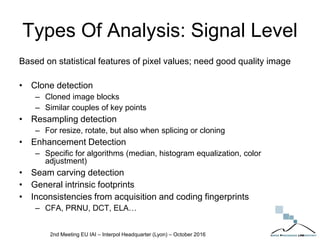
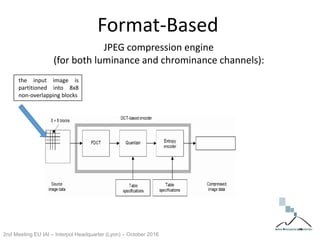
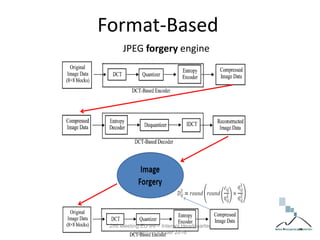
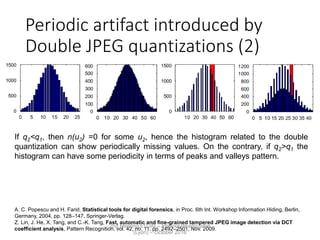
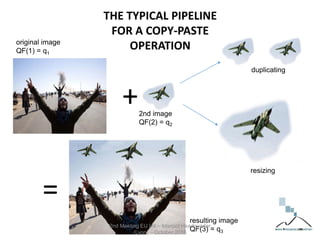
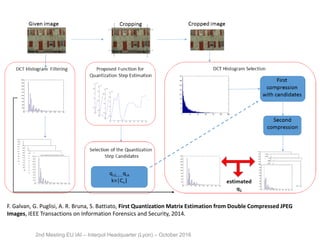
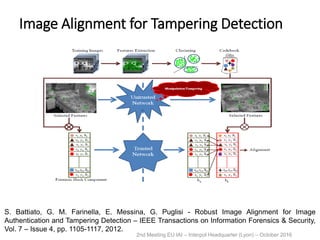
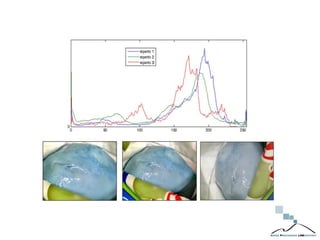
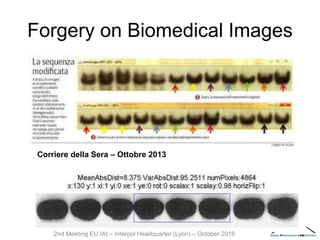
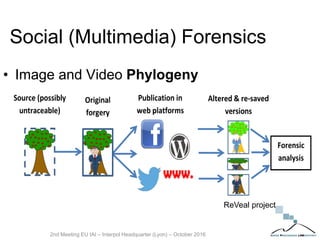
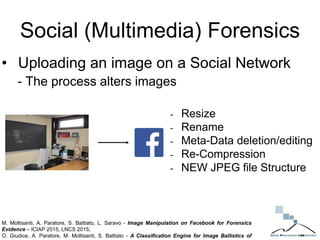
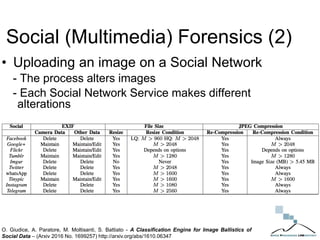
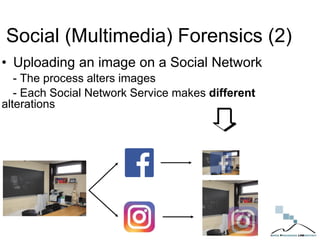
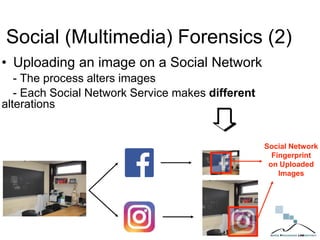
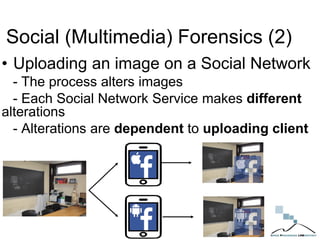
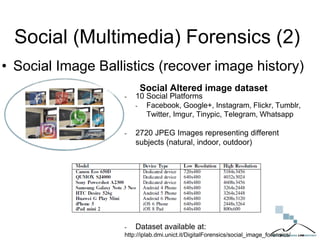
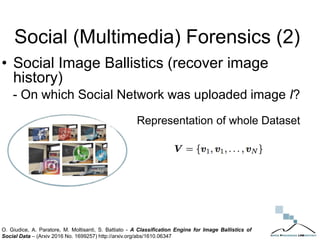
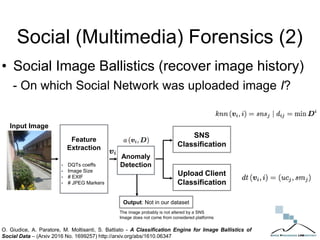
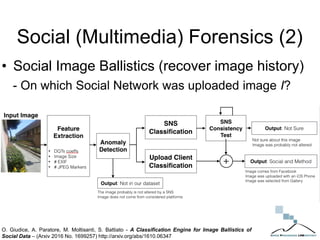
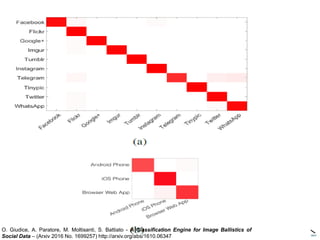
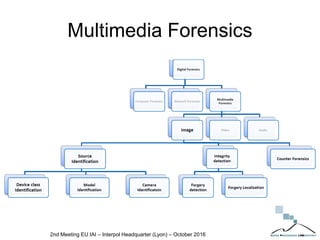
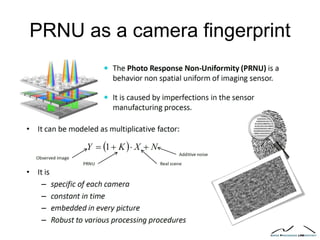
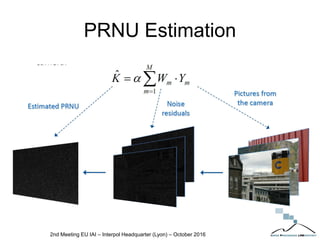
The document discusses multimedia forensics, focusing on techniques for source identification and integrity verification of digital media. It highlights the importance of identifying inherent traces in digital media to verify authenticity and the challenges posed by modern image editing techniques. Various methods of forensic analysis, including the assessment of image manipulation and the impact of social media on image history, are explored.


















![Sensor Identification Using
Pattern Noise
2nd Meeting EU IAI – Interpol Headquarter (Lyon) – October 2016
[Lukas2006] J. Lukas, J. Fridrich, and M. Goljan, “Digital Camera identification from sensor pattern noise” IEEE
Transaction Inf. Foren.Sec. Vol. 1, 205–214 (2006).](https://image.slidesharecdn.com/multimediaforensicssb-161021081516/85/Multimedia-Social-Forensics-30-320.jpg)