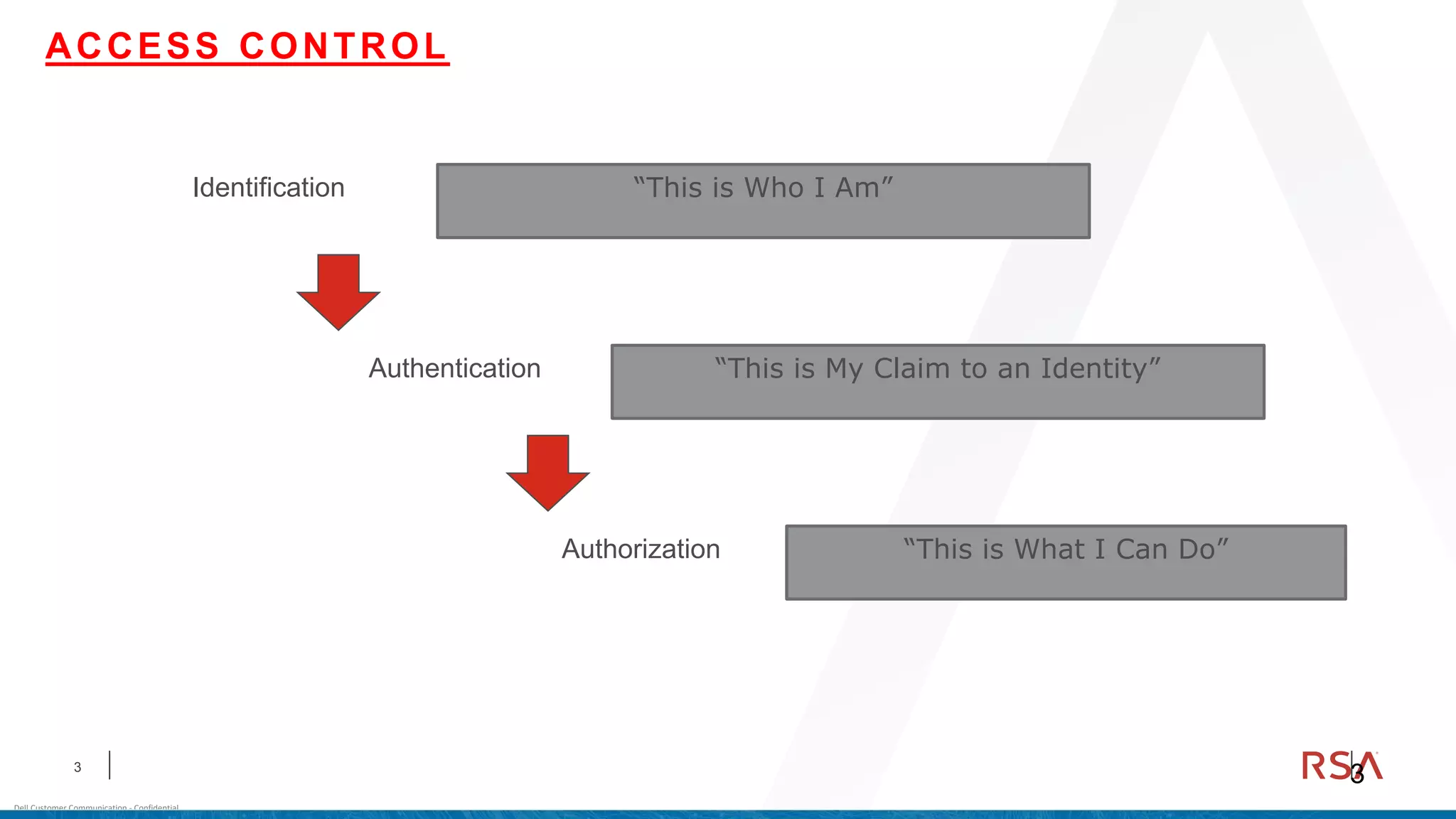
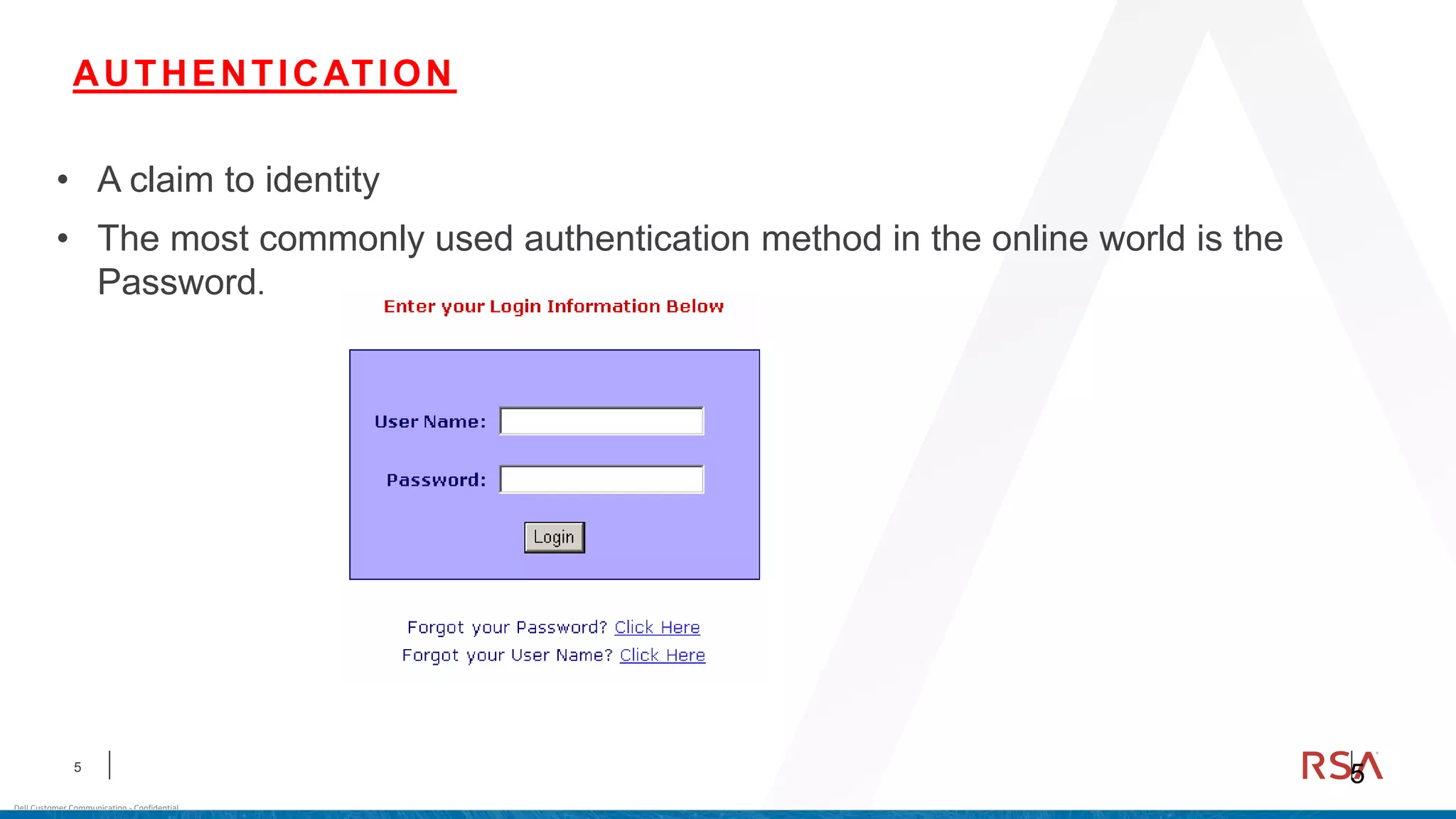
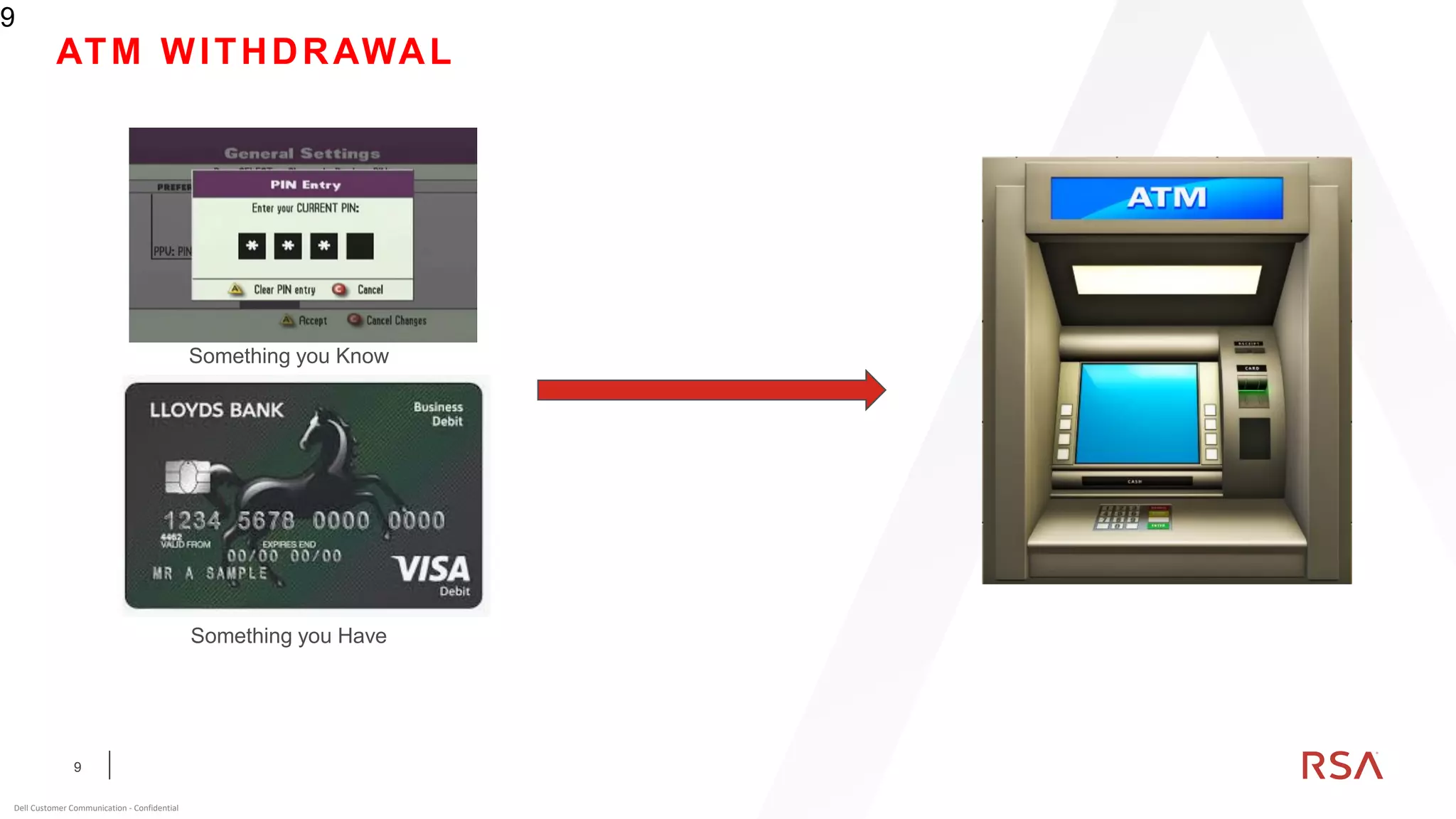
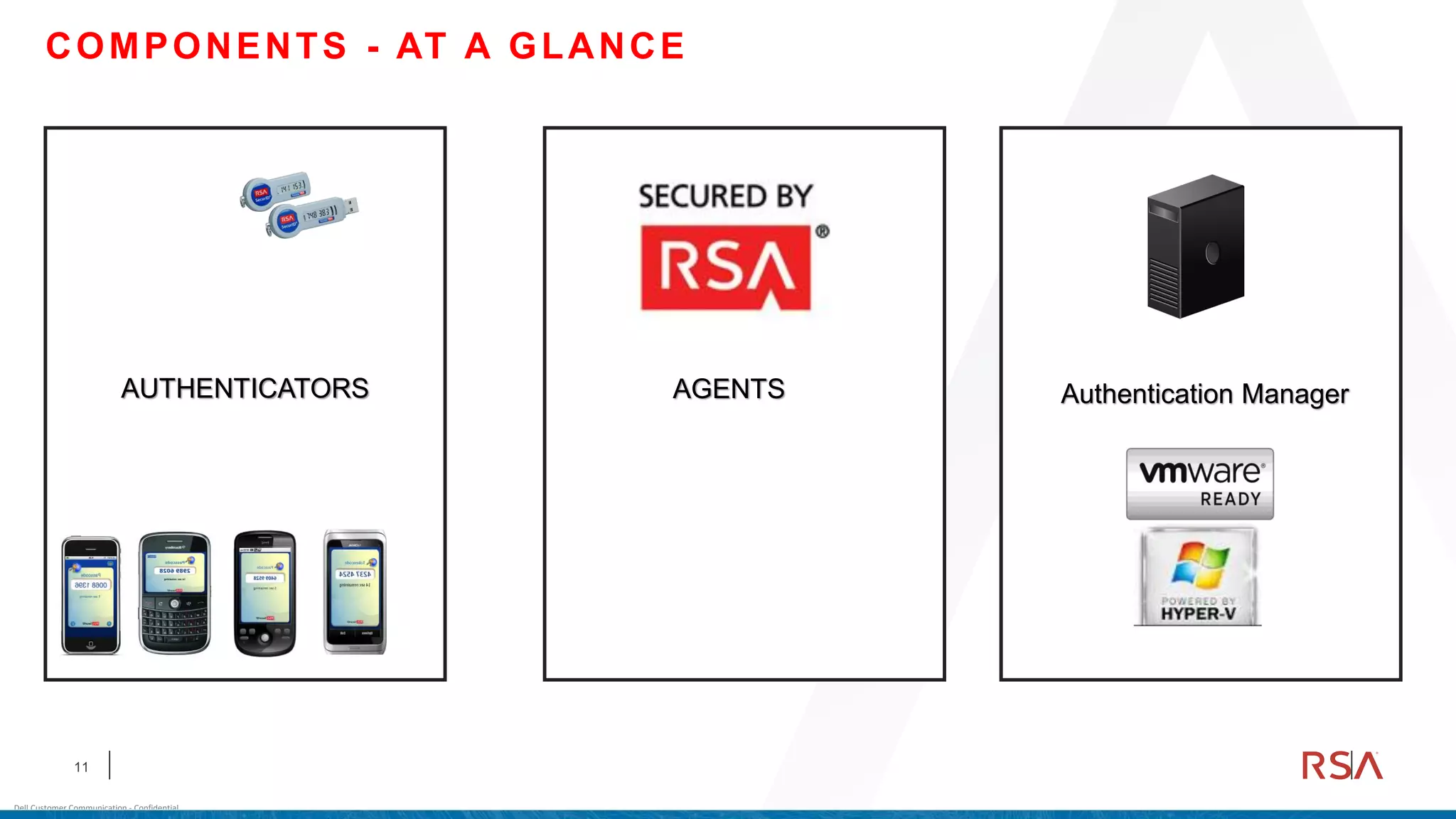
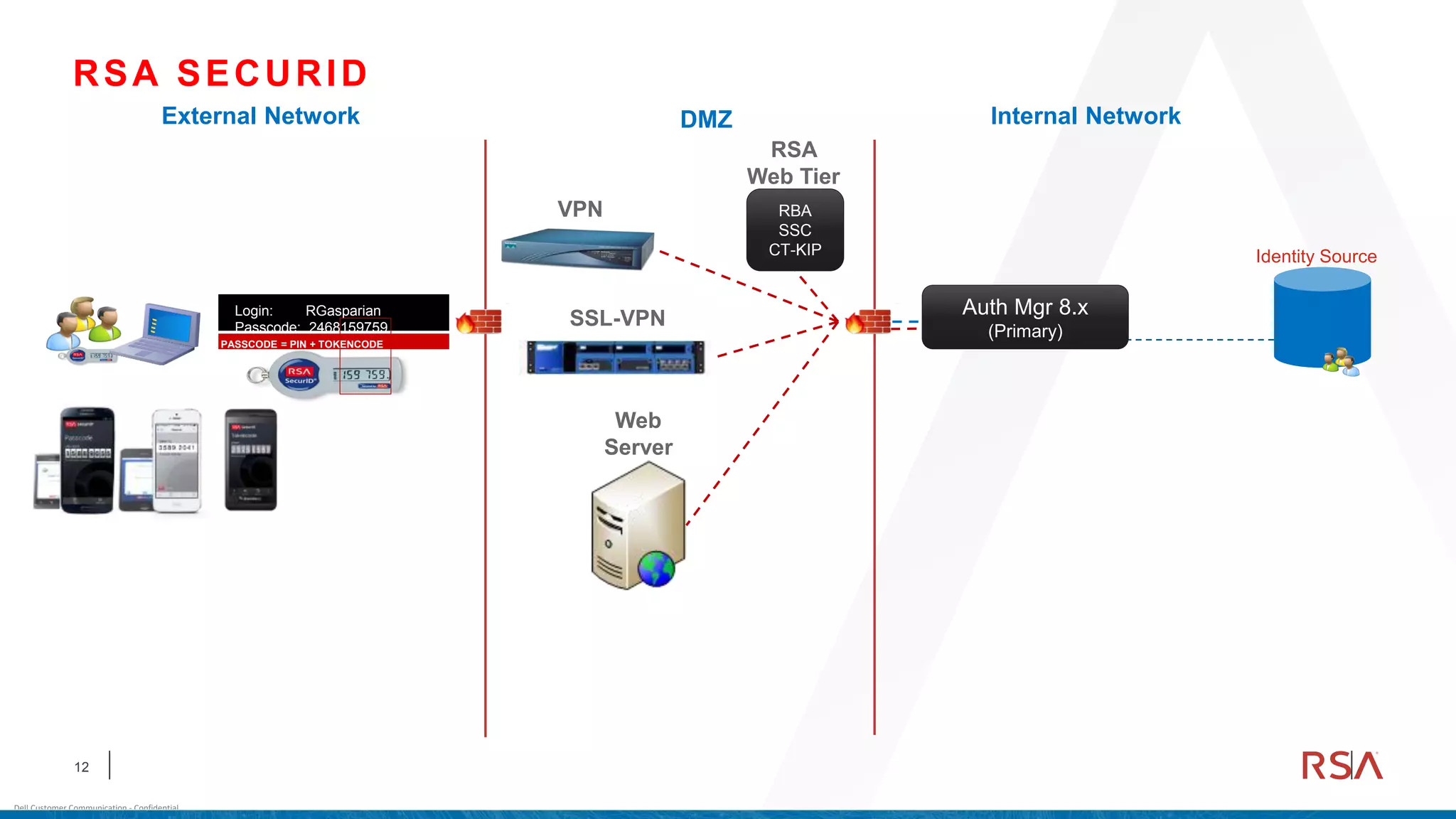
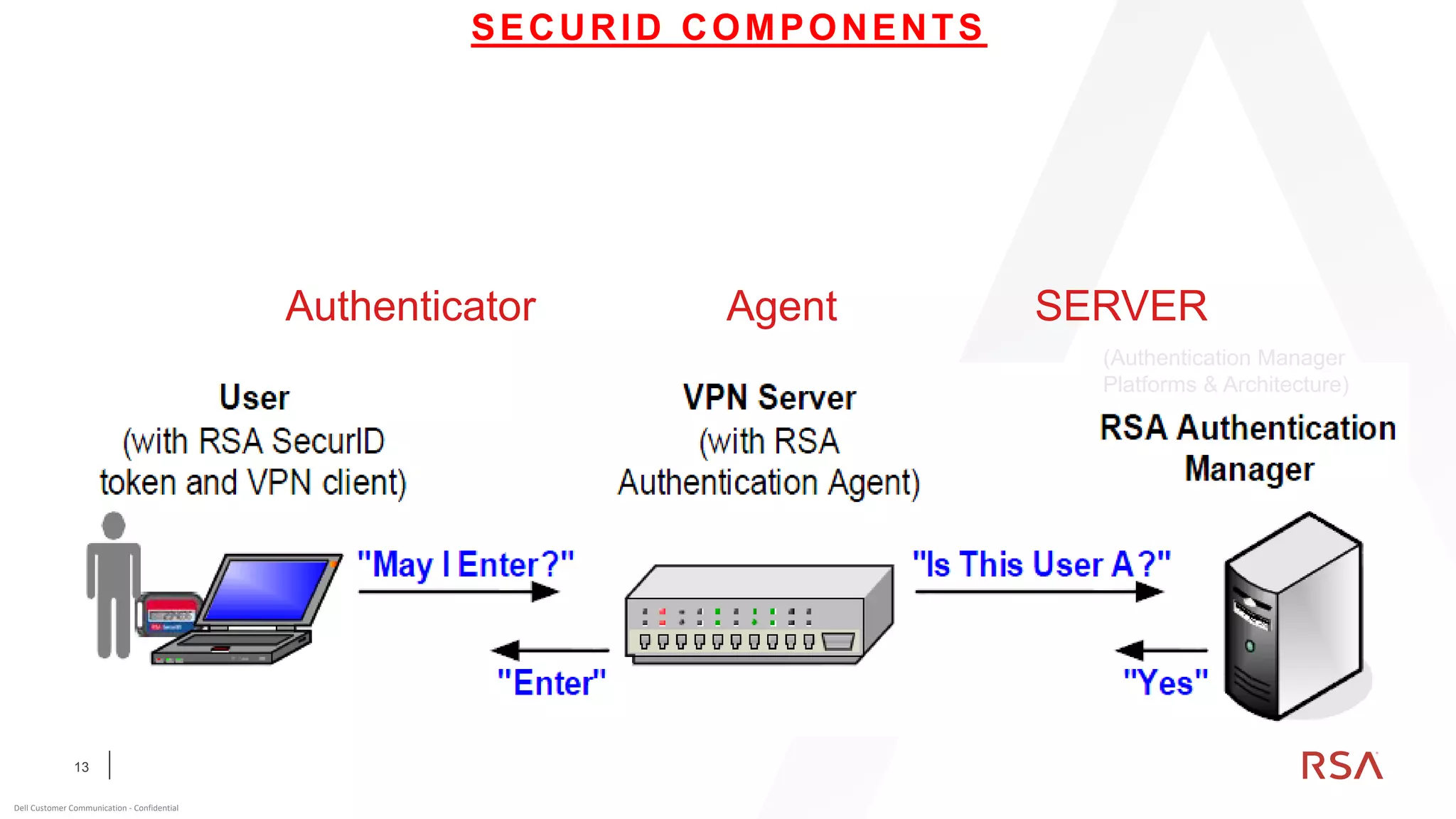
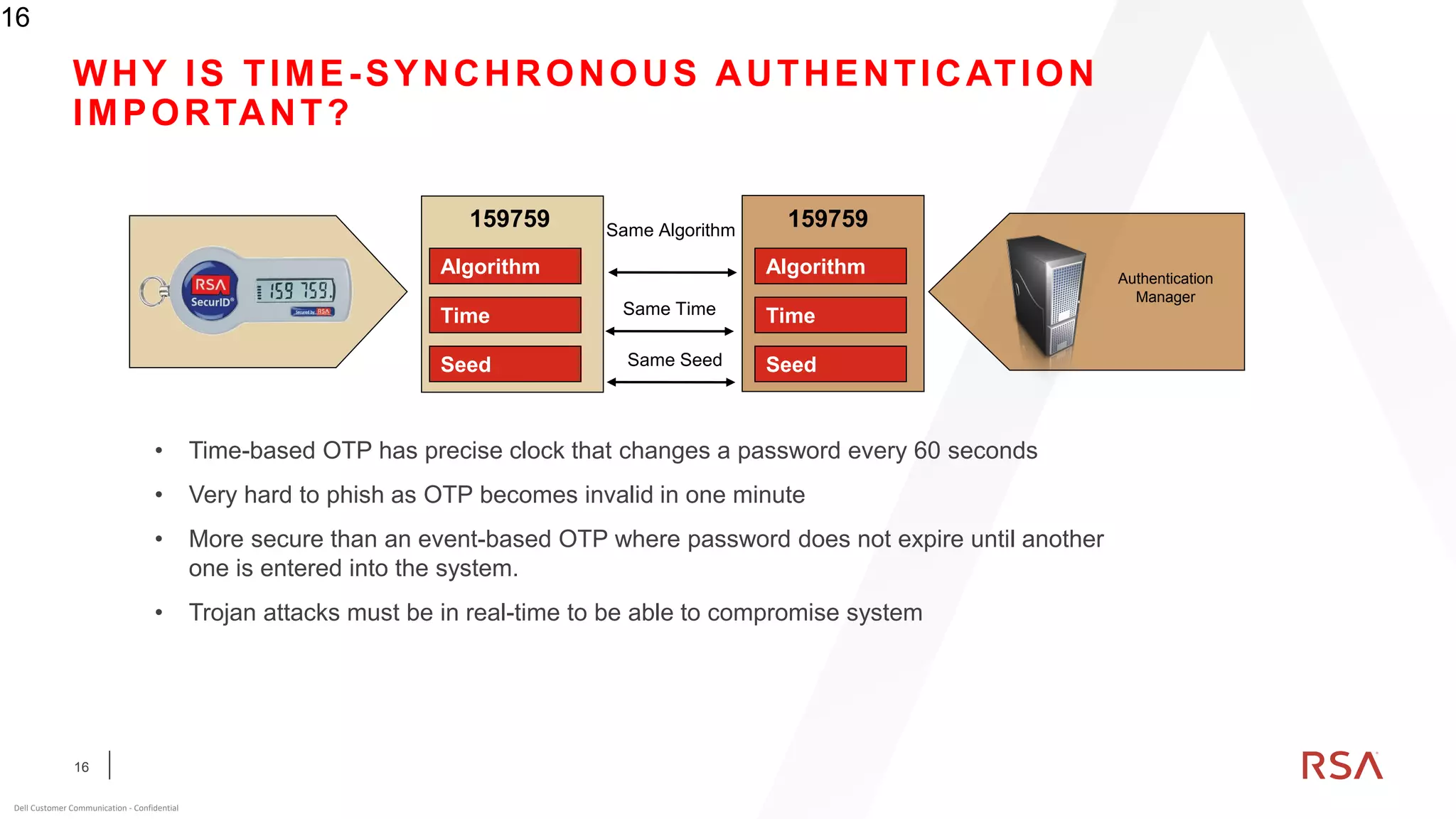
