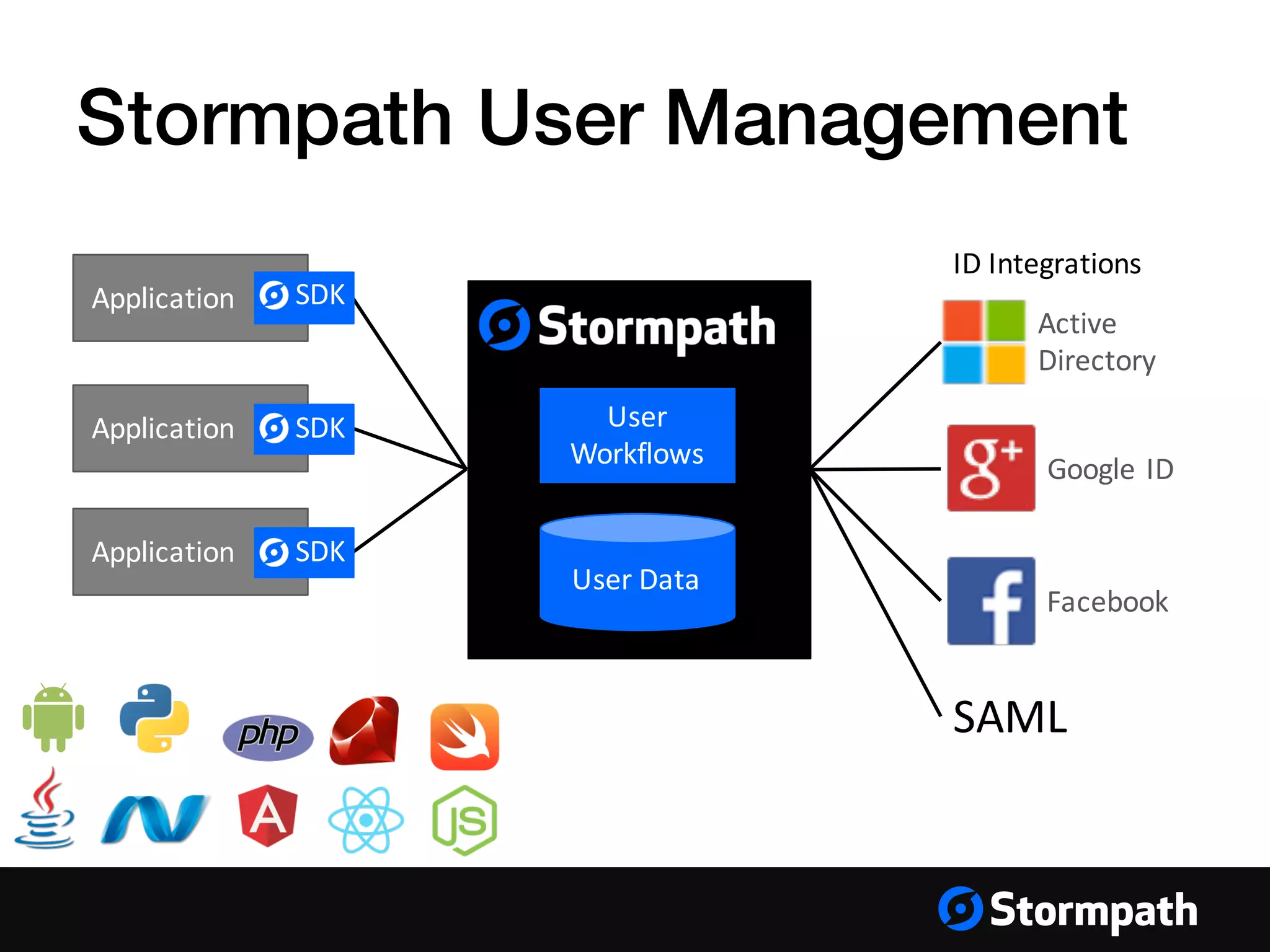
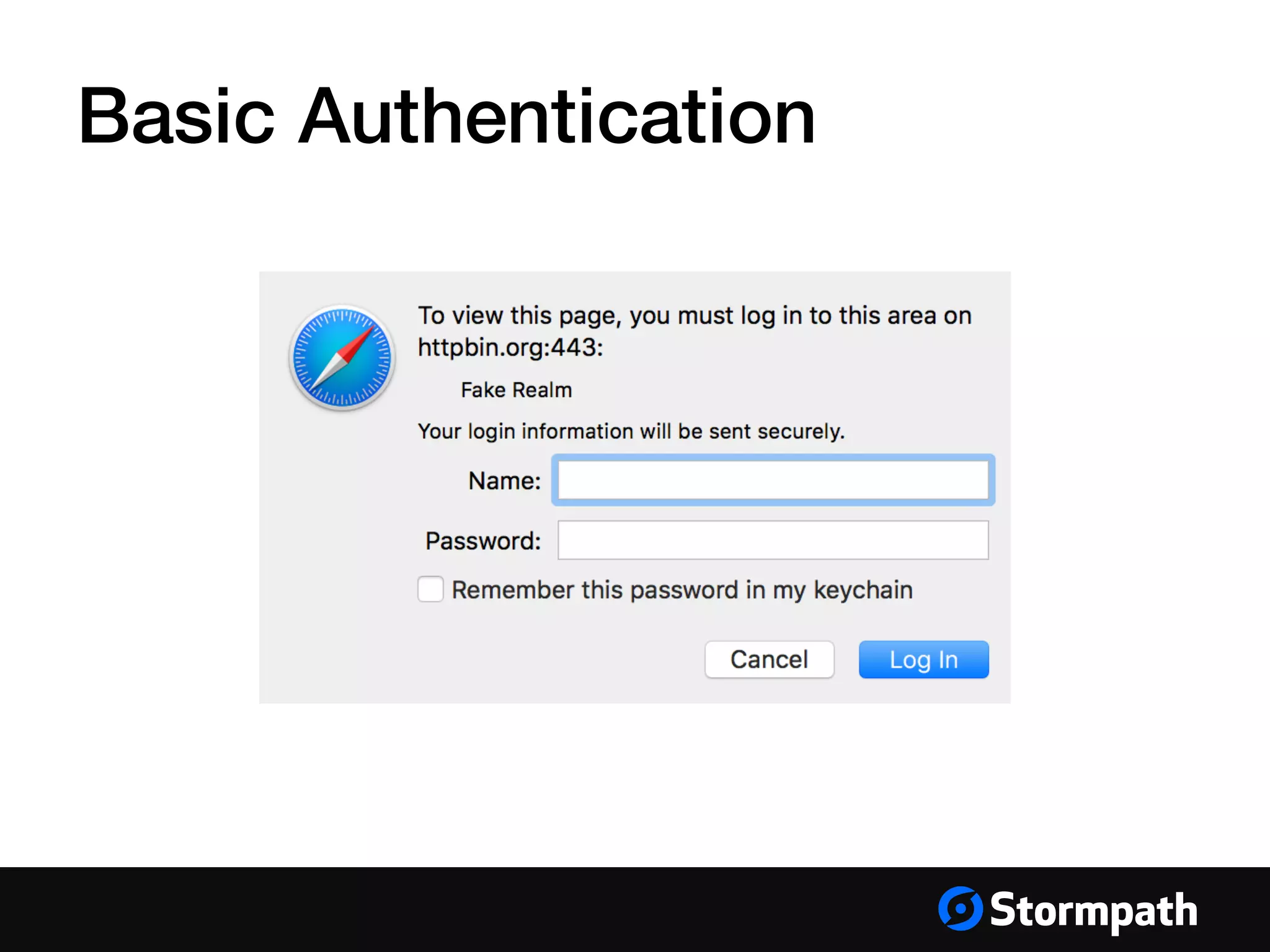
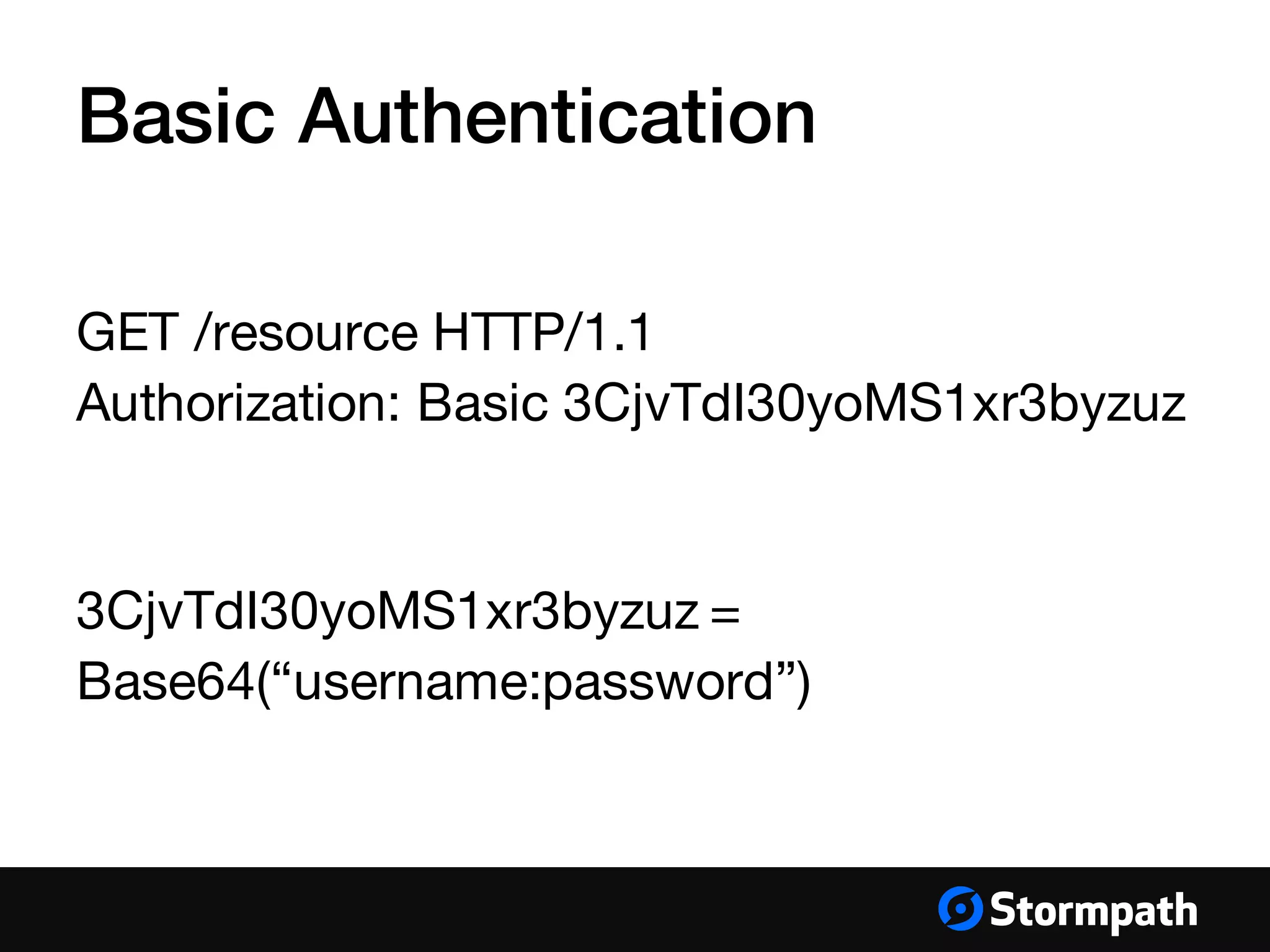
