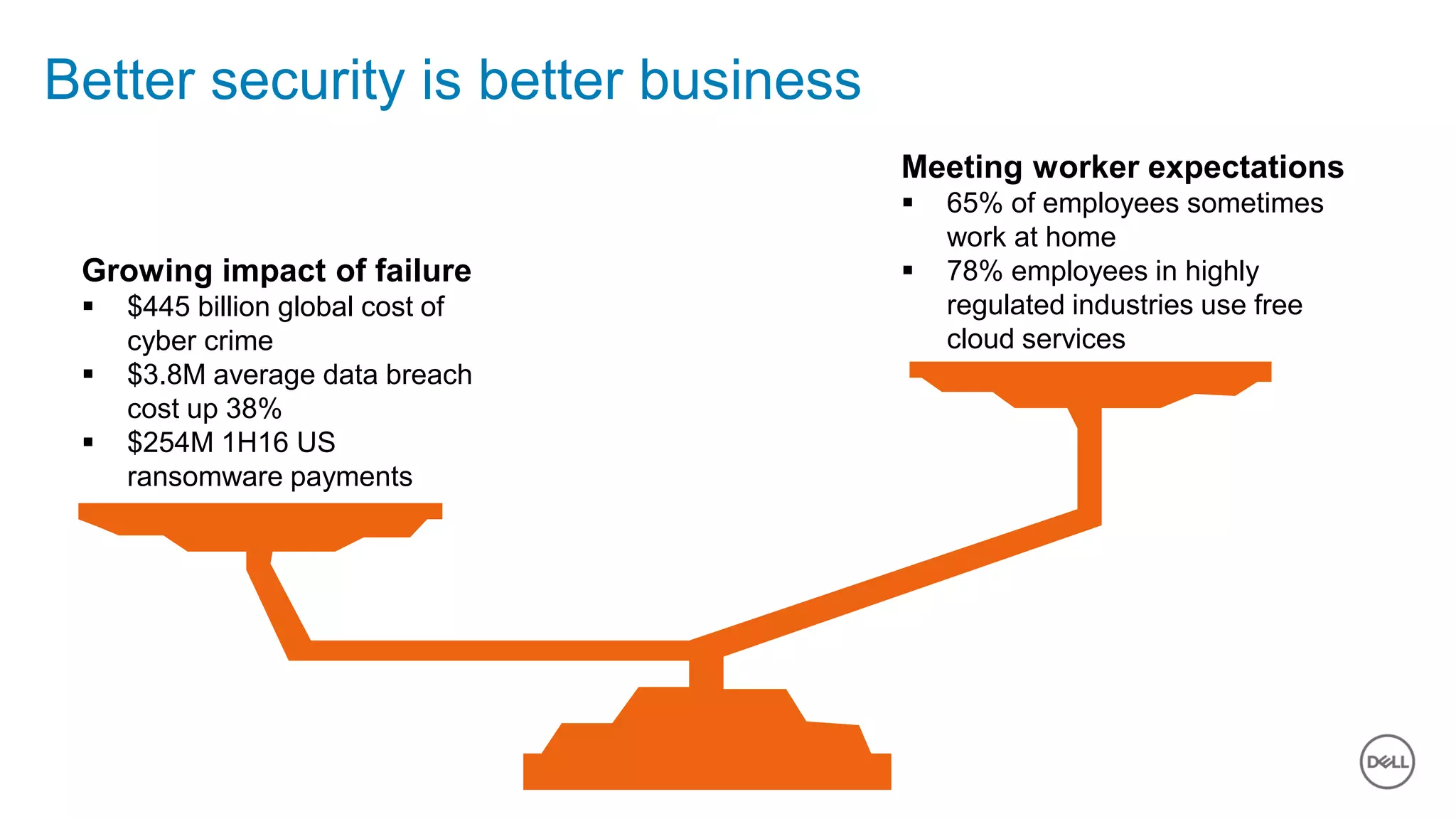
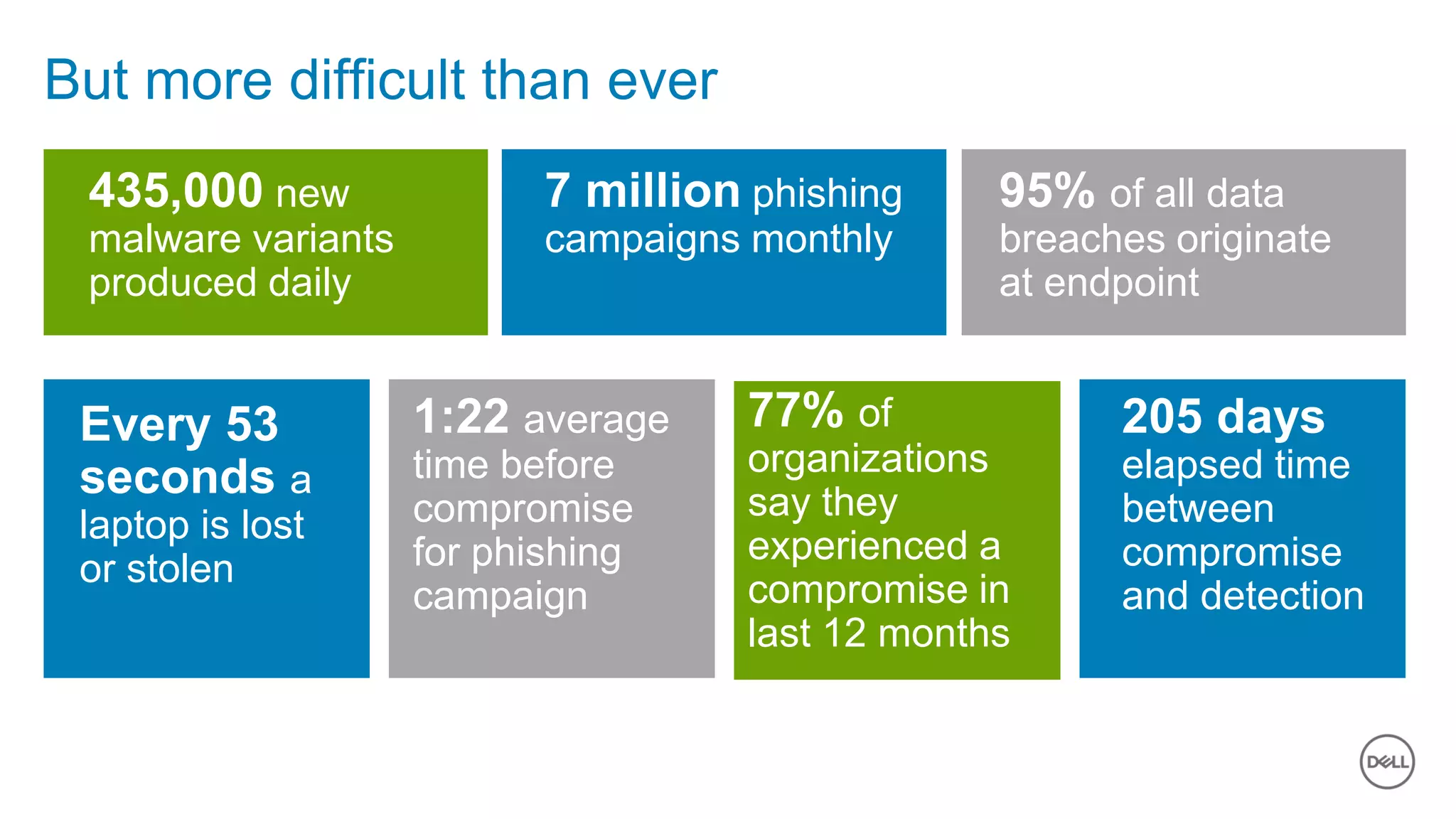
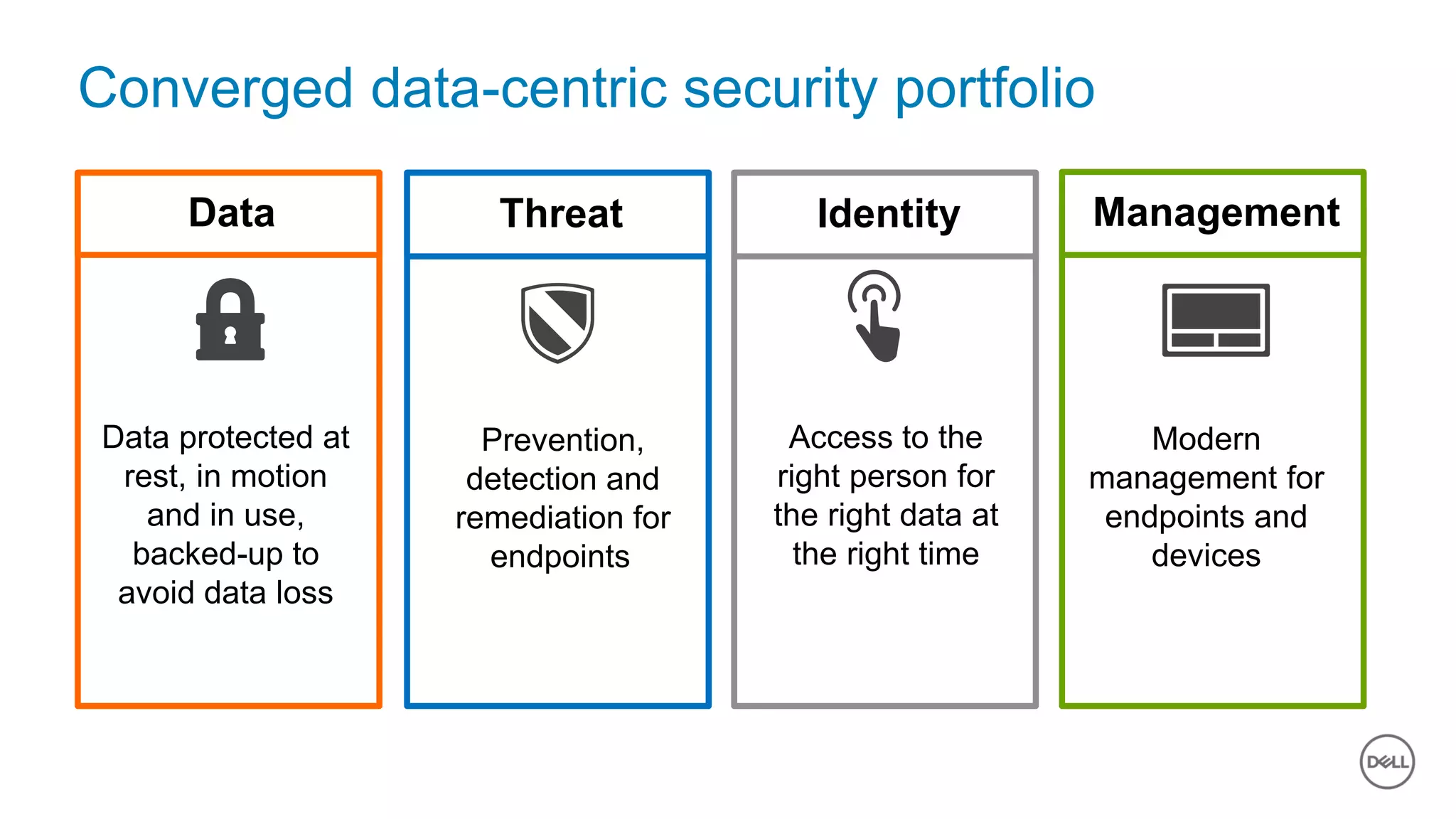