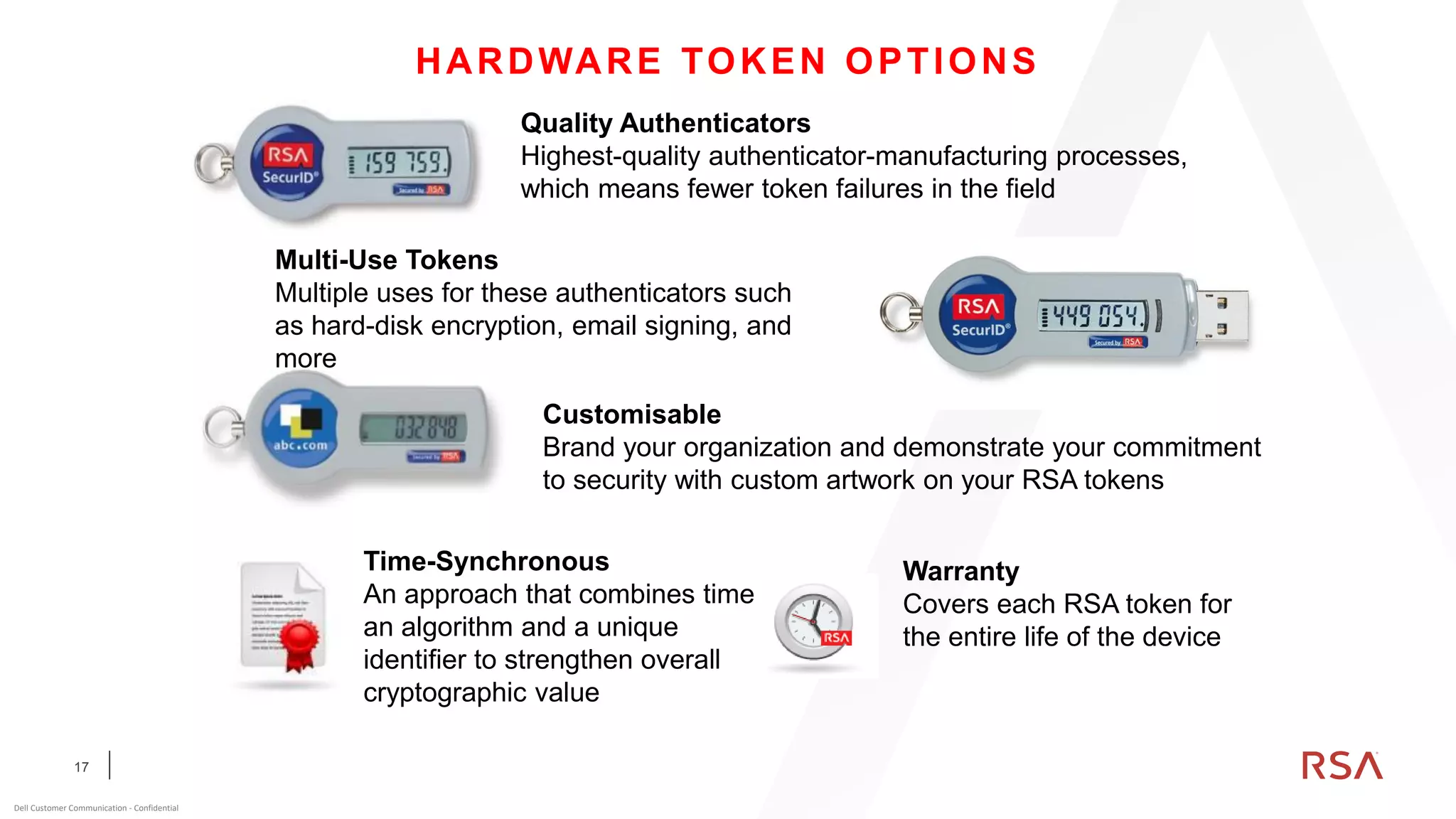
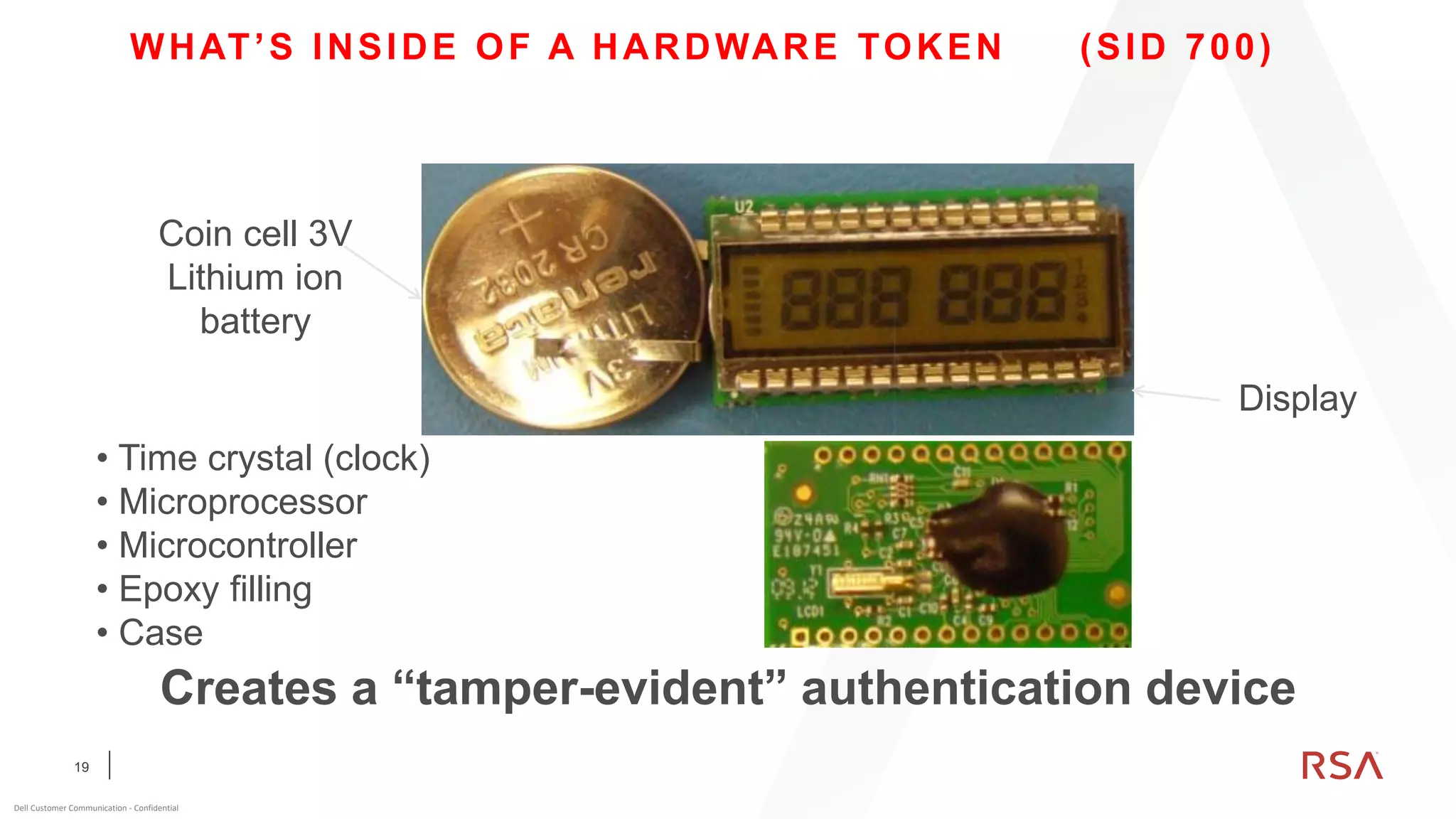
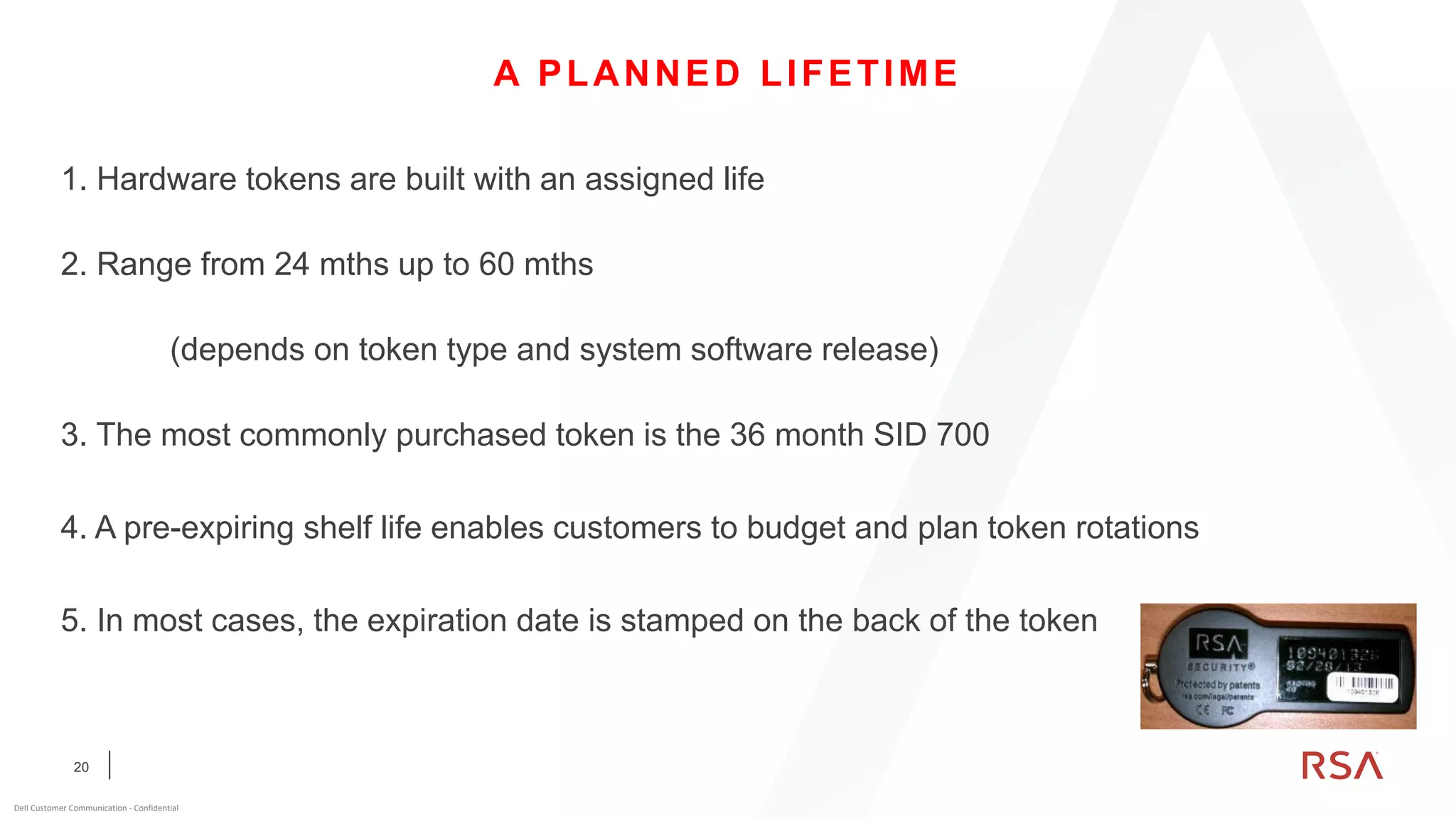
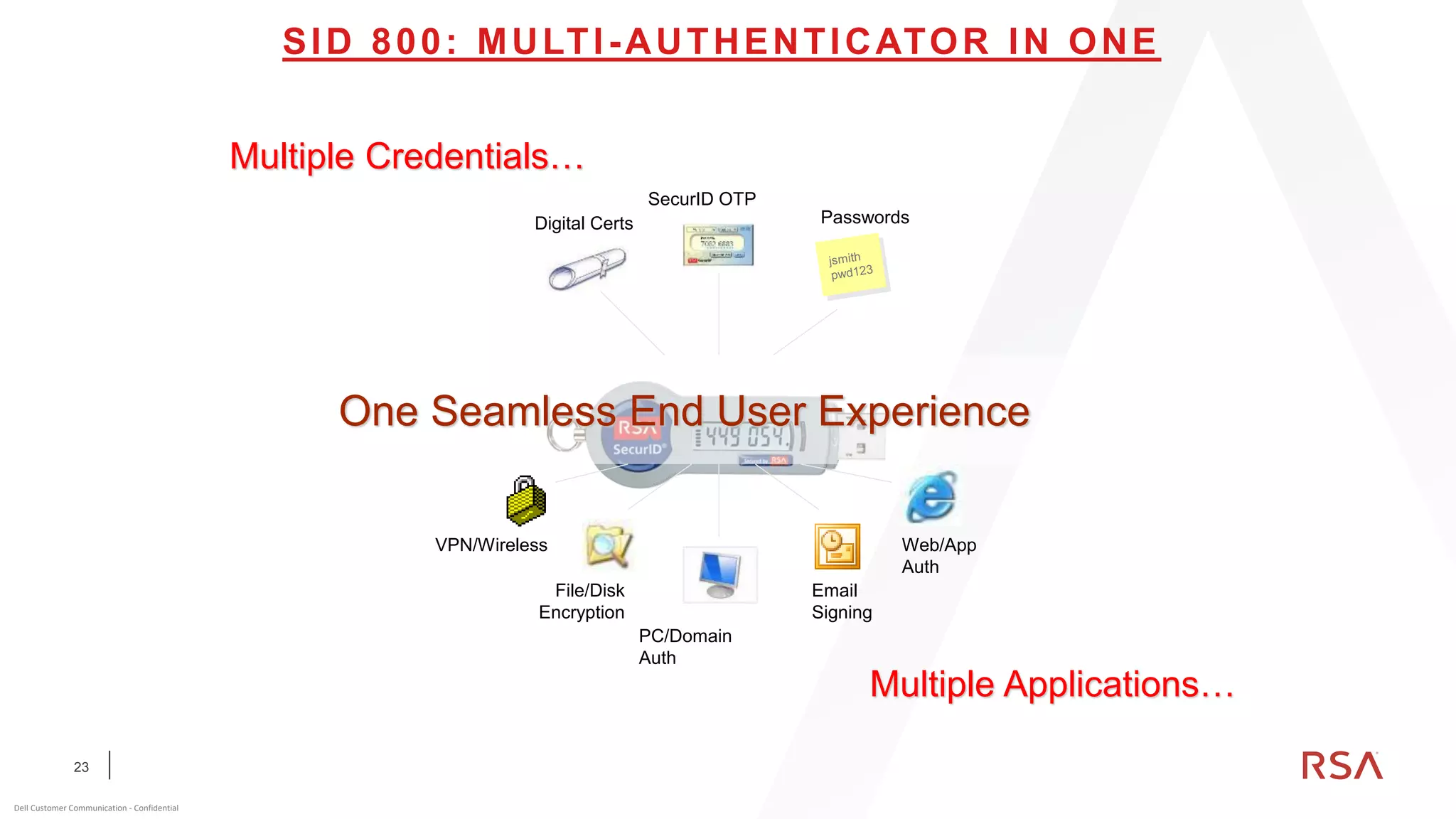
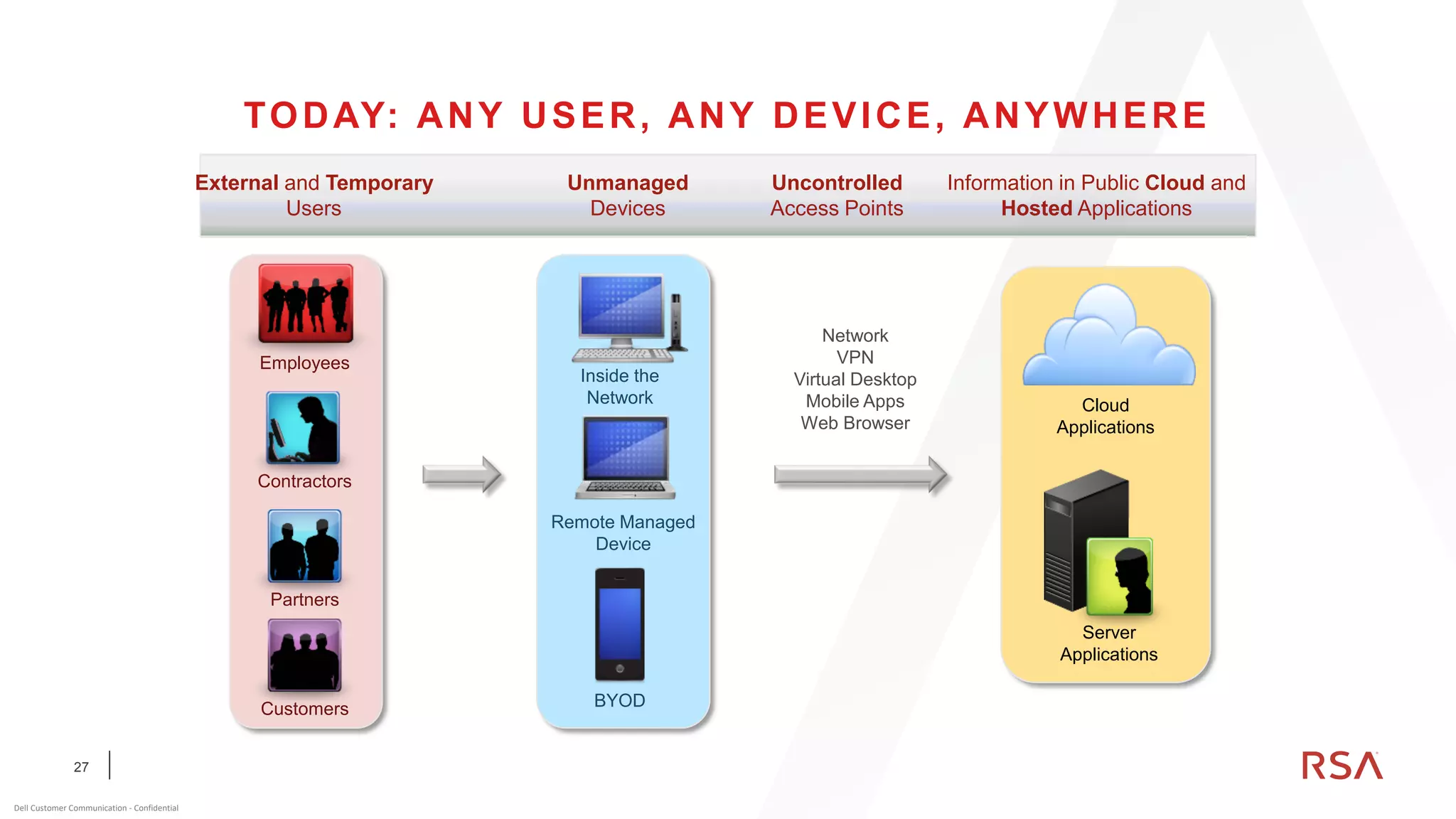
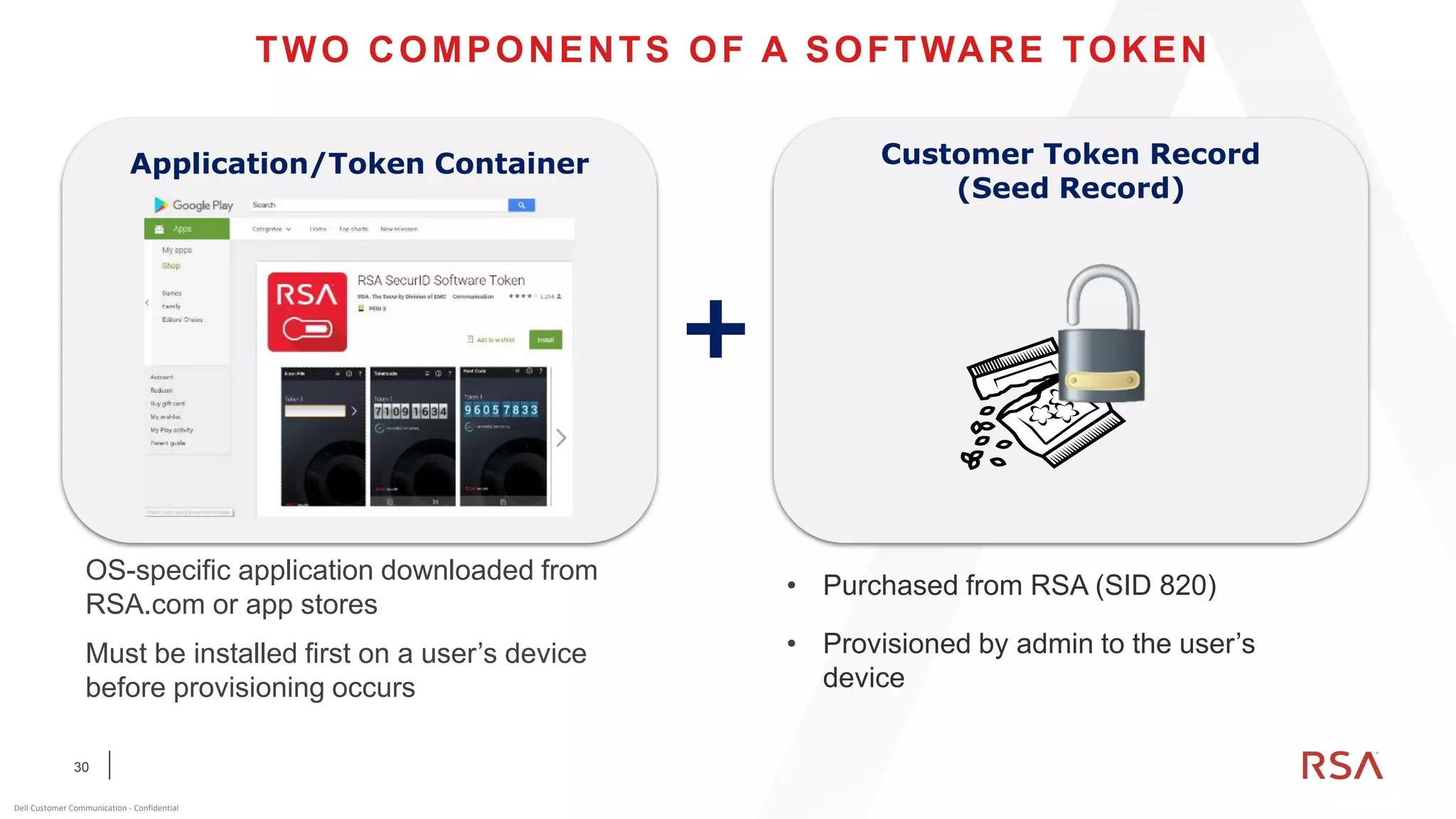
