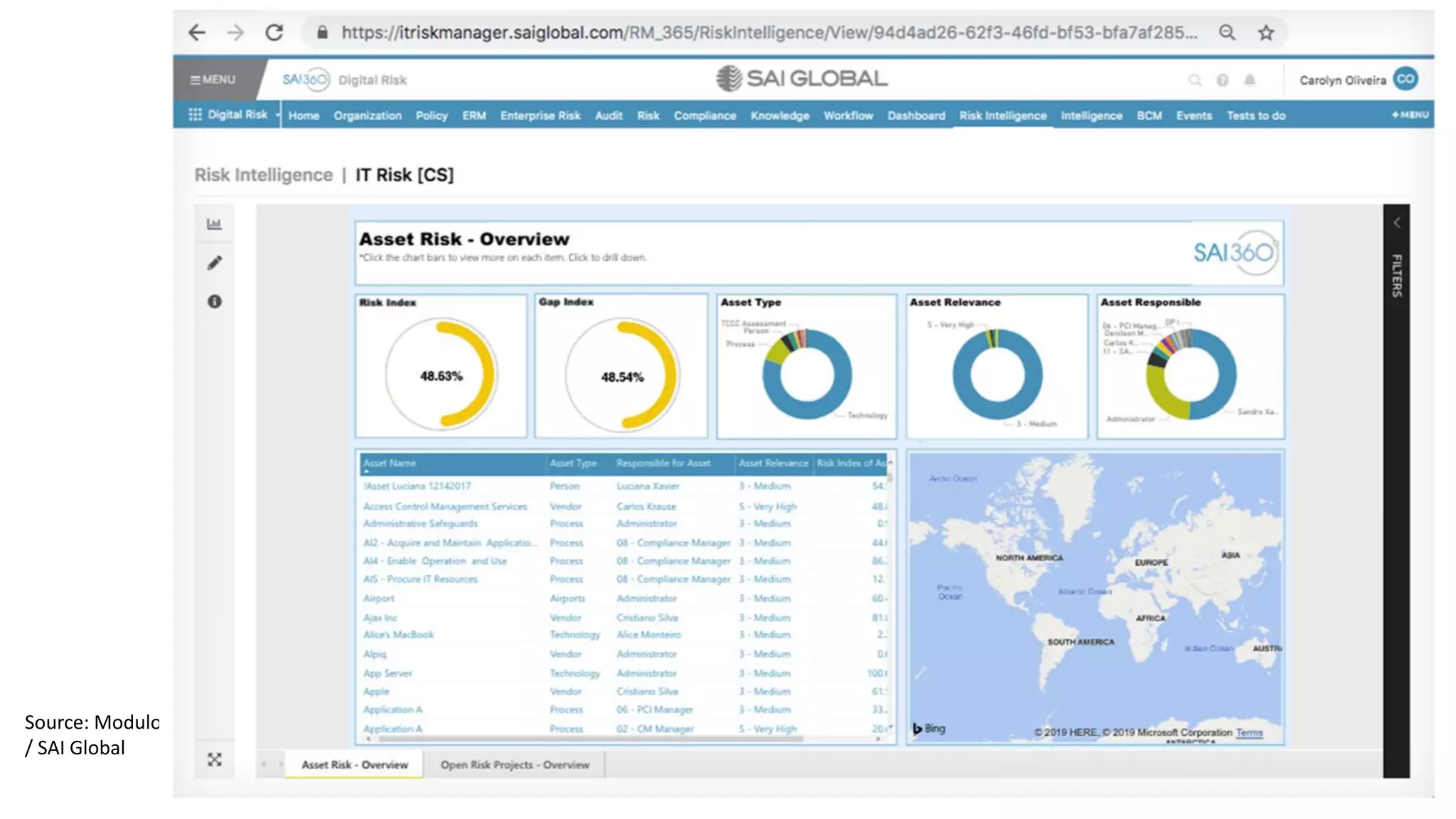
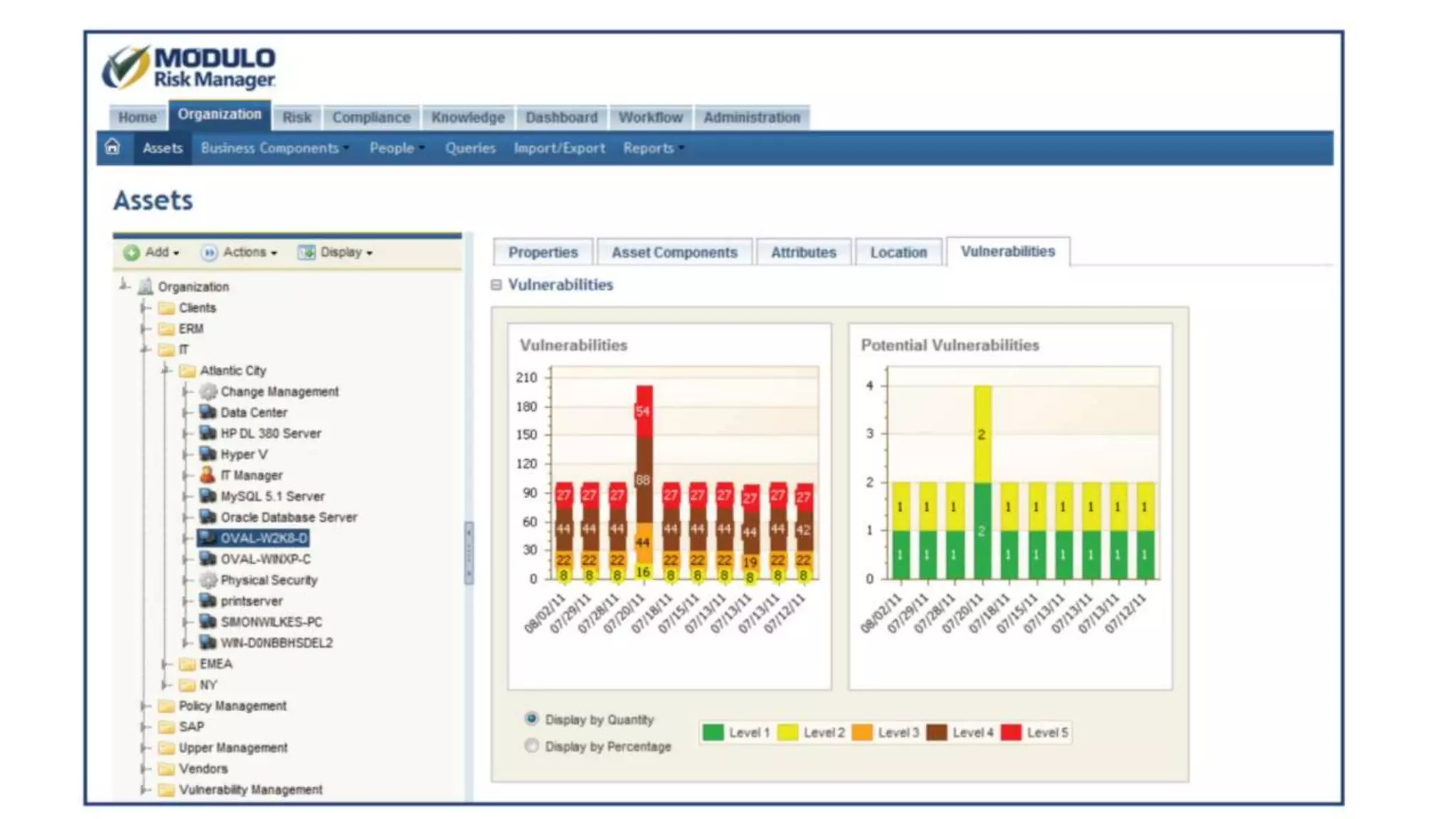
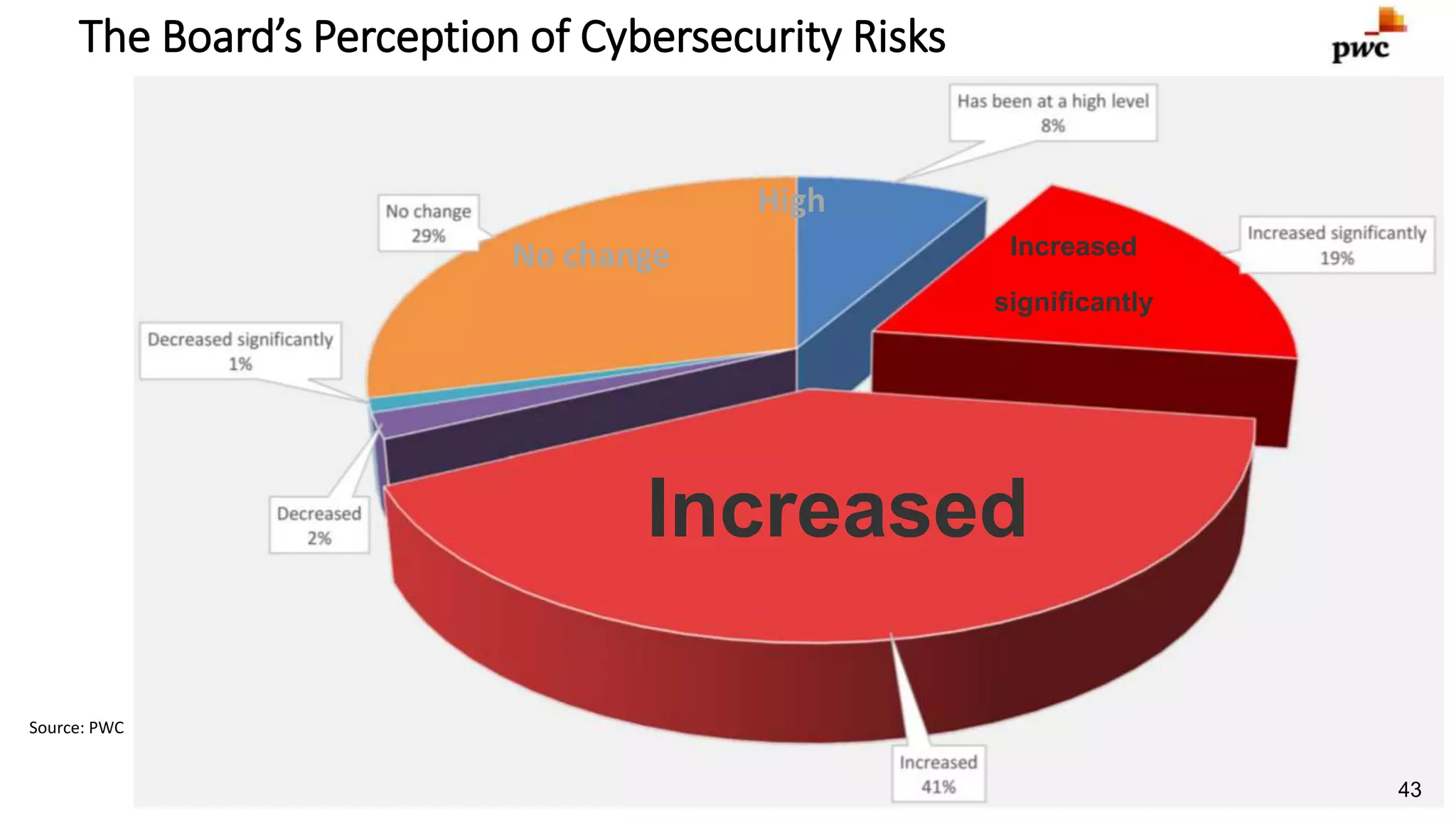
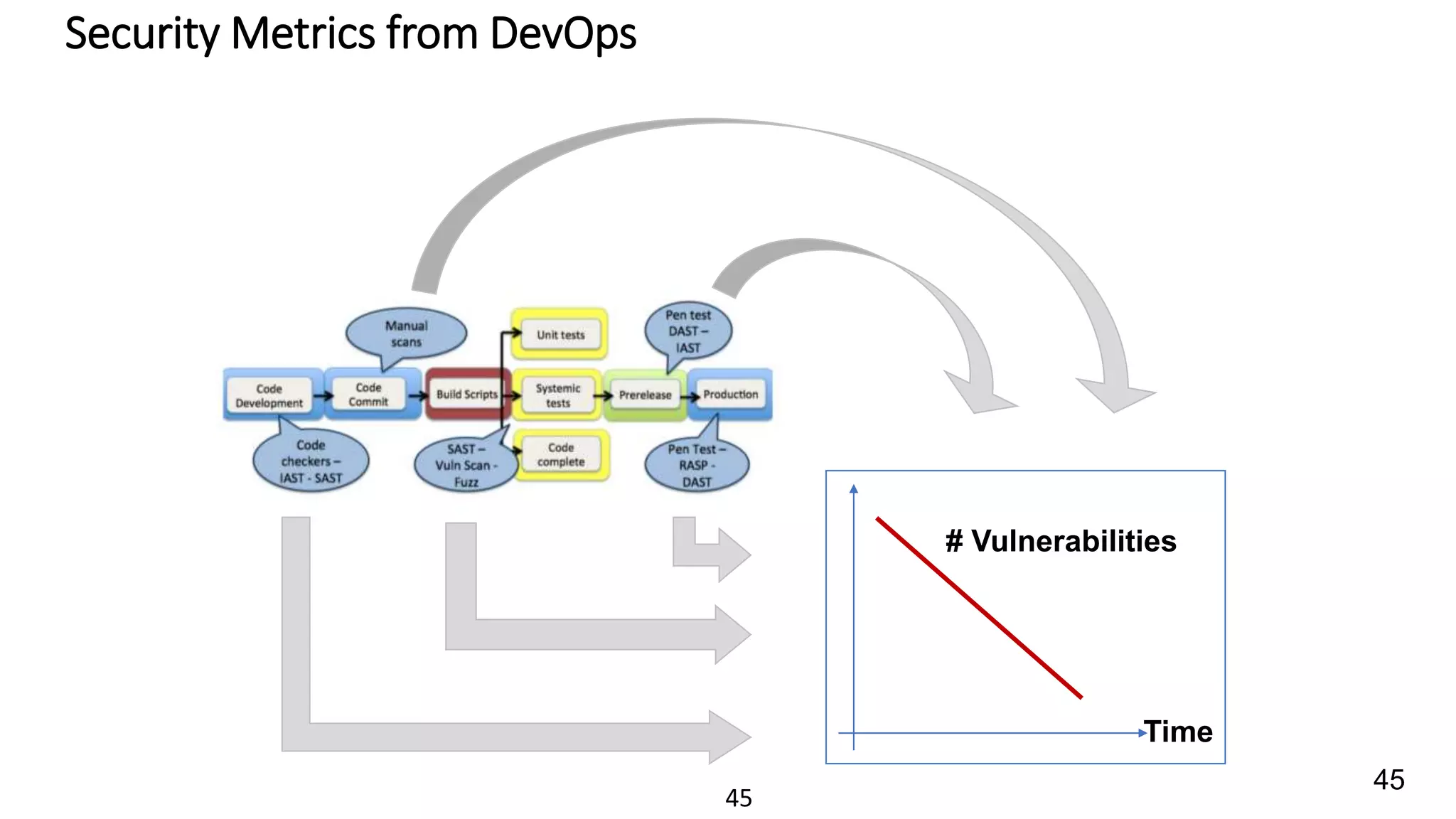
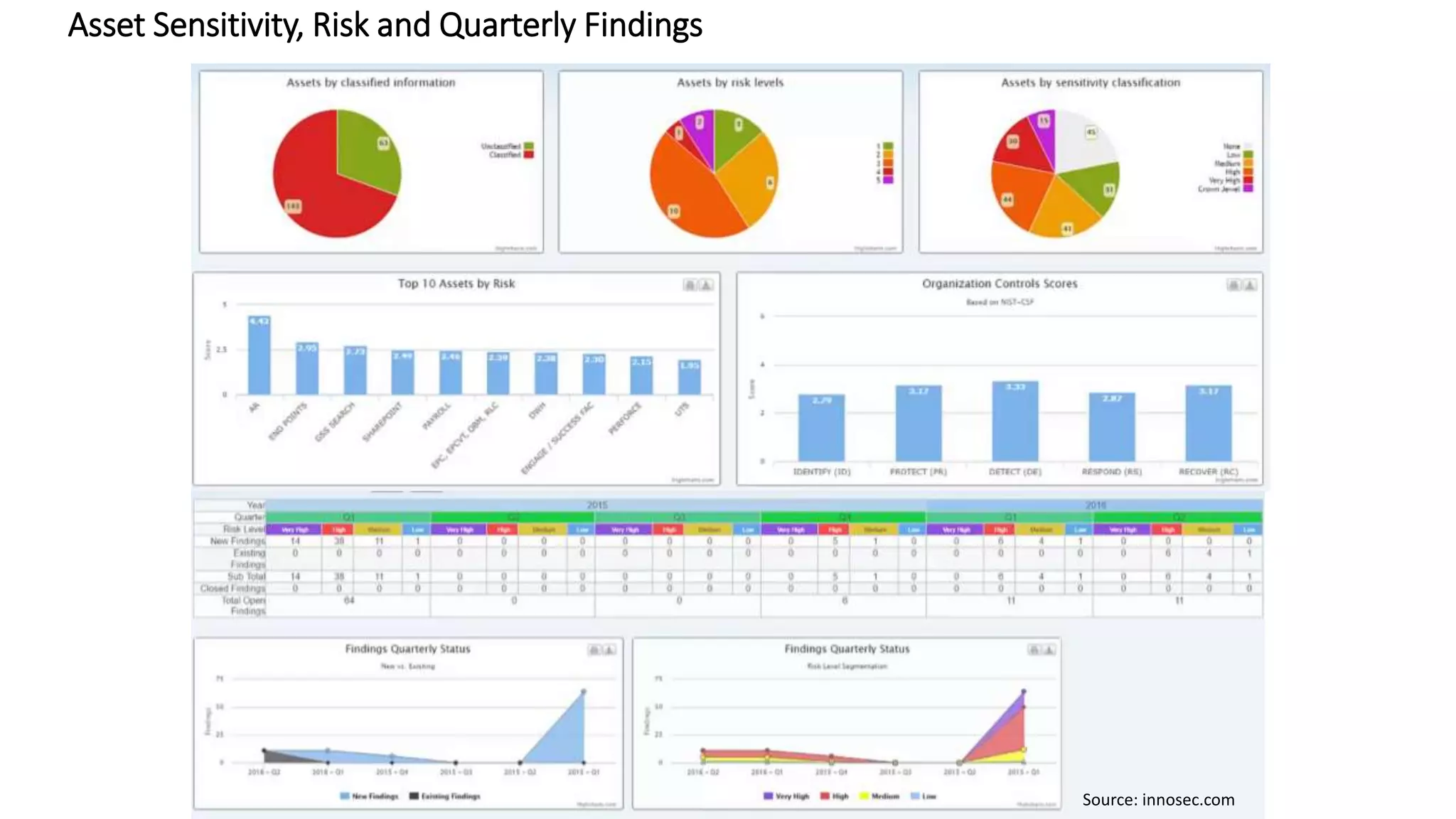
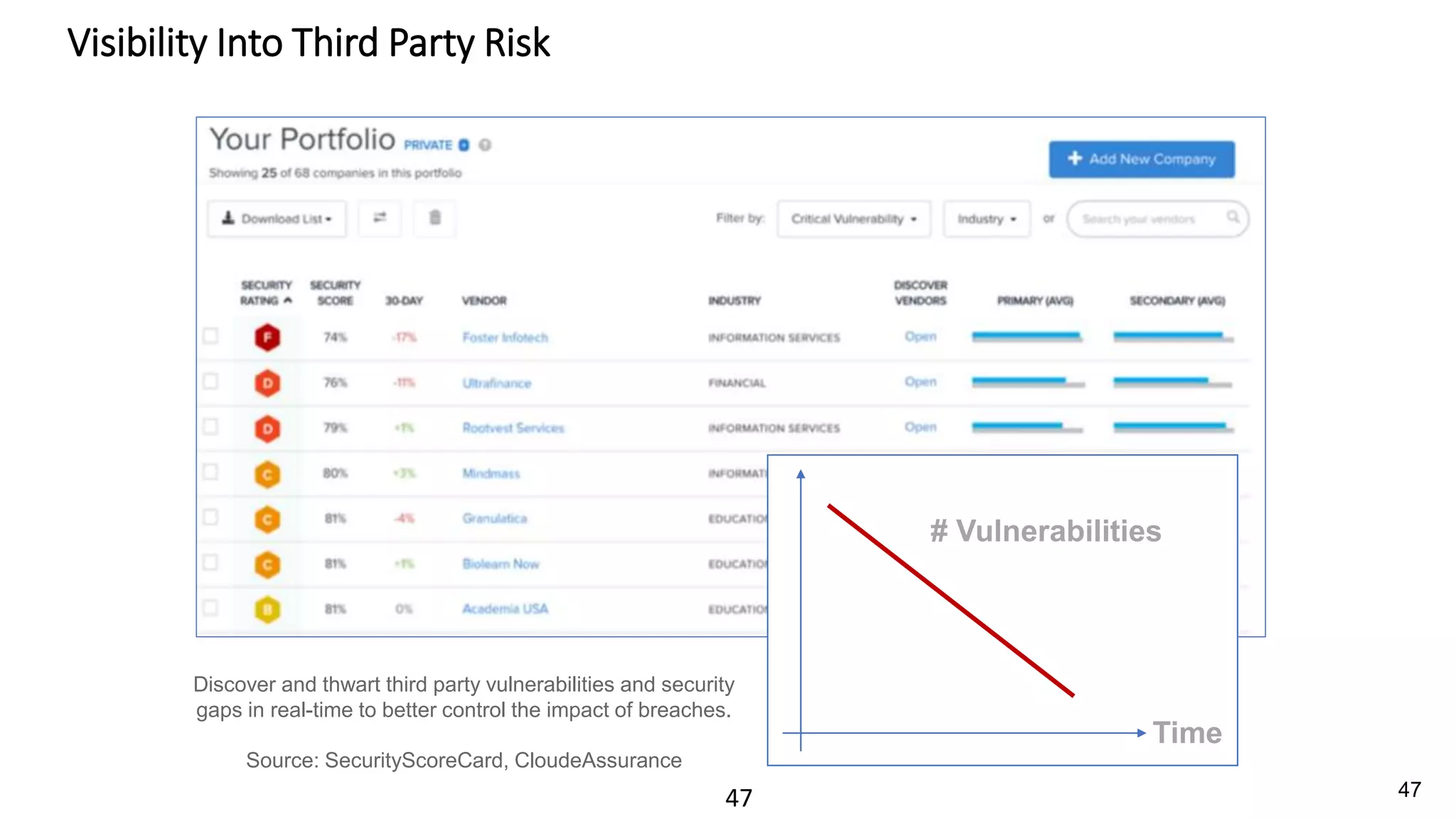
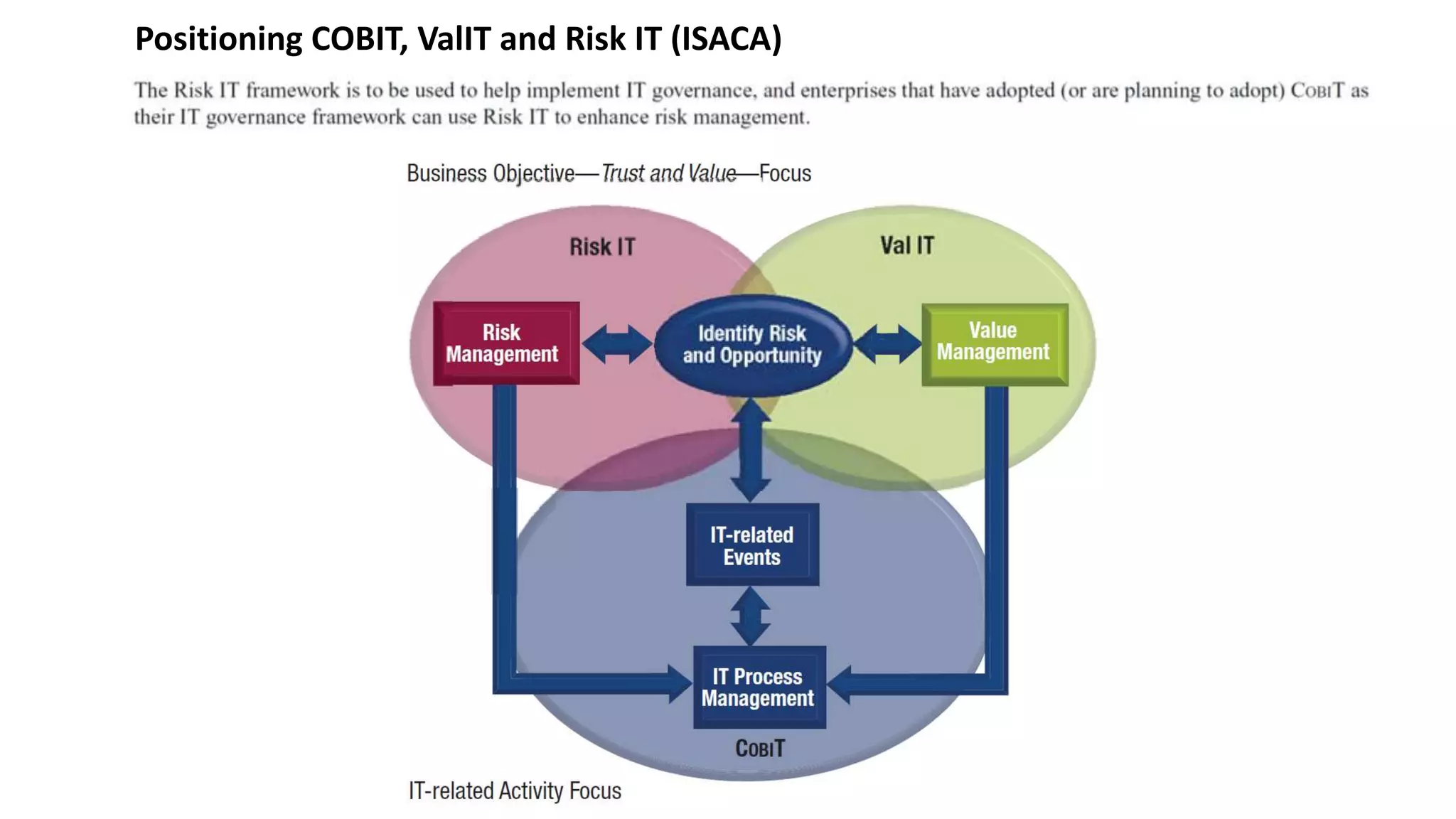
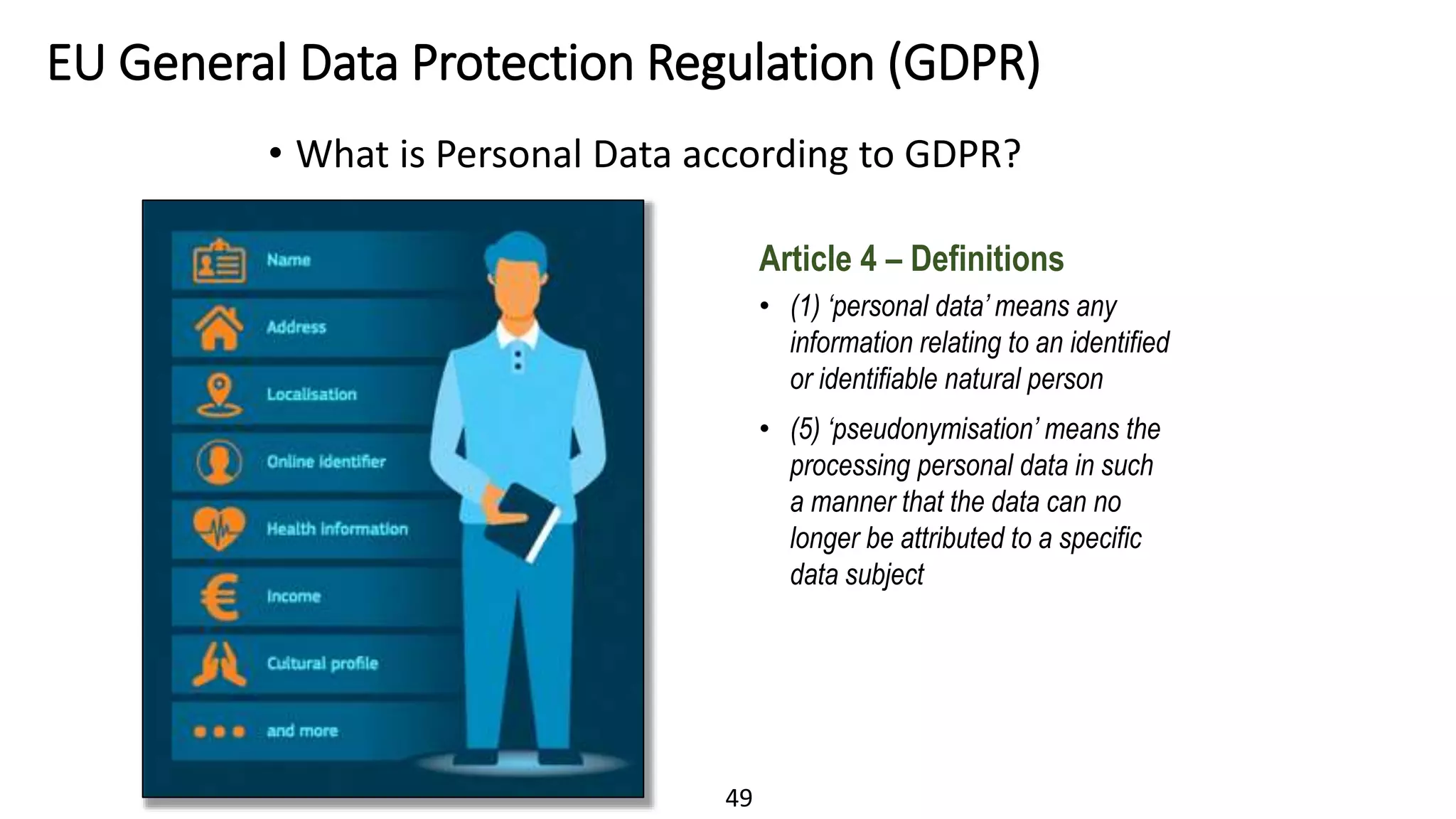
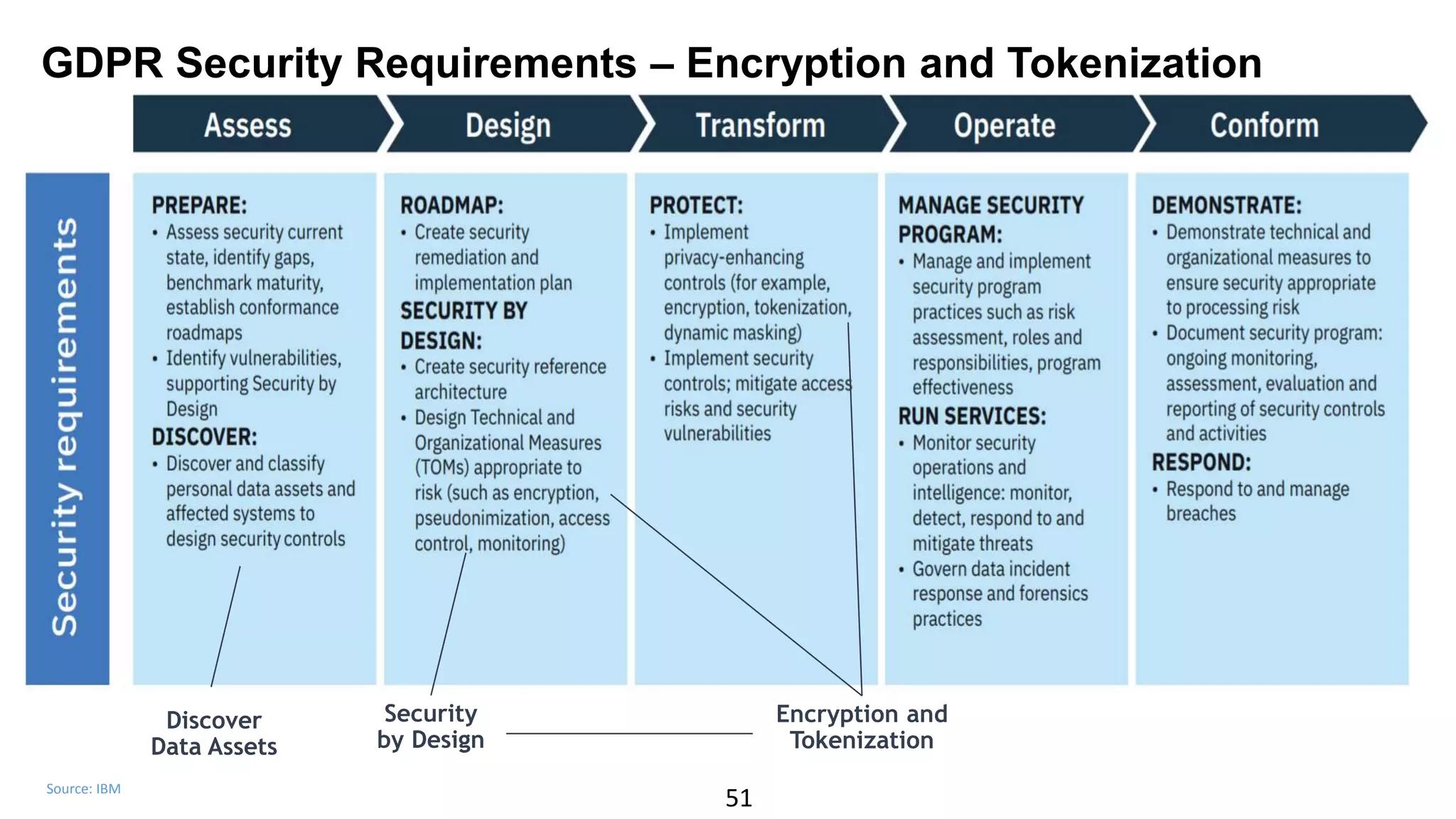
