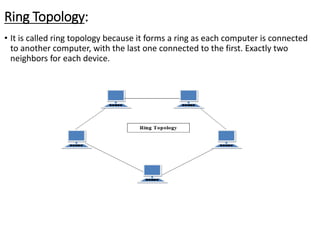
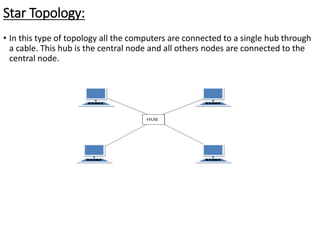
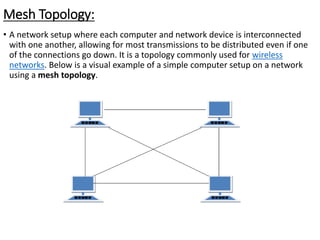
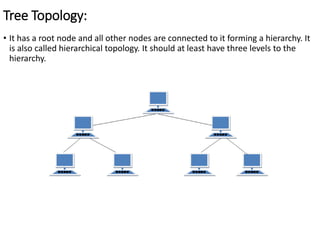
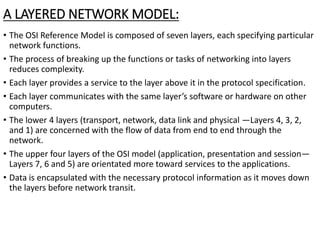
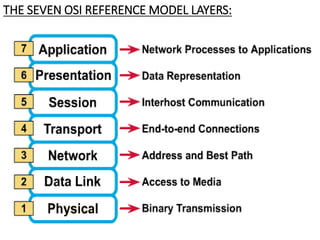
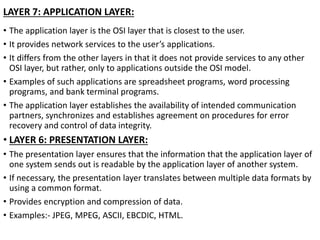
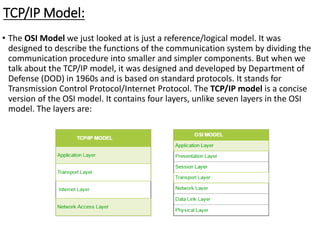
This document provides an overview of computer communication networks. It discusses what a computer network is, the advantages of computer networks like sharing resources and files, and the communication cycle involved. It also covers some key aspects of computer networks like performance, reliability, security, and the goals of sharing resources, high reliability, and cost savings. The document summarizes different types of networks including local area networks (LANs), metropolitan area networks (MANs), and wide area networks (WANs). It also discusses transmission modes in computer networks like simplex, half duplex, and full duplex modes.