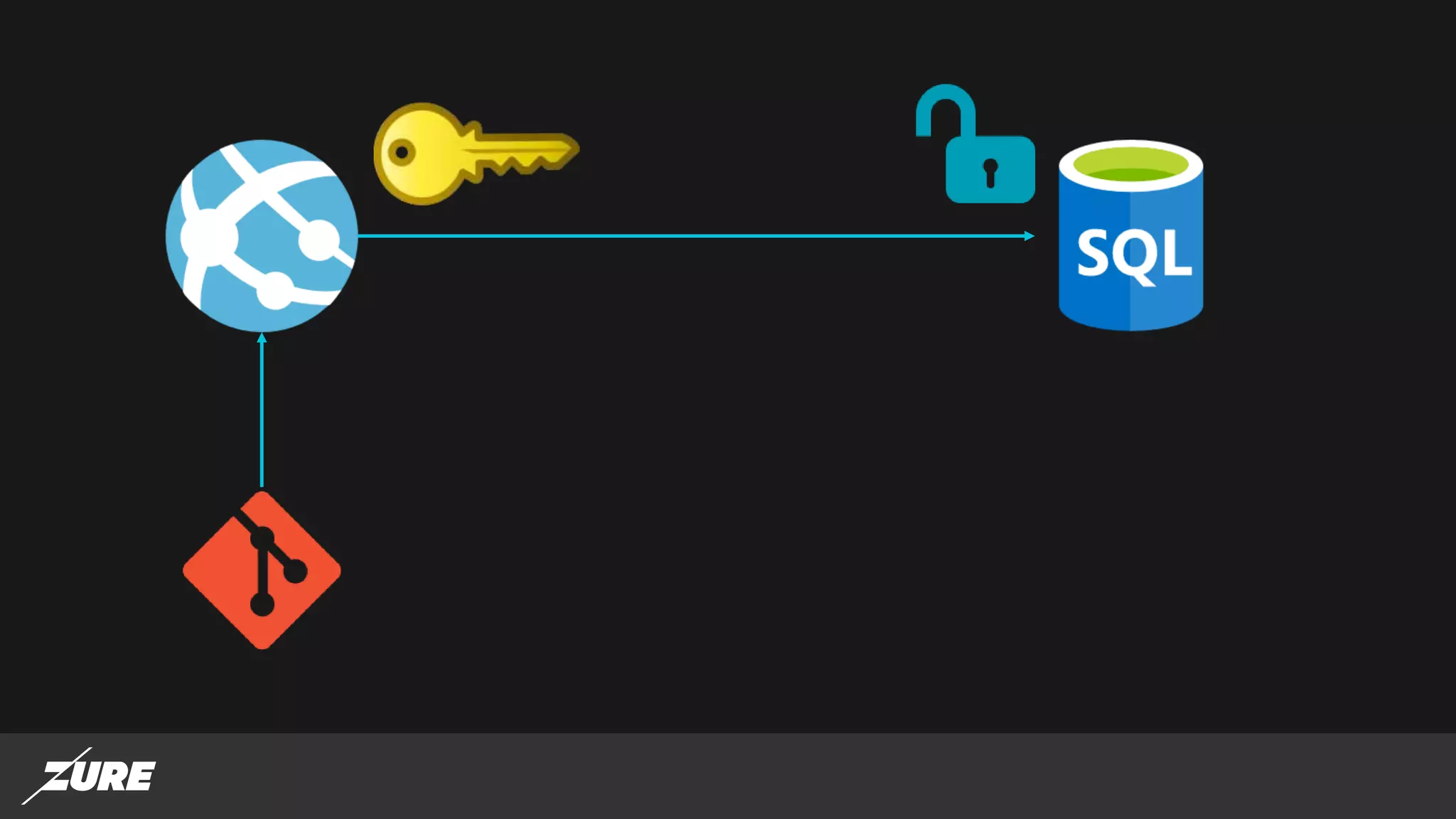
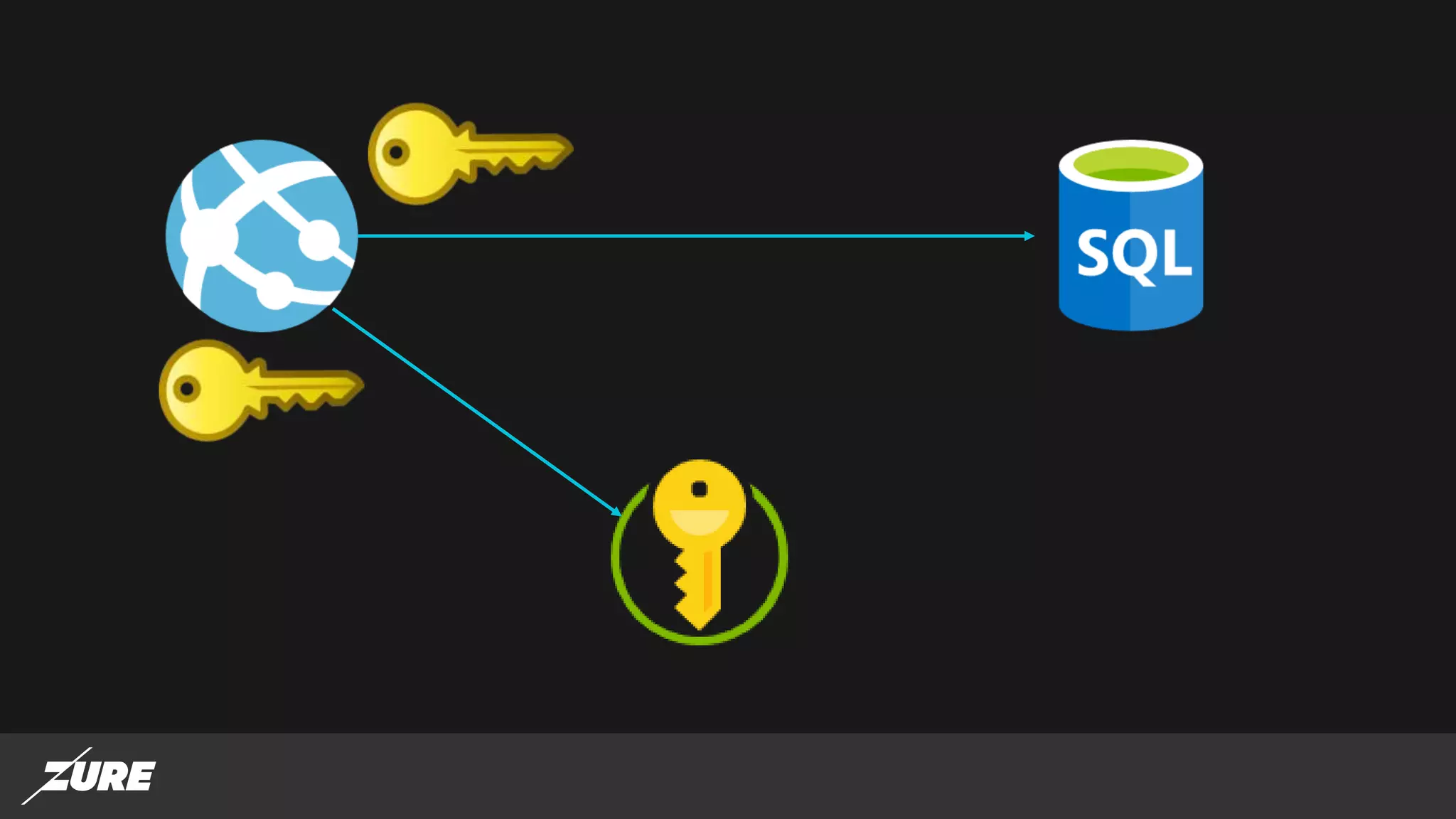
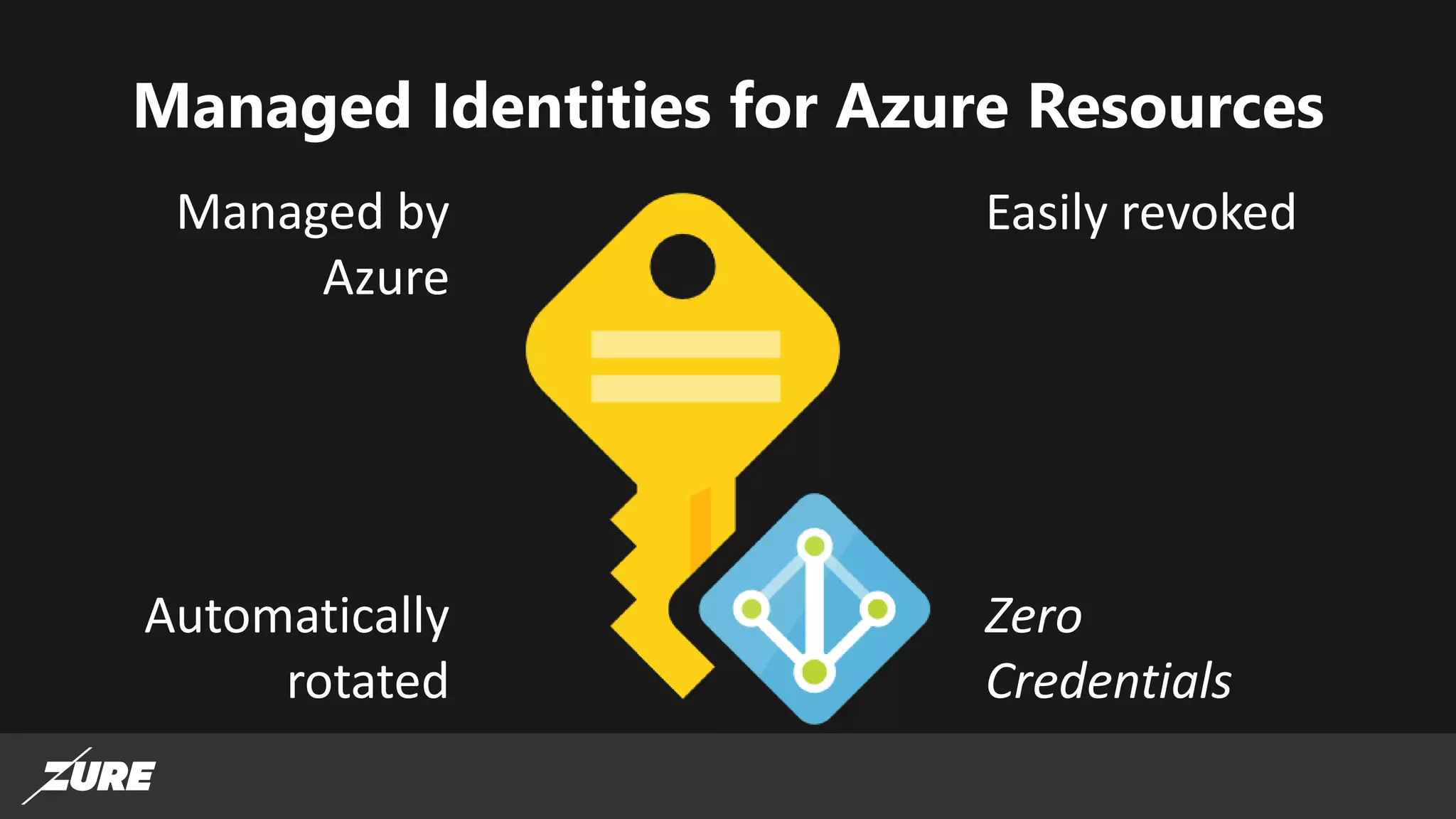