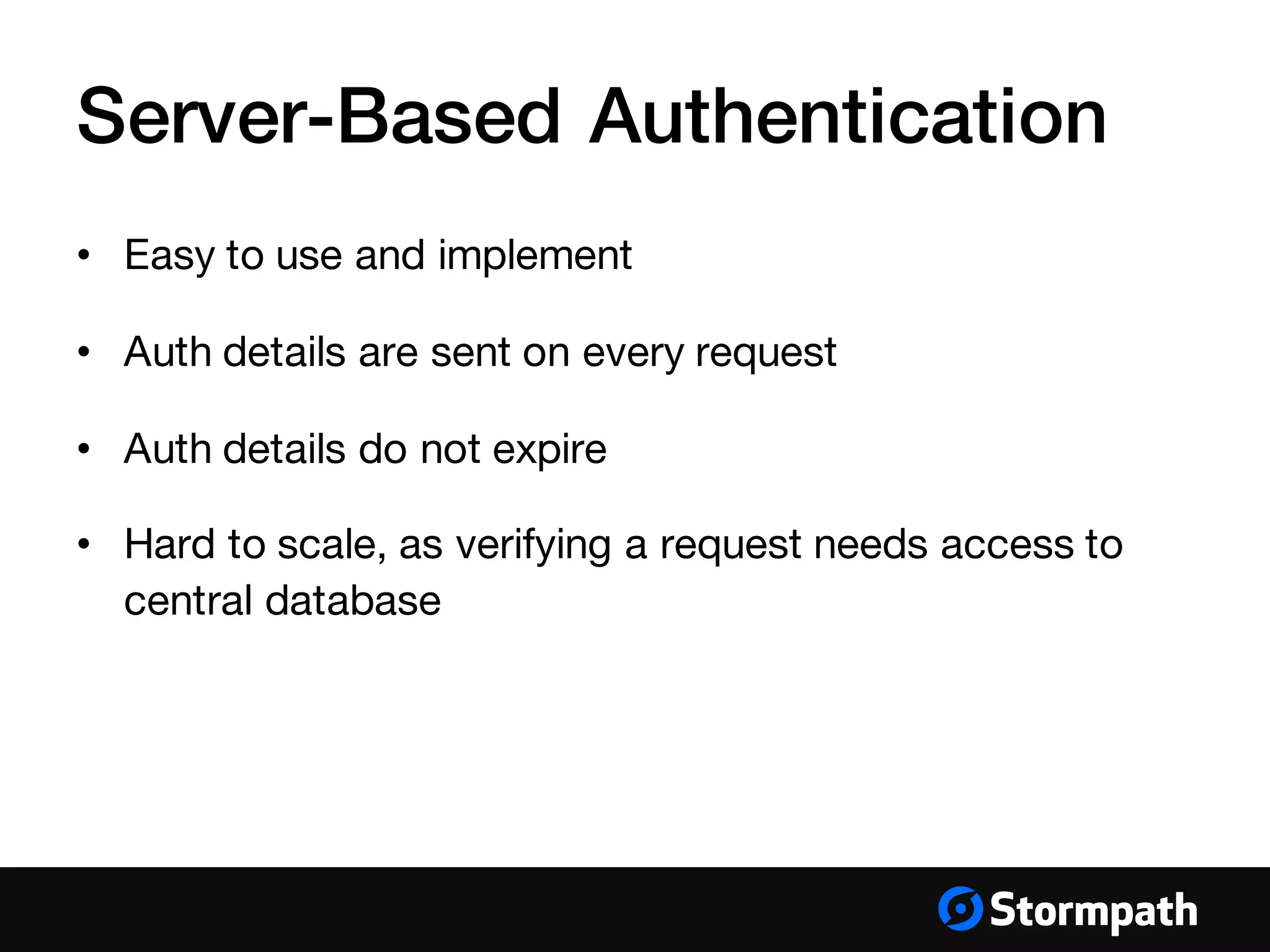
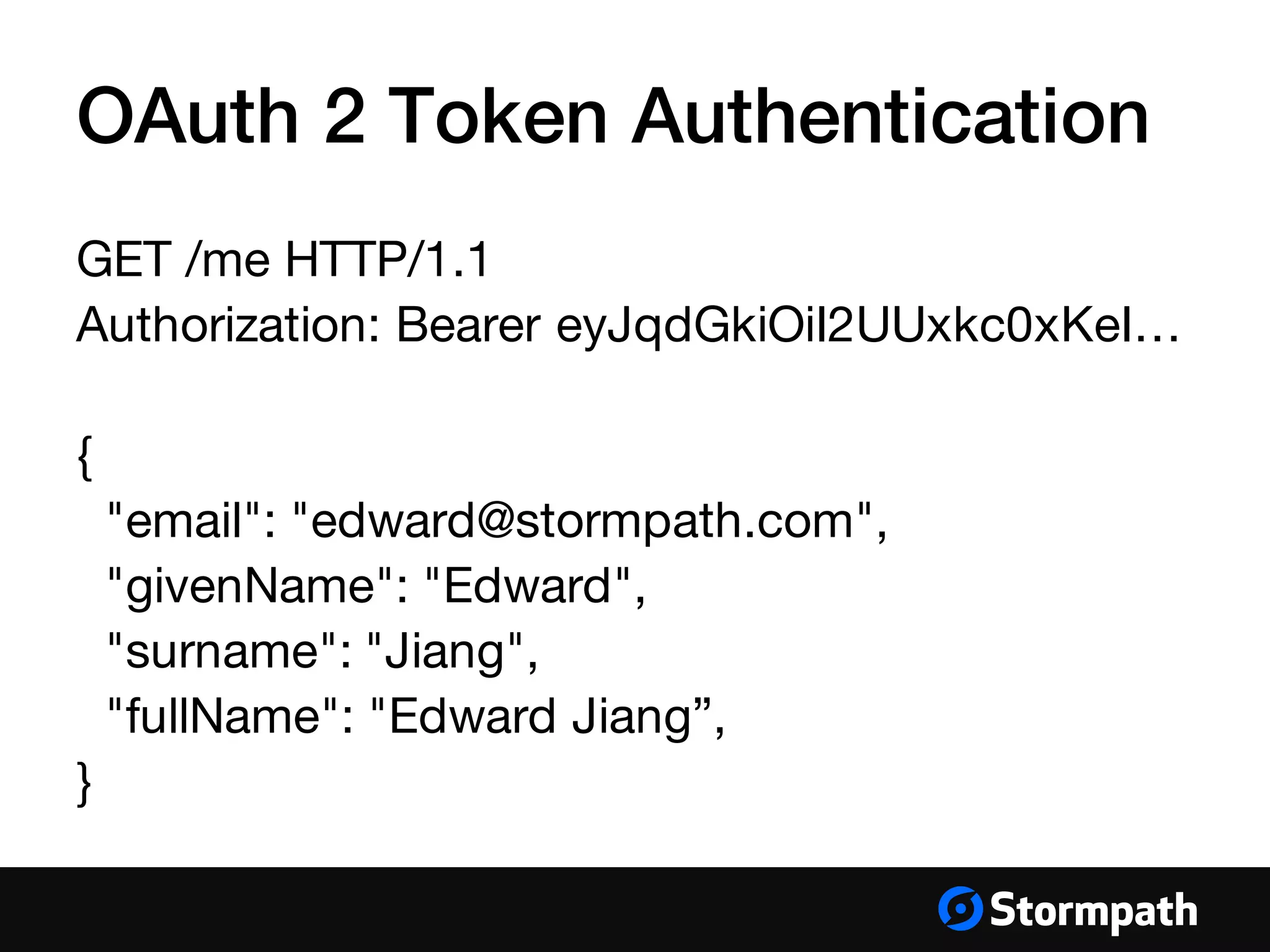
The document provides an overview of mobile authentication strategies for iOS applications, covering essential topics such as Stormpath services, common authentication methods, and OAuth 2 token authentication. It emphasizes the importance of security, scalability, and provides resources for implementing authentication in iOS apps. The presentation includes a Q&A session to address further inquiries.