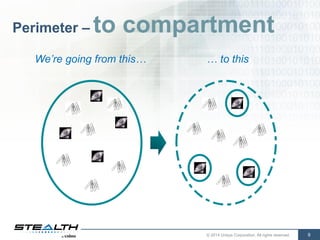
The document discusses the evolving cybersecurity landscape, emphasizing the challenges presented by the consumerization of IT and the sophisticated tactics of adversaries, such as advanced persistent threats. It critiques traditional security measures as inadequate and proposes the use of compartmentalized security models and modern encryption technologies to protect critical assets. Recommendations include focusing on access control, hiding sensitive information, and managing security through community-based interest systems.