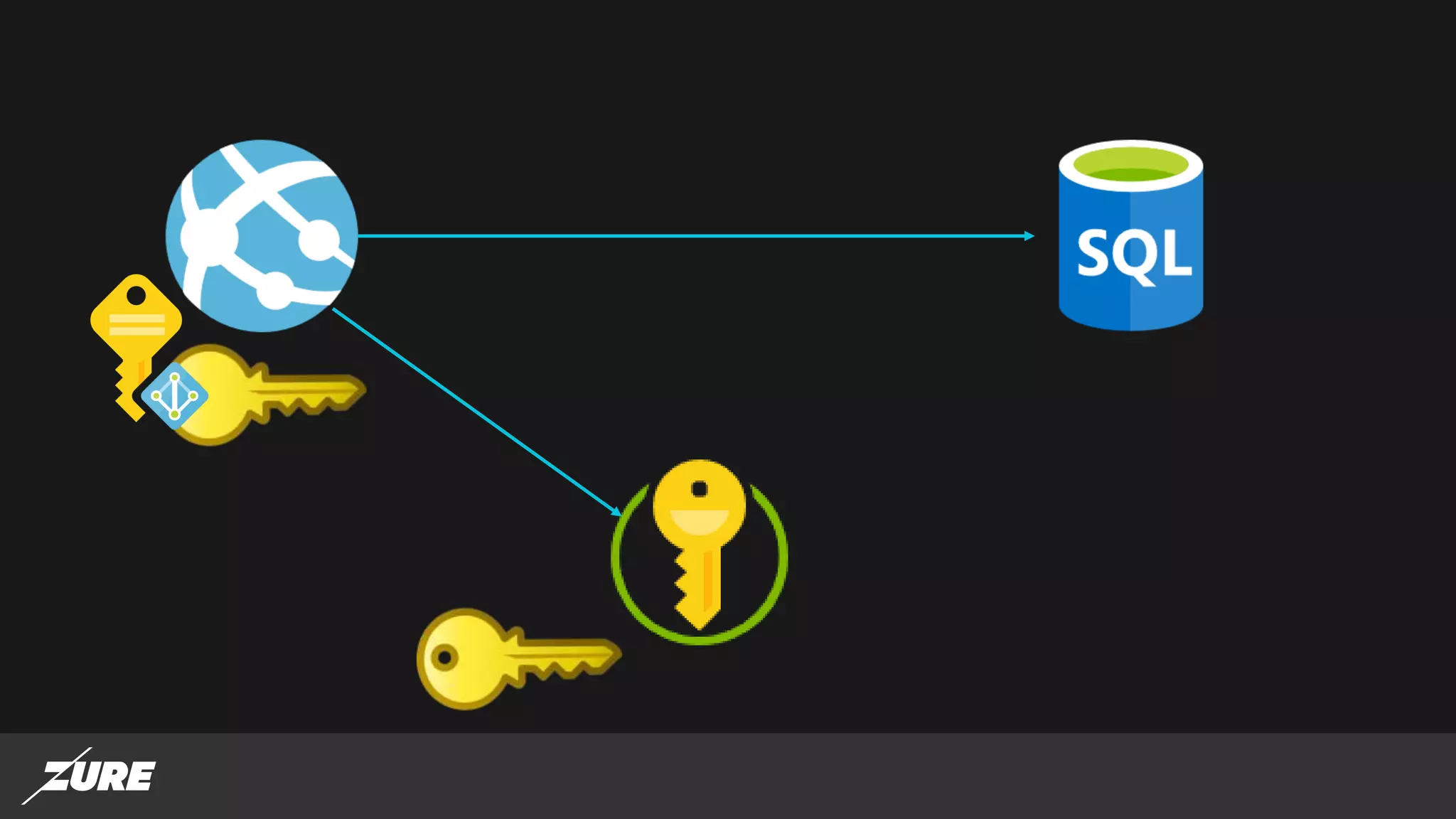
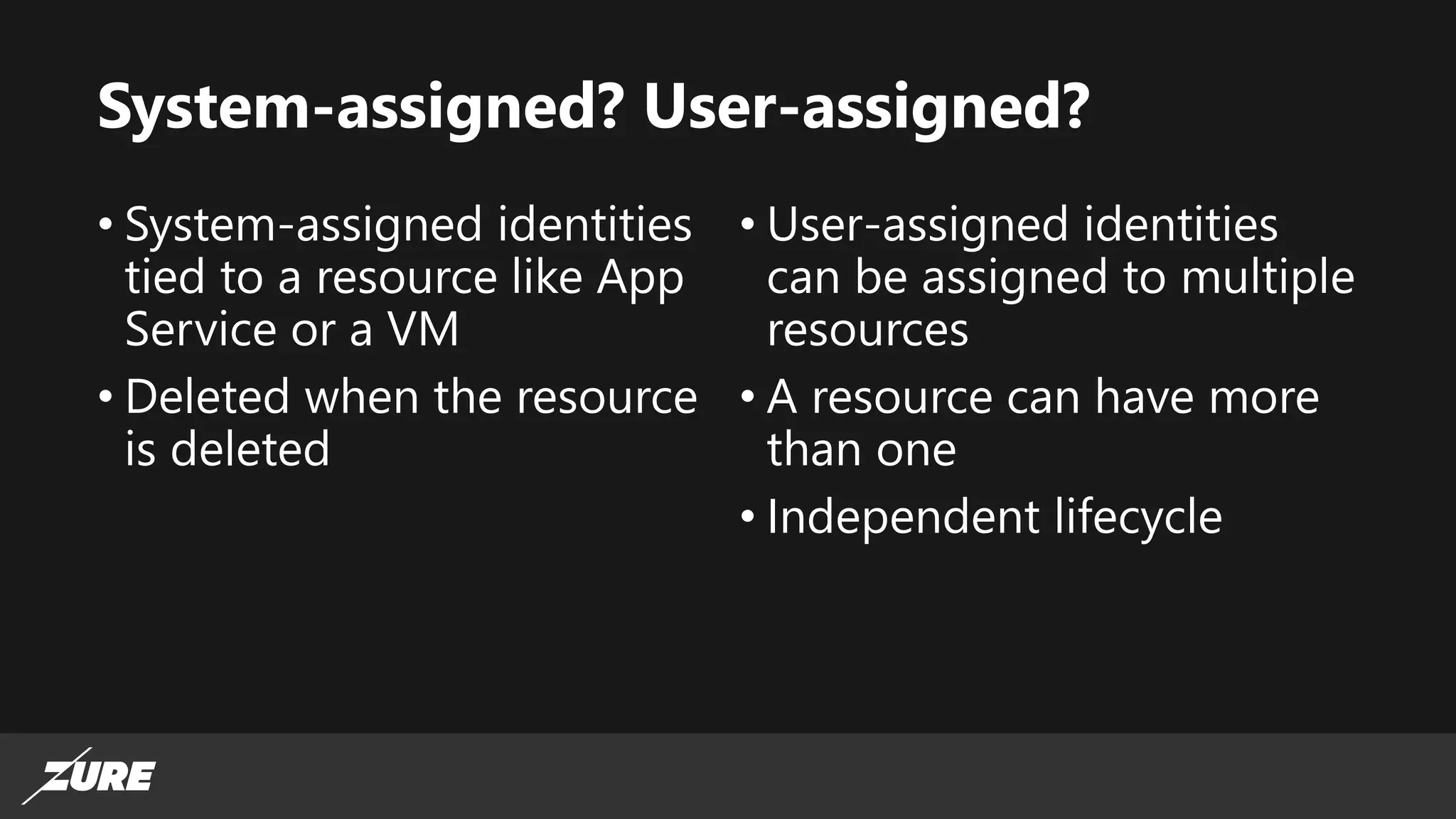
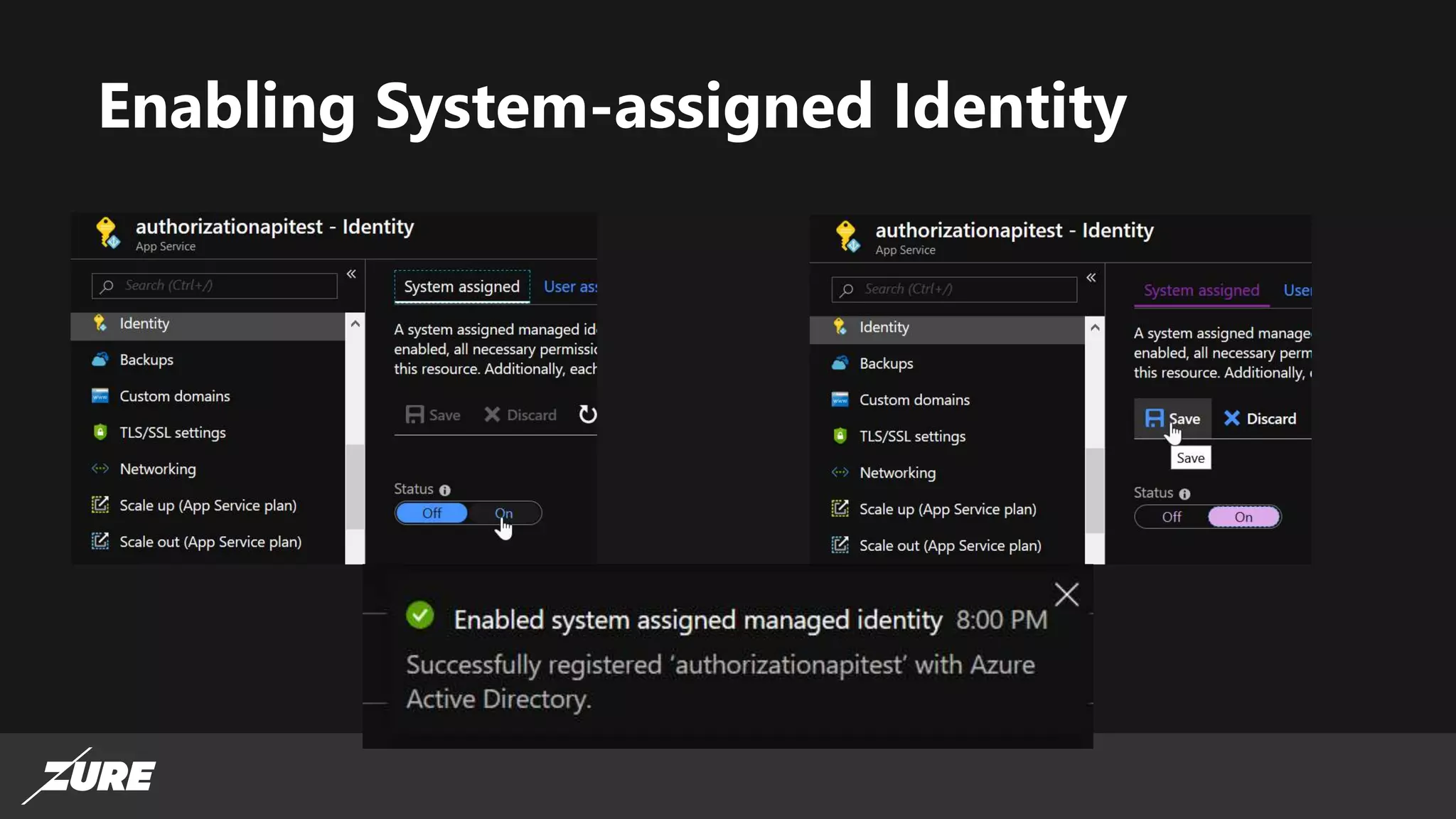
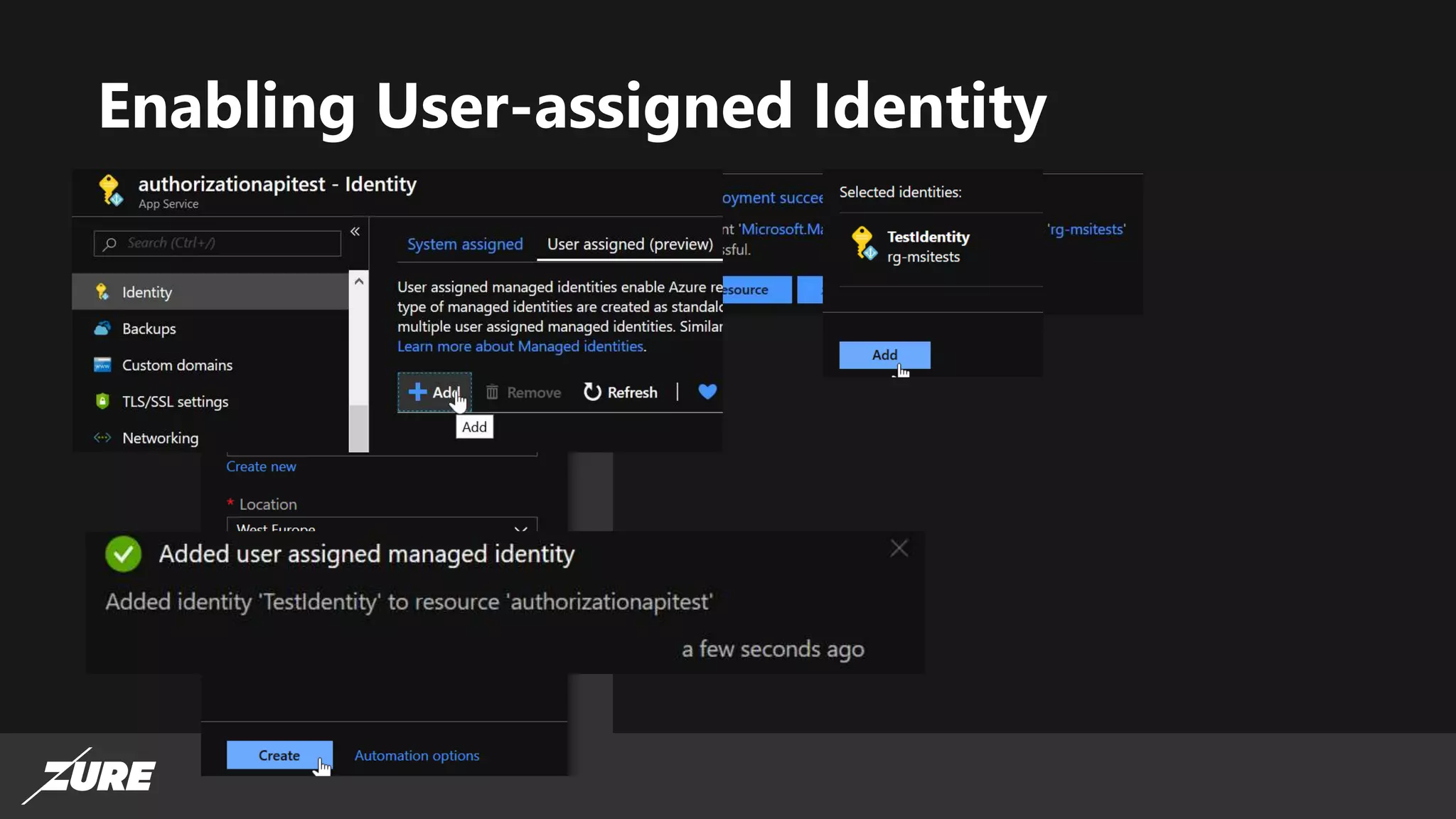
