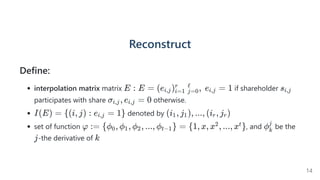
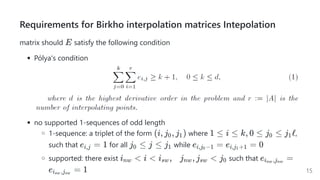
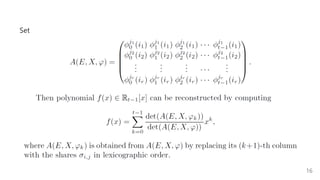
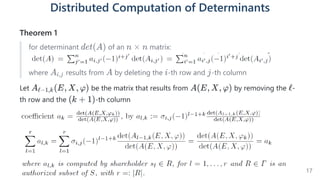
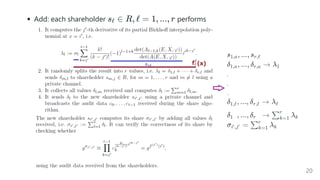
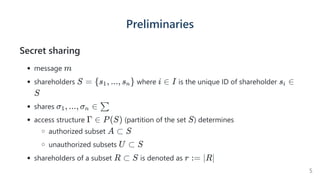
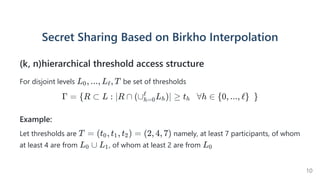
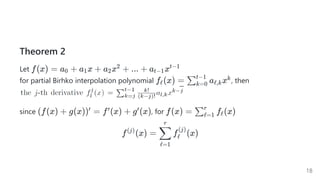The document introduces a dynamic and verifiable hierarchical secret sharing scheme designed to allow flexible management of shareholders and access conditions for secure vault operations. It outlines the mechanisms for adding, removing shareholders, and modifying access structures while ensuring perfect security and completeness. Key components include threshold signatures and Birkhoff interpolation for reconstructing the secret from shares held by authorized shareholders.









![Birkhointerpolation
problem of fnding a polynomial
satisfying the equalities , where is the ring of the polynomials
with degree at most
consider:
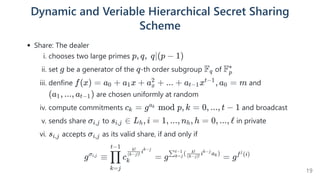
union of all shareholders from all levels constitutes the set of shareholders
S = {s , ..., s }, S =
1 n ∪ L
h=0
ℓ
h
threshold
f(x) = a +
0 a x +
1 a x +
2
2 ... + a x ∈
t−1
t−1 R [x]
t−1
f (i) =
j σi,j R [x]
t−1
t − 1
T = {t }
k k=0
m
12](https://image.slidesharecdn.com/dynamicandverifiablehierarchicalsecretsharing-210814073305/85/Dynamic-and-verifiable-hierarchical-secret-sharing-12-320.jpg)