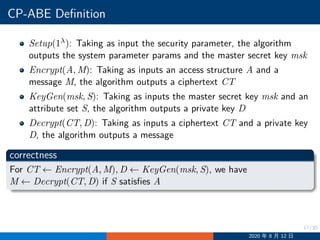
The document discusses attribute-based encryption (ABE) schemes, including Key-Policy ABE (KP-ABE) and Ciphertext-Policy ABE (CP-ABE). It defines the components of KP-ABE and CP-ABE, including setup, encryption, key generation, and decryption algorithms. It also describes the security models and proves the selective security of the GPSW KP-ABE scheme and correctness of the Waters CP-ABE scheme under the decisional bilinear Diffie-Hellman assumption. The document outlines the KP-ABE and CP-ABE constructions and security proofs in detail.


![6/30
KP-ABE Security Model
Guess: The adversary A outputs a bit b, and wins the game if b = b.
The advantage of the adversary A in winning the game is defined as
Adv(A) = Pr[b = b]−1/2
We say that an ABE scheme is CCA secure if for all PPT adversary
A, Adv(A) is negligible
2020 年 8 月 12 日](https://image.slidesharecdn.com/cpdaabe-200812110719/85/NCCU-CPDA-Lecture-12-Attribute-Based-Encryption-6-320.jpg)
![7/30
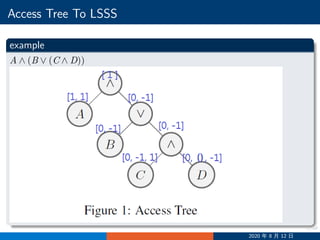
Access Tree To LSSS
1 label the root with [1] and label each node from the root to leaves
2 If an internal node is “∧”labelled with a vector v, then we label its left
son with [v, 1], and the right son with [0, ..., 0, −1]. The sum of left
and right should be [v, 0]
3 If an internal node is “∨”then we label the two sons with the same
vector as their parent
4 pad 0 to the shorter vectors to make all the vectors the same length
2020 年 8 月 12 日](https://image.slidesharecdn.com/cpdaabe-200812110719/85/NCCU-CPDA-Lecture-12-Attribute-Based-Encryption-7-320.jpg)
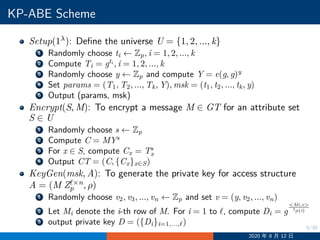
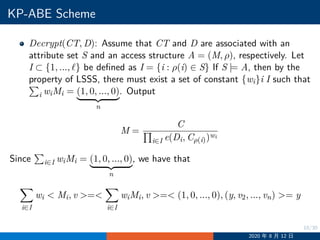
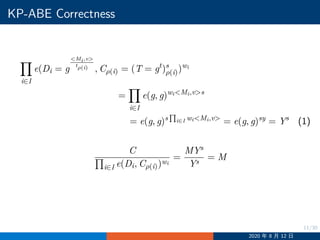
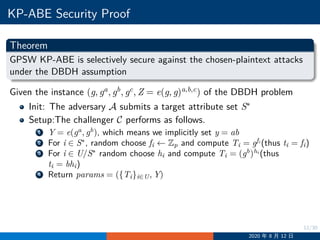
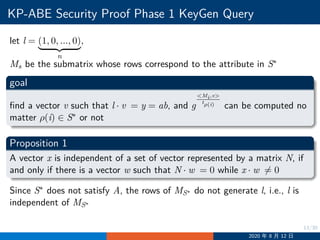
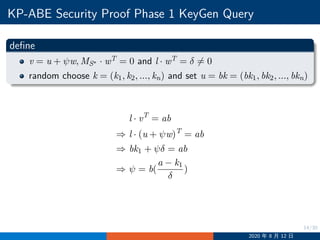
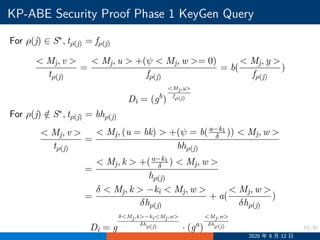

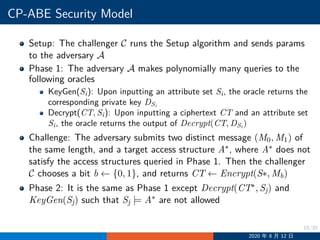
![19/30
CP-ABE Security Model
Guess: The adversary A outputs a bit b, and wins the game if b = b.