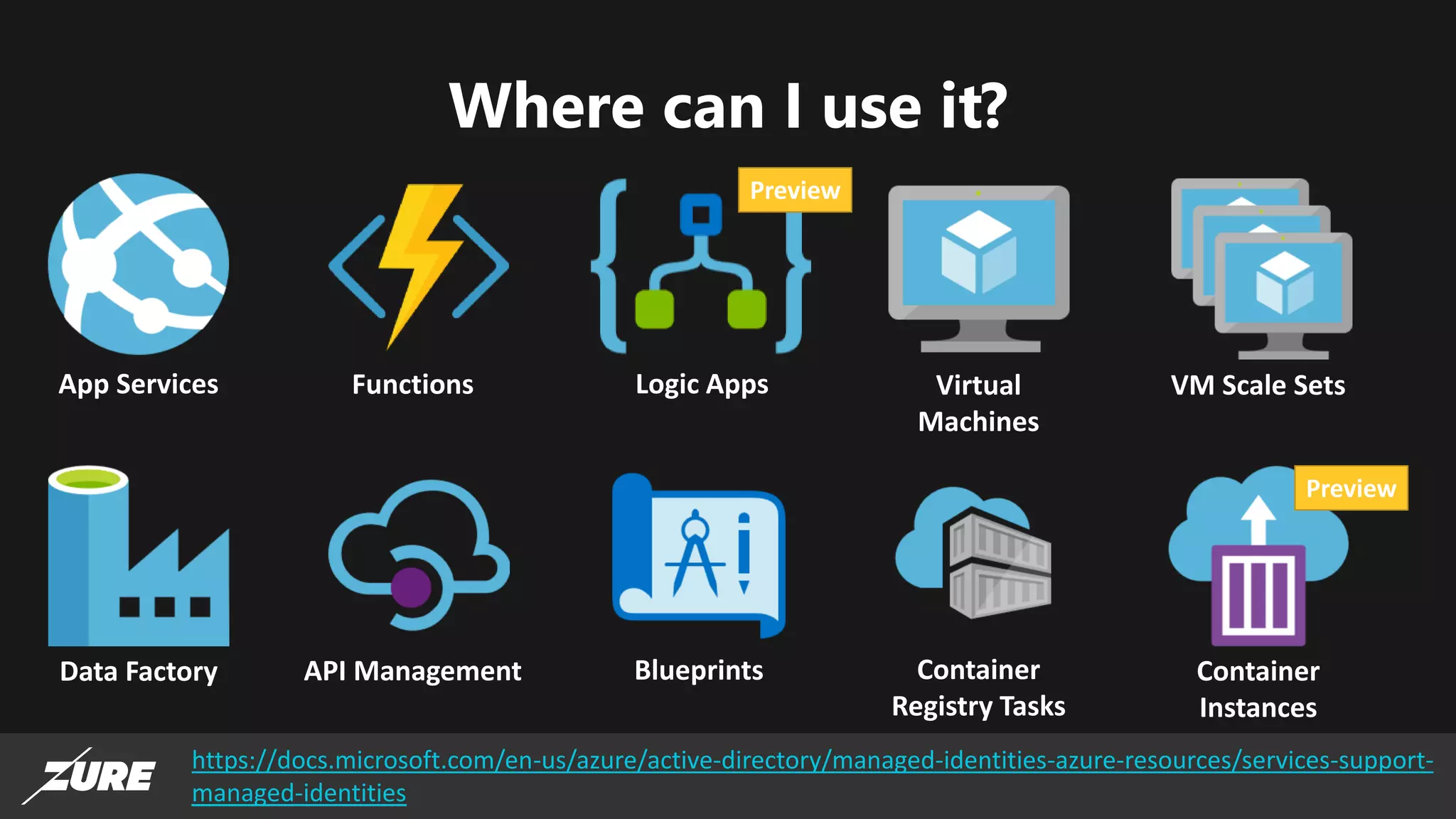
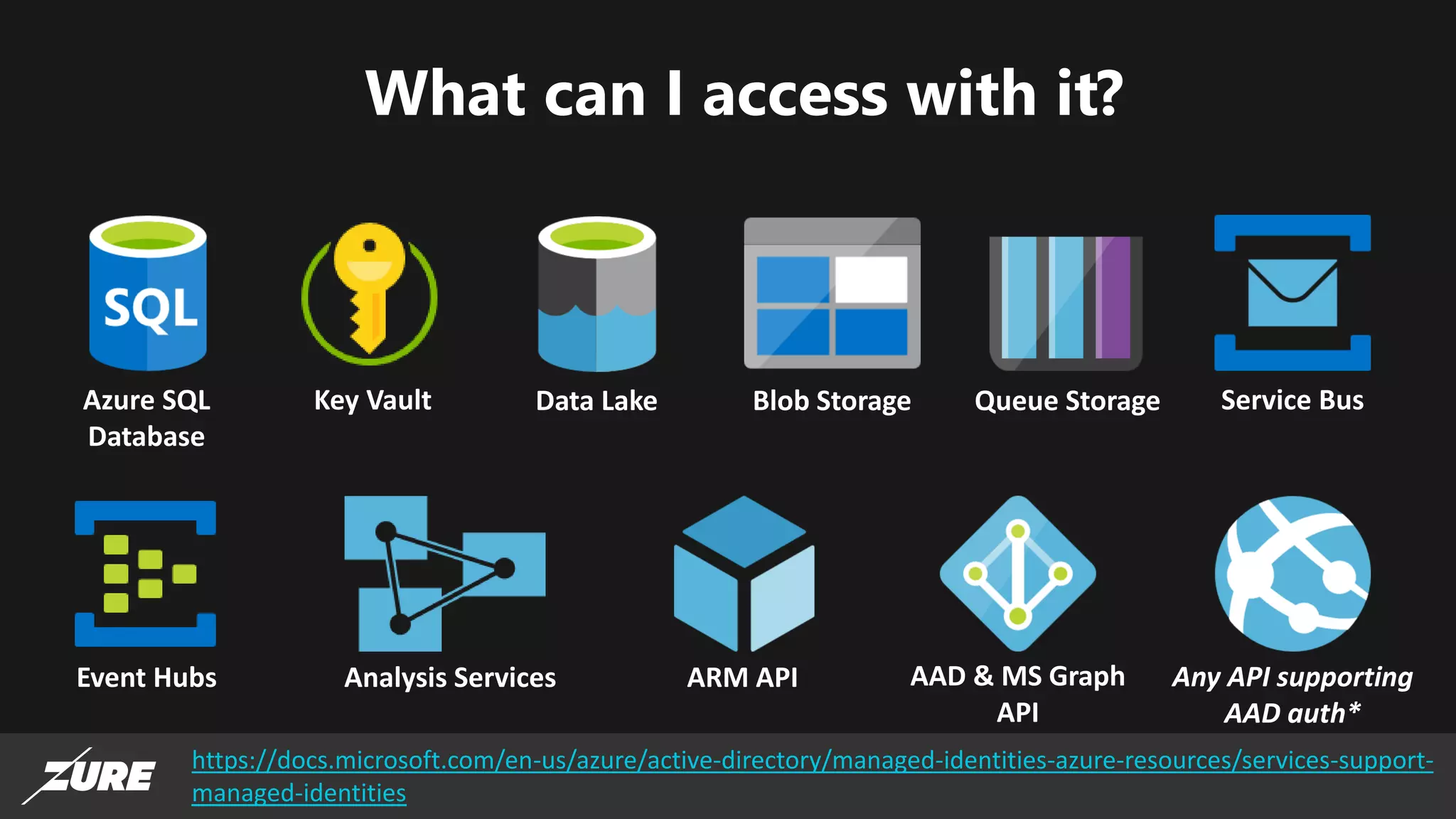
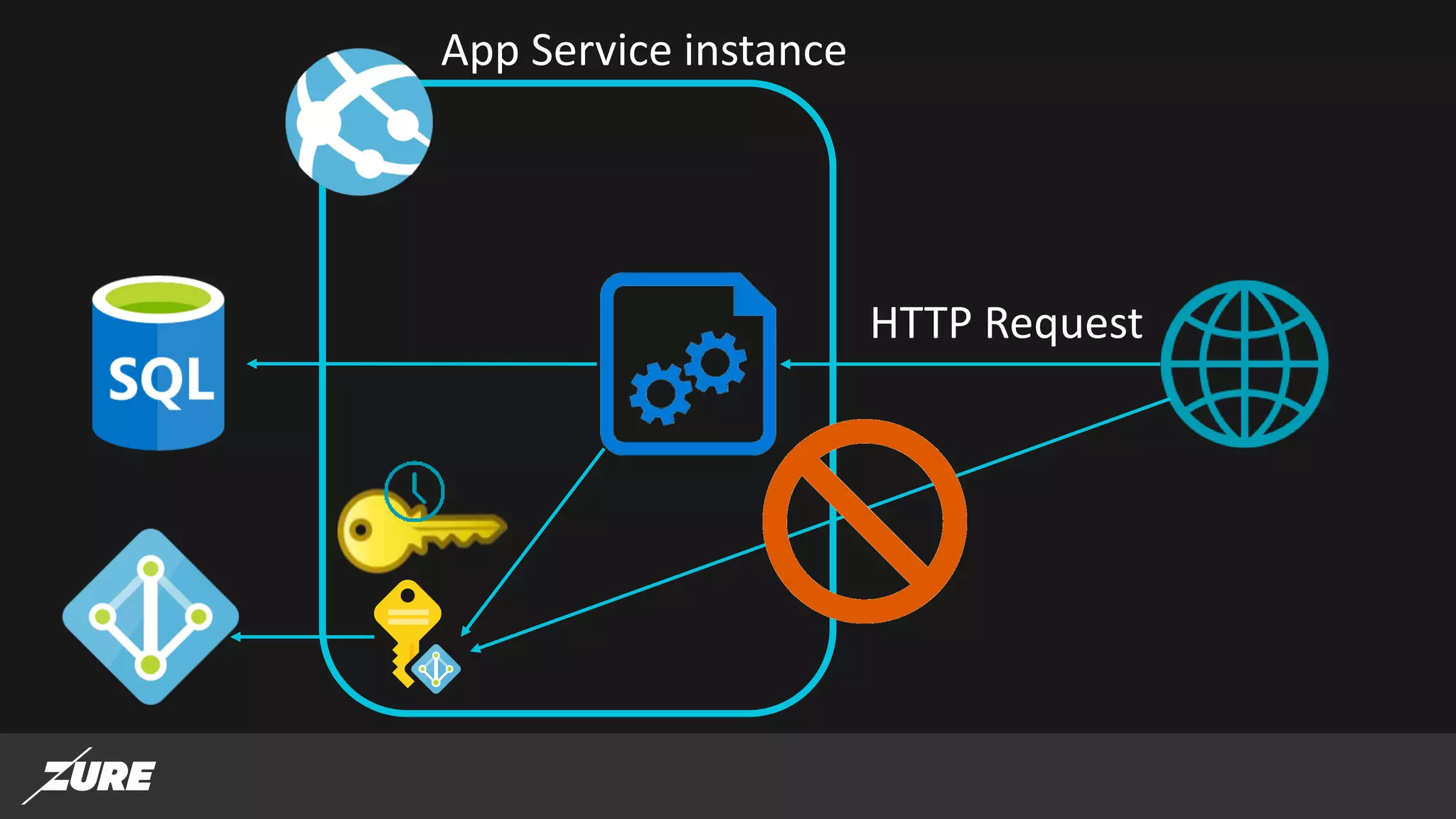
