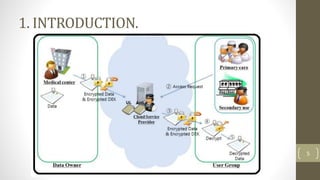
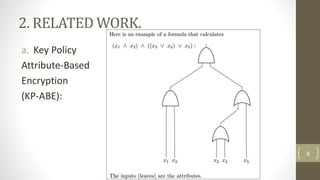
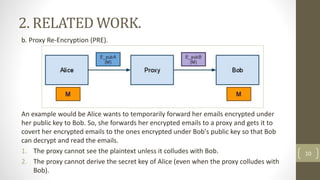
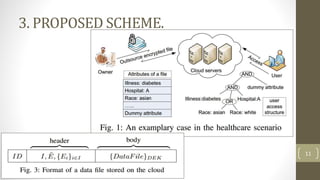
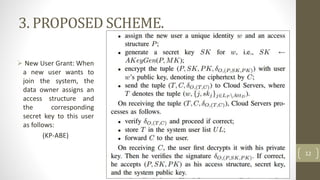
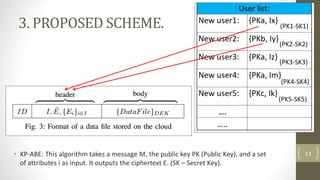
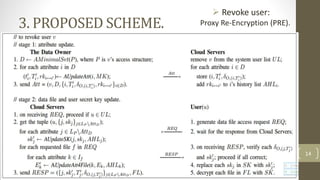
The document proposes a scheme to achieve secure, scalable, and fine-grained data access control in cloud computing. It combines key-policy attribute-based encryption (KP-ABE) and proxy re-encryption (PRE). When a new user joins, the data owner assigns them an access structure and secret key using KP-ABE. To revoke a user, the data is re-encrypted using PRE without needing to re-encrypt the entire data store or interact with the data owner. The proposed scheme provides fine-grained access control, confidentiality of user privileges, accountability of secret keys, and data confidentiality.