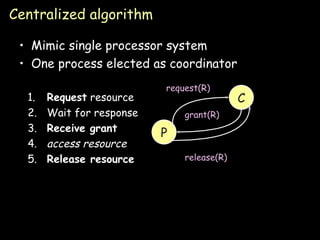
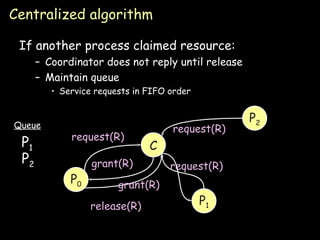
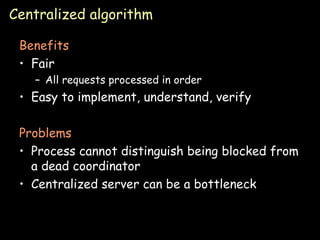
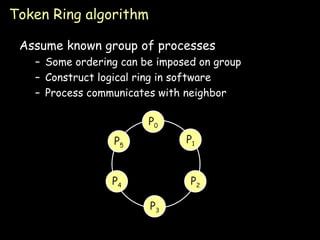
The document discusses several algorithms for process synchronization and mutual exclusion in distributed systems:
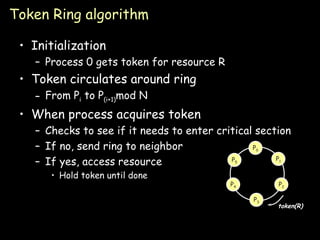
- Token ring algorithm passes an exclusive token around a logical ring of processes to control access to shared resources.
- Ricart-Agrawala algorithm uses message ordering and timestamps to elect a process to enter the critical section.
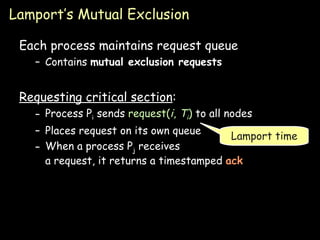
- Lamport's mutual exclusion algorithm uses request queues and timestamps to ensure only one process is in the critical section at a time.
- Election algorithms like the Bully and Ring algorithms elect a coordinator process to handle synchronization and recovery from failures.
![Mutual Exclusion & Election Algorithms Paul Krzyzanowski [email_address] [email_address] Distributed Systems Except as otherwise noted, the content of this presentation is licensed under the Creative Commons Attribution 2.5 License.](https://image.slidesharecdn.com/12-mutualexclusion-election-090902071103-phpapp01/75/Mutual-Exclusion-Election-Distributed-computing-1-2048.jpg)