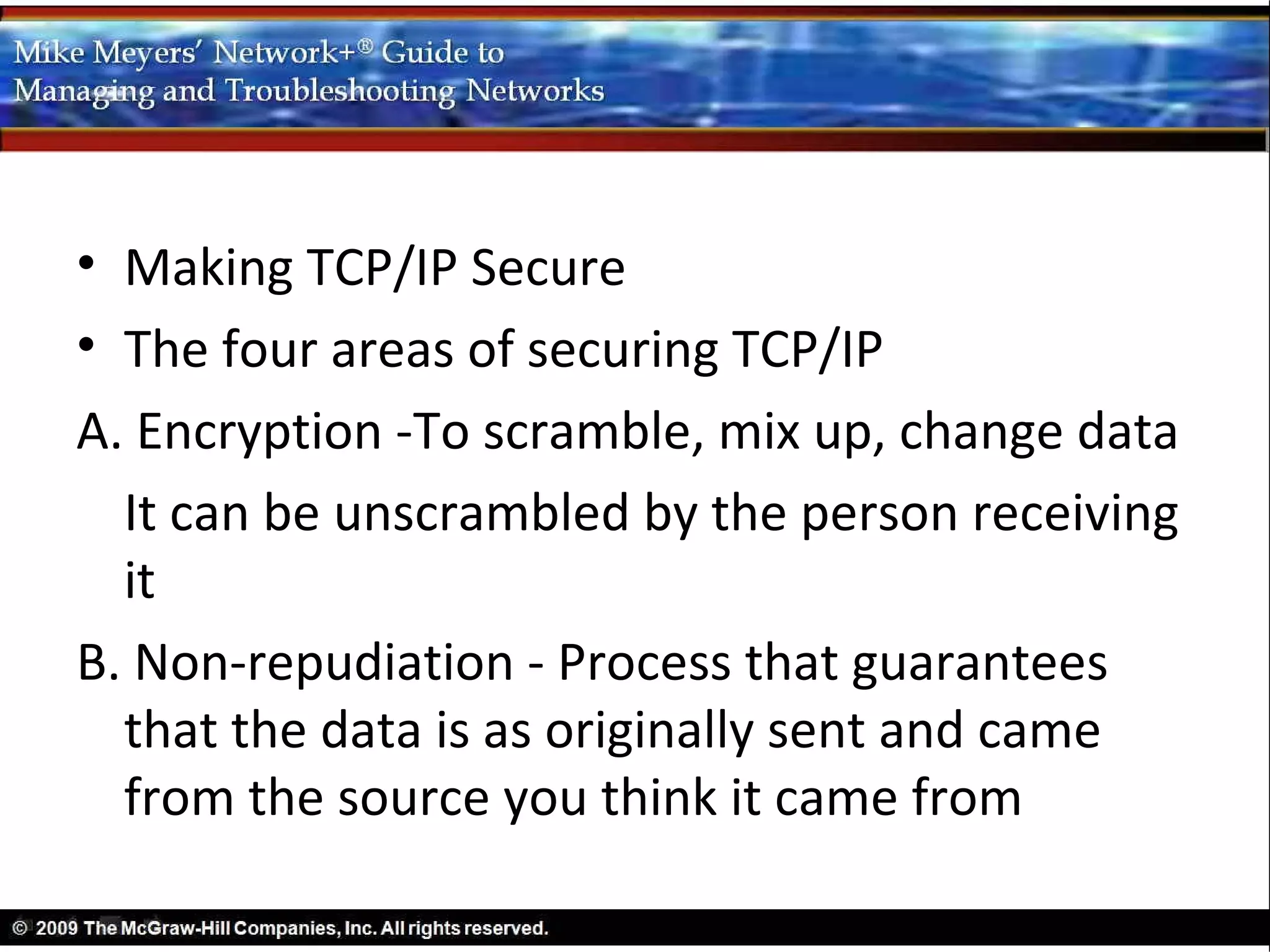
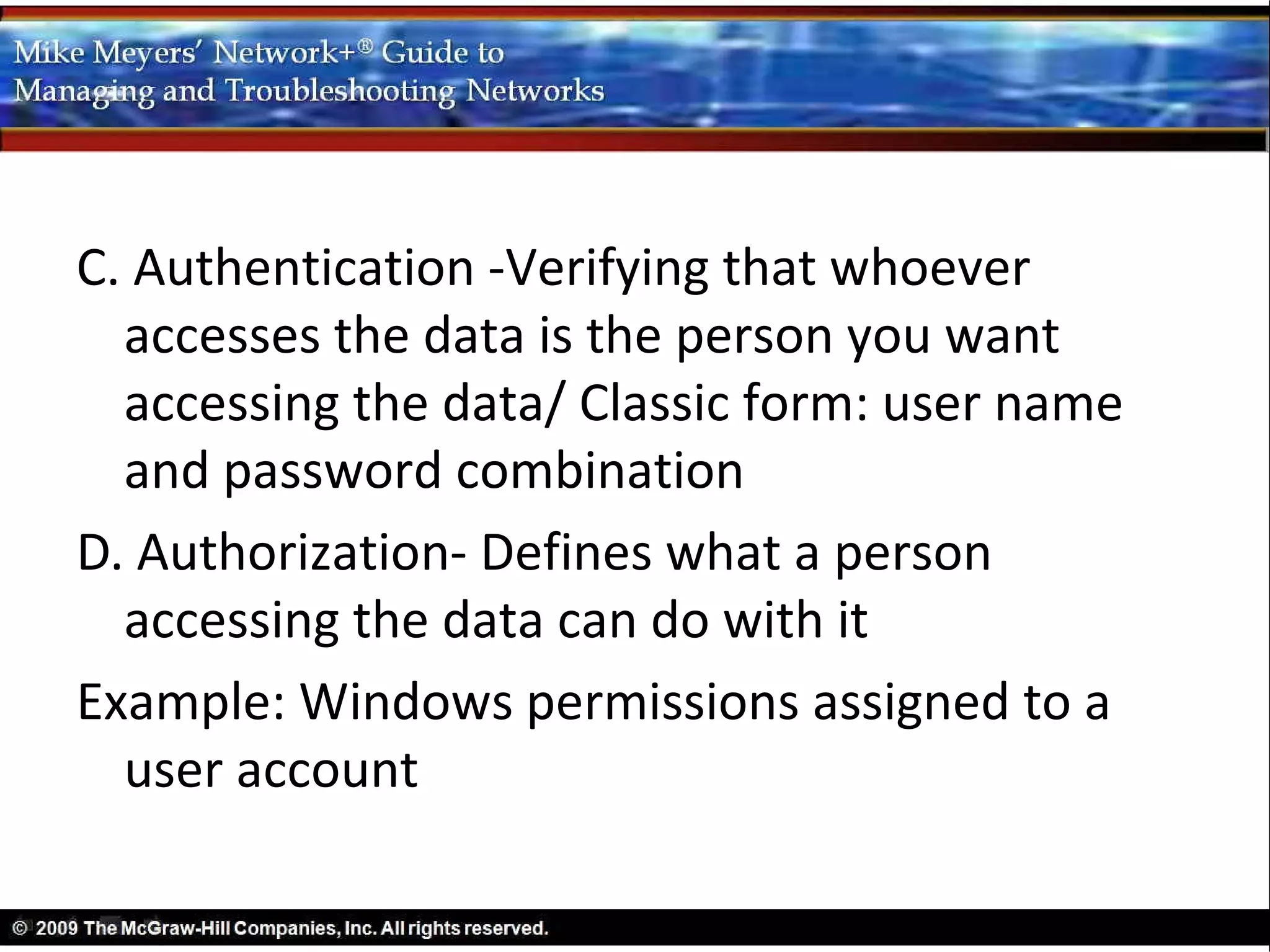
This document discusses securing TCP/IP networks. It covers four main areas of TCP/IP security: encryption, non-repudiation, authentication, and authorization. Encryption involves scrambling data so it can only be unscrambled by the intended recipient. Common encryption standards discussed include asymmetric key algorithms which allow secure key exchange. Secure TCP/IP applications then use these standards and tools to protect data in transit, such as HTTPS which uses SSL/TLS encryption for web traffic security.



![• Secure TCP/IP Applications
A. The applications that use the above standards
and tools
B. HTTPS [Introduced in Chapter 9]
- HTTPS documents page addresses begin with
https://
-Most browsers also show a lock icon
somewhere
- HTTPS uses SSL/TLS for](https://image.slidesharecdn.com/net2eppt11-120801064945-phpapp02/75/Networking-Chapter-11-10-2048.jpg)