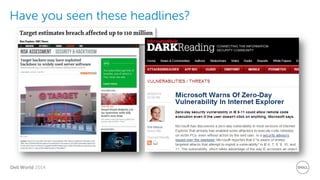
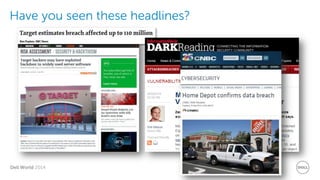
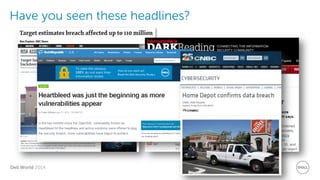
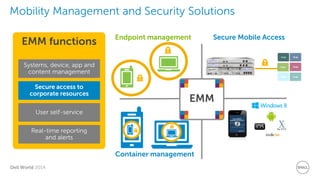
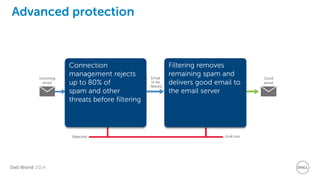
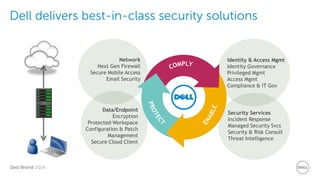
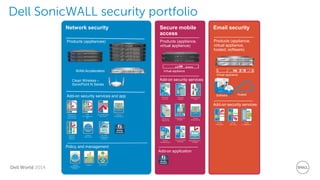
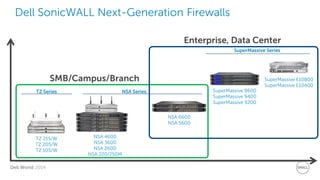
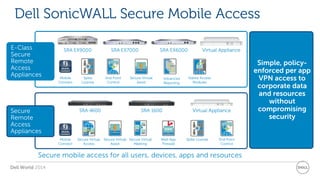
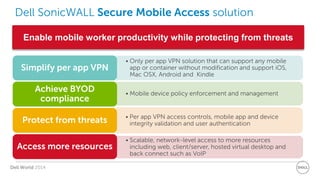
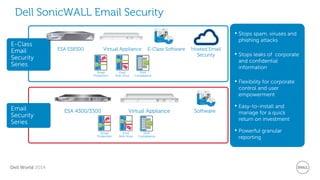
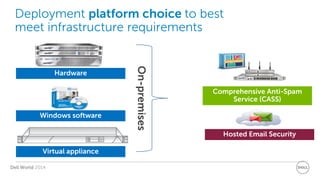
The document discusses Dell Security Solutions presented at Dell World 2014, highlighting the increasing cybersecurity threats such as malware and data breaches impacting businesses. It emphasizes the importance of next-generation firewalls, mobile security, and email security to protect corporate networks and data. Additionally, it showcases Dell's various security products and services designed to address contemporary security challenges and improve compliance and efficiency.