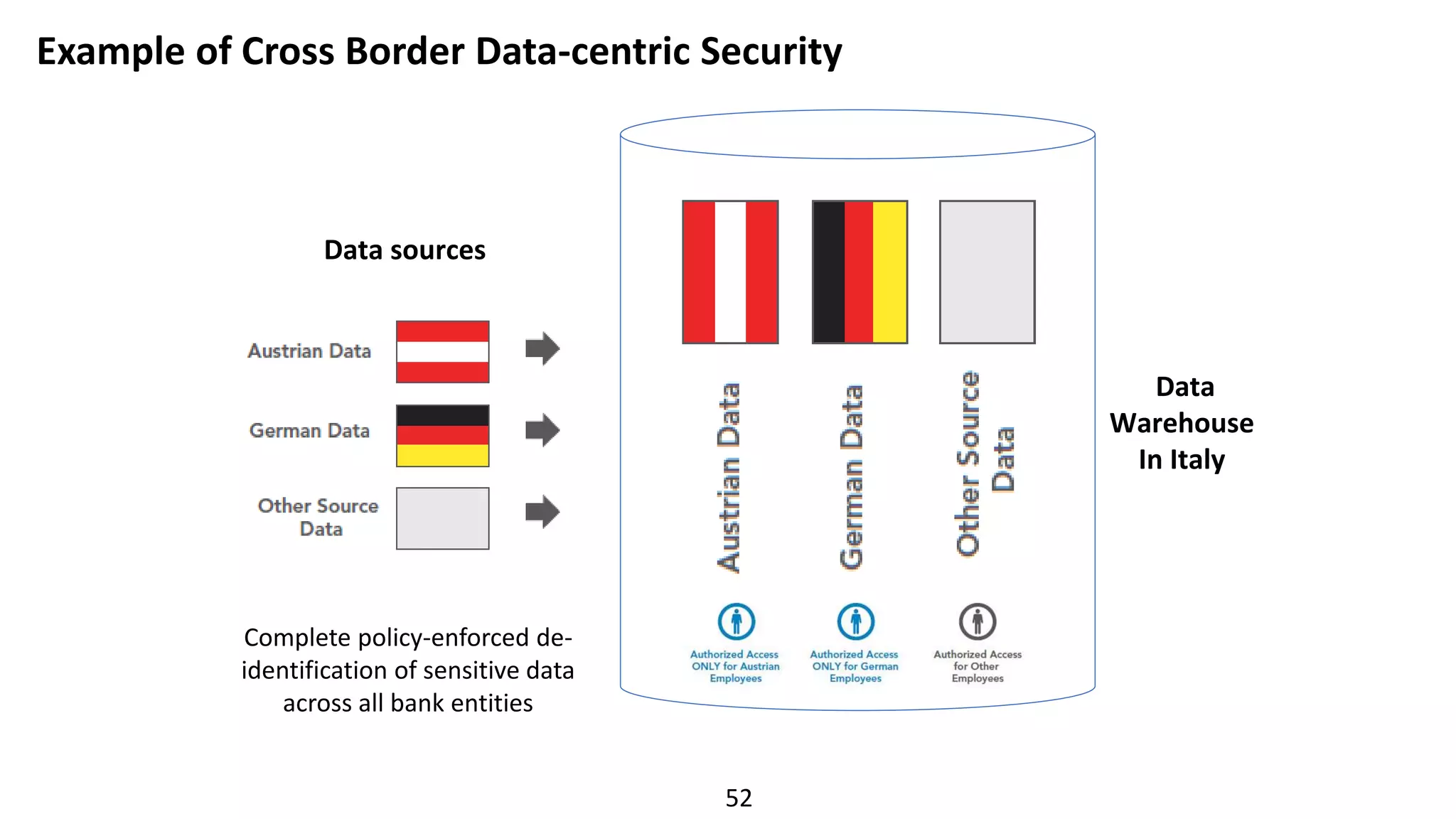
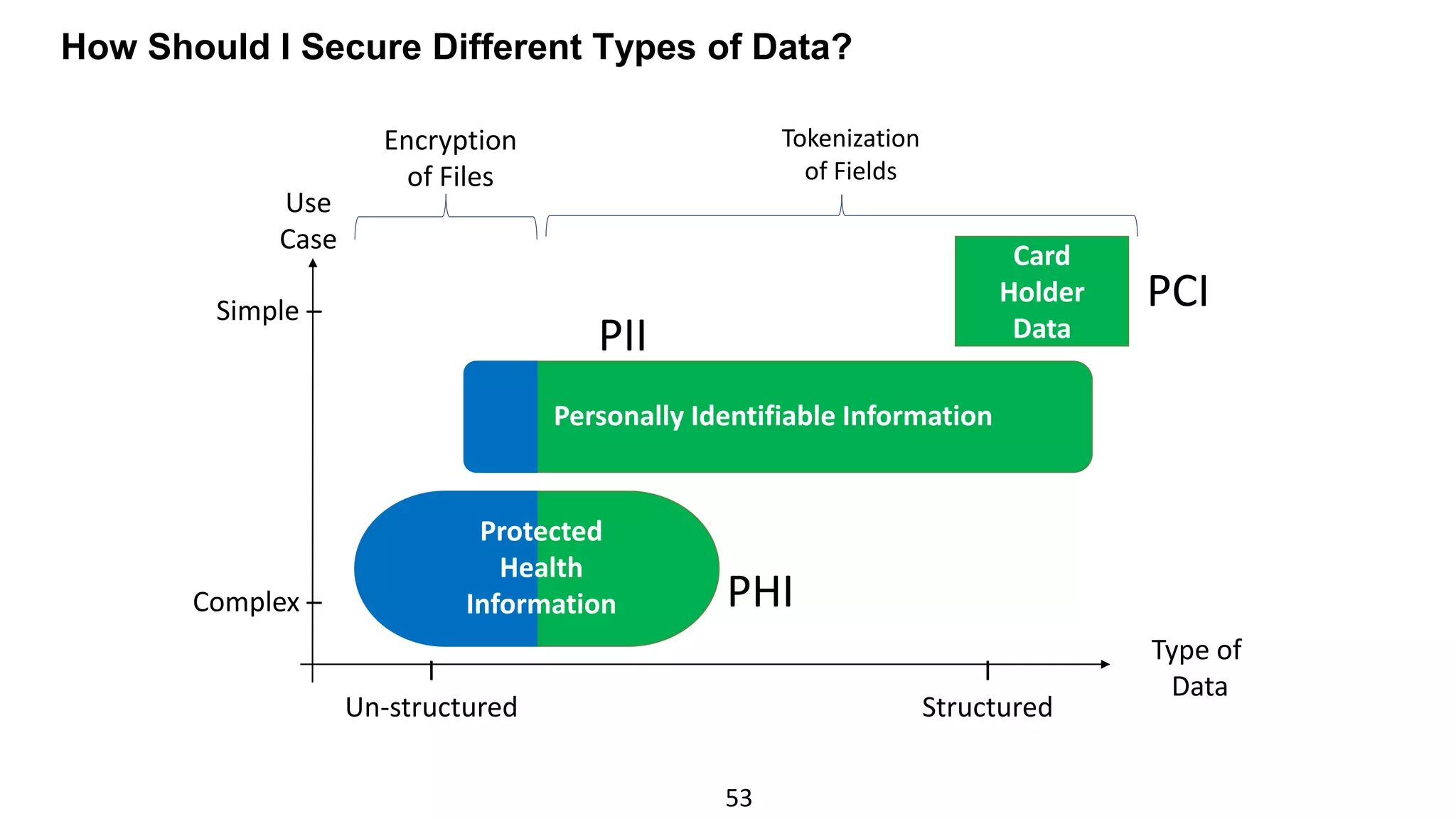
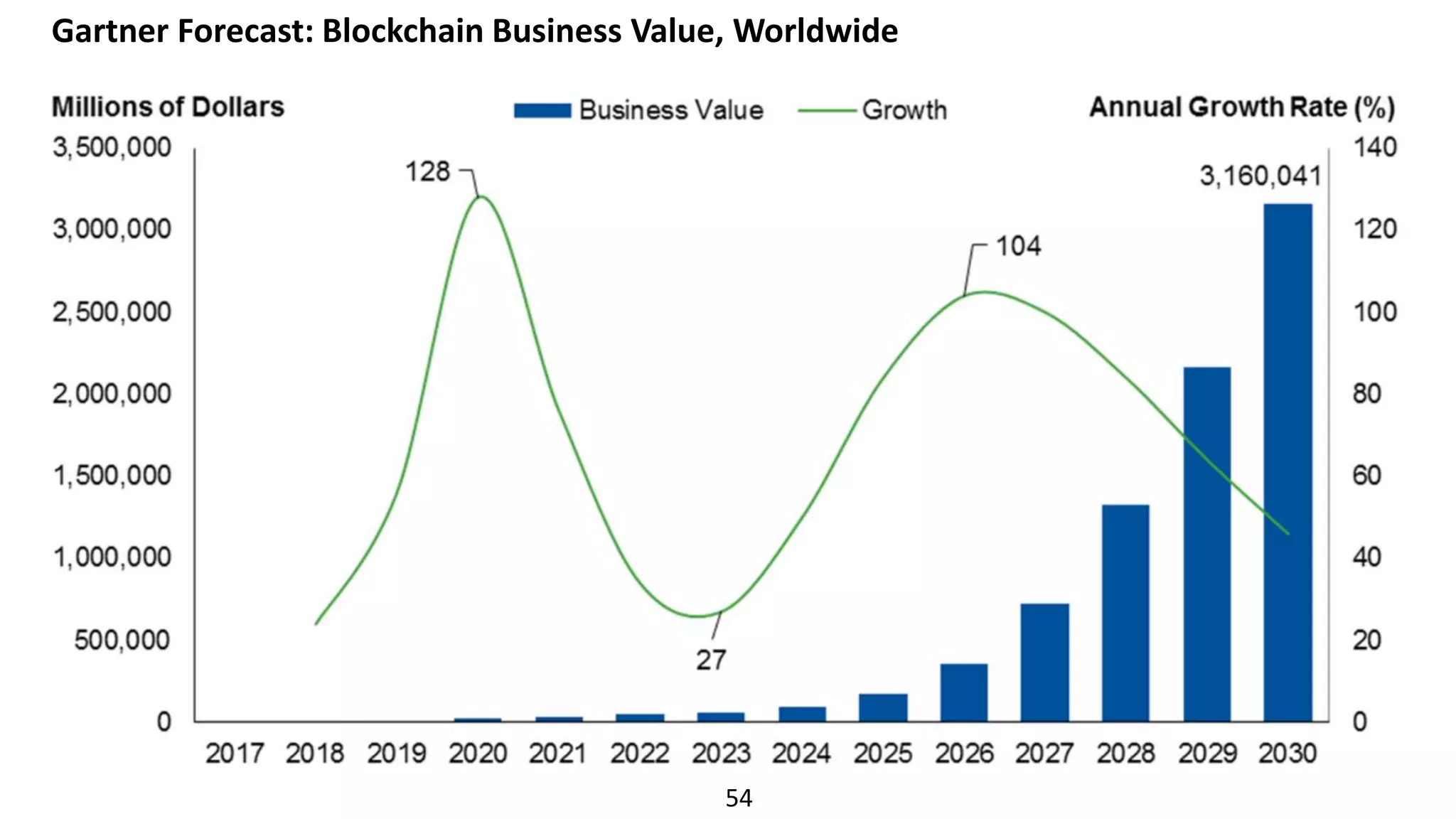
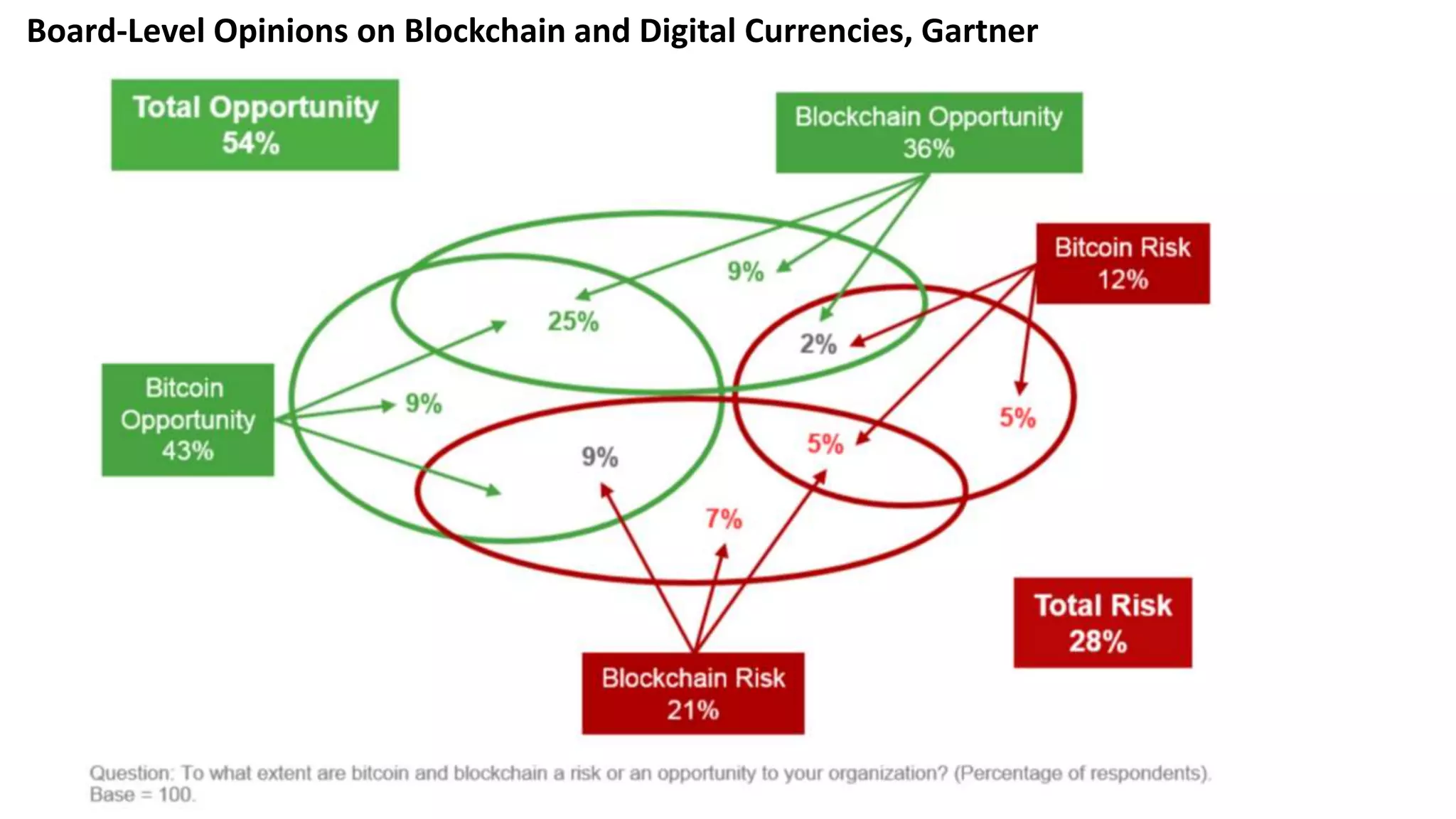
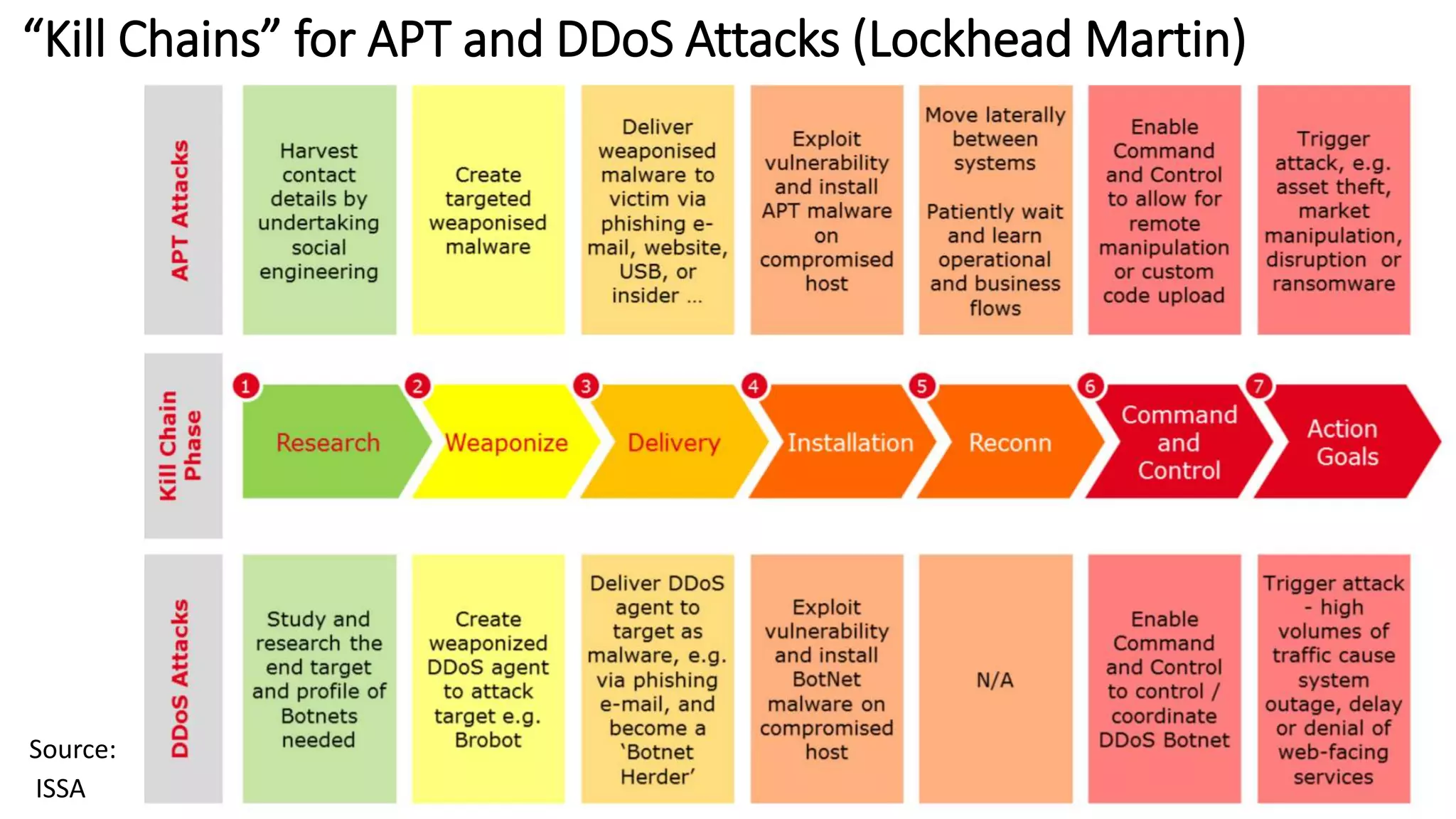
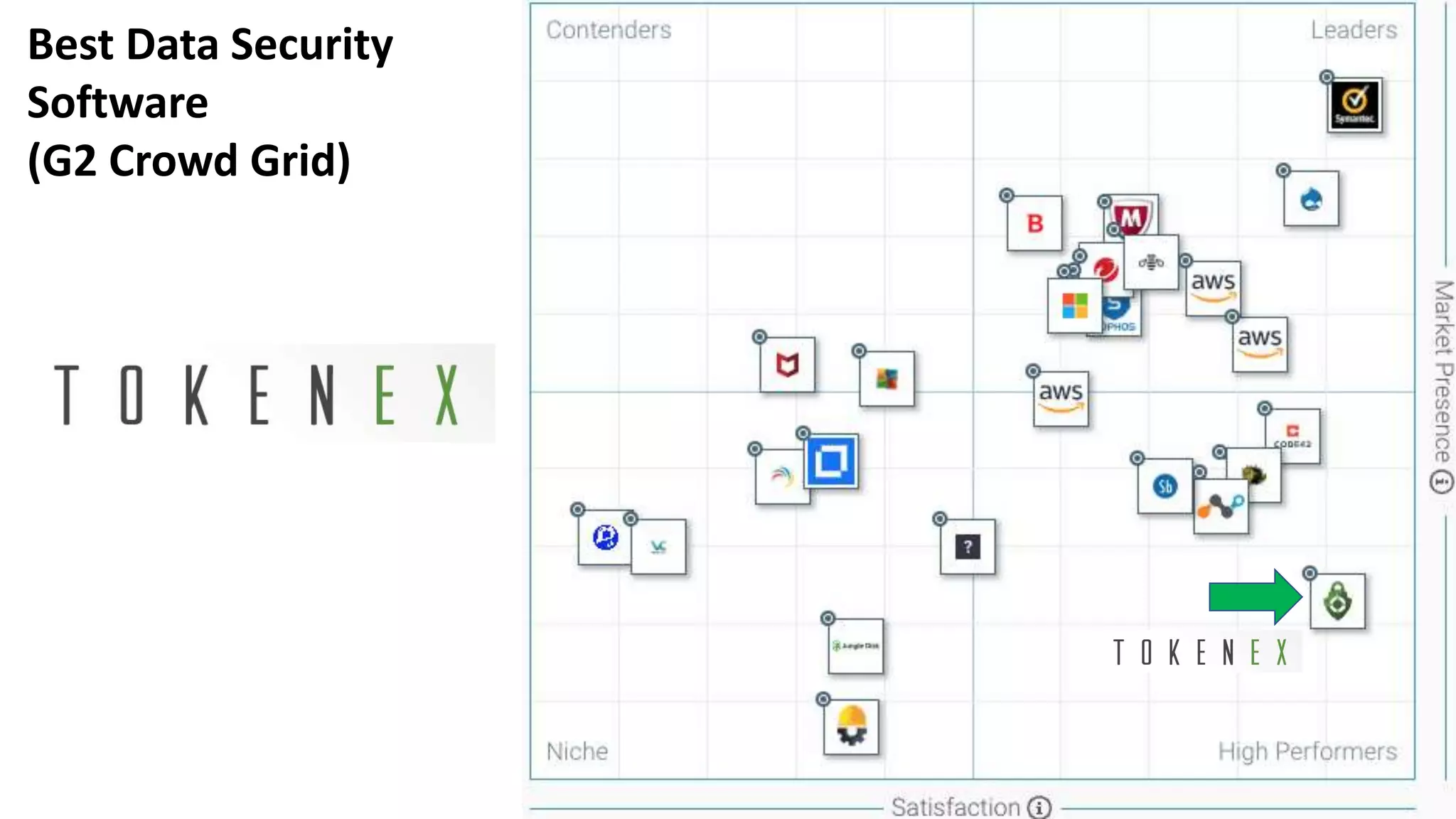
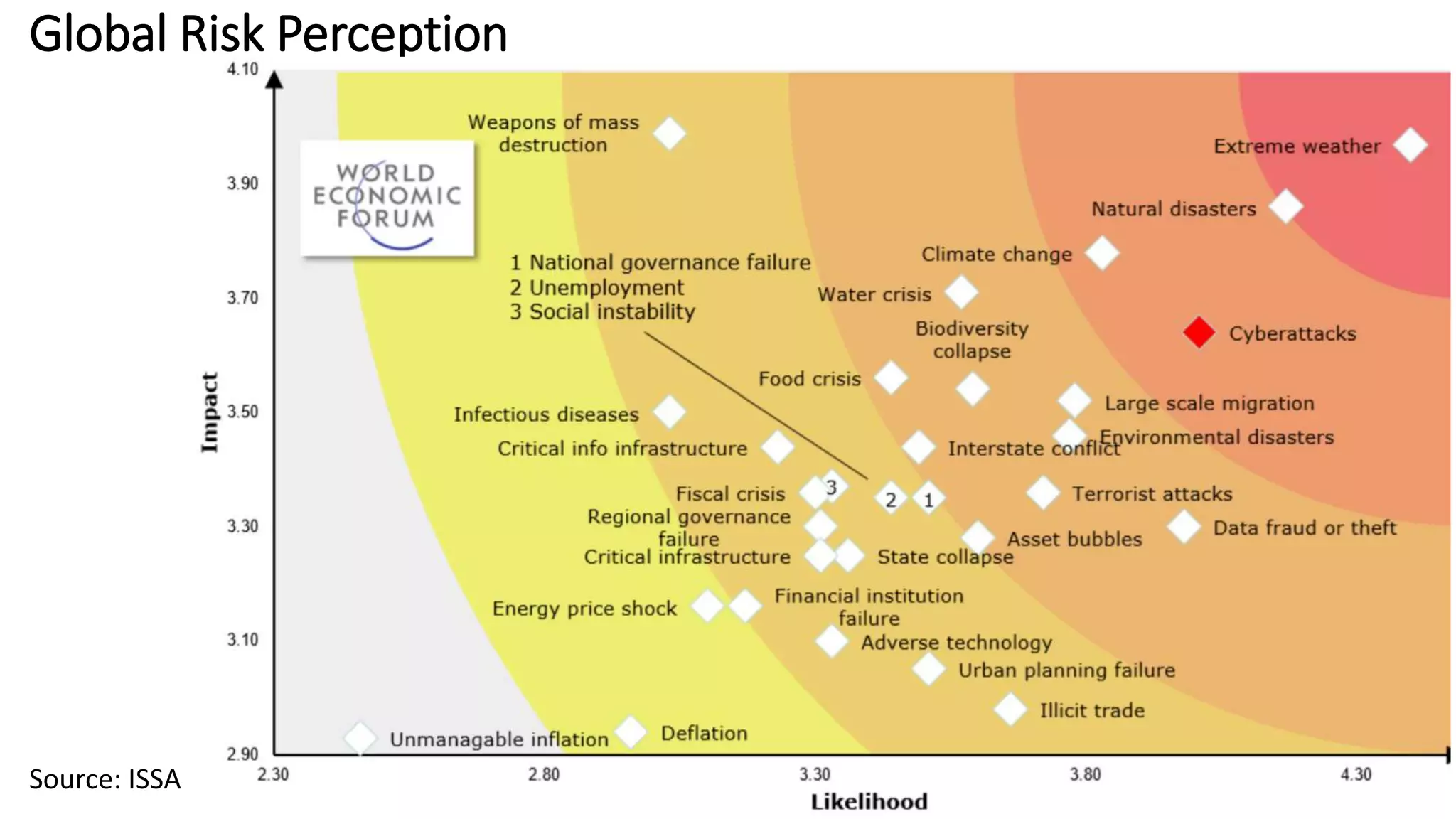
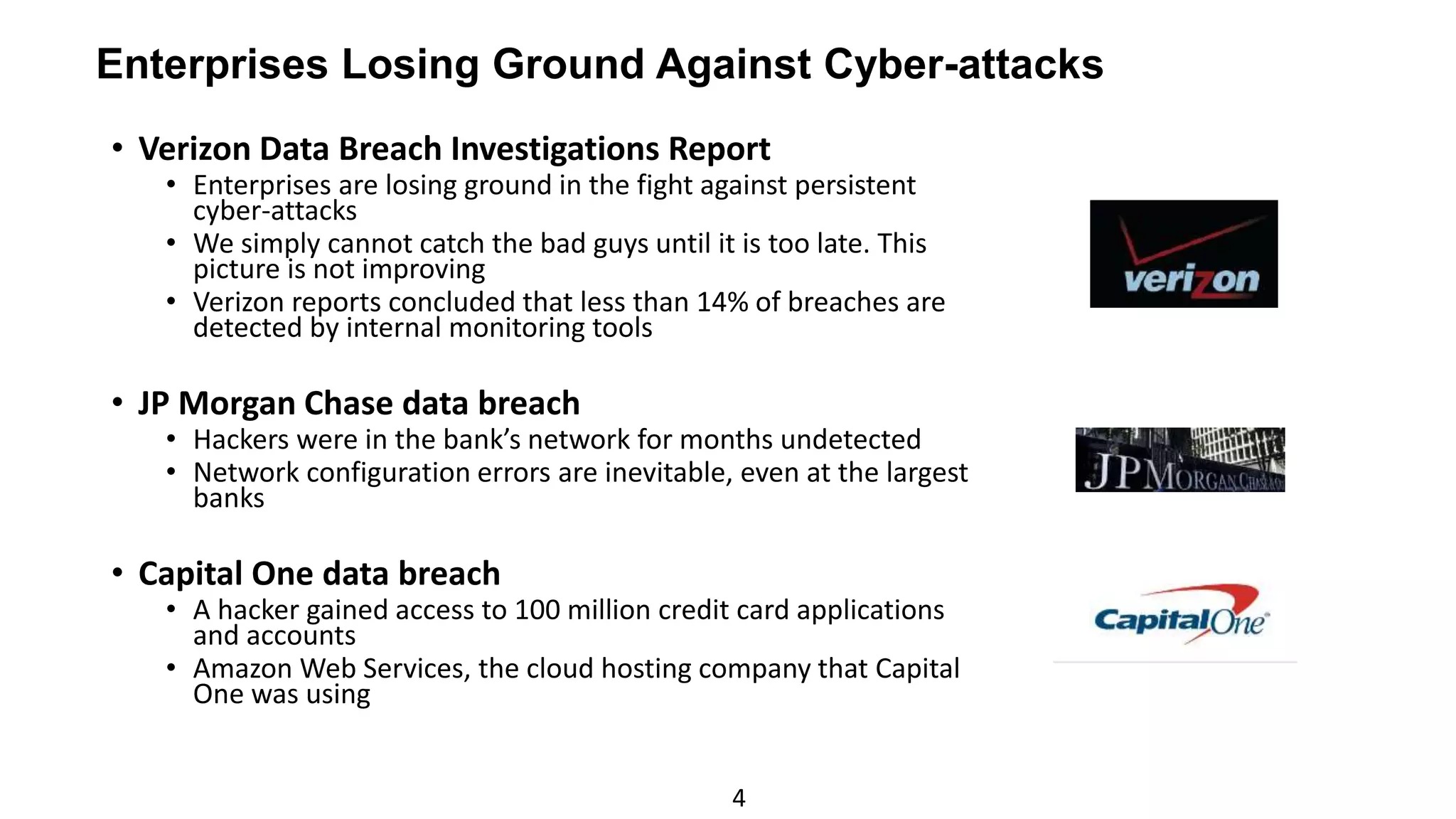
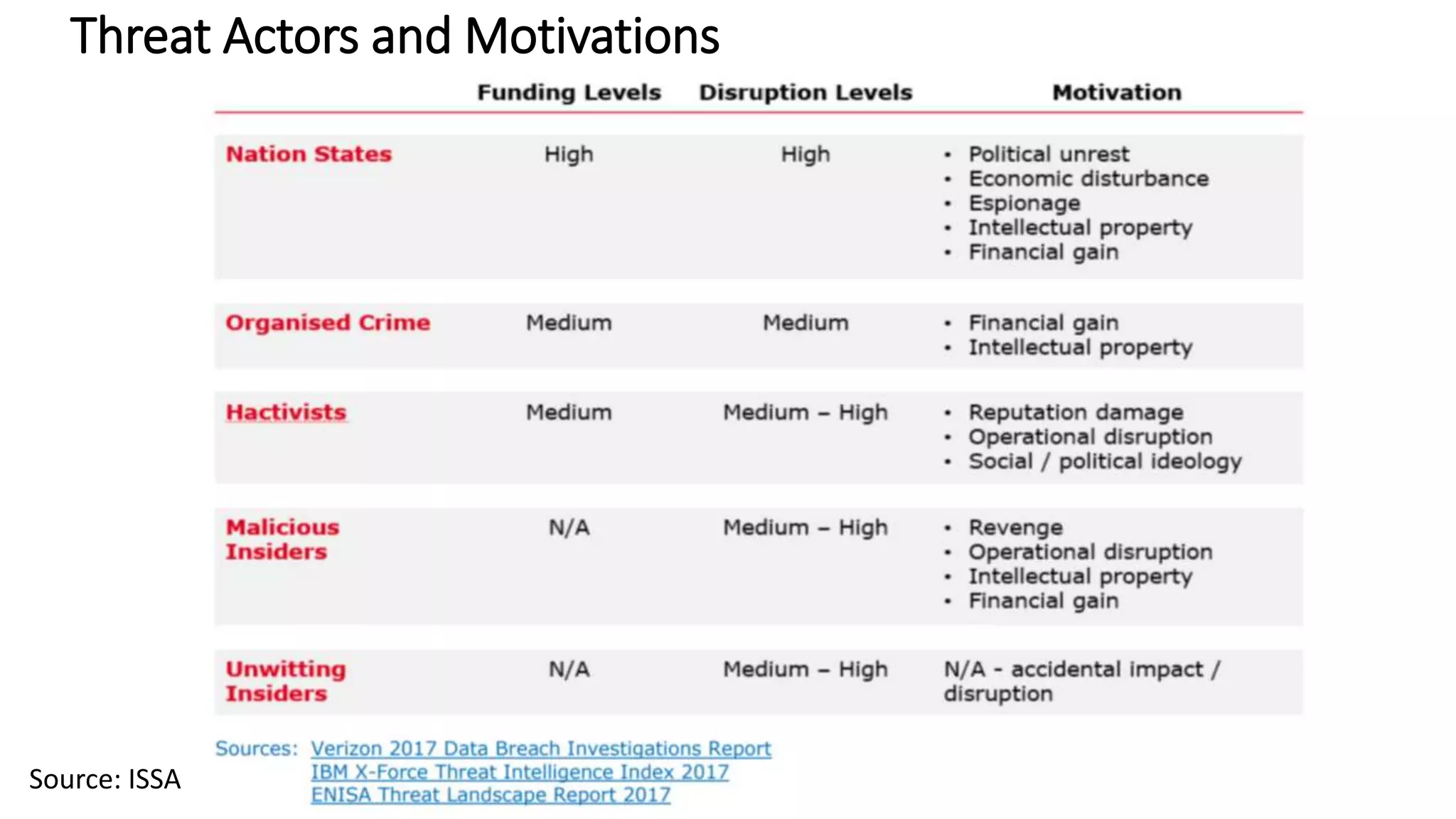
