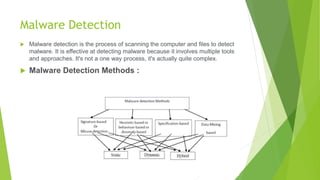
This document presents information on malware detection using machine learning. It defines malware and describes common types like viruses, adware, ransomware, rootkits, and spyware. It also outlines malware detection methods and symptoms. Machine learning algorithms like decision trees, SVM, random forest, and XGBoost are proposed for detection. Existing systems apply techniques like malware behavior analysis, classification, and neural networks. The document concludes machine learning can accurately detect malware and help overcome drawbacks of previous systems.