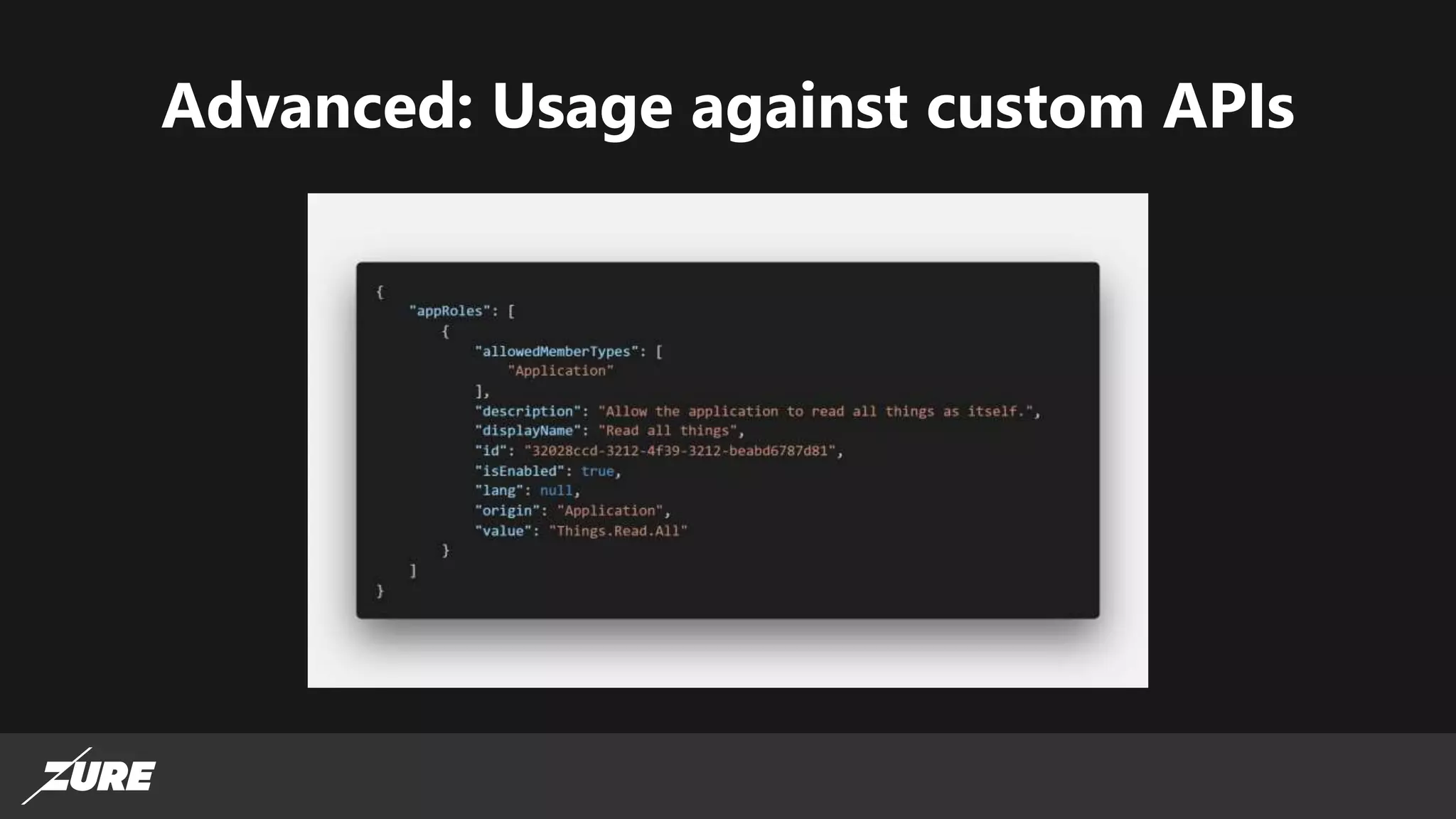
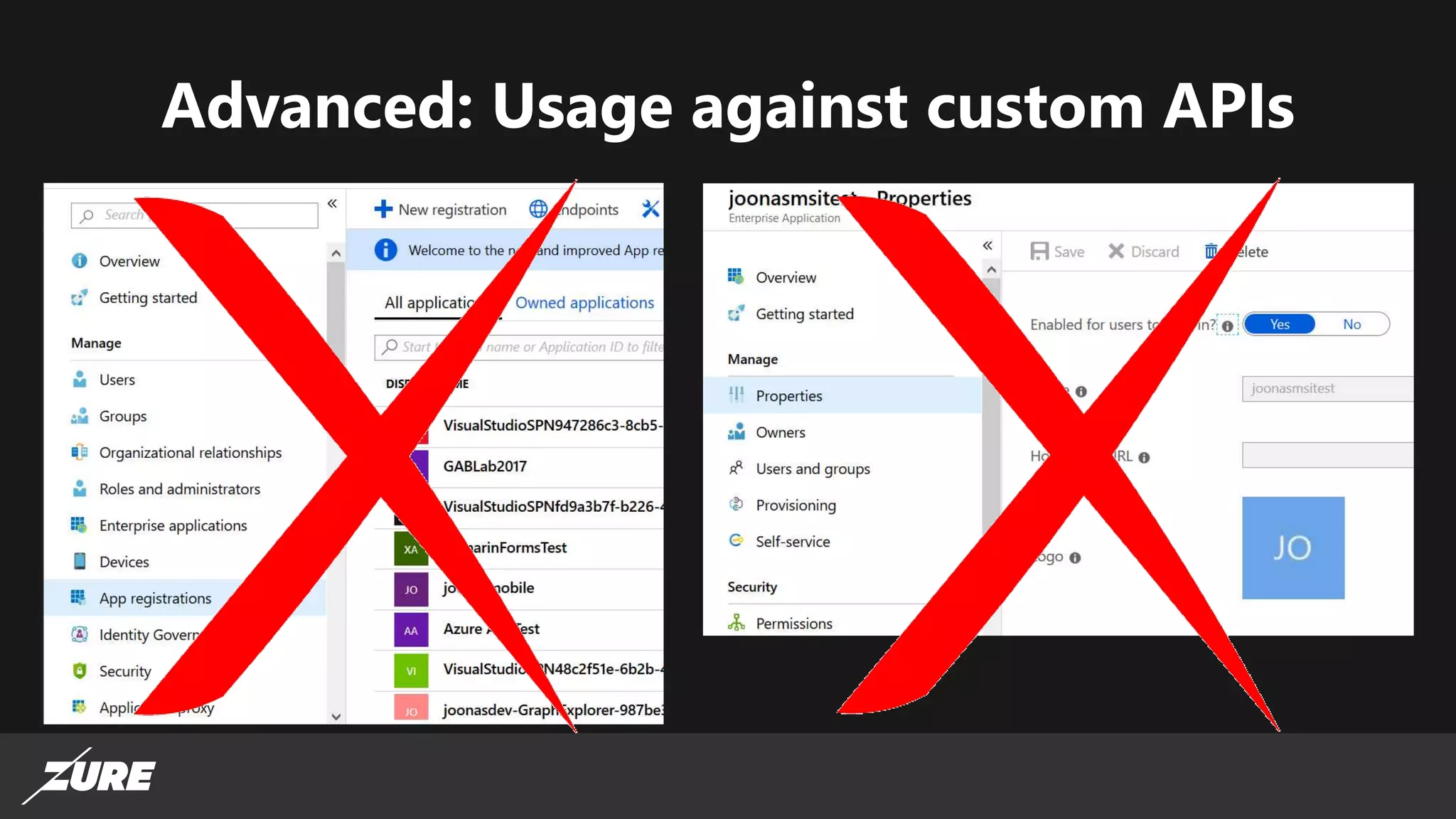
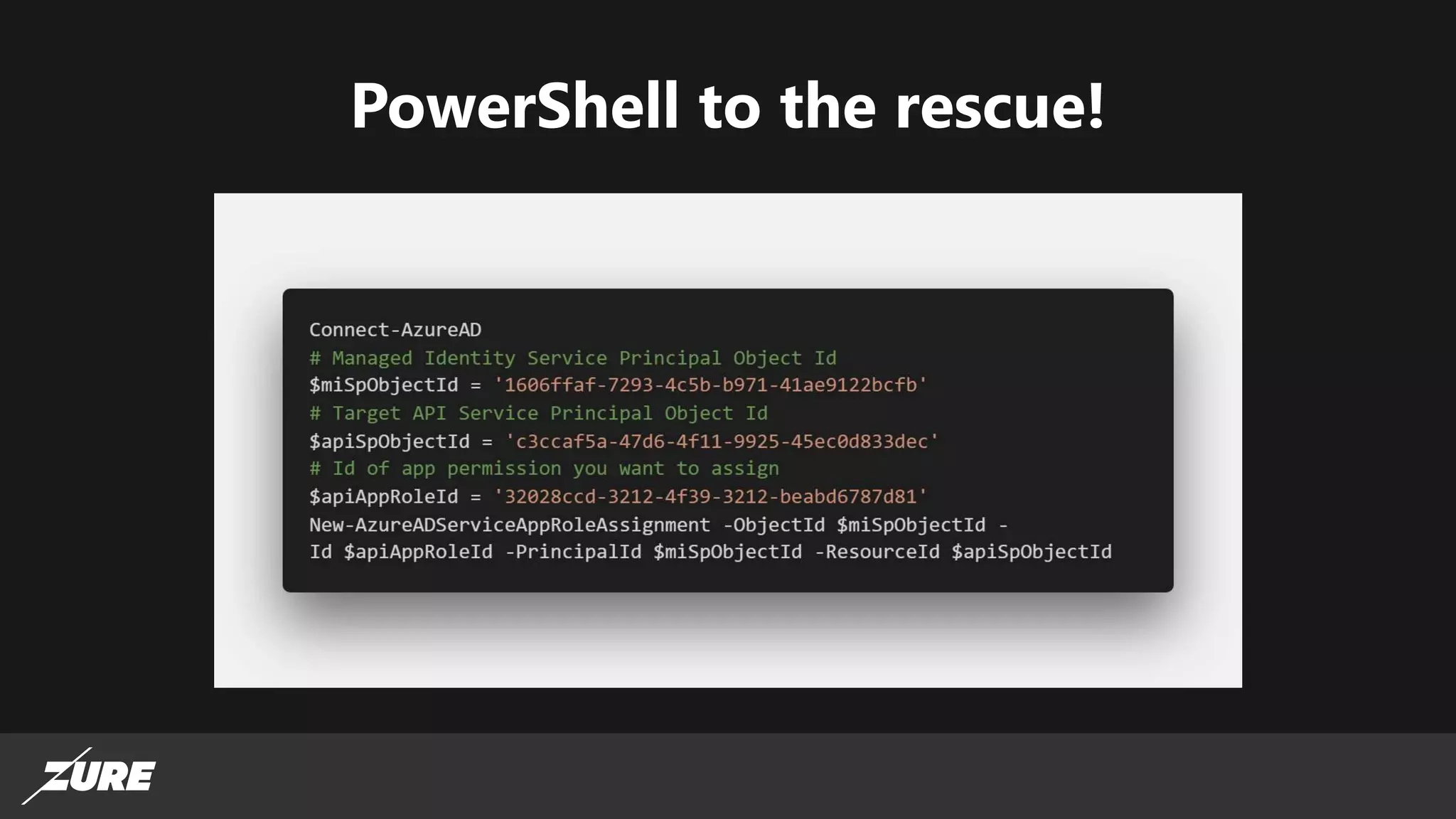