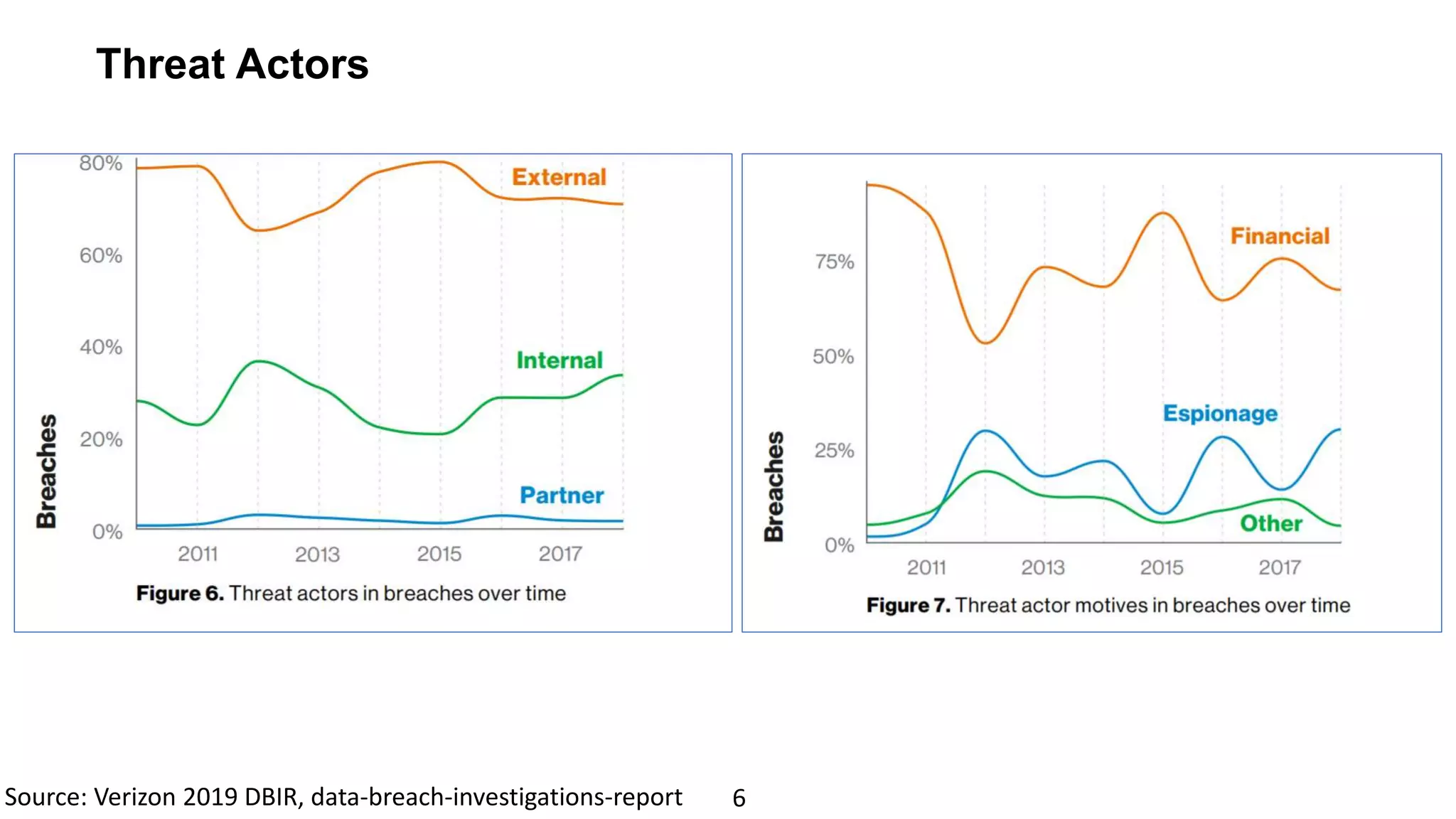
The document discusses the escalating risks of cyber-attacks in multi-cloud environments and emphasizes the necessity for improved security measures, including data encryption, tokenization, and cloud access security brokers. It highlights the persistent threats posed by hackers, citing major breaches and the limitations of current