The advantage of the adversary A in winning the game is defined as
Adv(A) = Pr[b = b]−1/2
We say that an ABE scheme is CCA secure if for all PPT adversary
A, Adv(A) is negligible
2020 年 8 月 12 日](https://image.slidesharecdn.com/cpdaabe-200812110719/85/NCCU-CPDA-Lecture-12-Attribute-Based-Encryption-19-320.jpg)
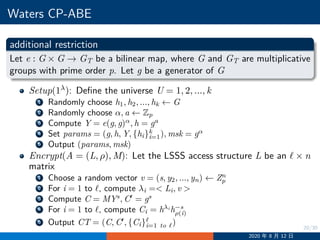
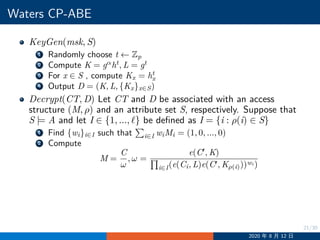
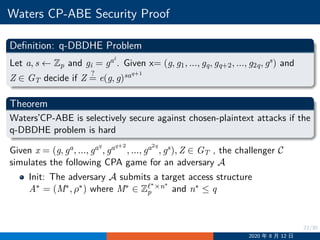
![24/30
Waters CP-ABE Security Proof
Setup:
1 Randomly choose α′
and set Y = e(ga
, gaq
)e(g, g)α′
, which means
α = αq+1
+ α′
2 Set h = ga
3 For x ∈ U choose randomly zx ←− Zp
4 For x /∈ U, if there is an i such that ρ∗
(i) = x, set
hx = gzx
gaMi[1]
ga2
Mi[2]
, ..., gan∗
Mi[n∗
]
where Mi[j] denotes the j-th entry of Mi; otherwise set hx = gzx
5 Return params = (g, h, Y, {hx}x∈U)
2020 年 8 月 12 日](https://image.slidesharecdn.com/cpdaabe-200812110719/85/NCCU-CPDA-Lecture-12-Attribute-Based-Encryption-24-320.jpg)
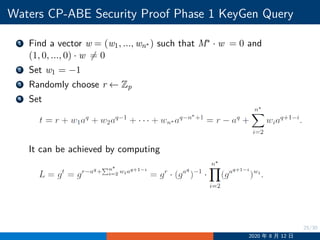
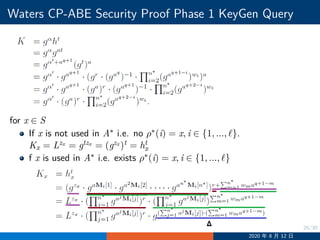
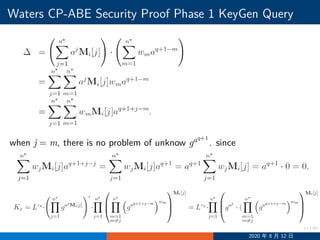
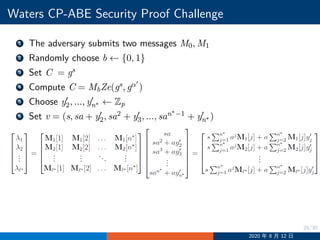
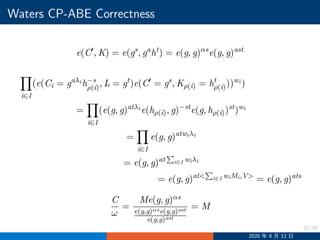
![29/30
Waters CP-ABE Security Proof Challenge
Ci = gaλi
h−s
ρ∗(i), hρ∗(i) = gzρ∗(i)+
∑n∗
j=1 ajMi[j]
2020 年 8 月 12 日](https://image.slidesharecdn.com/cpdaabe-200812110719/85/NCCU-CPDA-Lecture-12-Attribute-Based-Encryption-29-320.jpg)