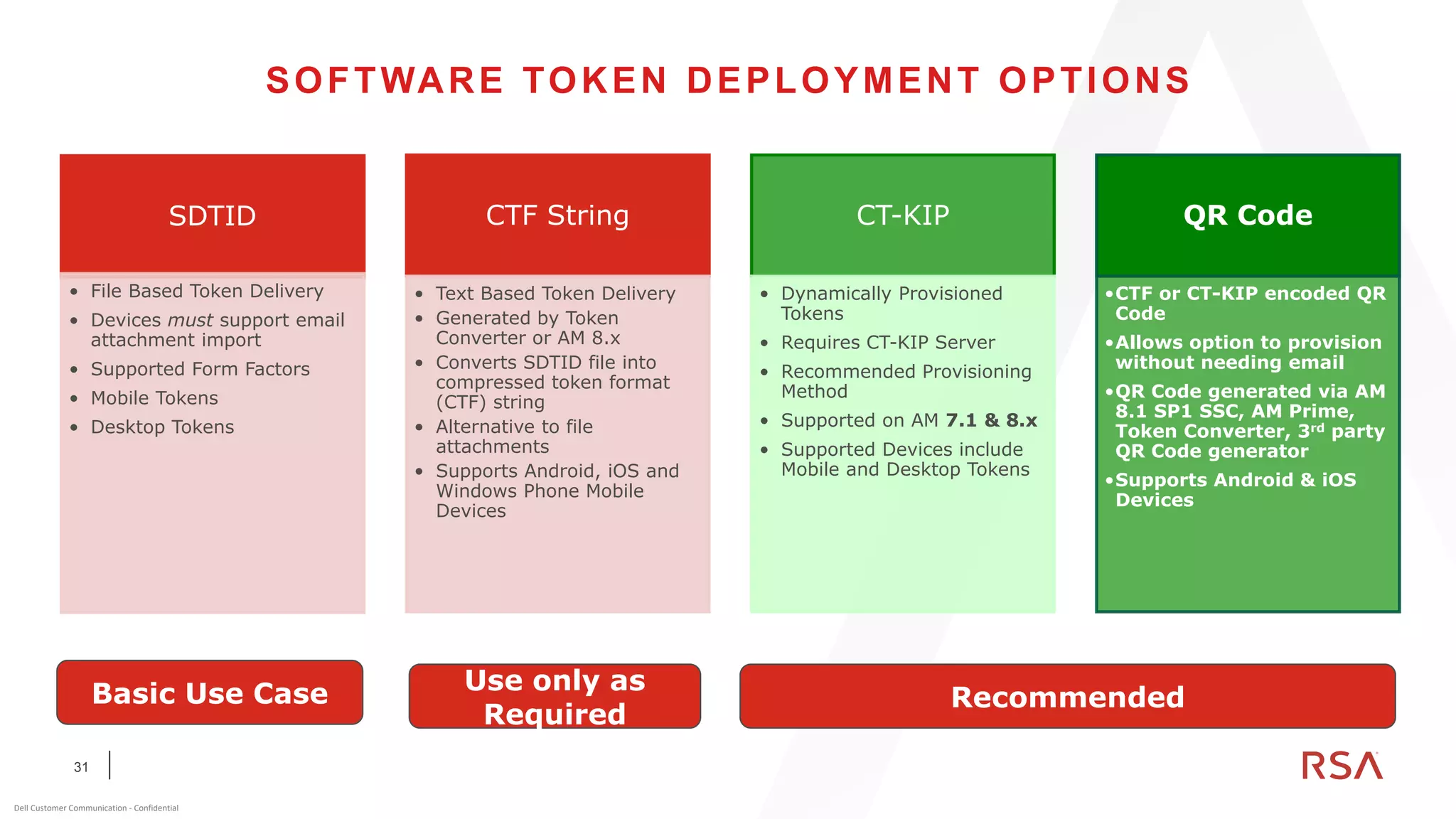
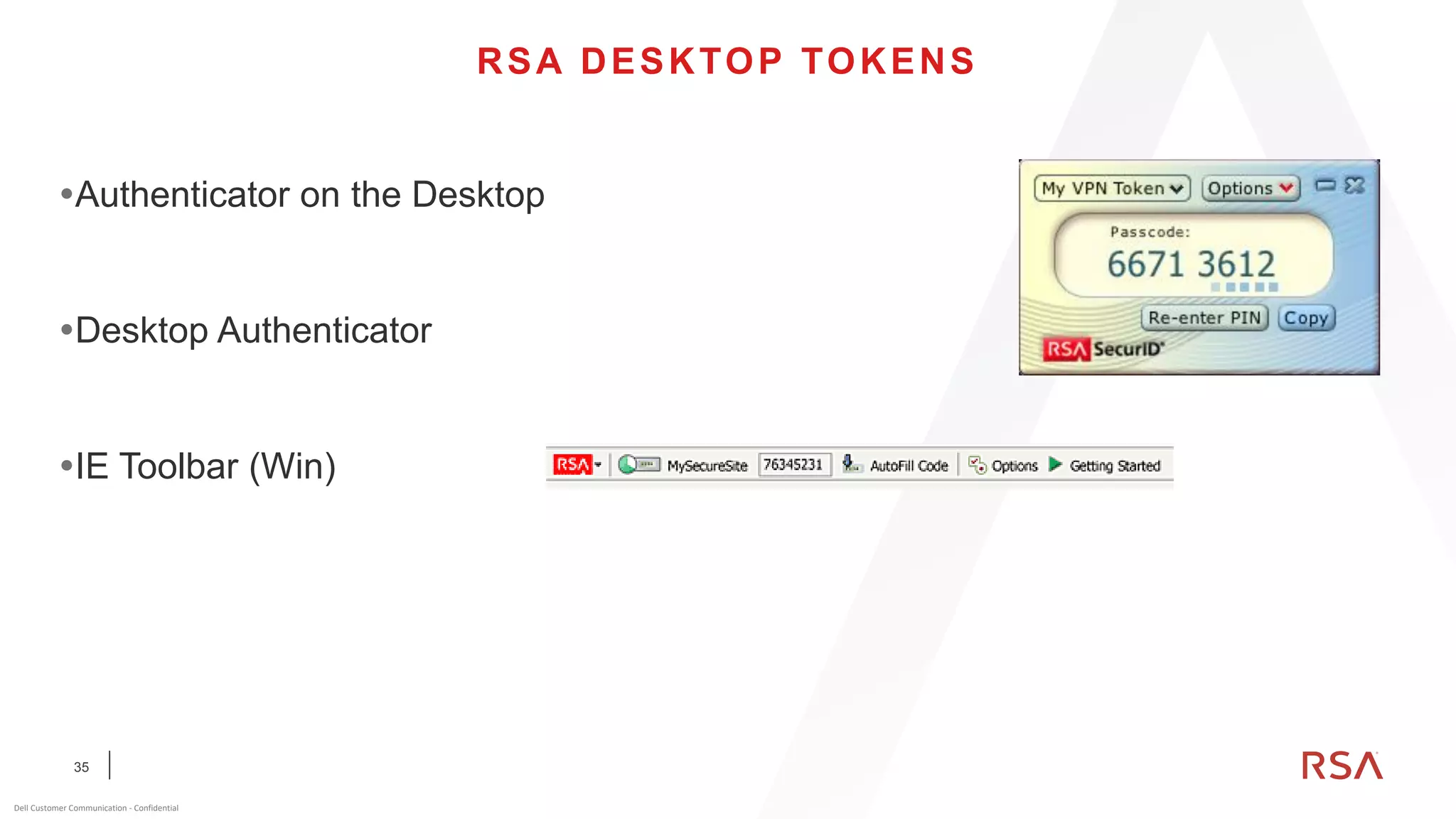
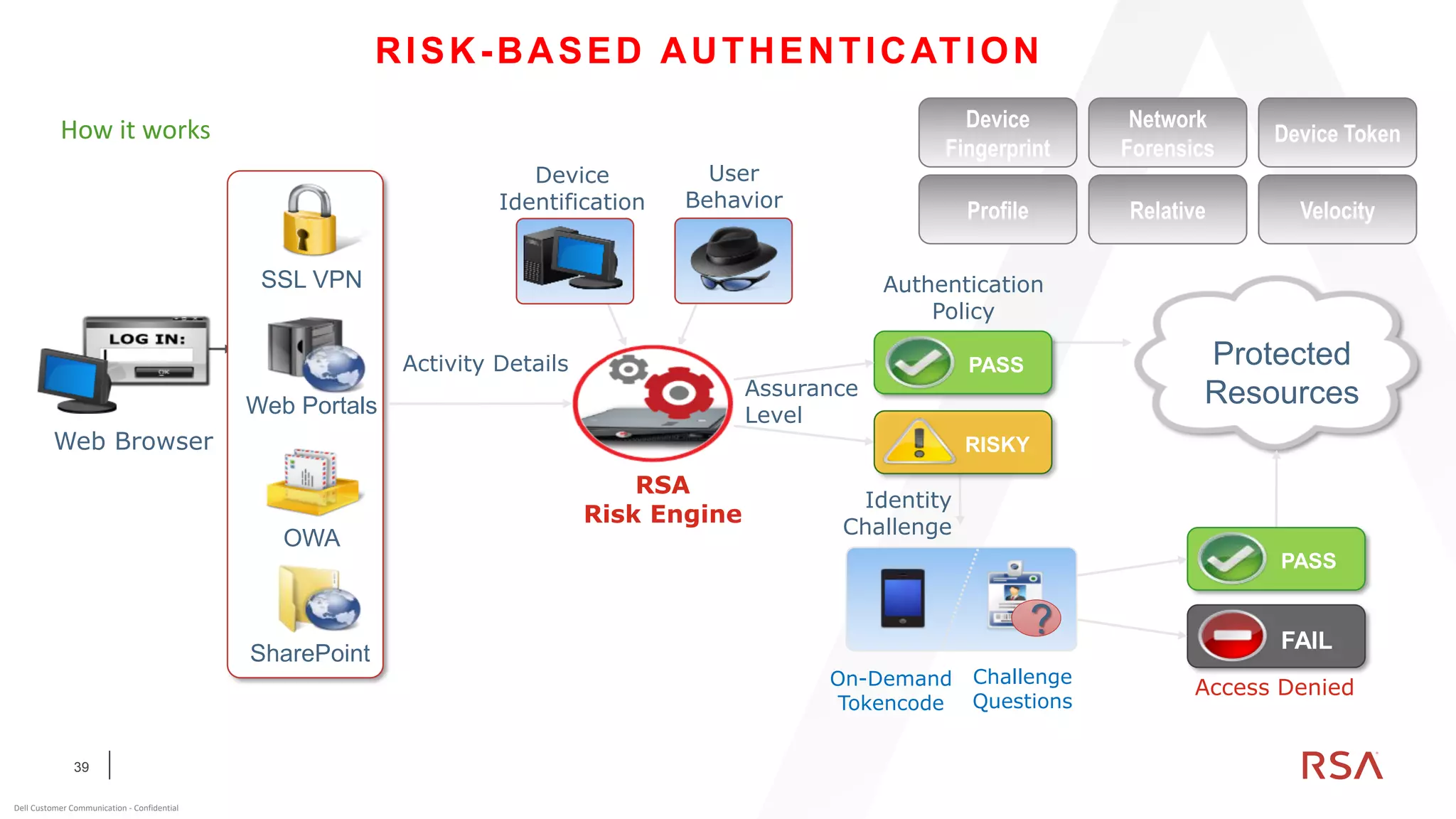
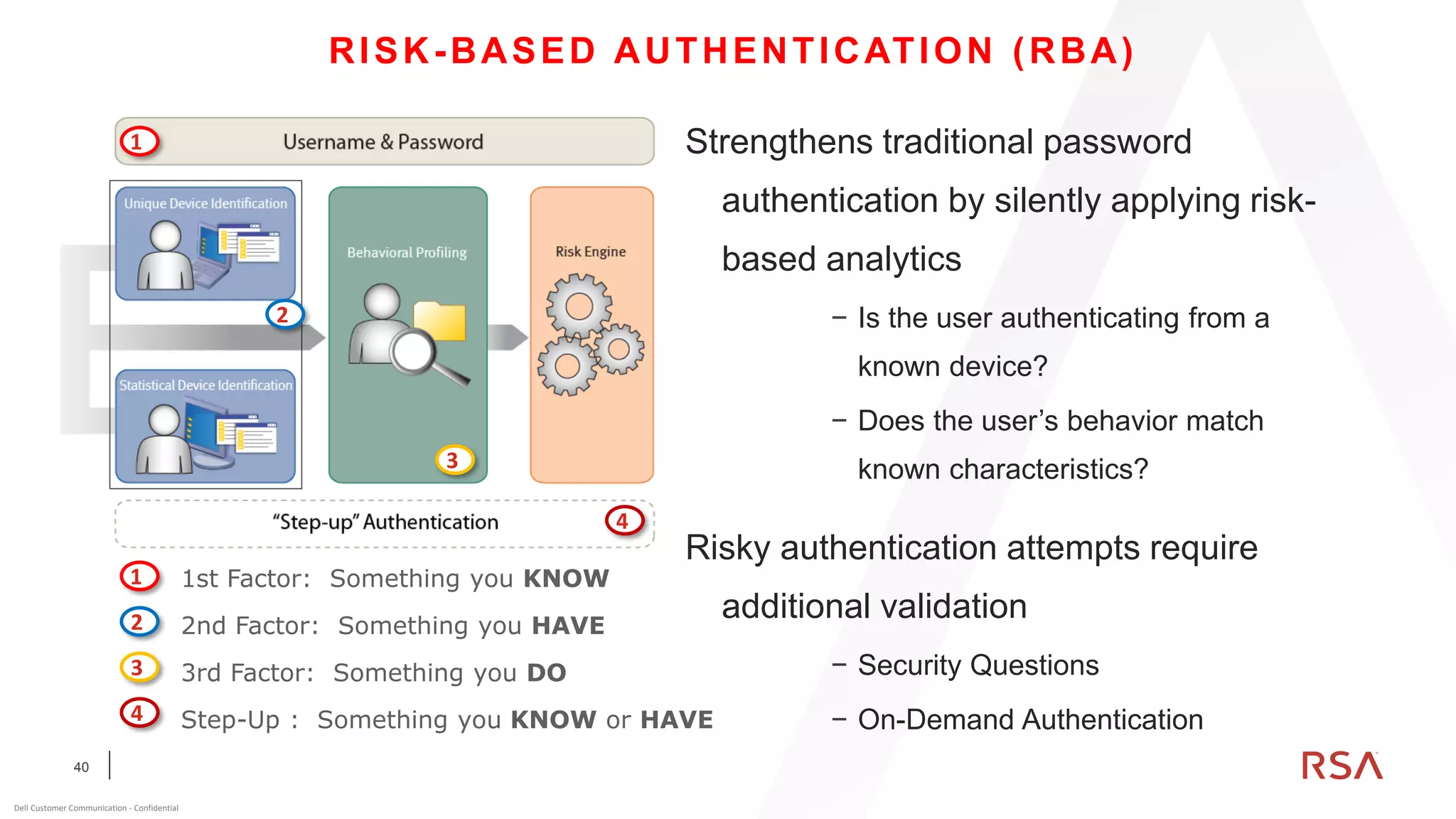
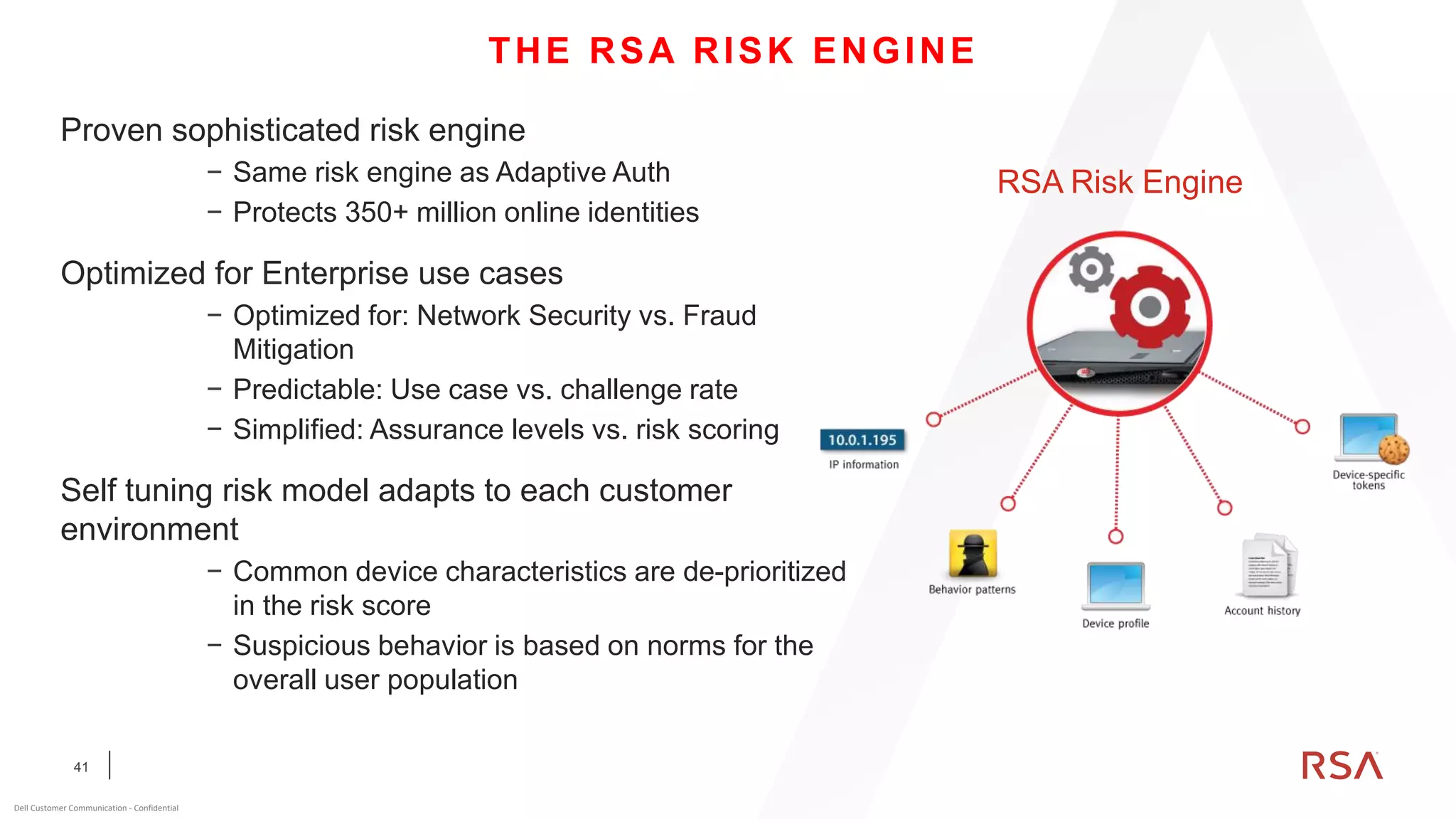
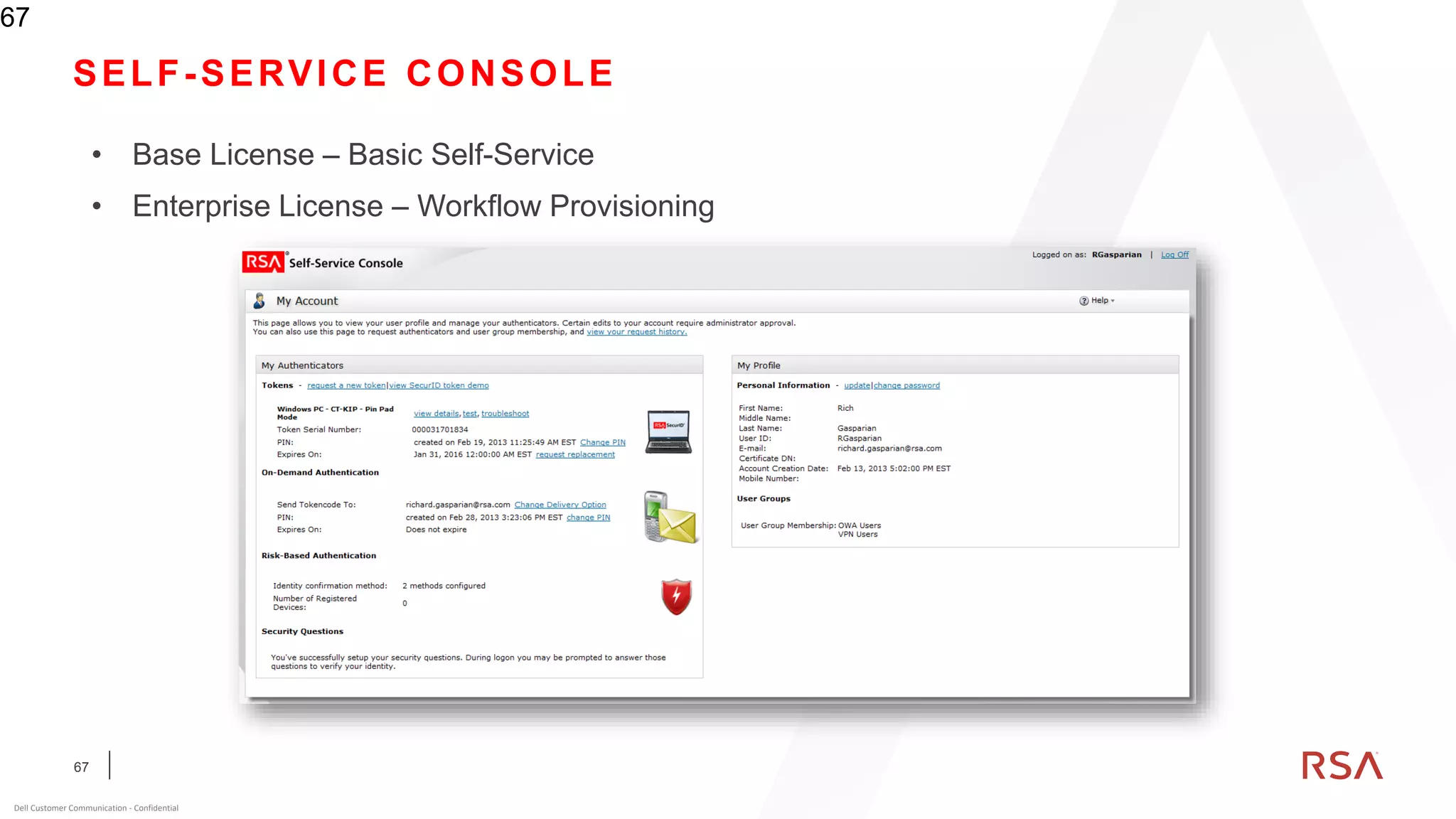
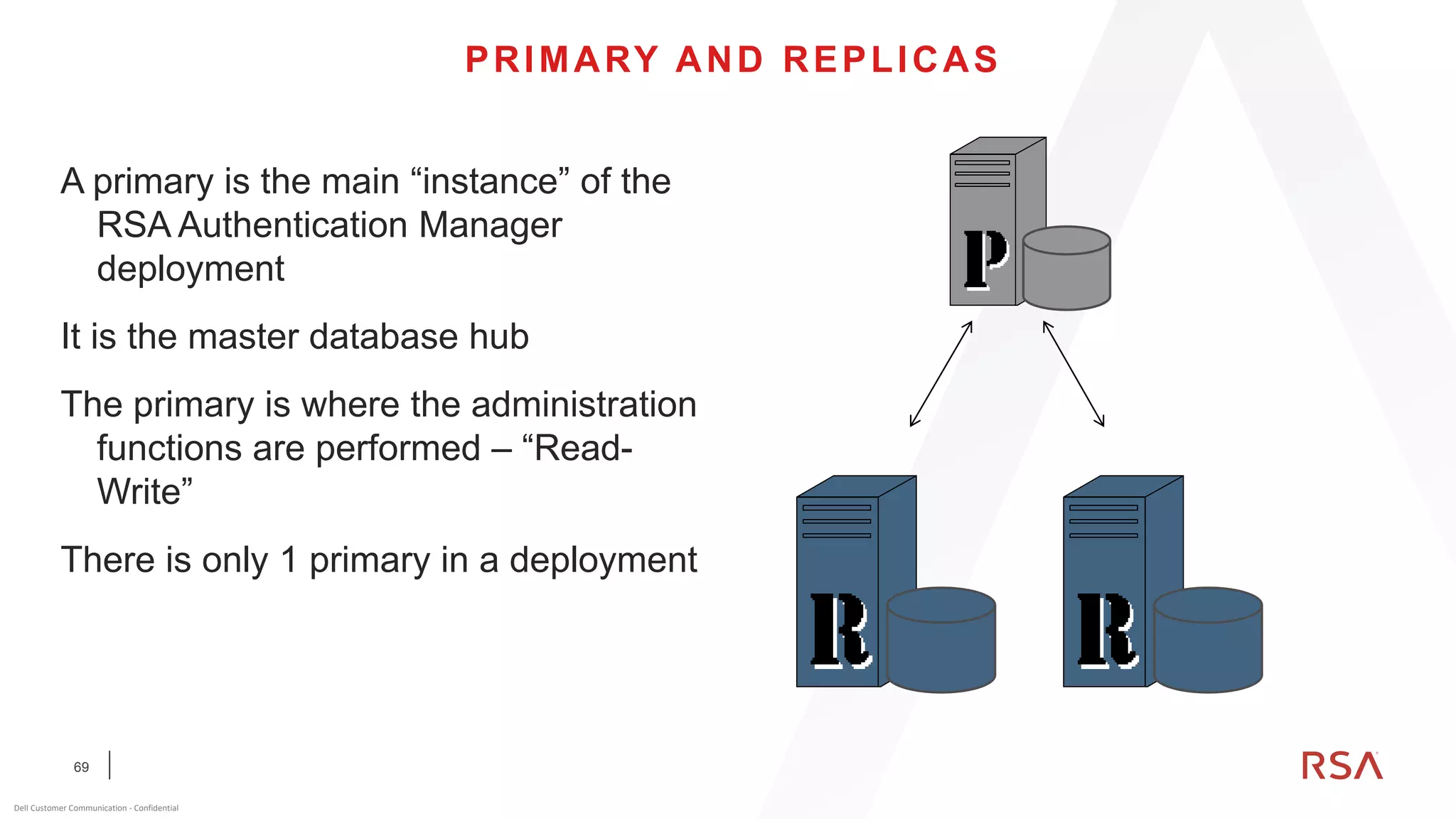