internal monitoring tools. Additionally, it addresses the anticipated risks from quantum computing, urging organizations to adopt quantum-resistant encryption strategies to safeguard sensitive data.




![34
What to do about Risks from Quantum Computing
Arvind Krishna – Director of IBM Research
• “Anyone that wants to make sure that their data is protected for longer than 10 years should move to
alternate forms of encryption now,” said Arvind Krishna, Director of IBM Research…
• “Quantum computers can solve some types of problems near-instantaneously compared with
billions of years of processing using conventional computers.
National Institute of Standards and Technology (NIST)
• “For public key cryptography, the damage from quantum computers will be catastrophic. We must
look for quantum-resistant counterparts for these cryptosystems.”
• Dr. Lily Chen, head of the National Institute of Standards and Technology’s Cryptographic Technology Group.
Institute for Quantum Computing University of Waterloo, CA
• Dr. Michele Mosca, cofounder of the Institute for Quantum Computing at the University of Waterloo.
• It isn’t too early [to act now] for companies handling data that remains valuable for many years, such
as medical or financial records.
• Such companies need to consider the risk that an adversary could capture encrypted data and store
it until the day a quantum computer can decrypt it, says Mosca.
• Mosca estimates a one in seven chance that by 2026 someone, likely a nation state, will have a
quantum computer able to crack encryption used for critical data today.
• “The industry’s usual recipe of waiting for catastrophe and then fixing it is very risky,” he says.
Source: ANSI X9](https://image.slidesharecdn.com/practicalriskmanagementforthemulti-cloudoct92019e-191010170627/75/Practical-risk-management-for-the-multi-cloud-34-2048.jpg)