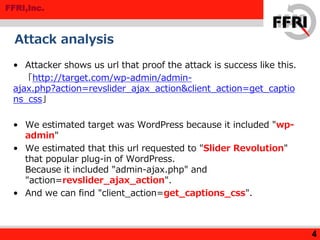
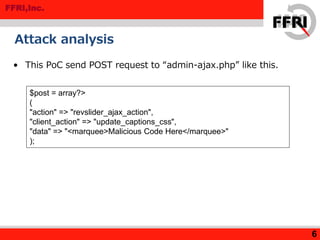
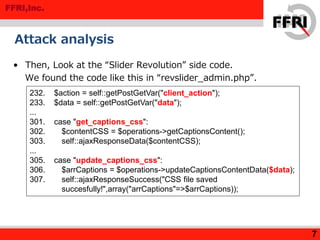
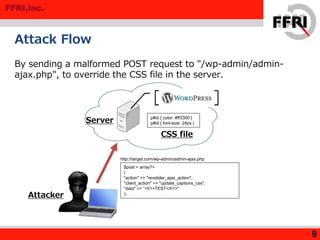
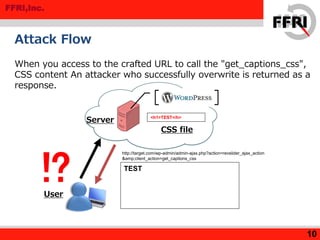
The document discusses a rise in web defacing attacks targeting WordPress and its plugins, notably the Slider Revolution, resulting in at least 18,000 affected sites. It analyzes the techniques used by attackers to exploit vulnerabilities and inject malicious code, emphasizing the ease of targeting popular products through their plugins. Recommendations for countermeasures include updating plugins, limiting access to wp-admin, and disabling certain functions to mitigate risks.