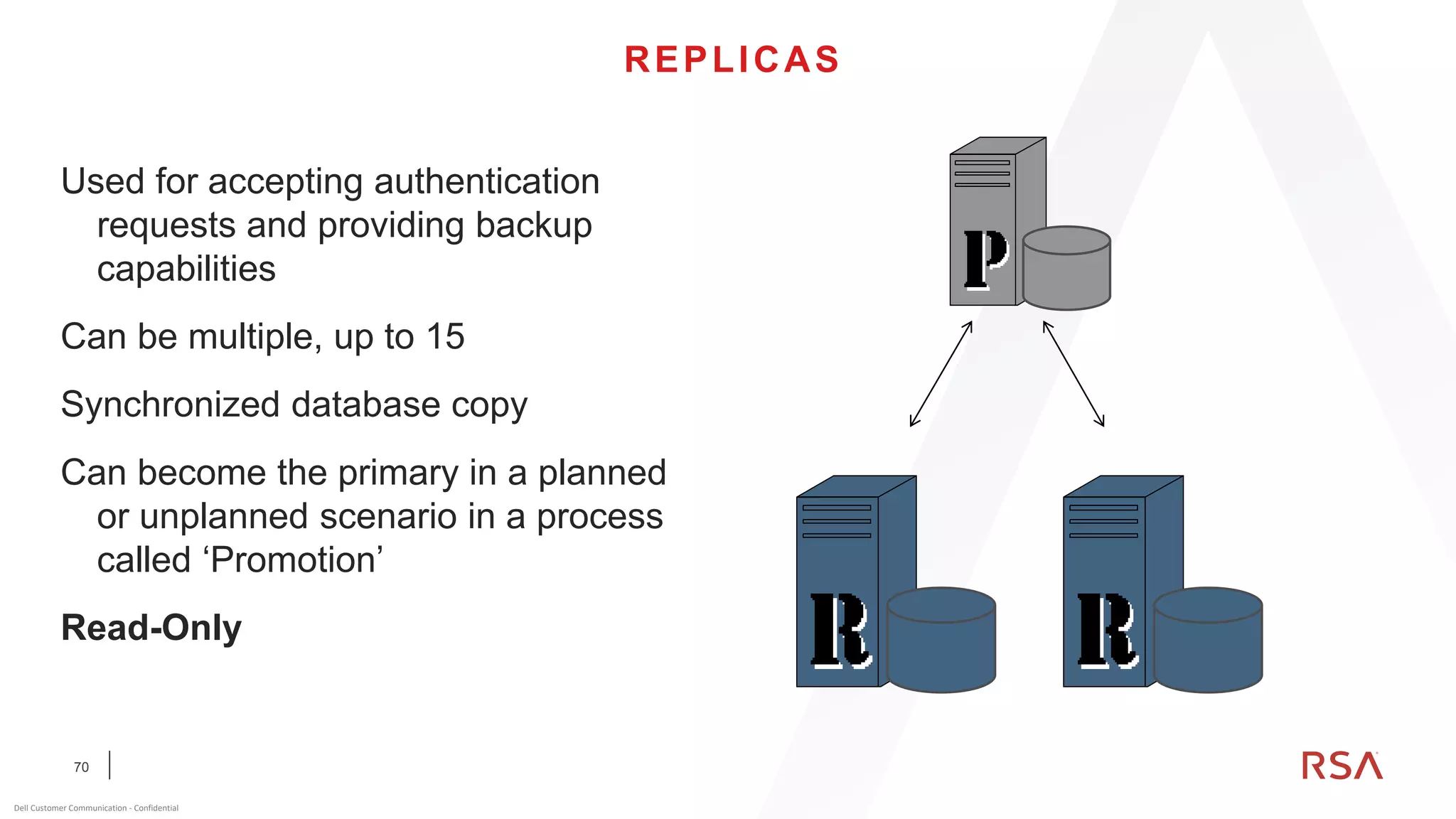
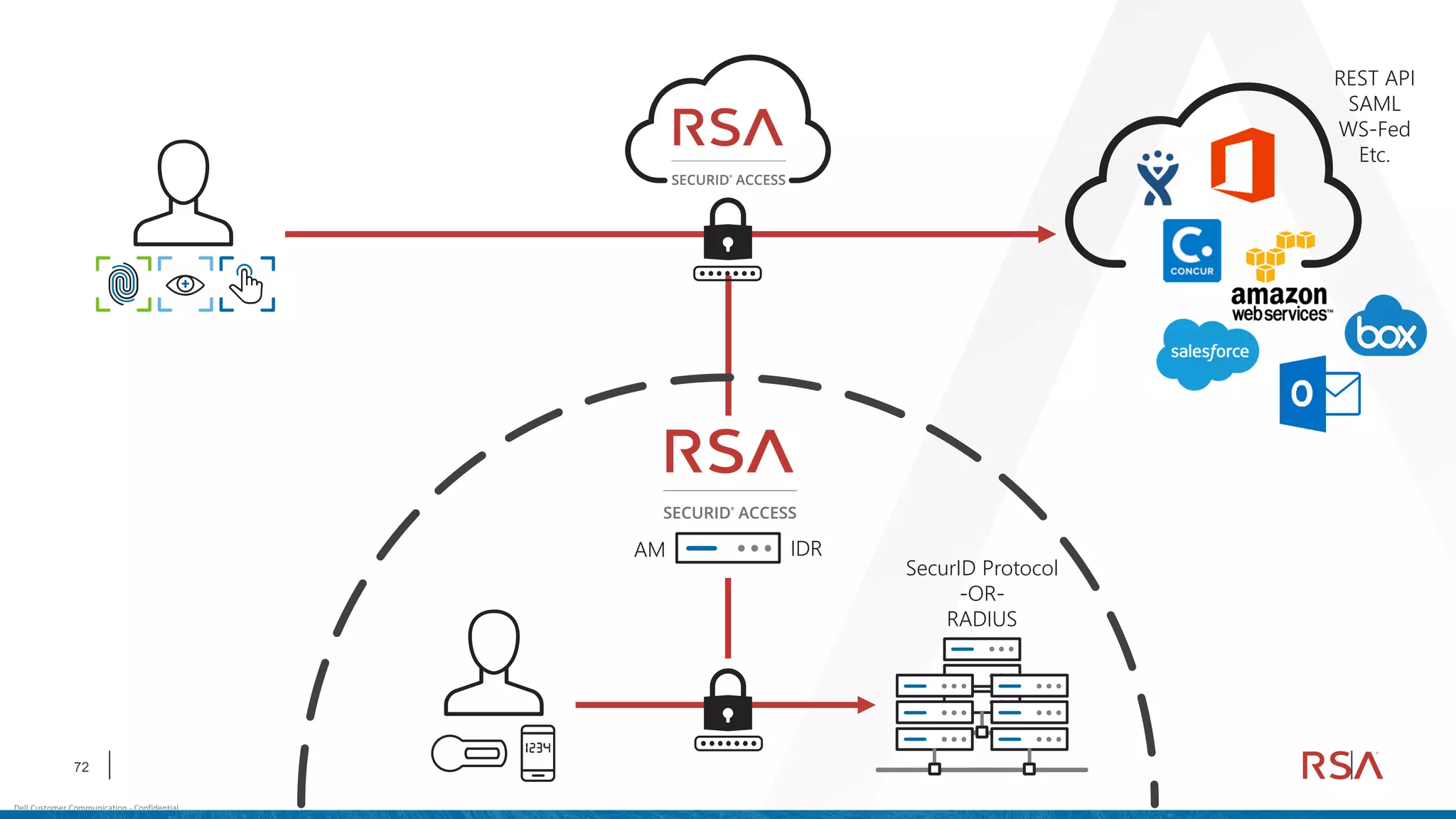
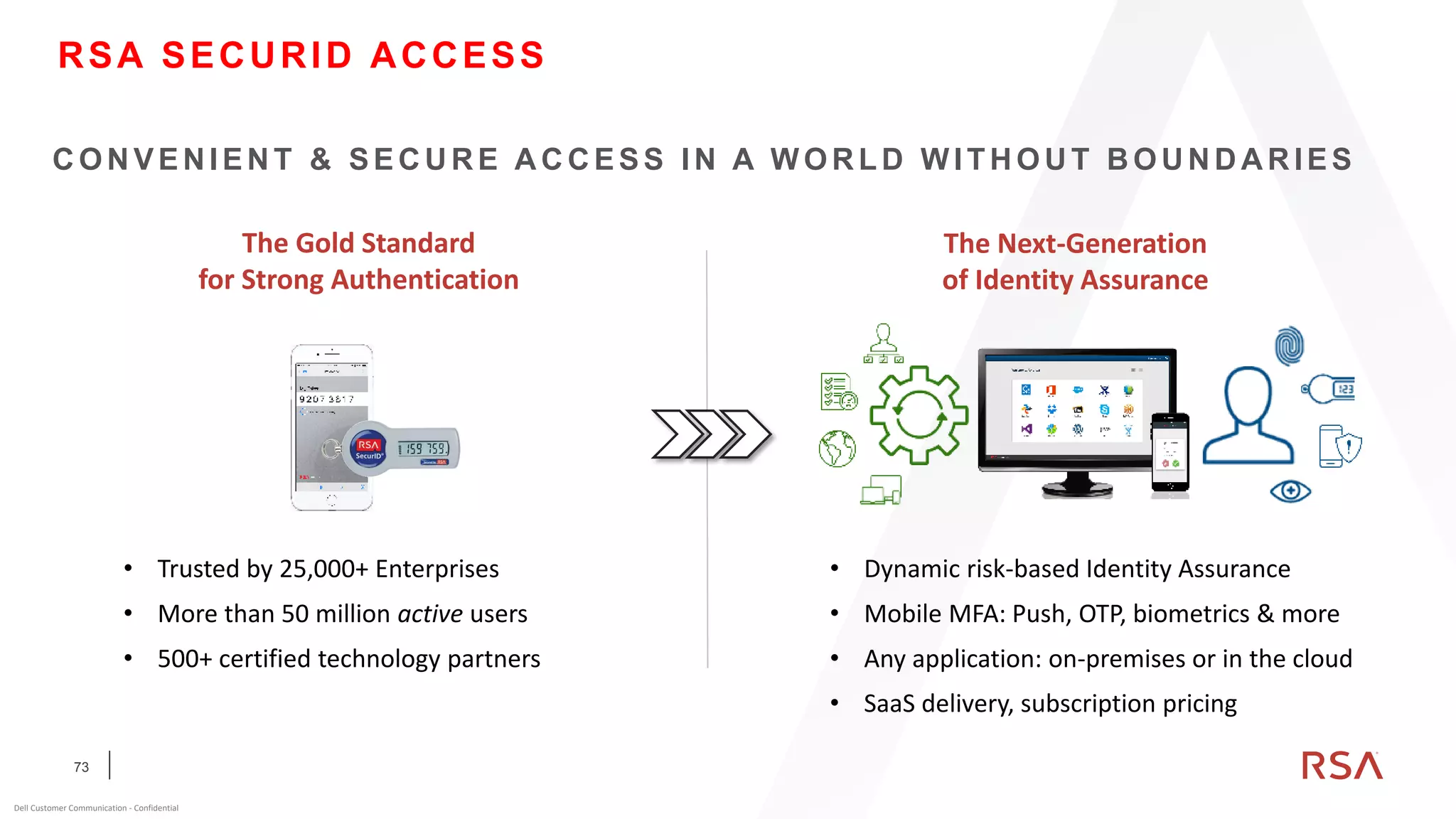
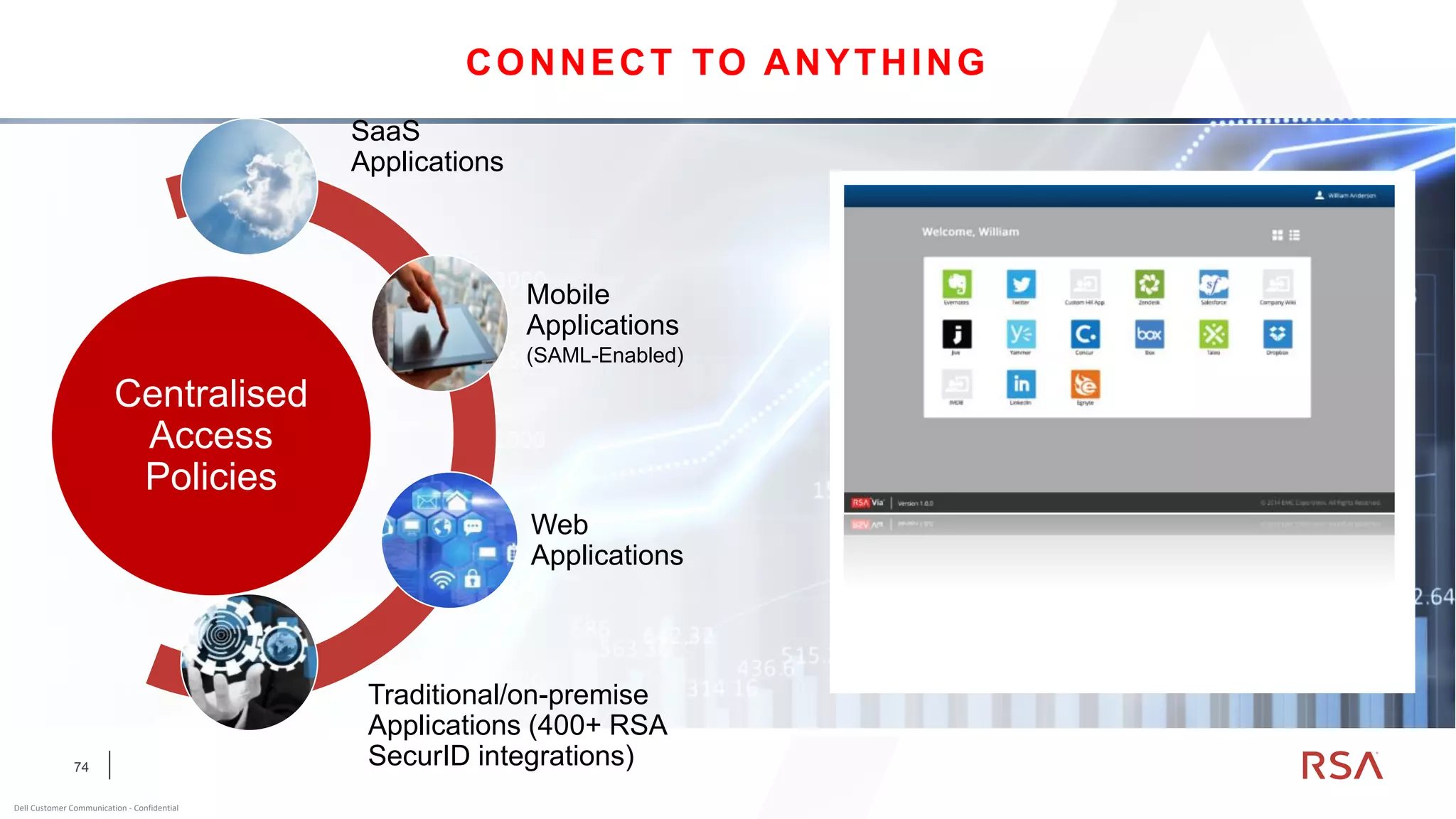
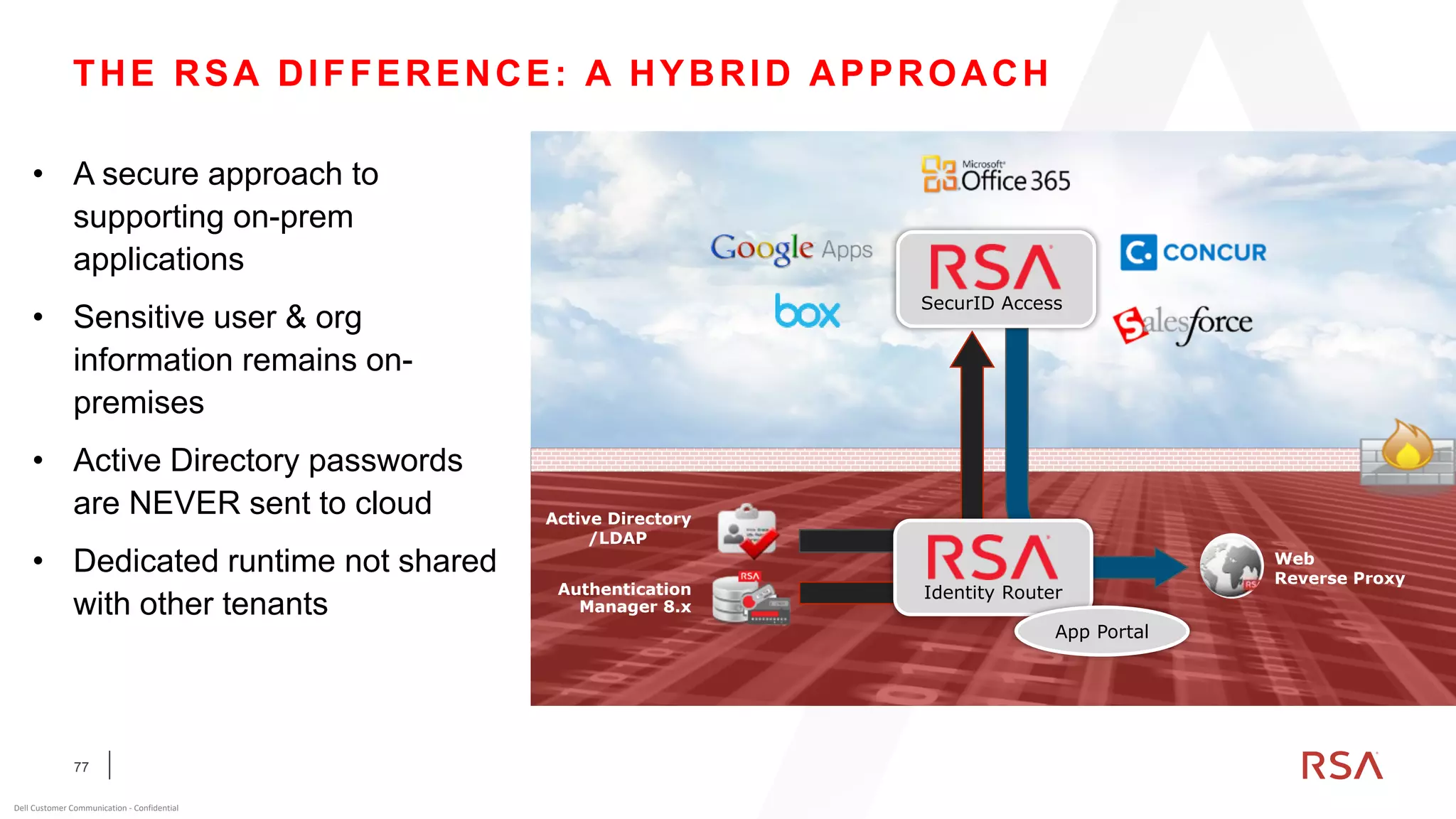
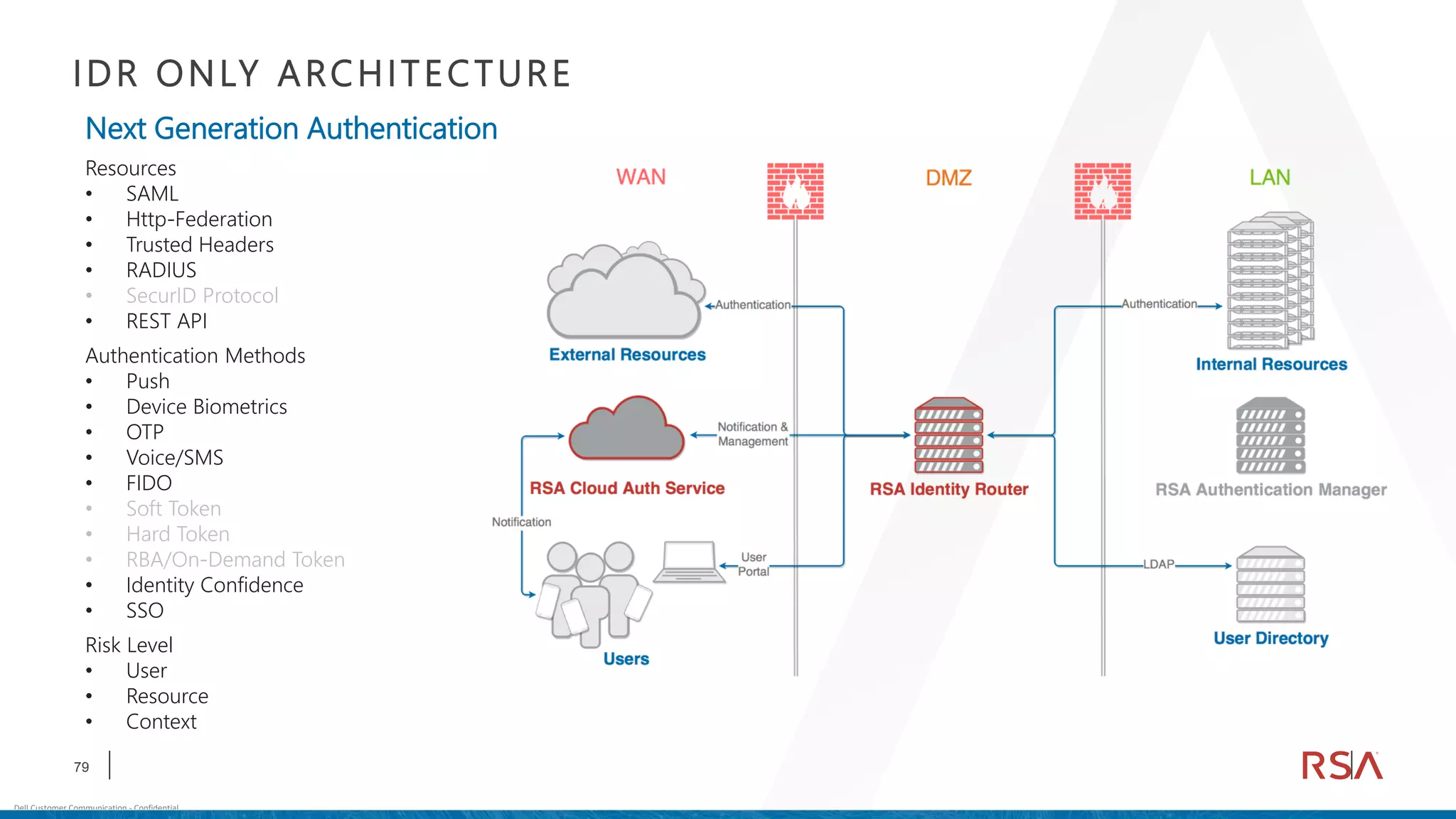