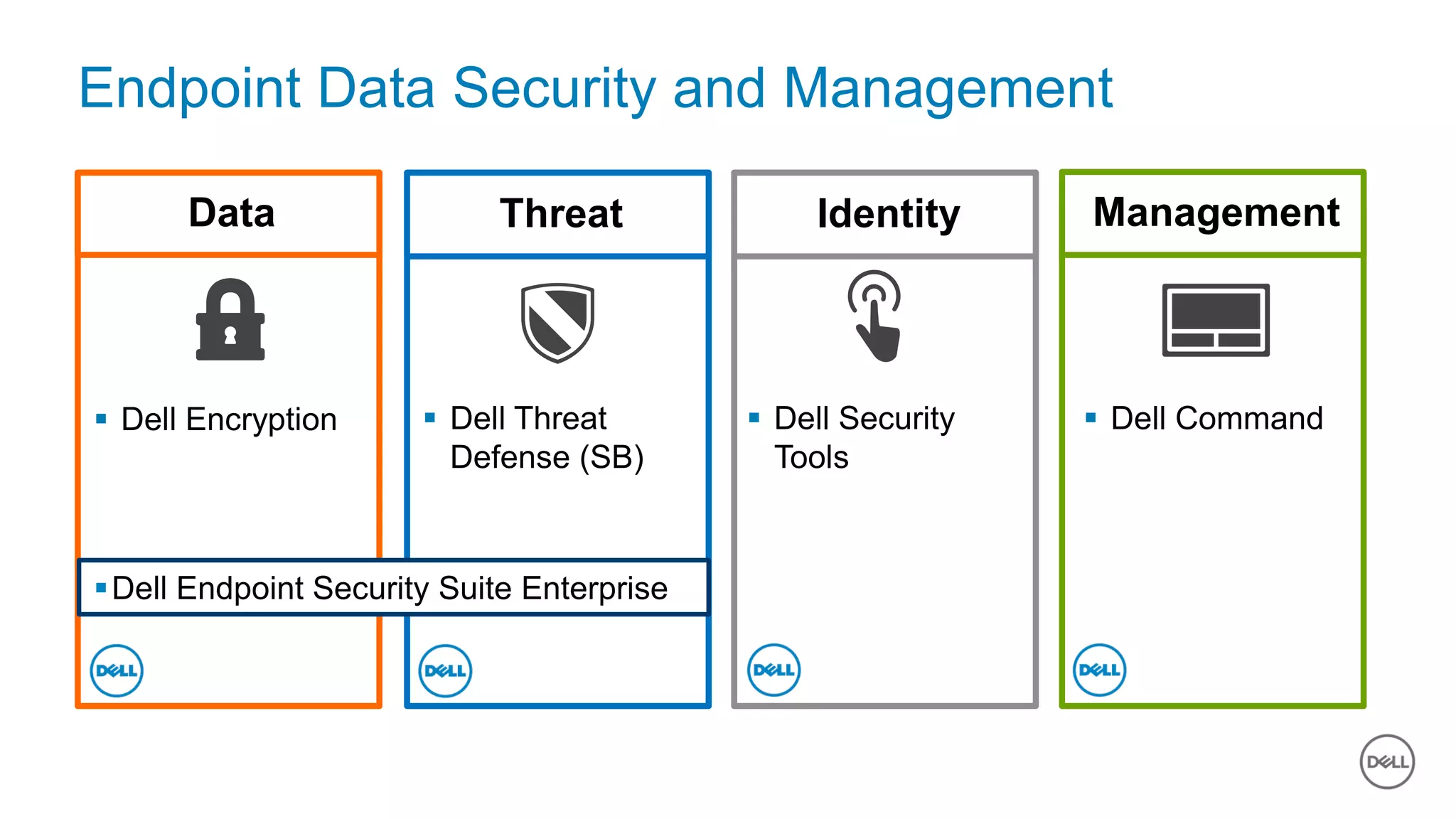
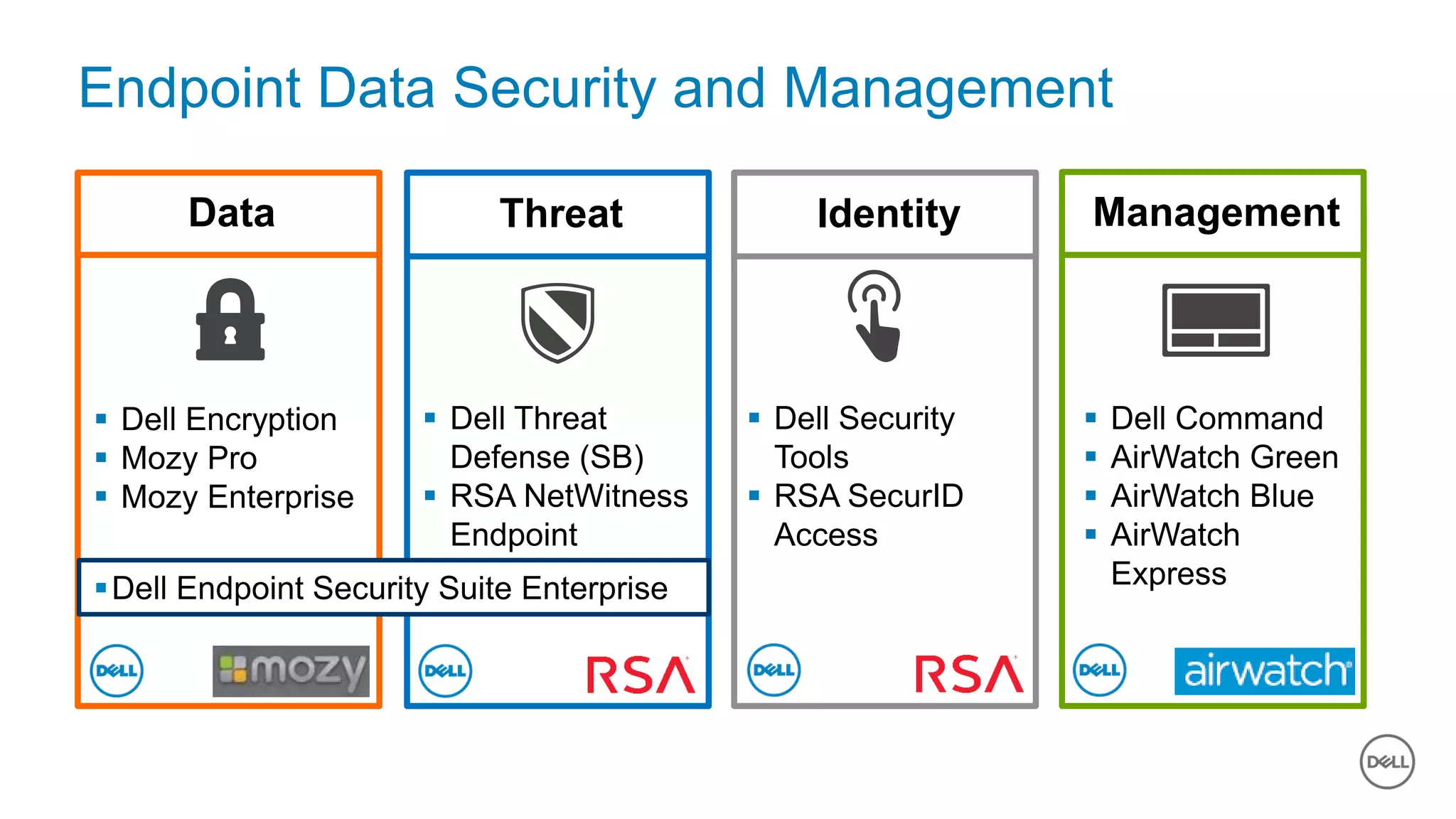
