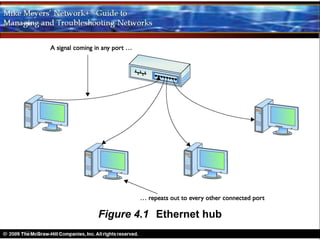
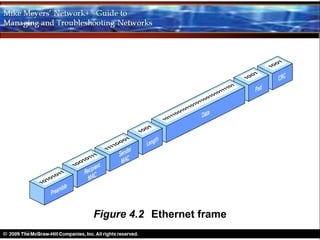
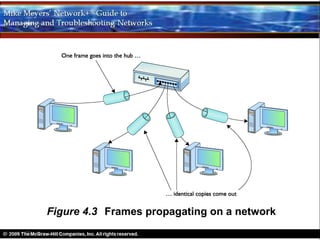
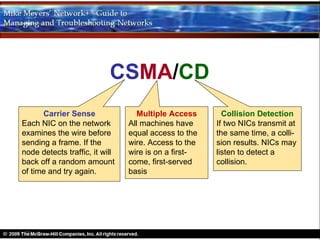
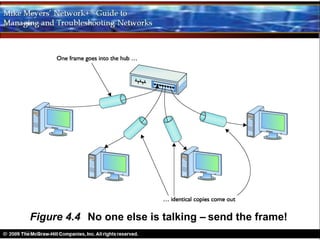
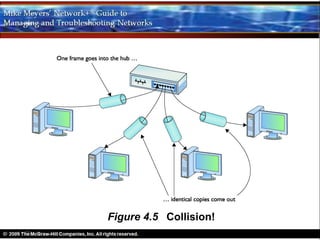
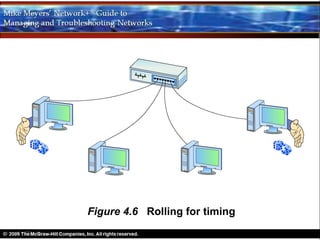
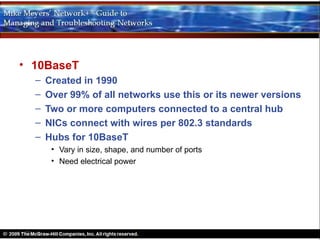
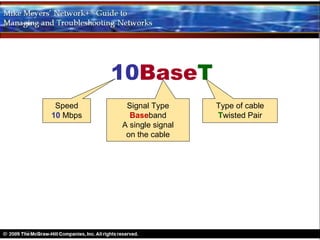
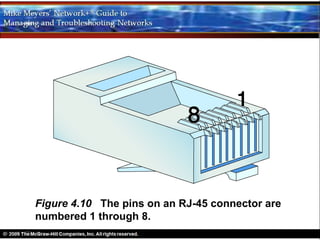
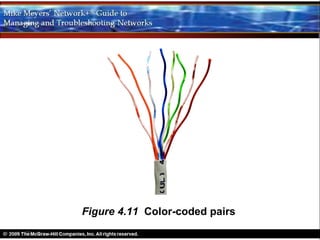
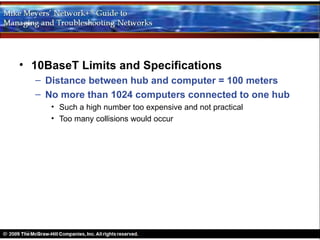
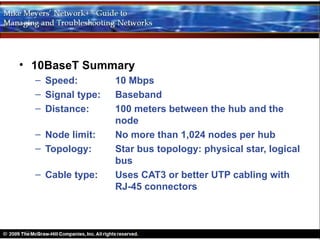
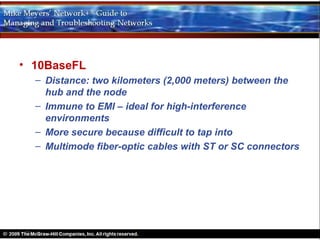
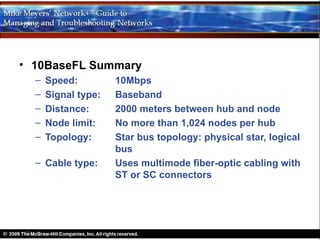
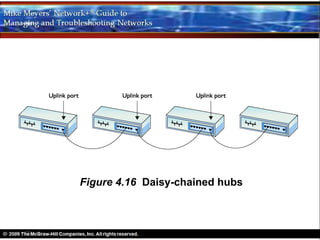
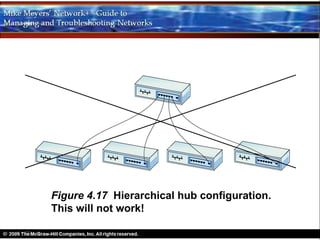
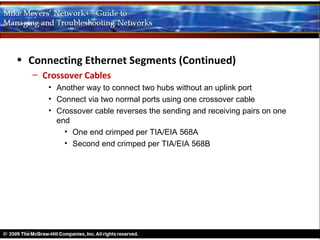
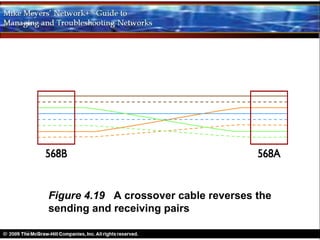
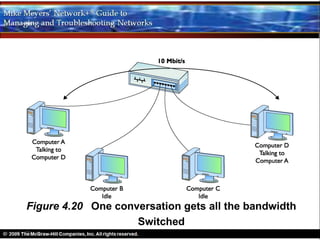
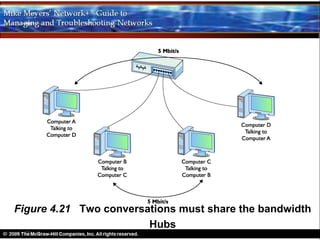
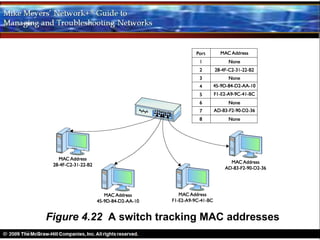
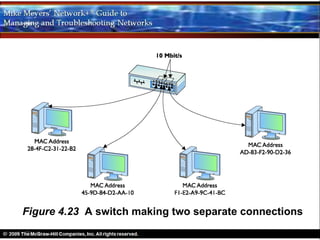
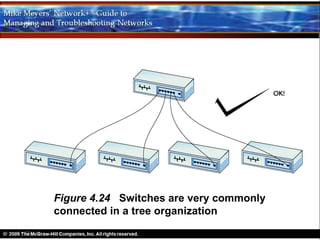
Ethernet is a standard for network technologies that share a bus topology and frame format. Early Ethernet implementations transferred data at speeds up to 10Mbps using coaxial cable or twisted pair cabling. 10BaseT networks used twisted pair cabling and hubs to connect computers in a star topology up to 100 meters apart. Switches were later introduced to avoid bandwidth limitations of hubs by creating point-to-point connections between communicating devices using MAC addresses. This increased overall network speed and allowed larger, more complex network topologies.