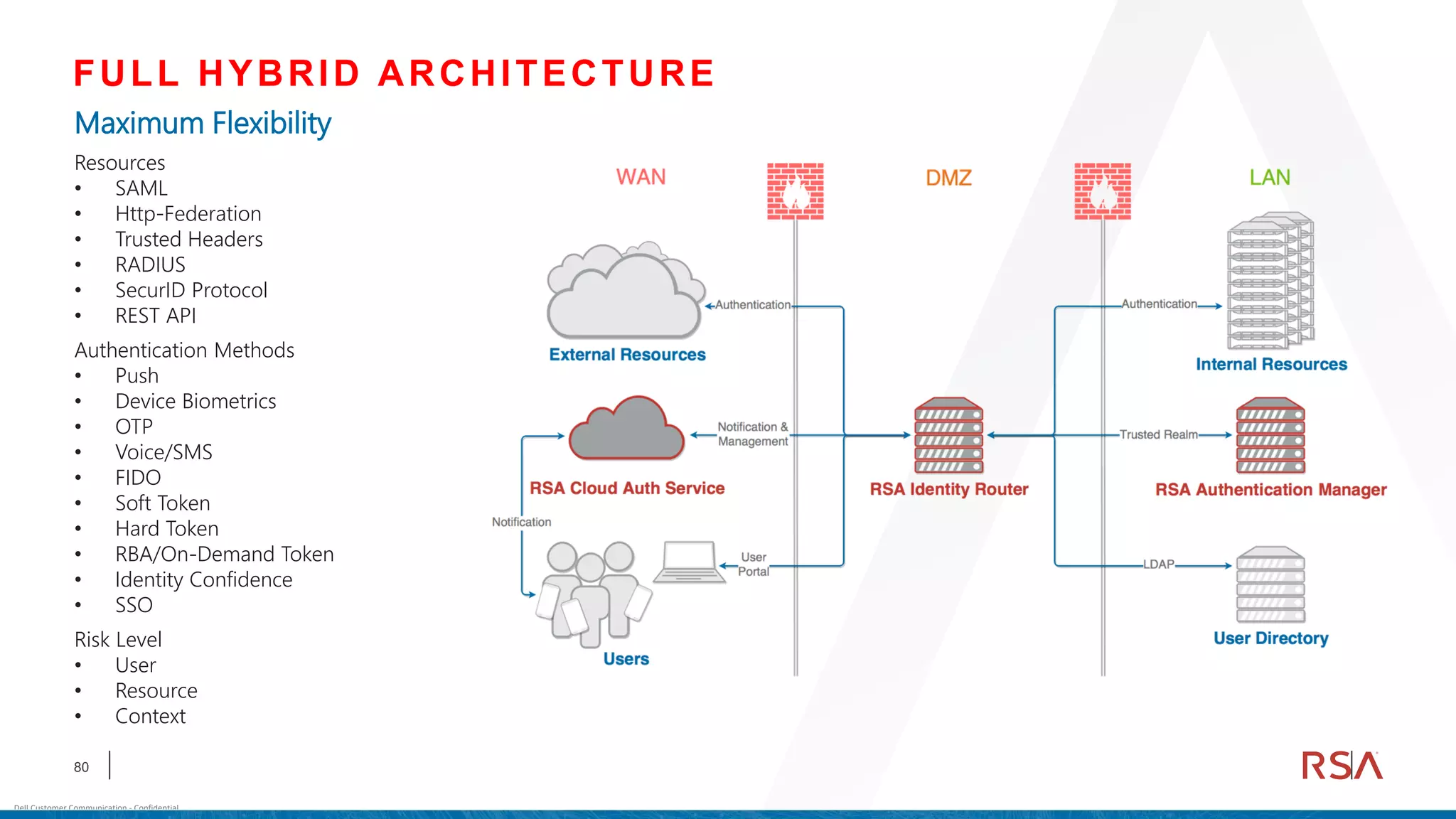
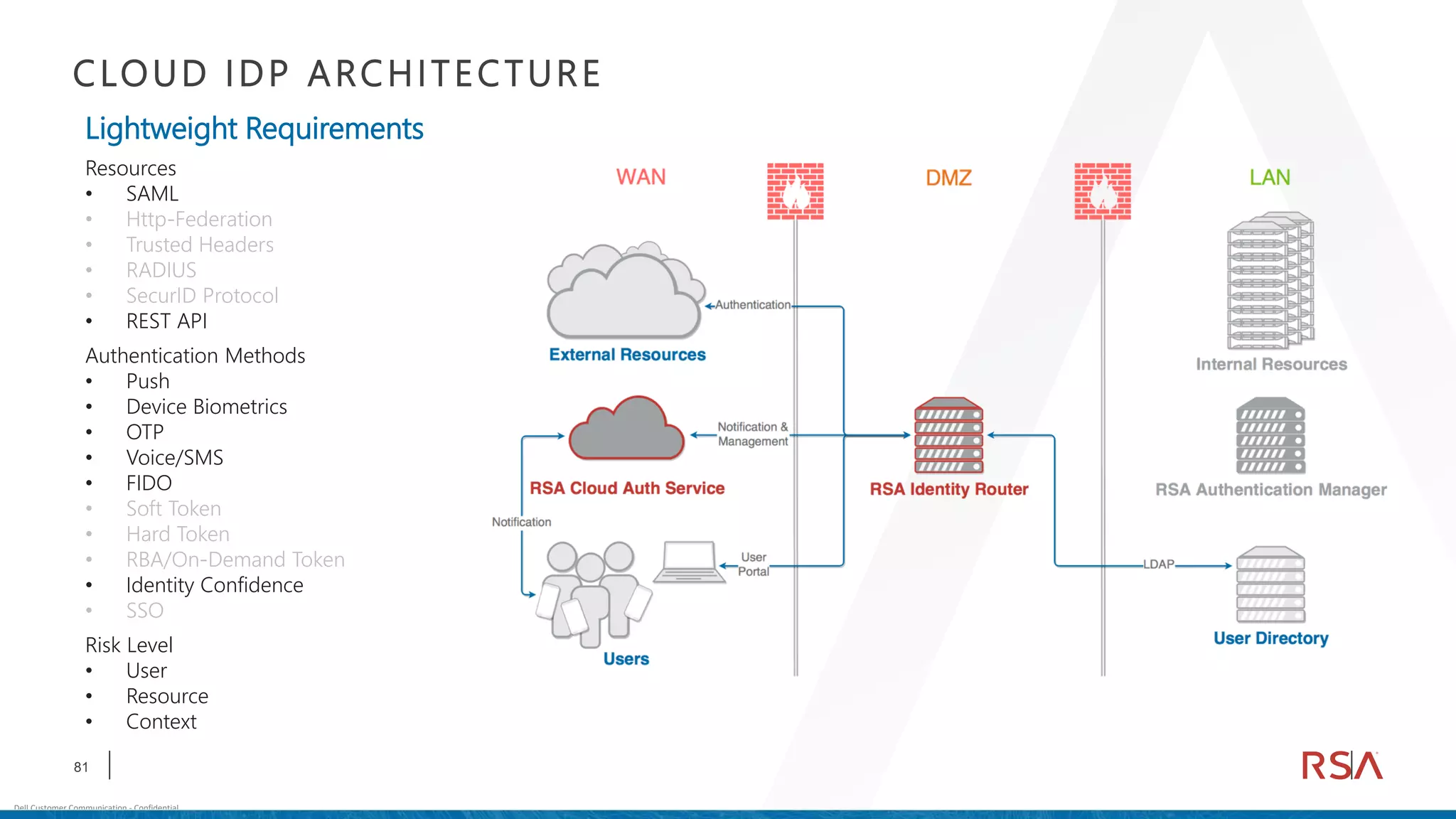
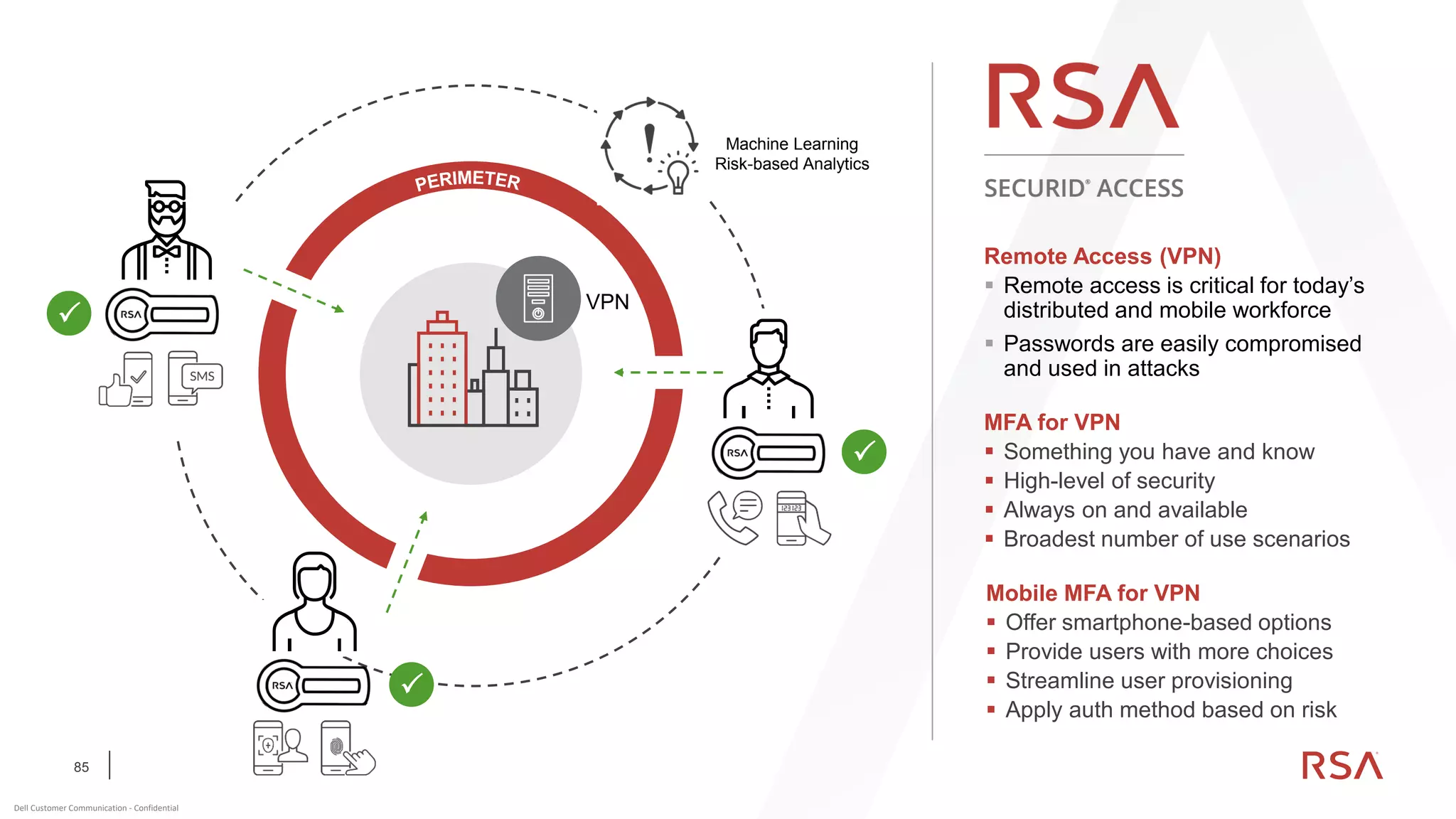
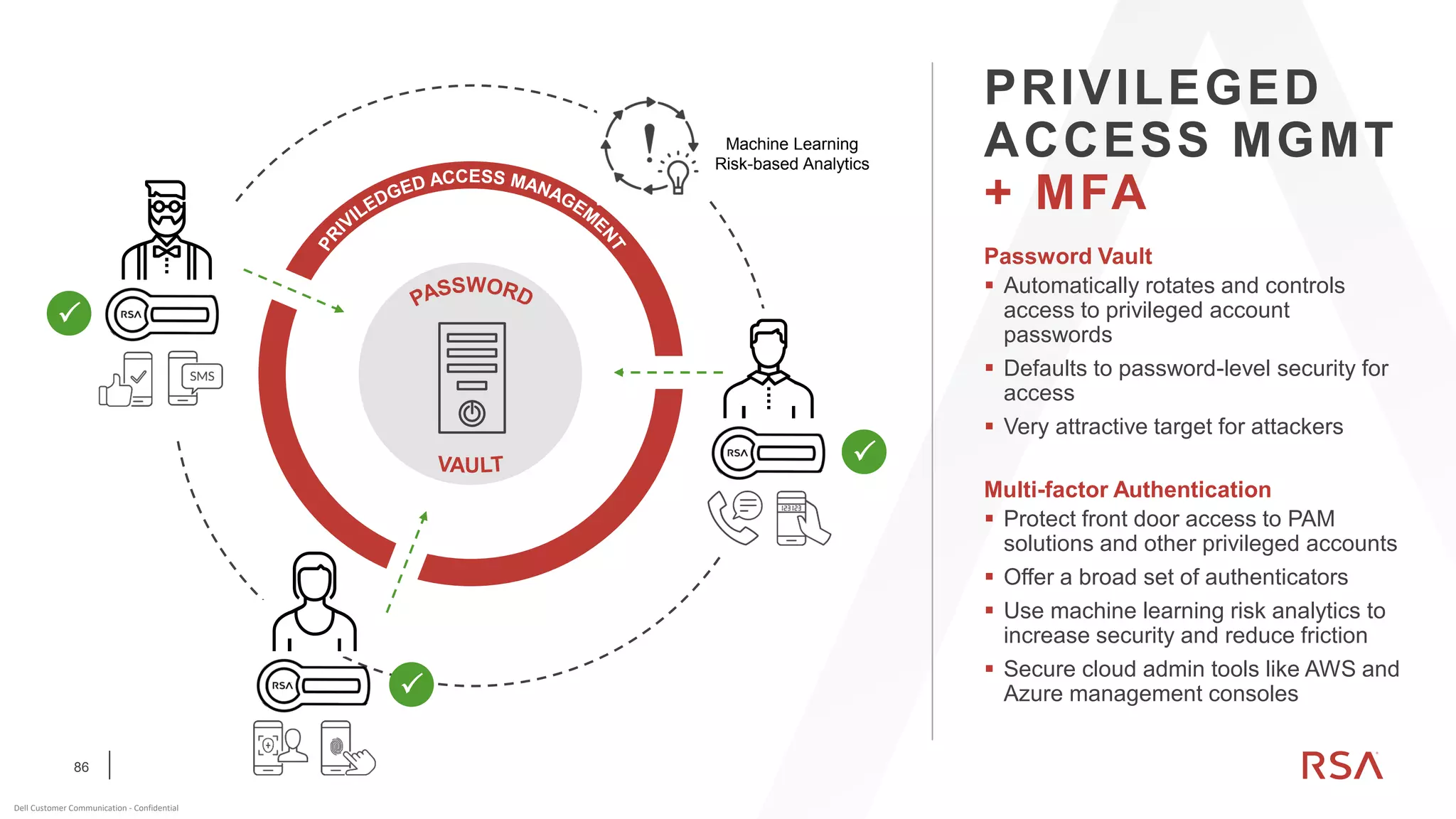
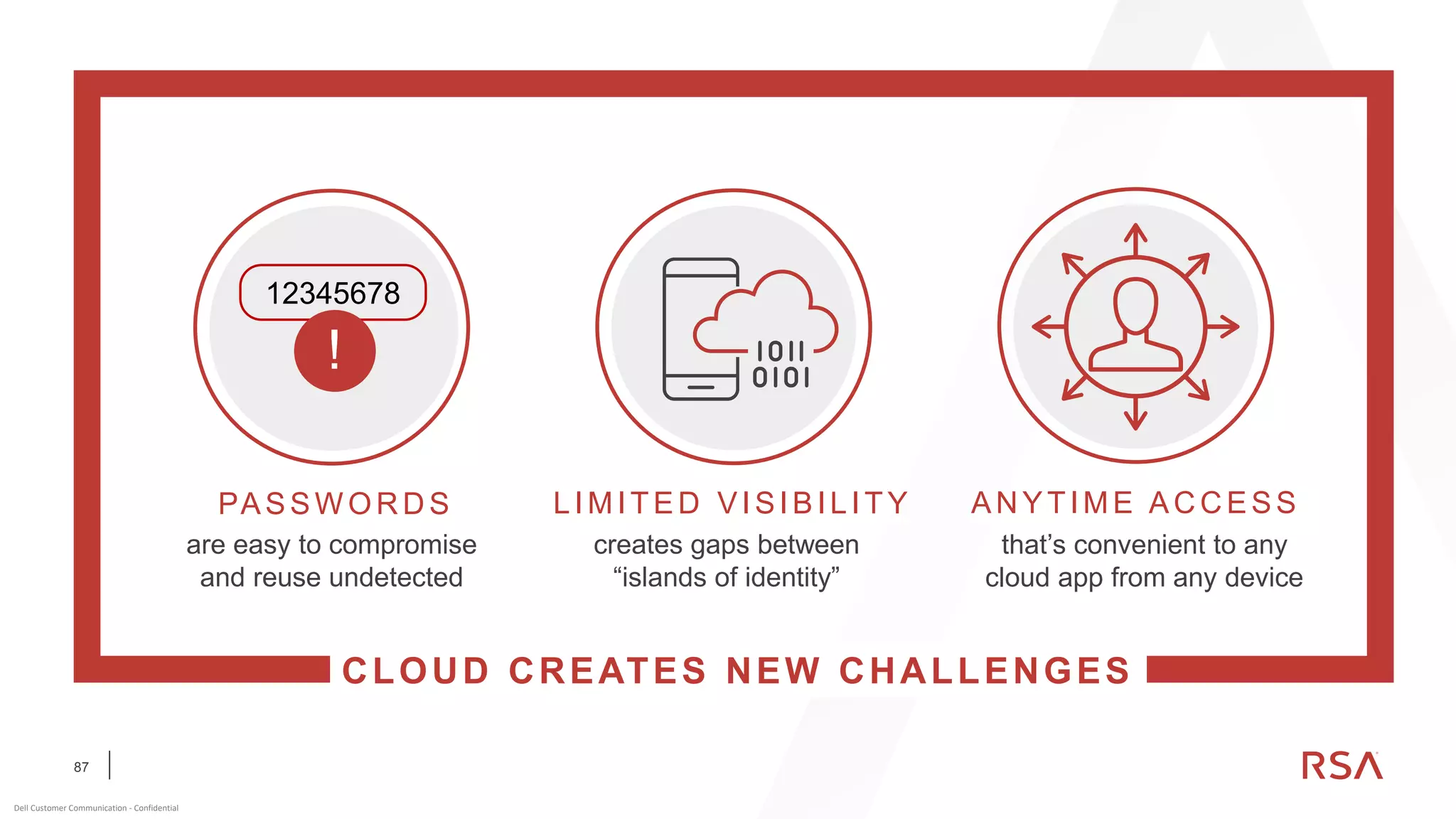
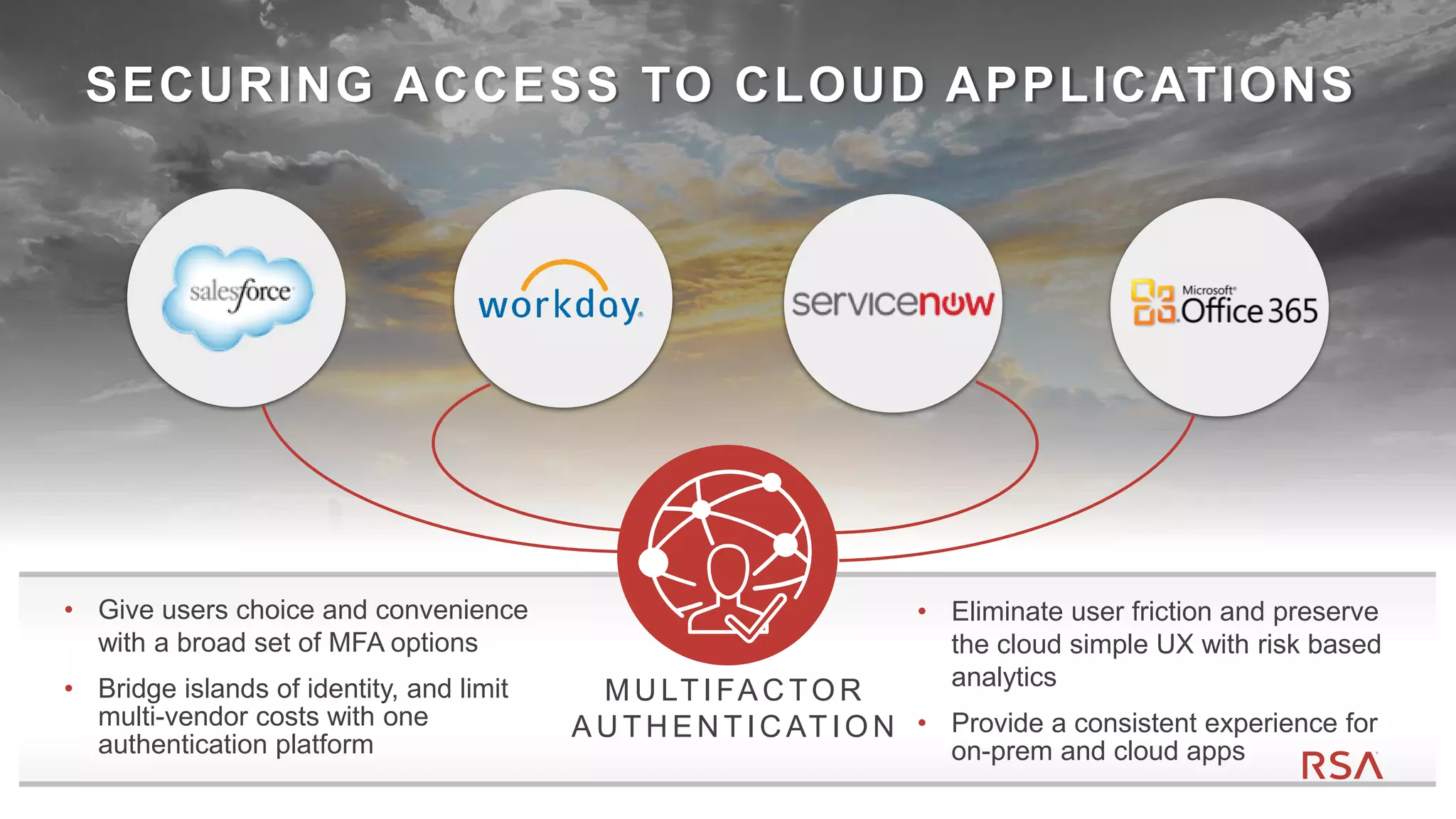
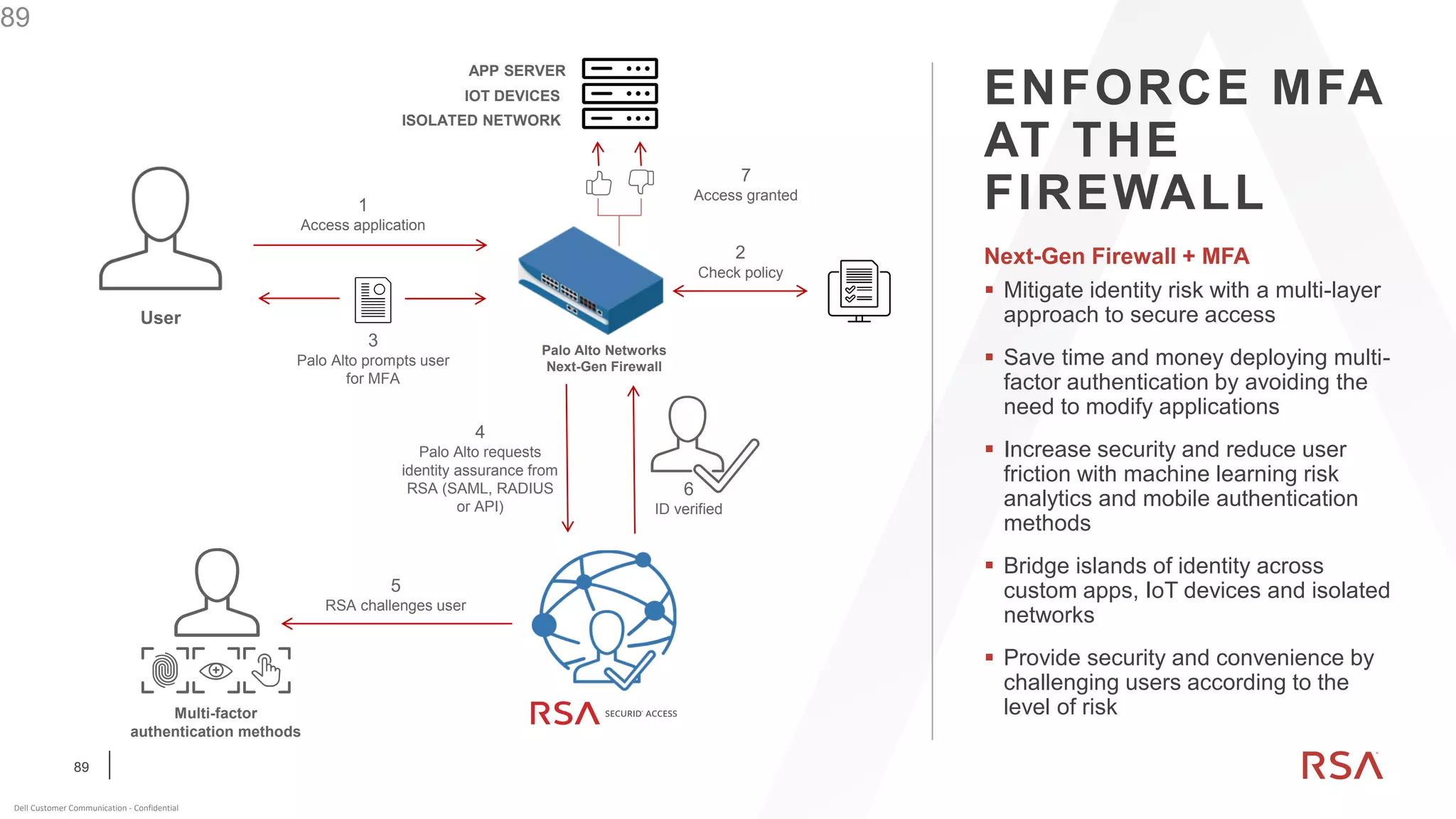
