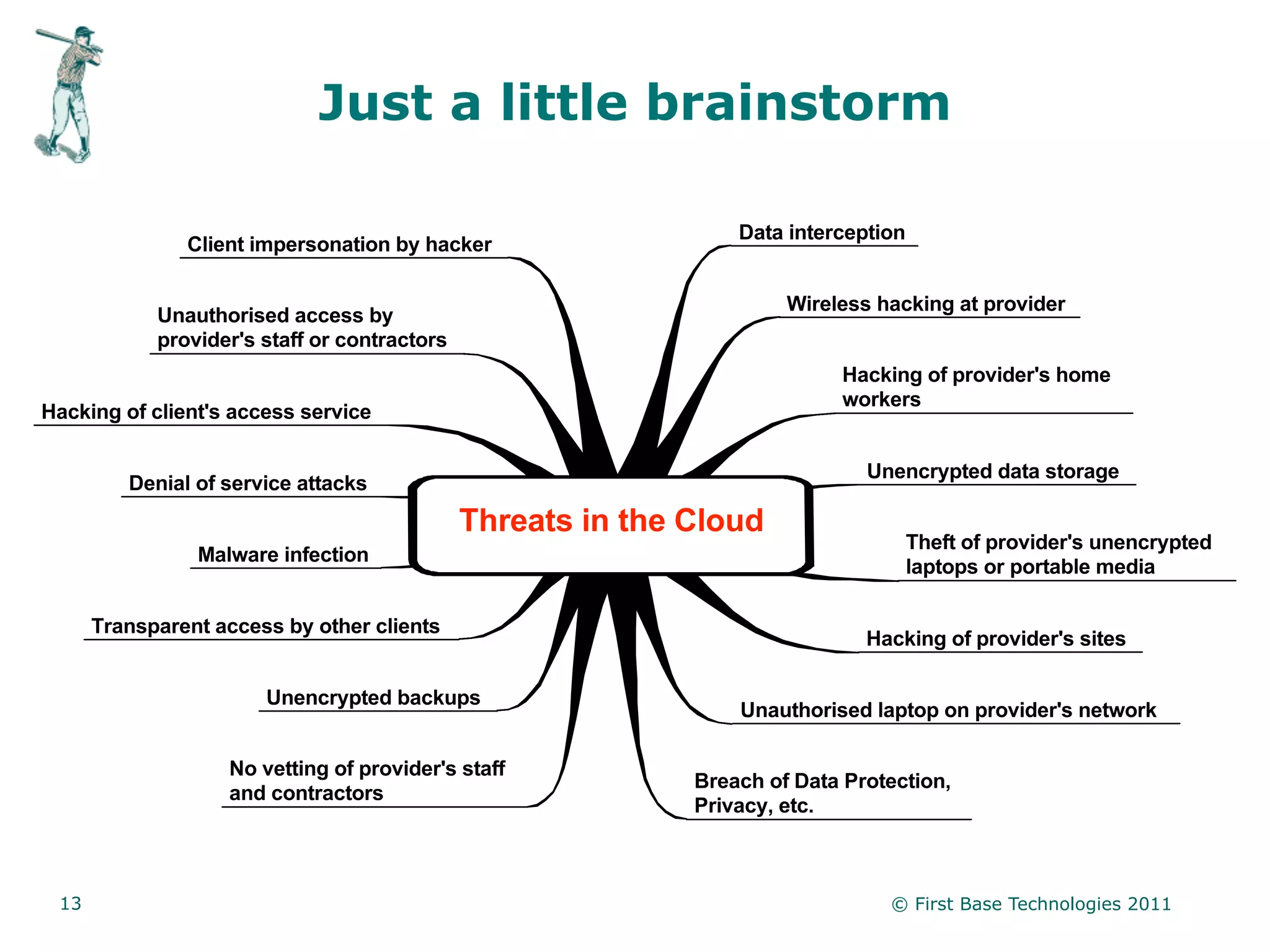
The document presents an overview of cloud security from the perspective of Peter Wood, an expert in ethical hacking and CEO of First Base Technologies. It defines cloud computing, explores its security concerns, outlines various service and deployment models, and emphasizes the importance of risk assessment and understanding data flows before migrating to the cloud. The presentation concludes with guidance on evaluating cloud services and highlights critical security considerations.