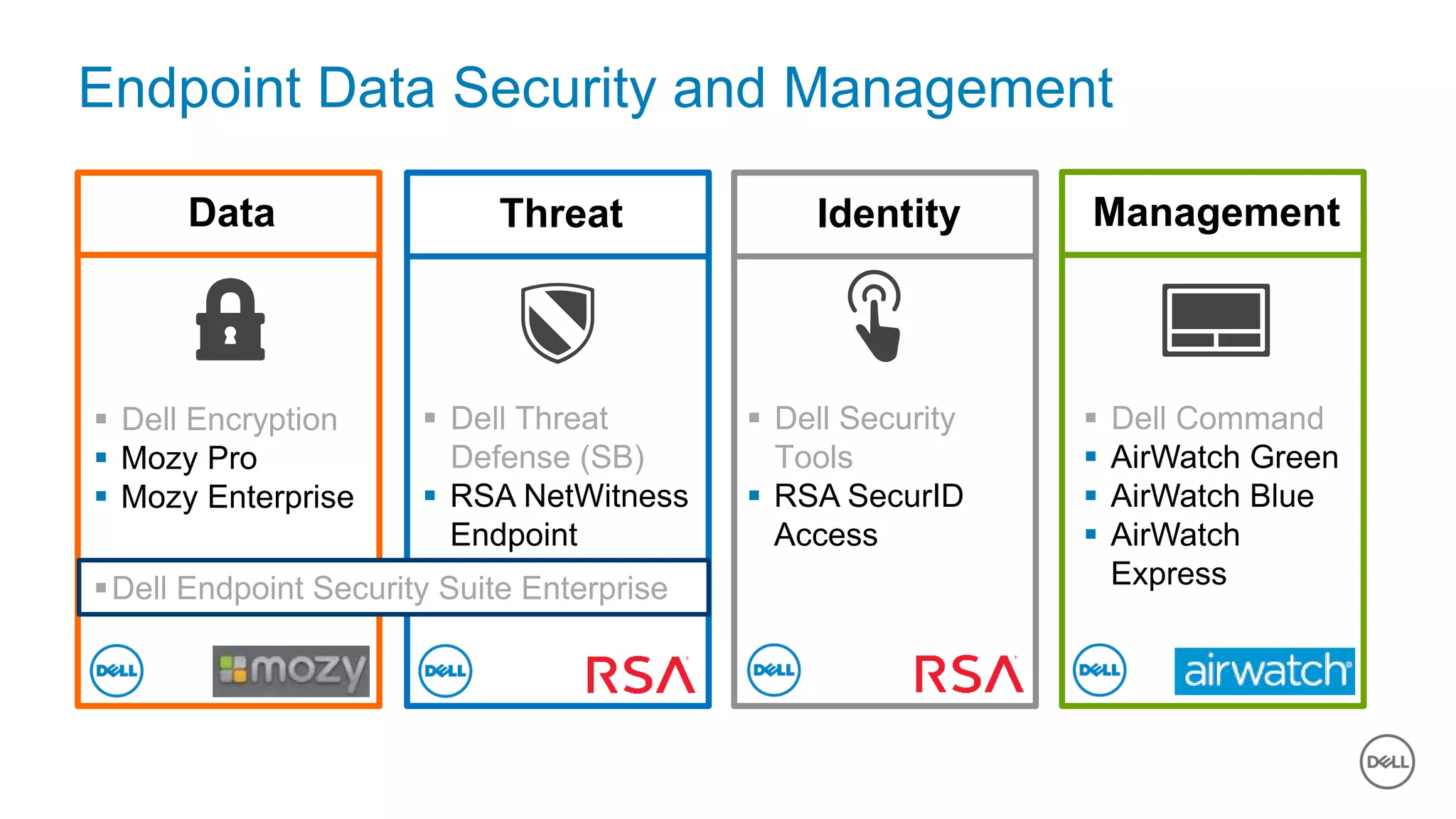
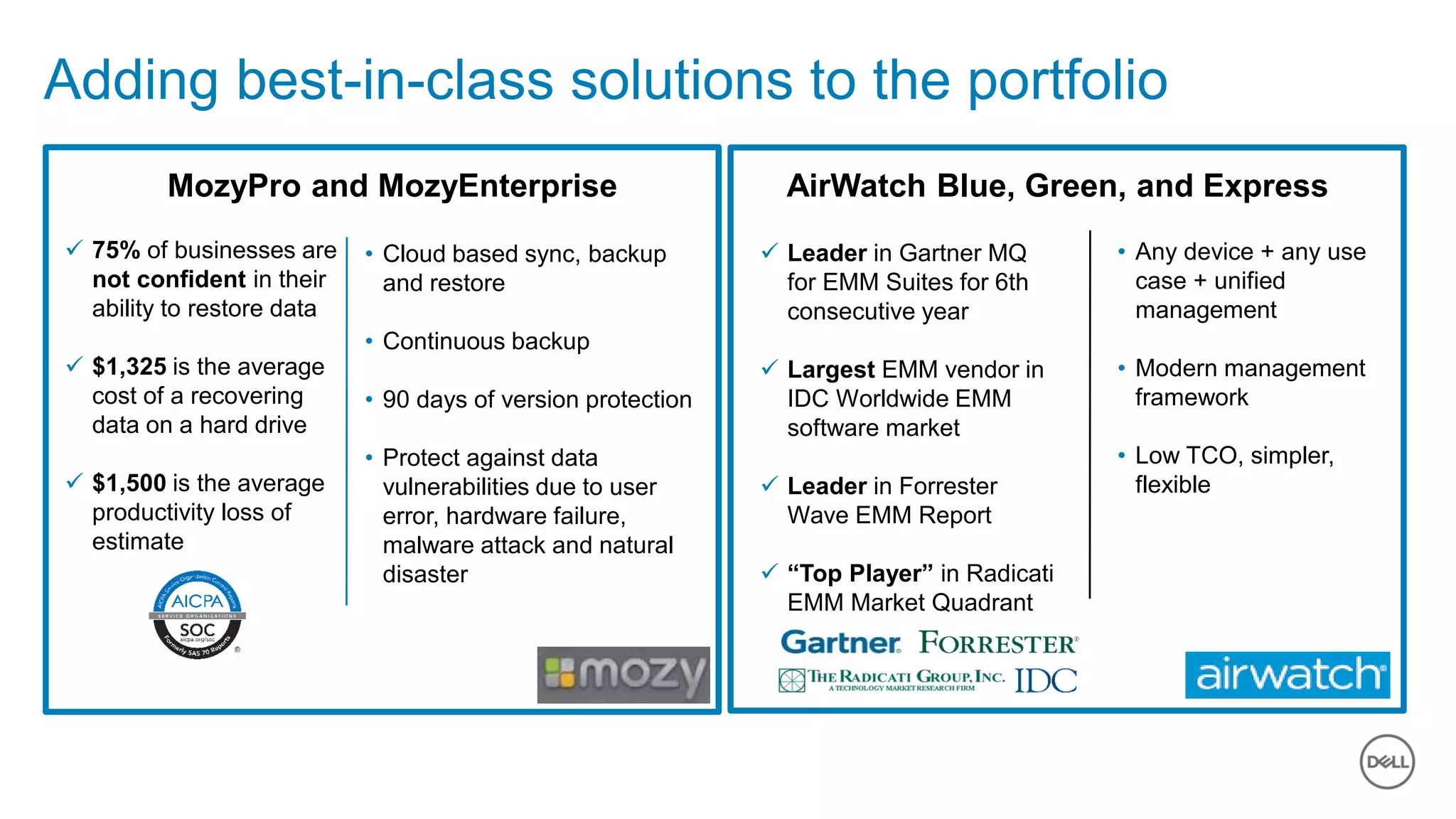
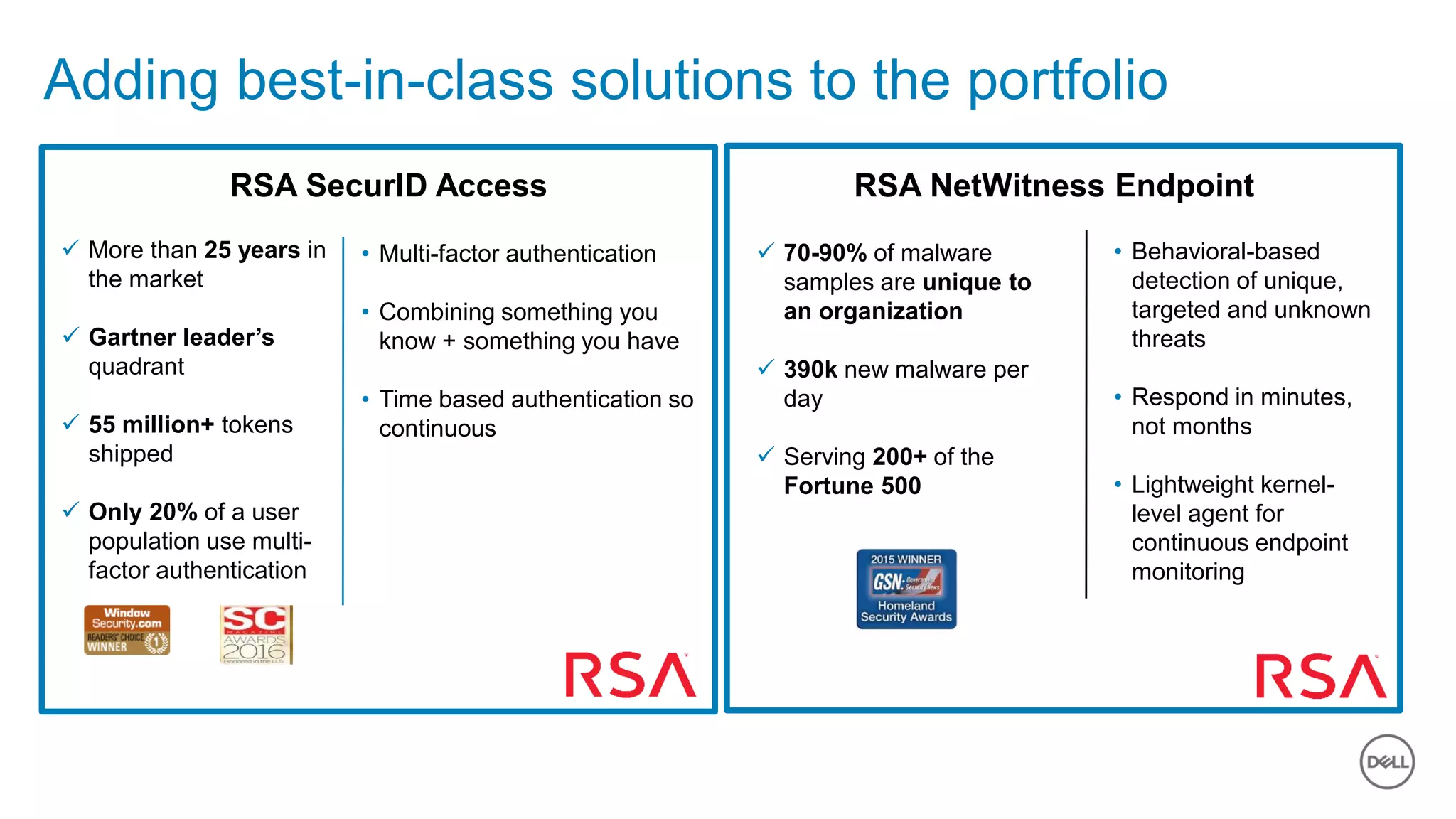