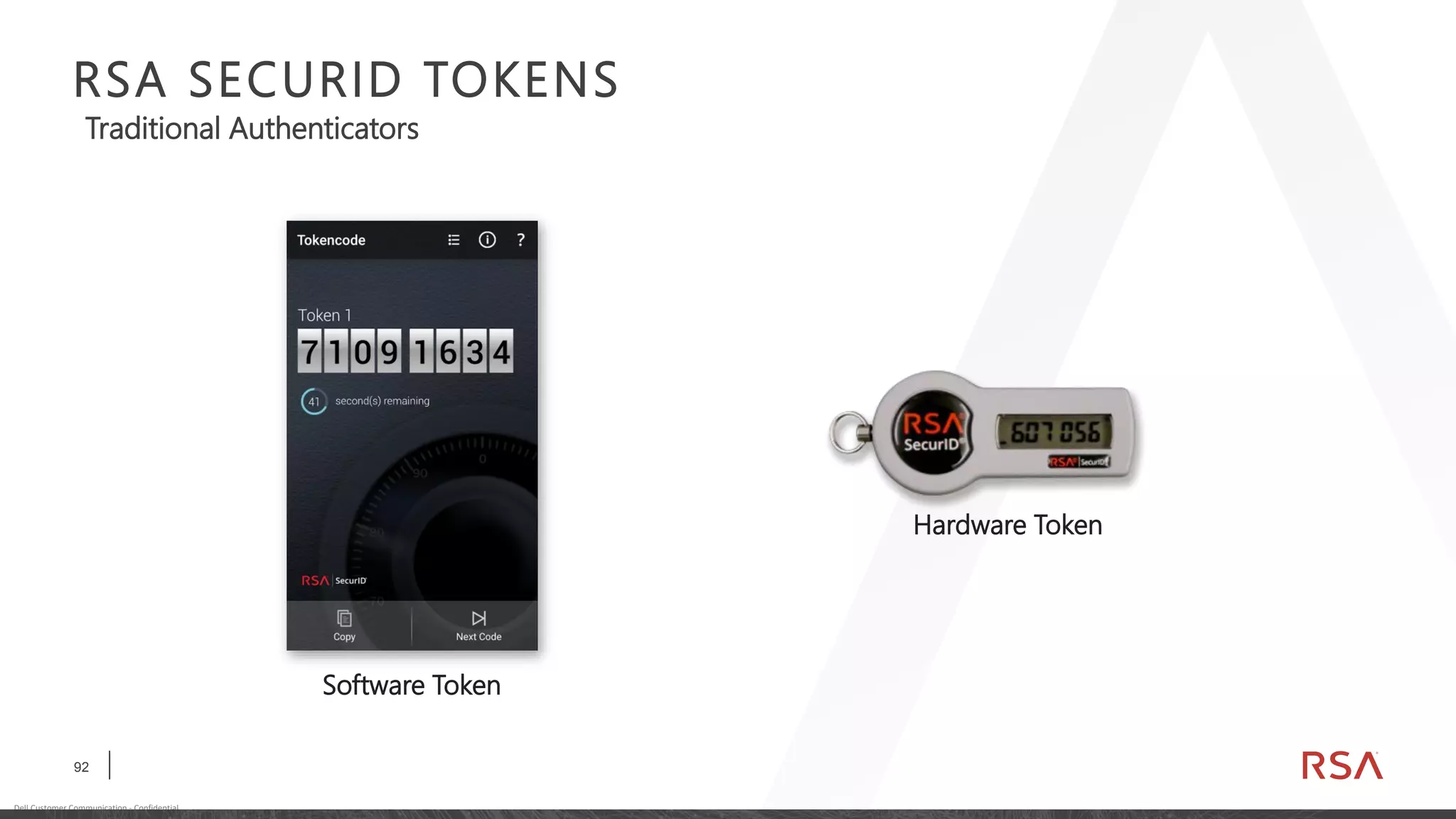
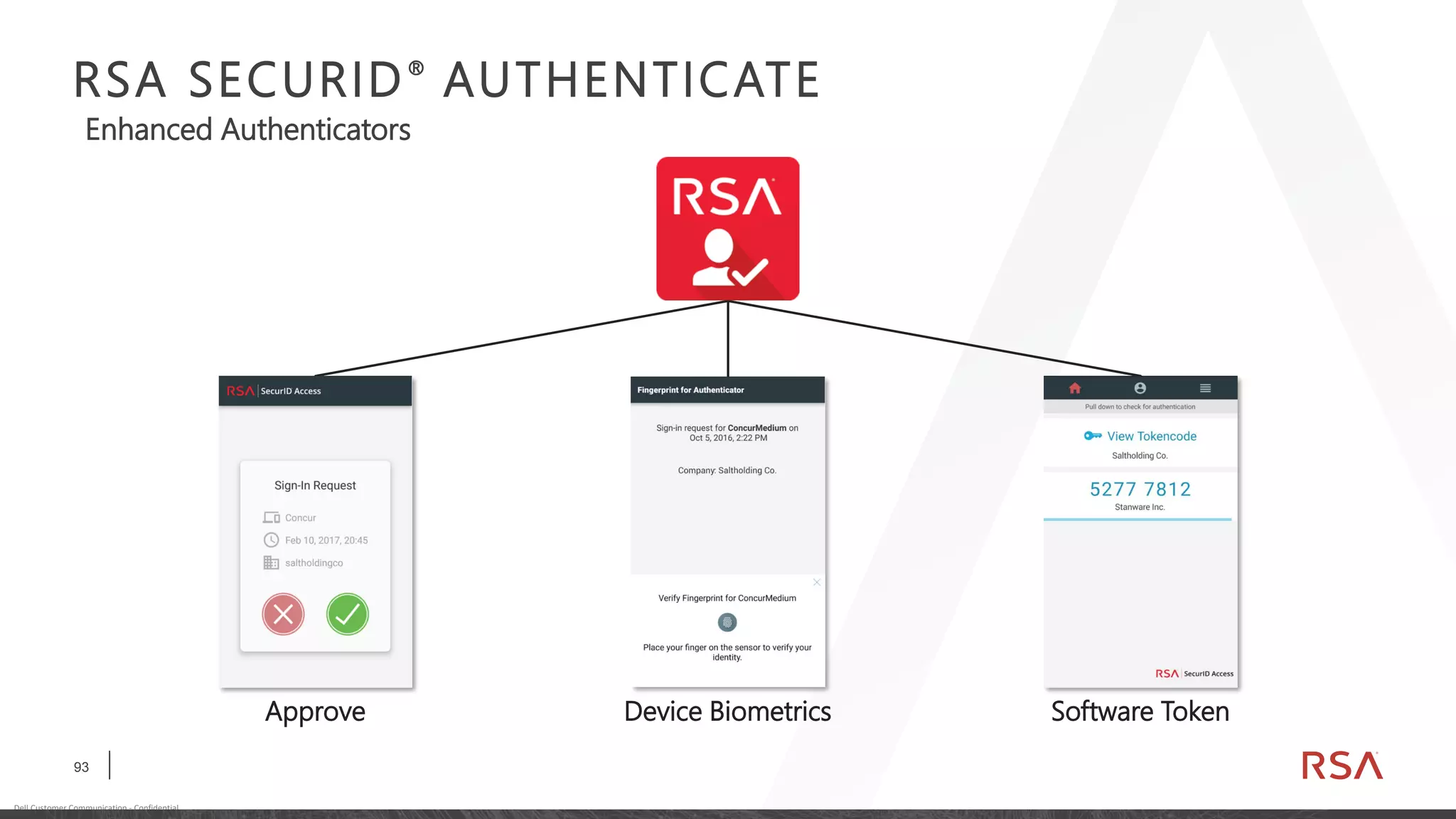
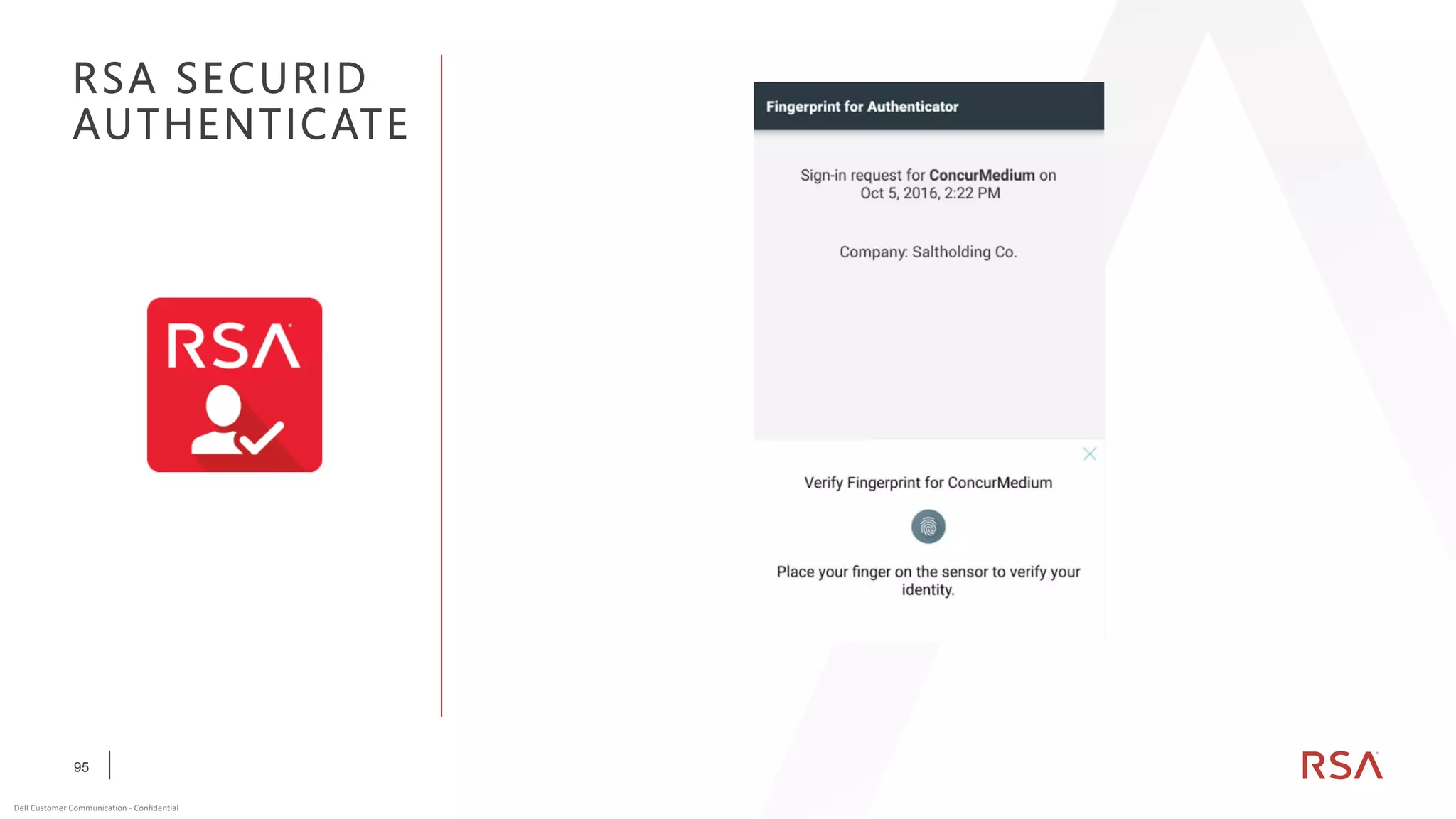
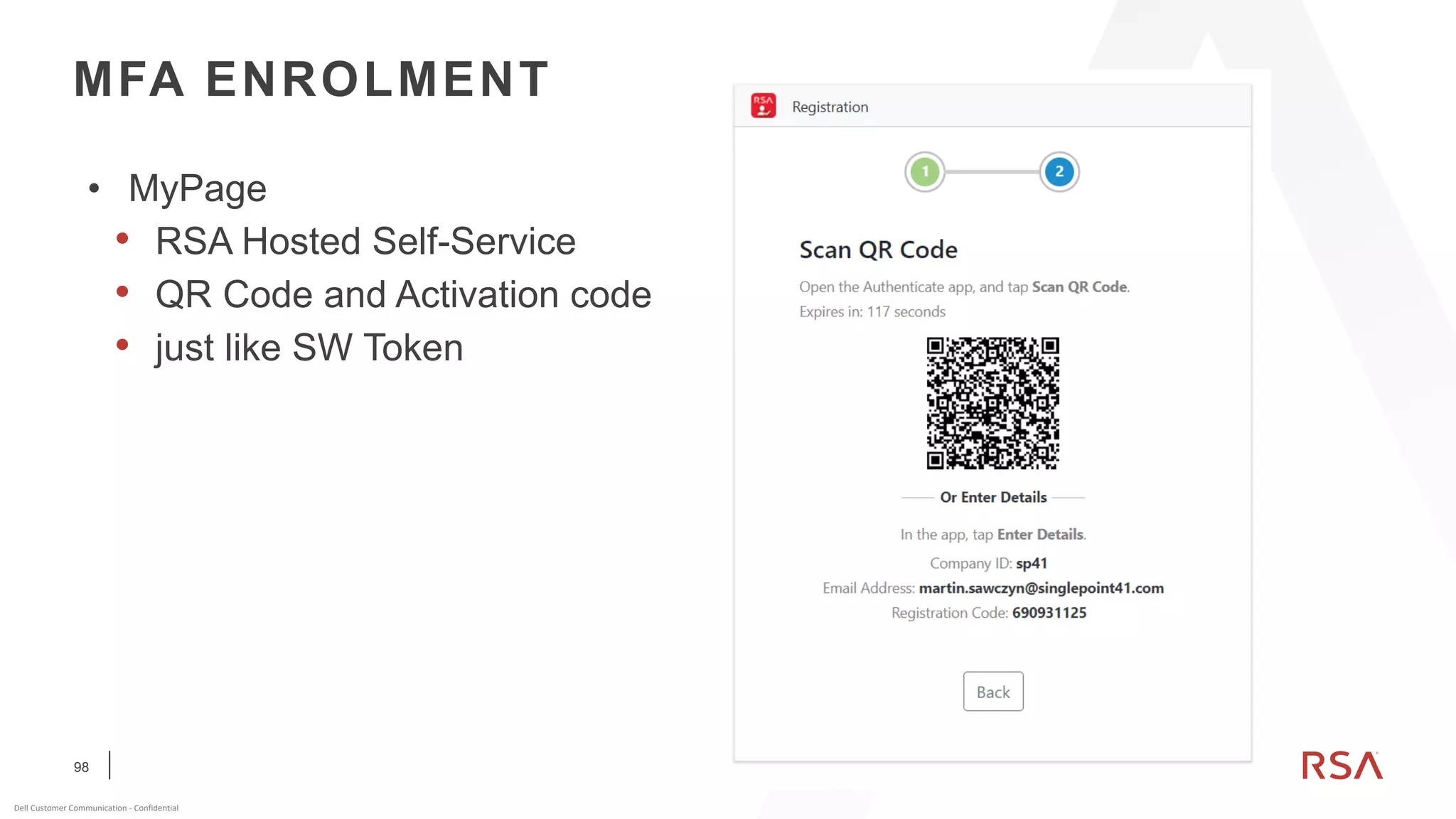
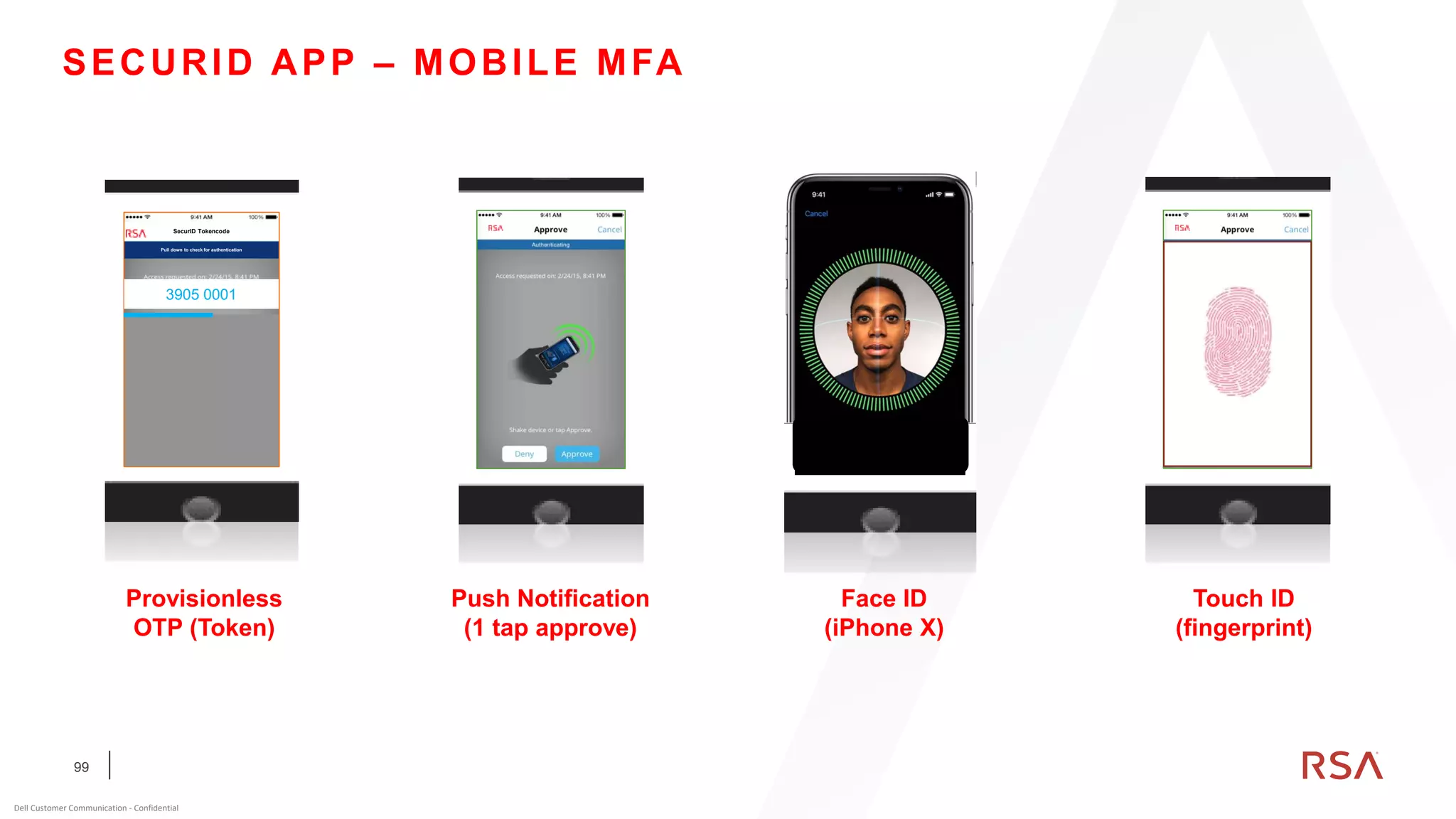
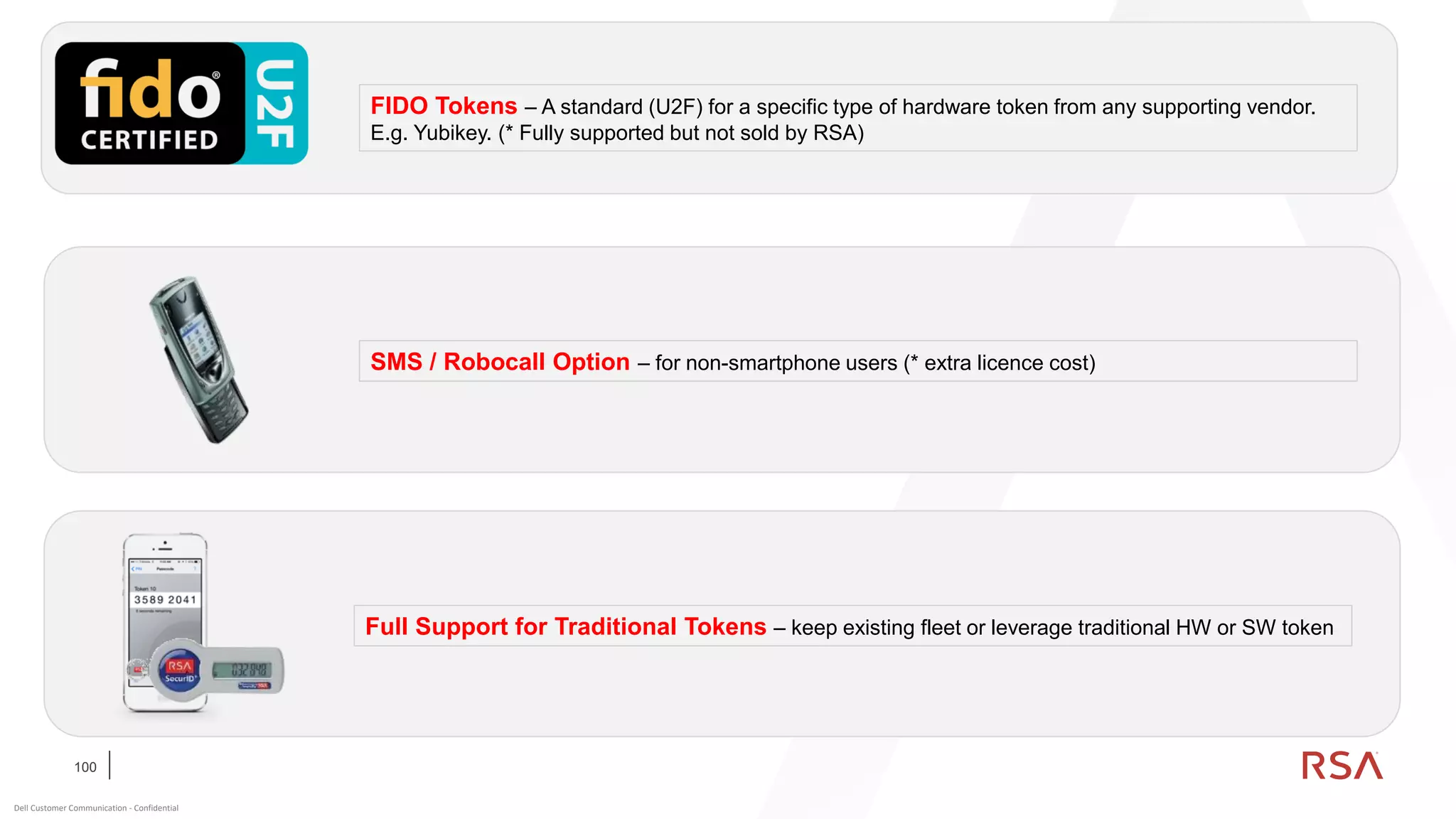
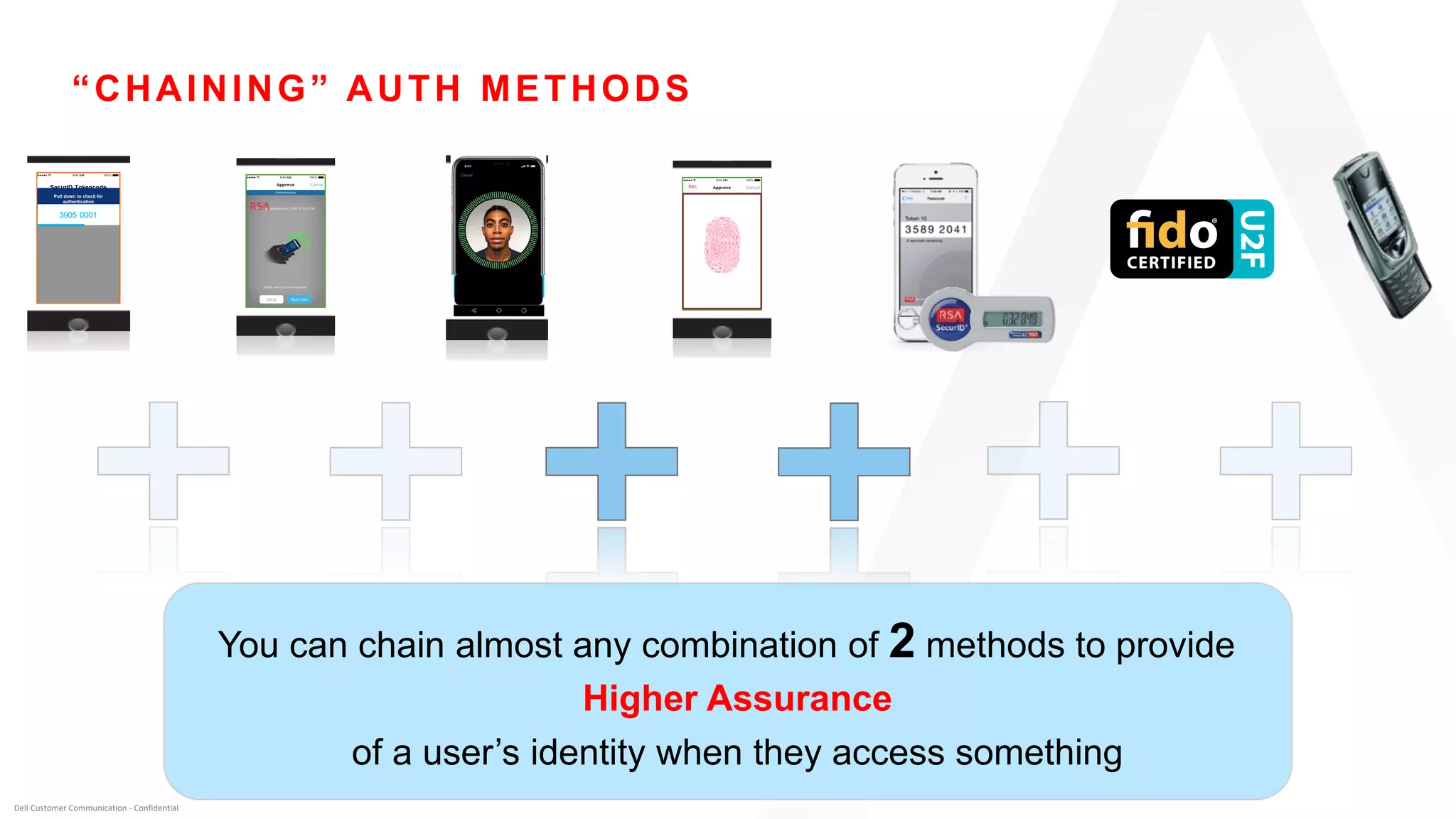