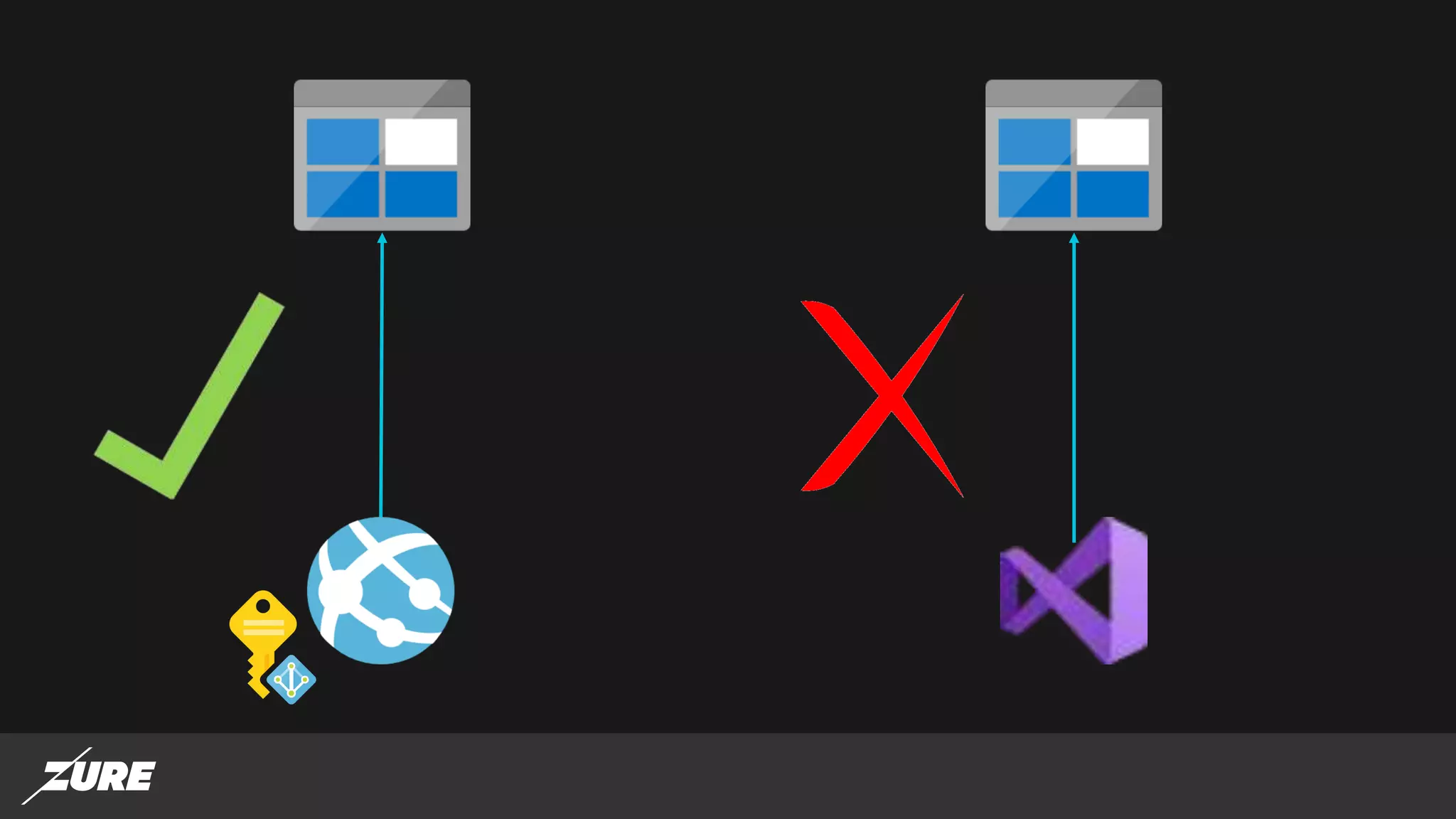
The document discusses the use of managed identities for Azure resources, highlighting their ability to simplify credential management by automating key rotation, revocation, and management, which is cost-free. It details system-assigned and user-assigned identities, their lifecycle, and various applications where managed identities can be utilized securely. Recommendations for development with managed identities, including tools and methods for accessing services that support Azure AD authentication, are also provided.