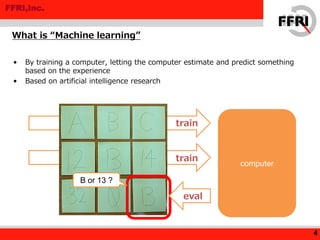
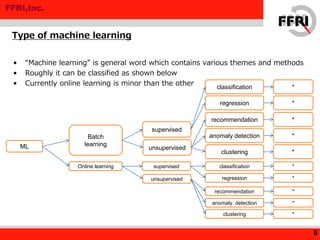
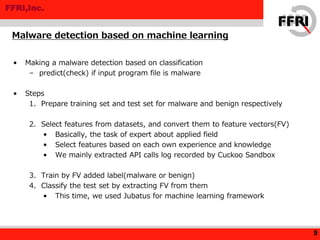
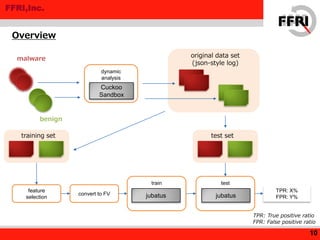
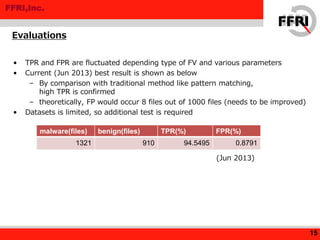
This document discusses applying machine learning techniques to malware detection. It begins with an overview of machine learning basics and types of machine learning. It then describes using machine learning for malware detection by extracting features from malware behavior logs, training a model, and classifying new files. Experimental results using the Jubatus framework achieved a 94.5% true positive rate and 0.88% false positive rate on test data. The document concludes that machine learning shows promise for malware detection and potentially other security applications.