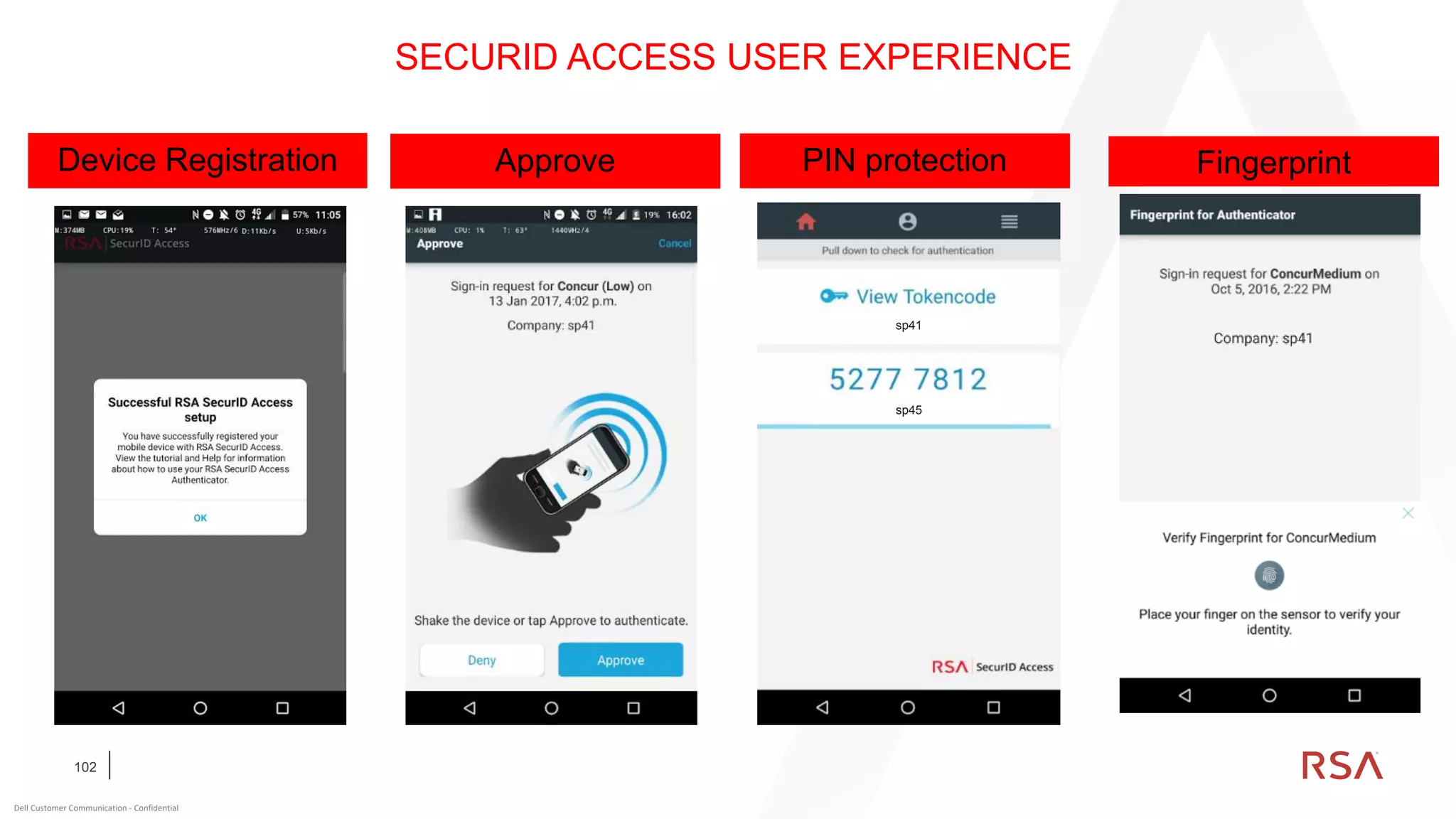
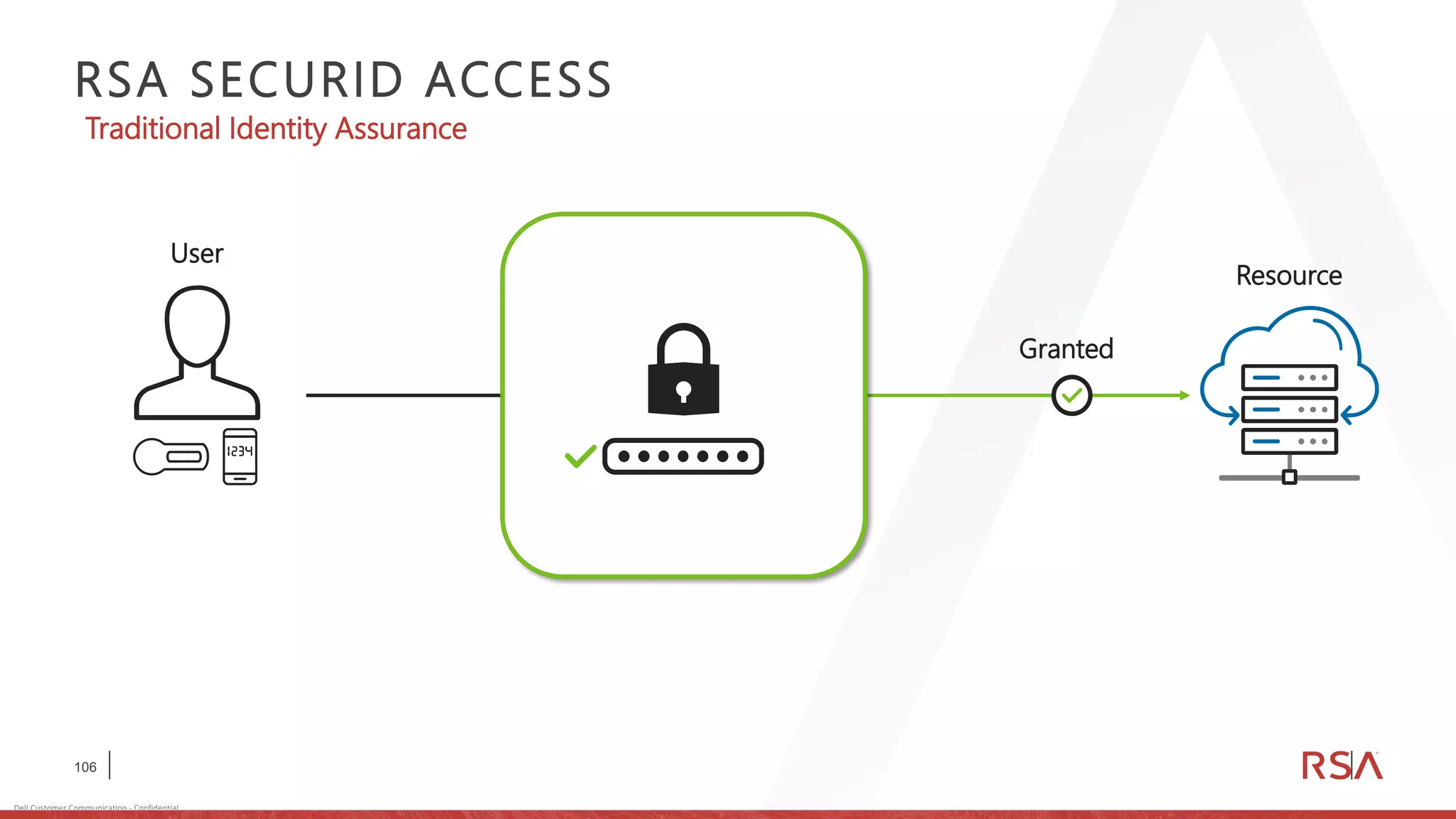
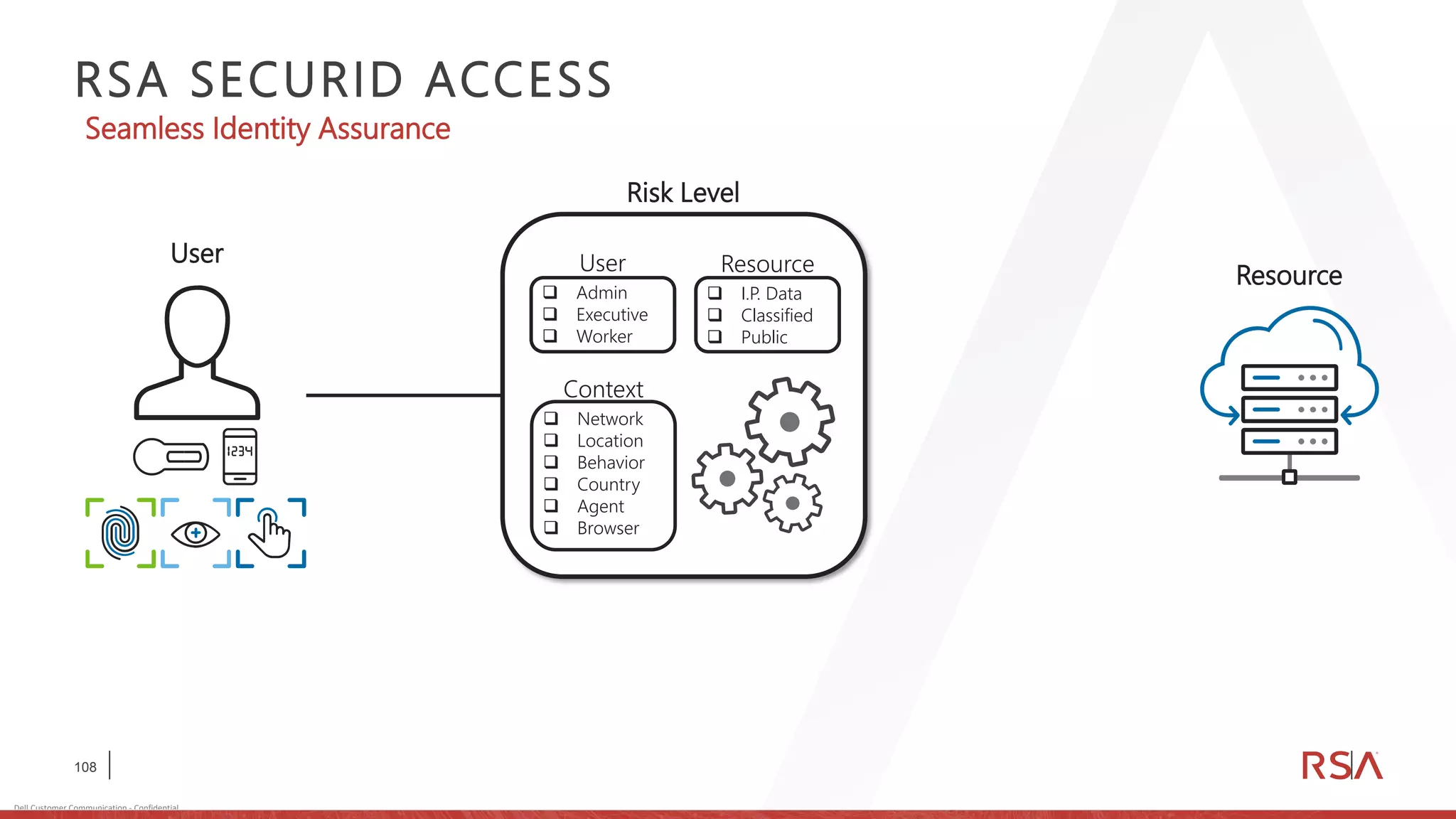
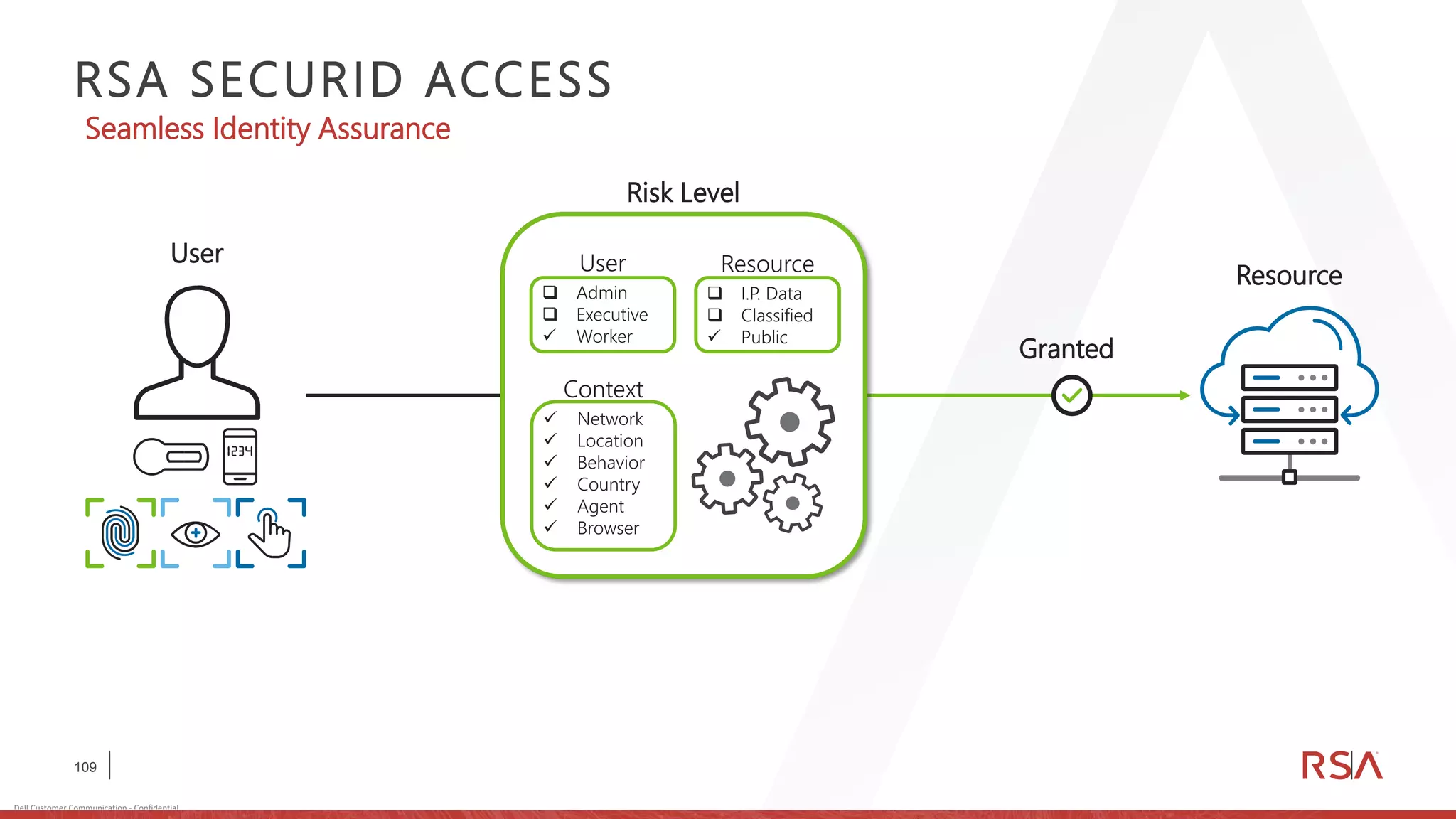
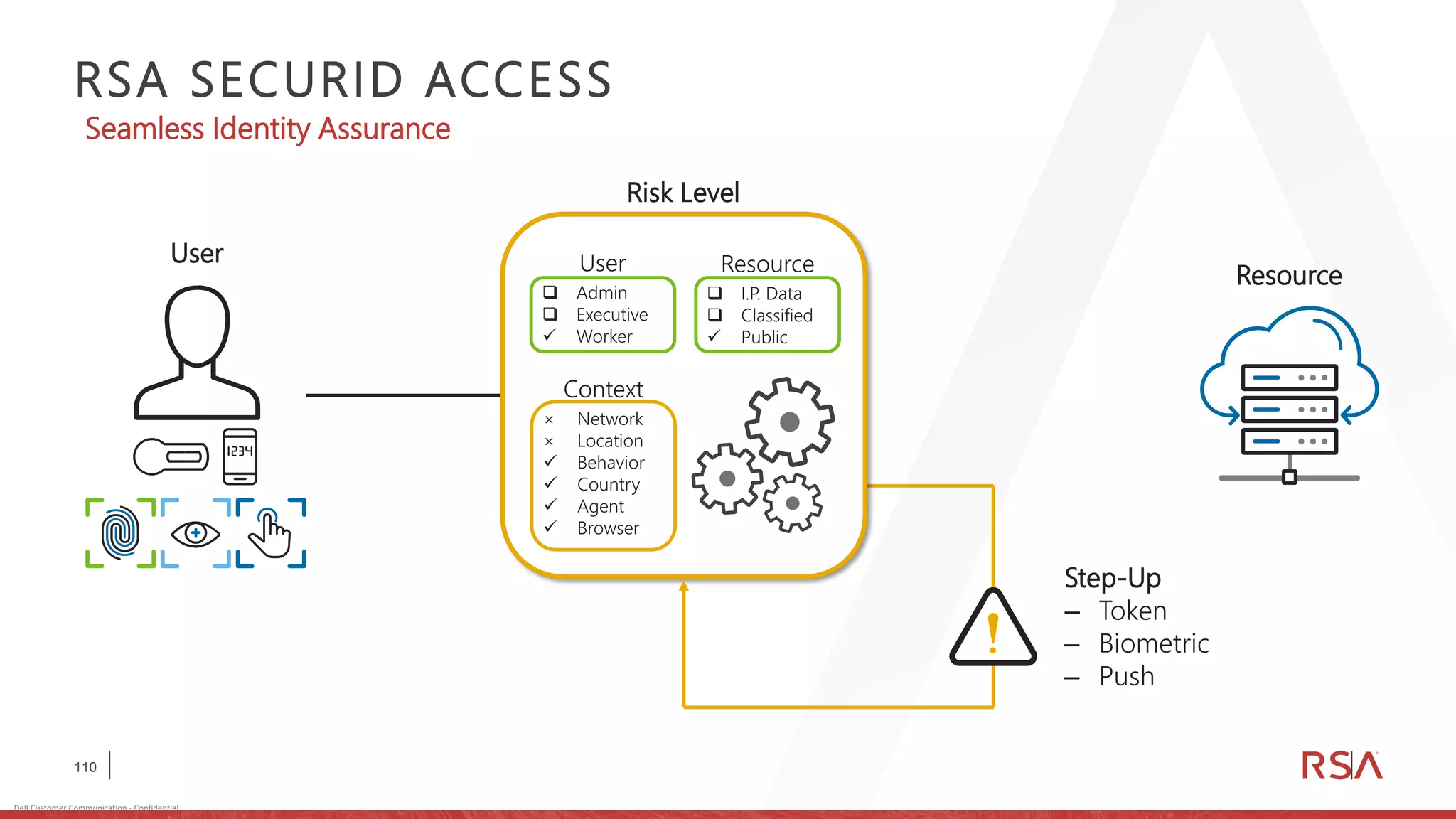
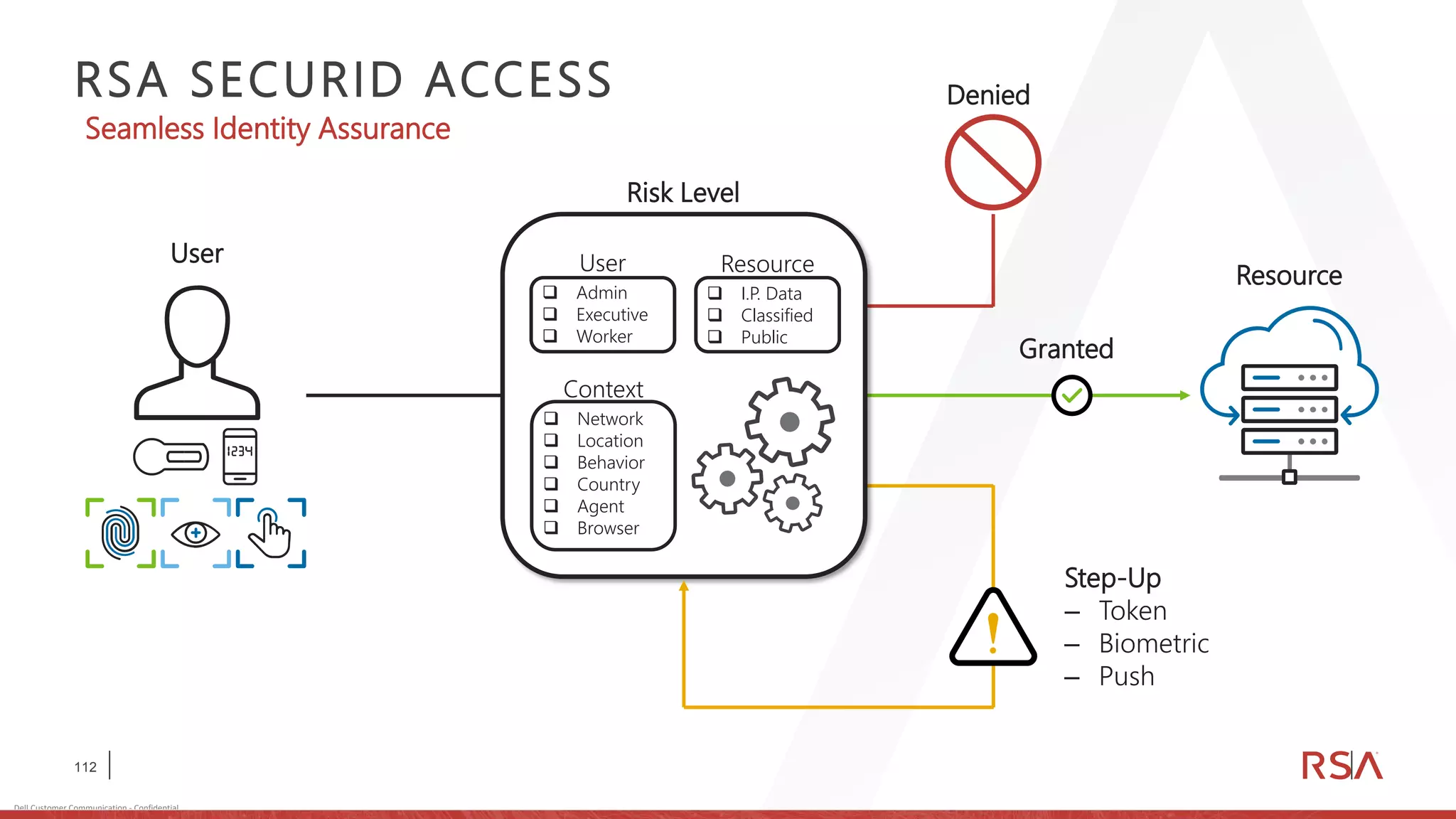