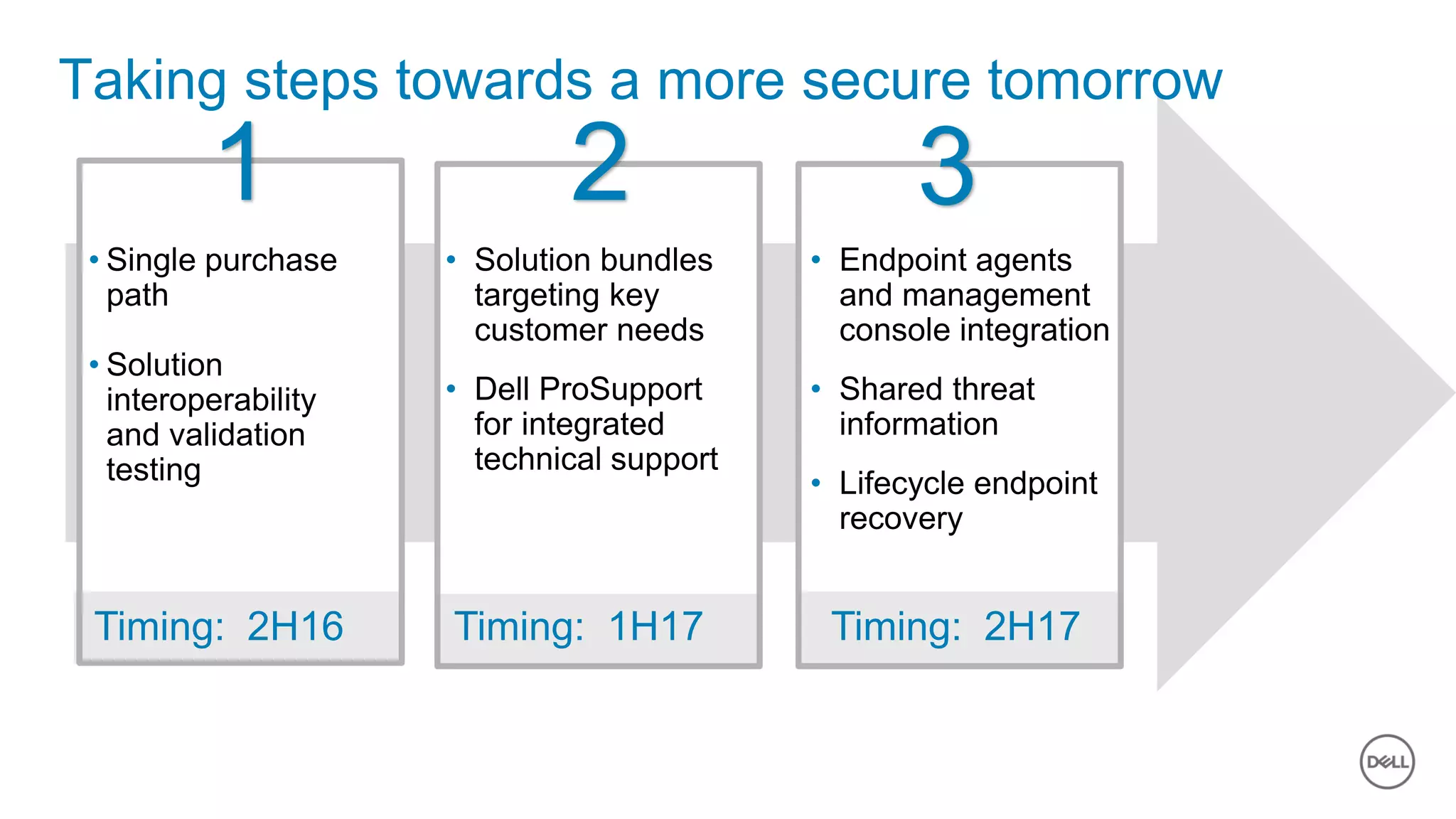
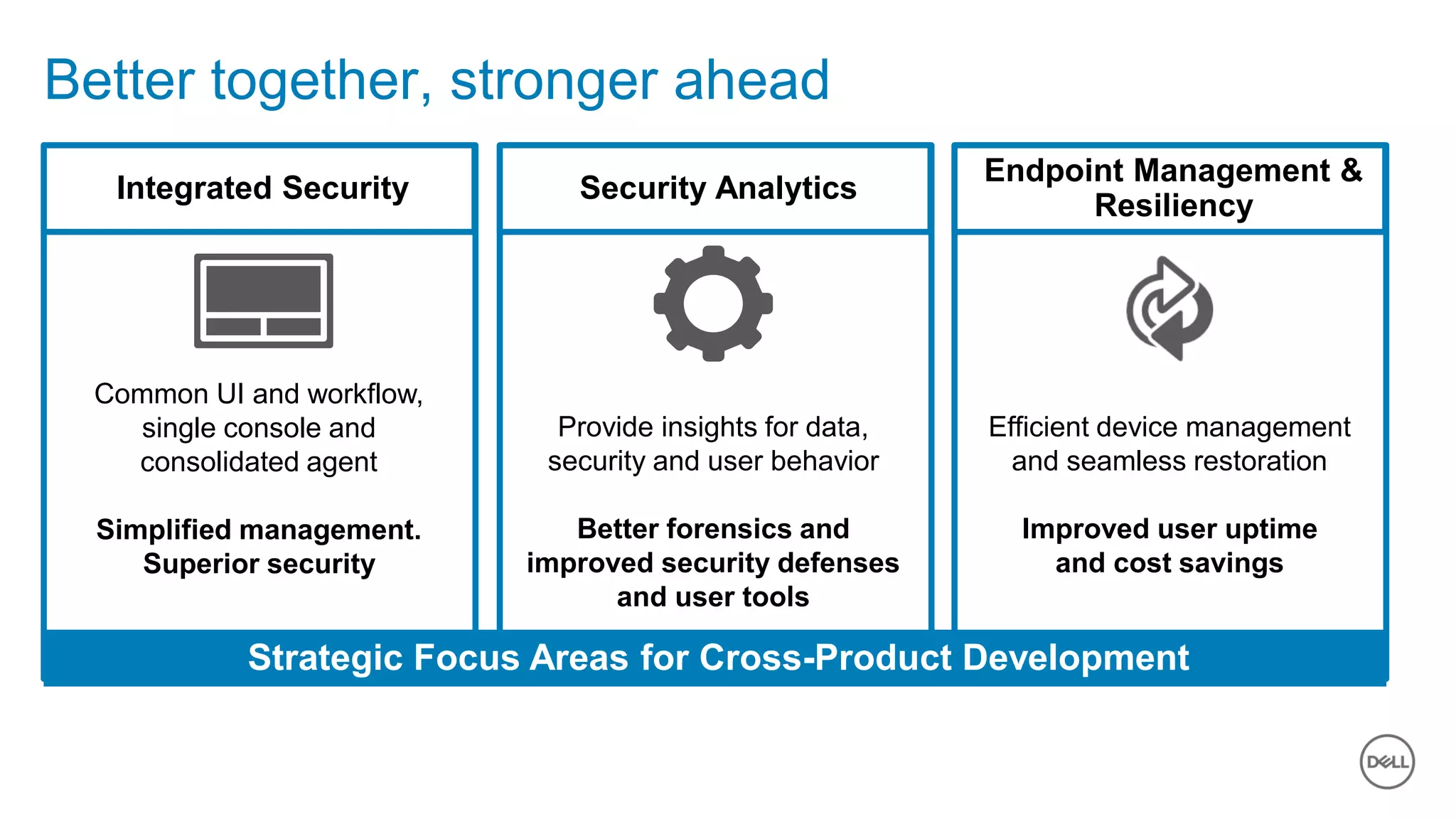
The document discusses the urgent need for improved cybersecurity measures due to the rising costs of cybercrime and data breaches. It outlines significant challenges and proposes a comprehensive cybersecurity strategy that includes securing endpoints, educating users, and utilizing a layered security approach. Additionally, it highlights Dell's portfolio of integrated security solutions designed to address current security threats effectively.