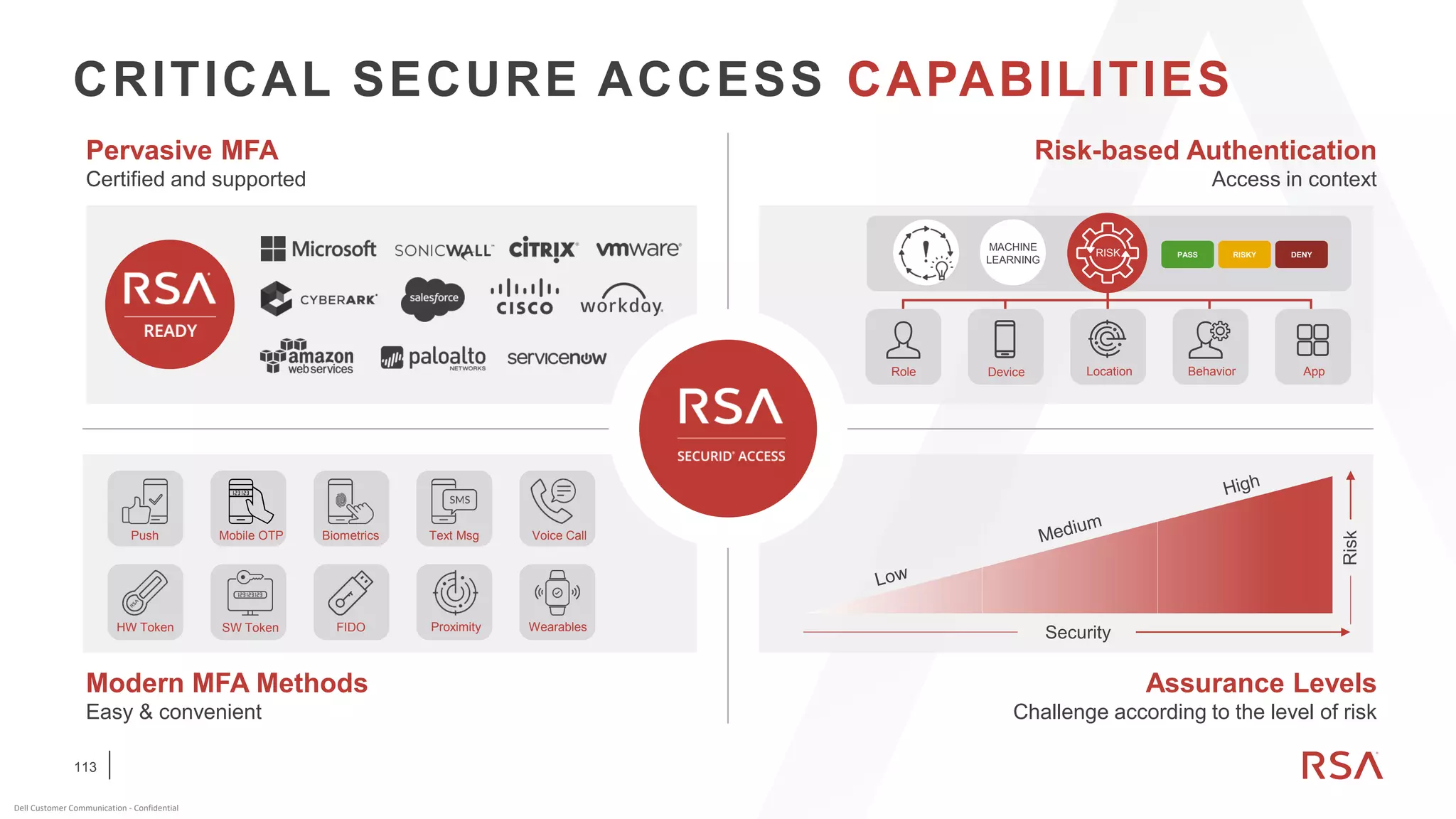
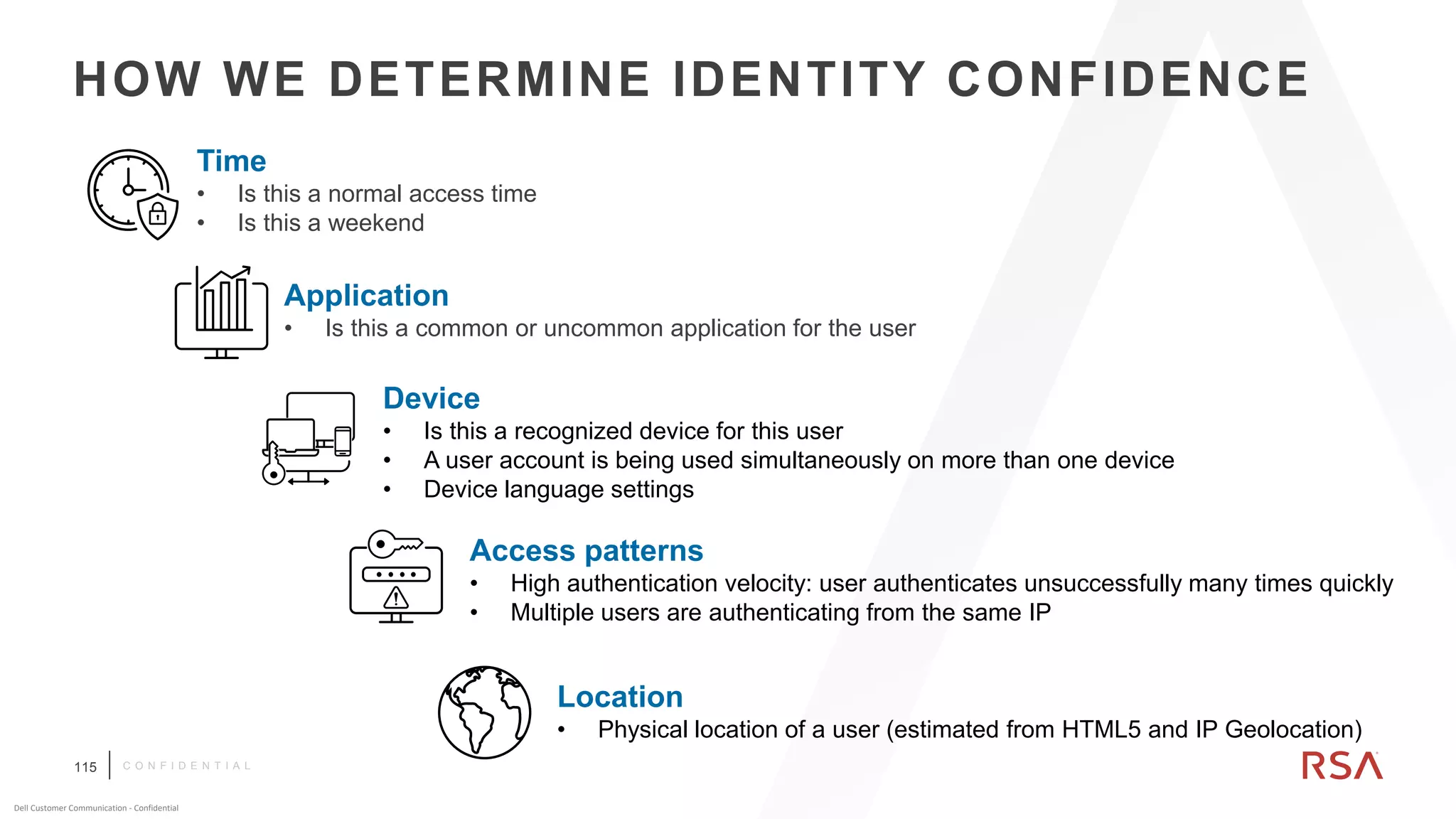
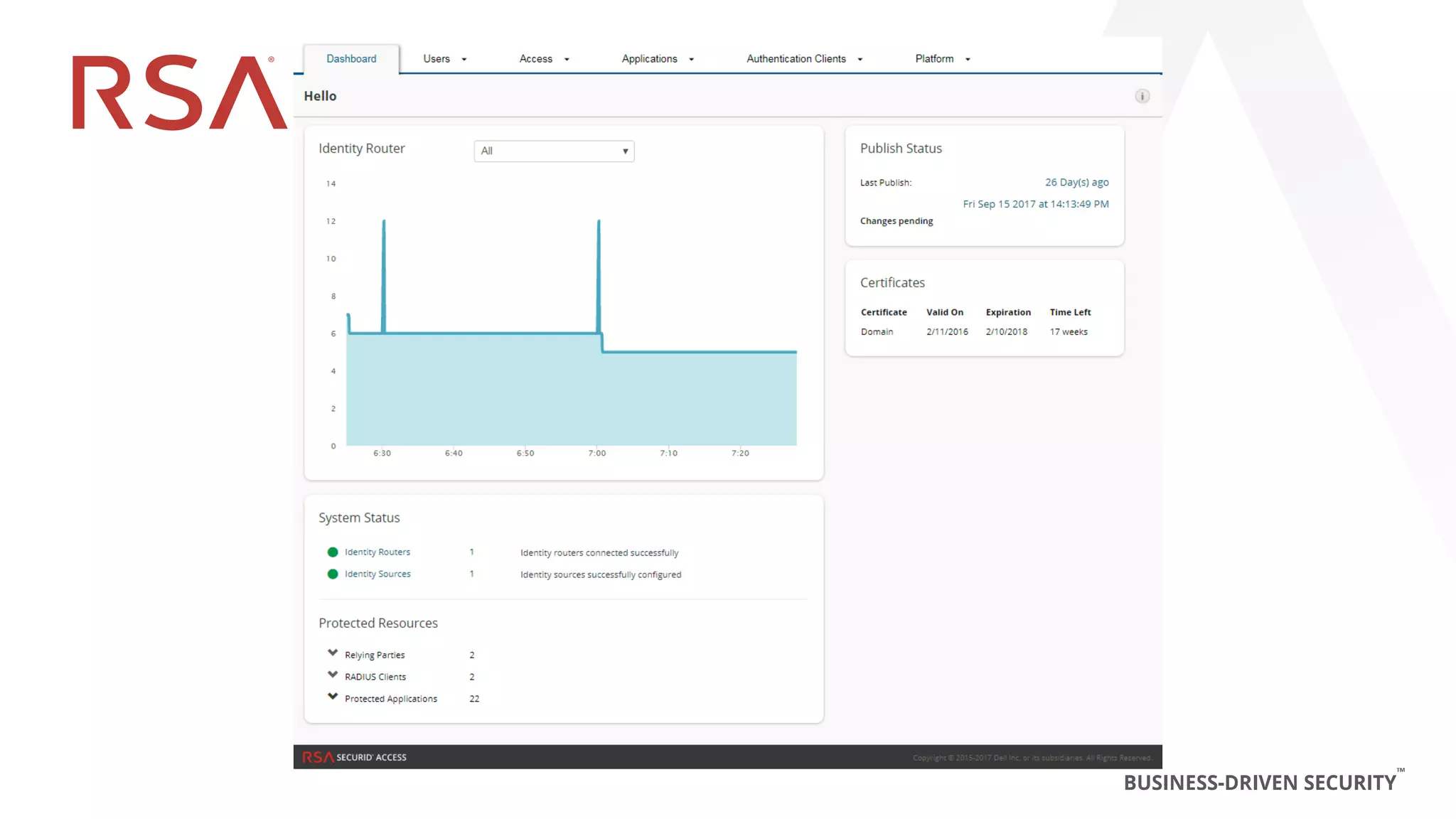
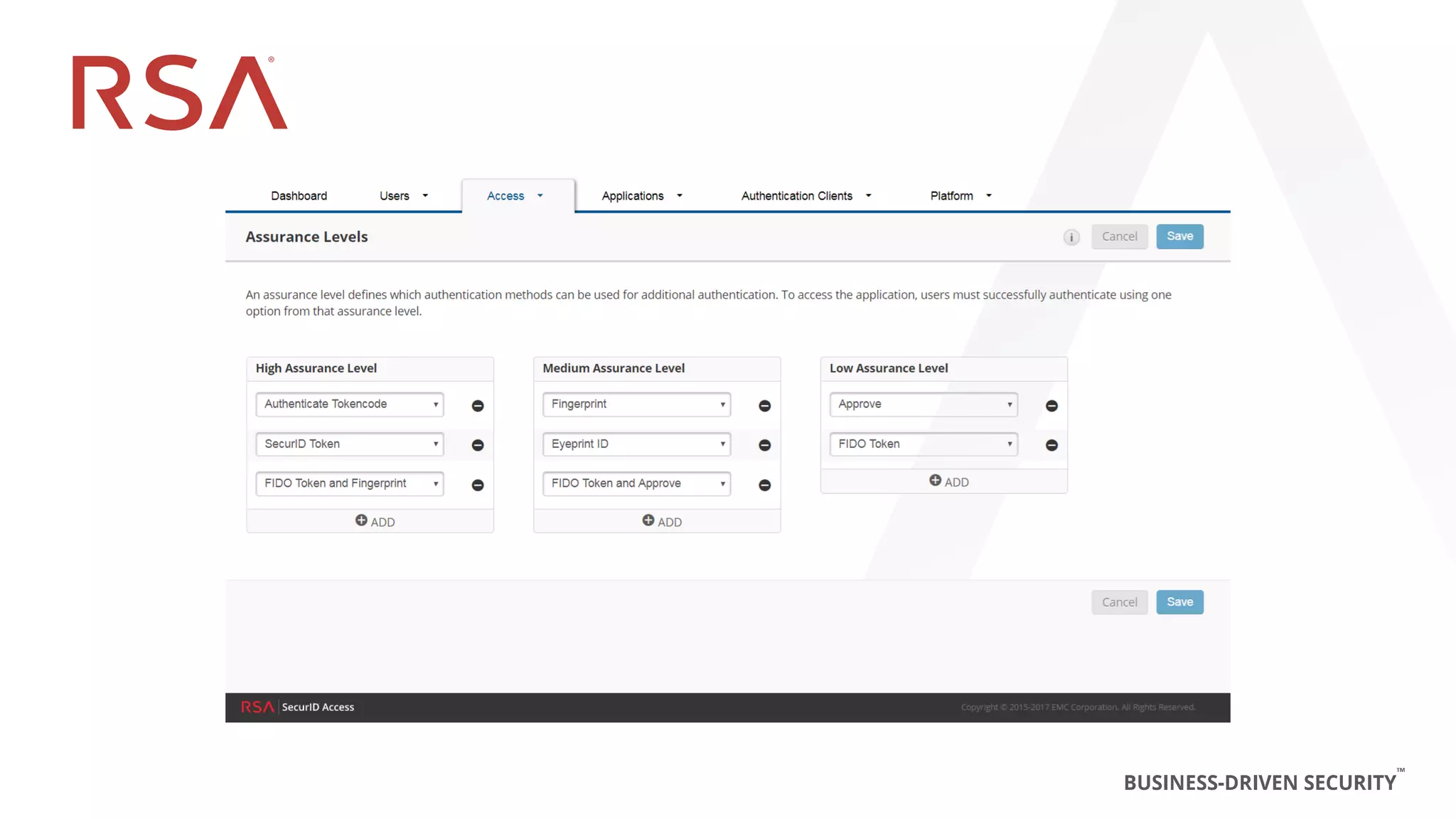
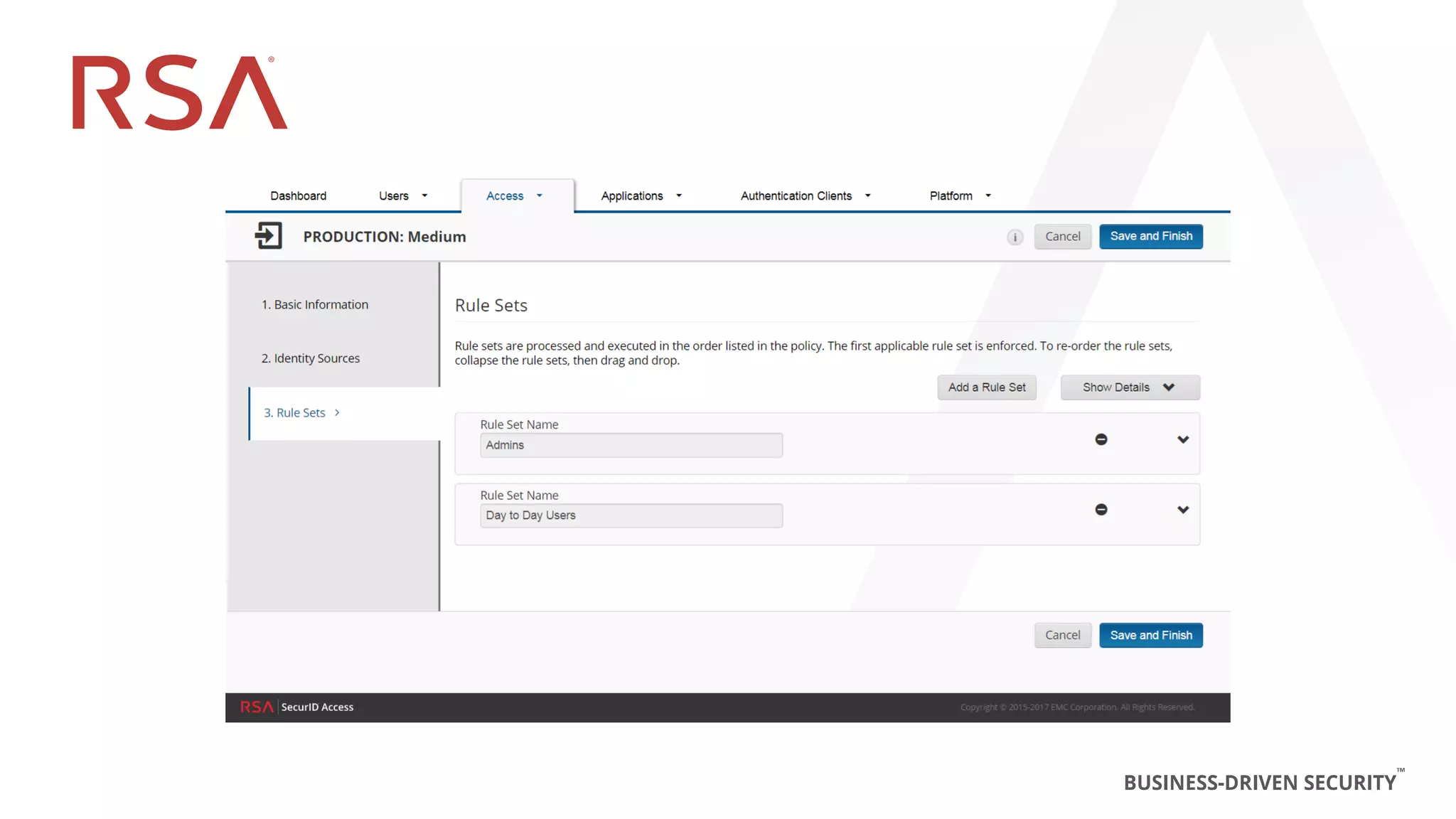
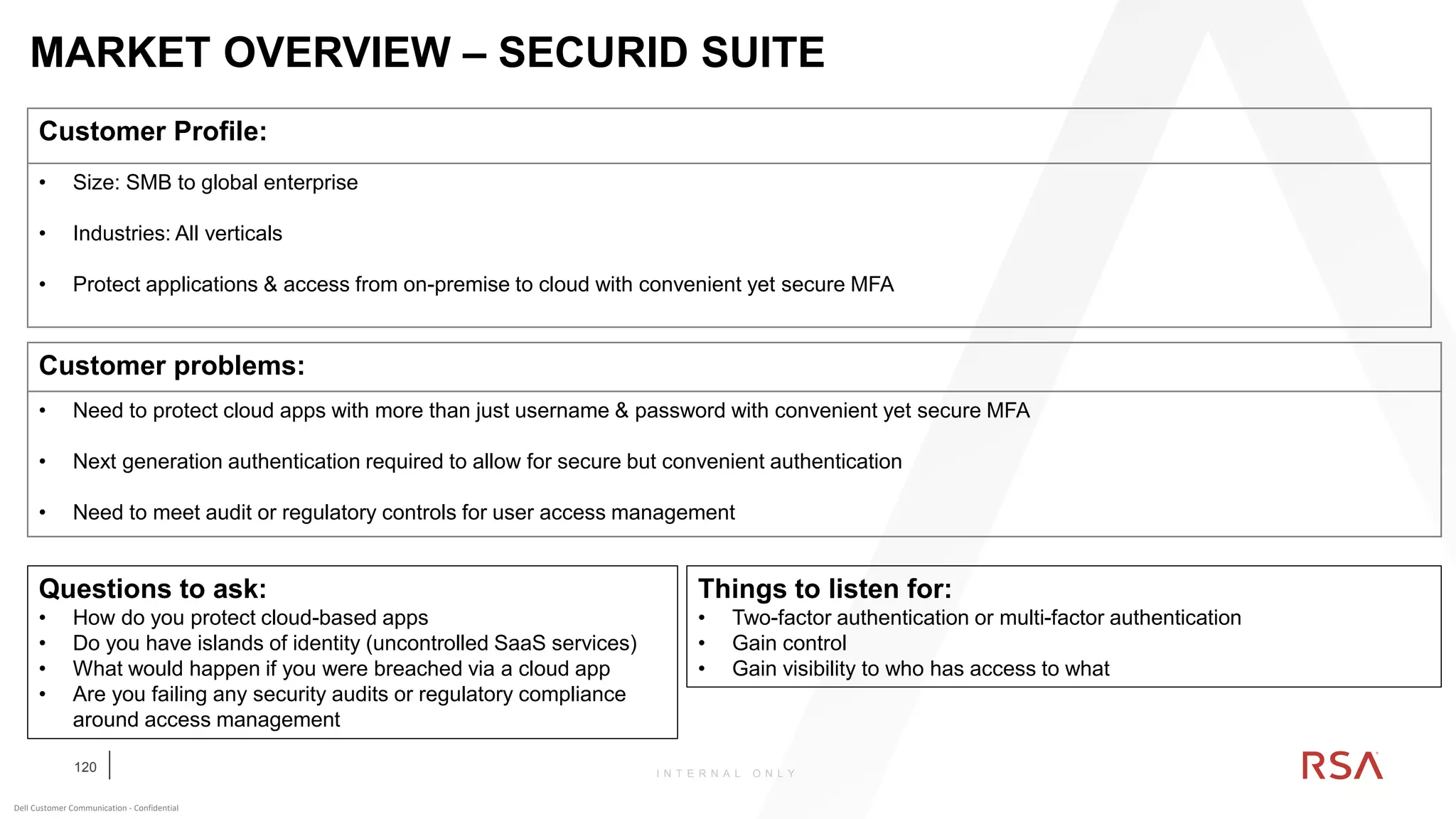
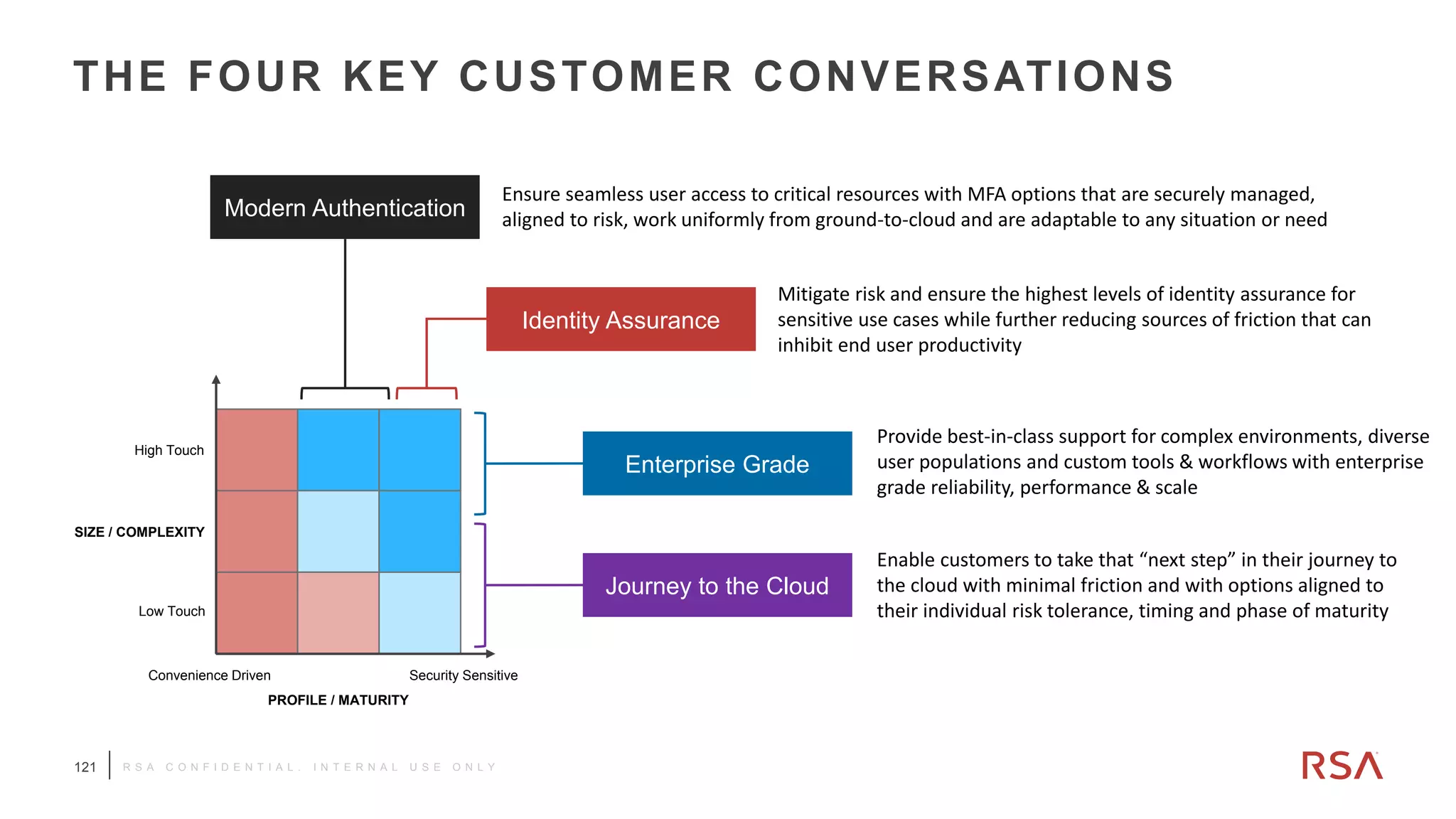
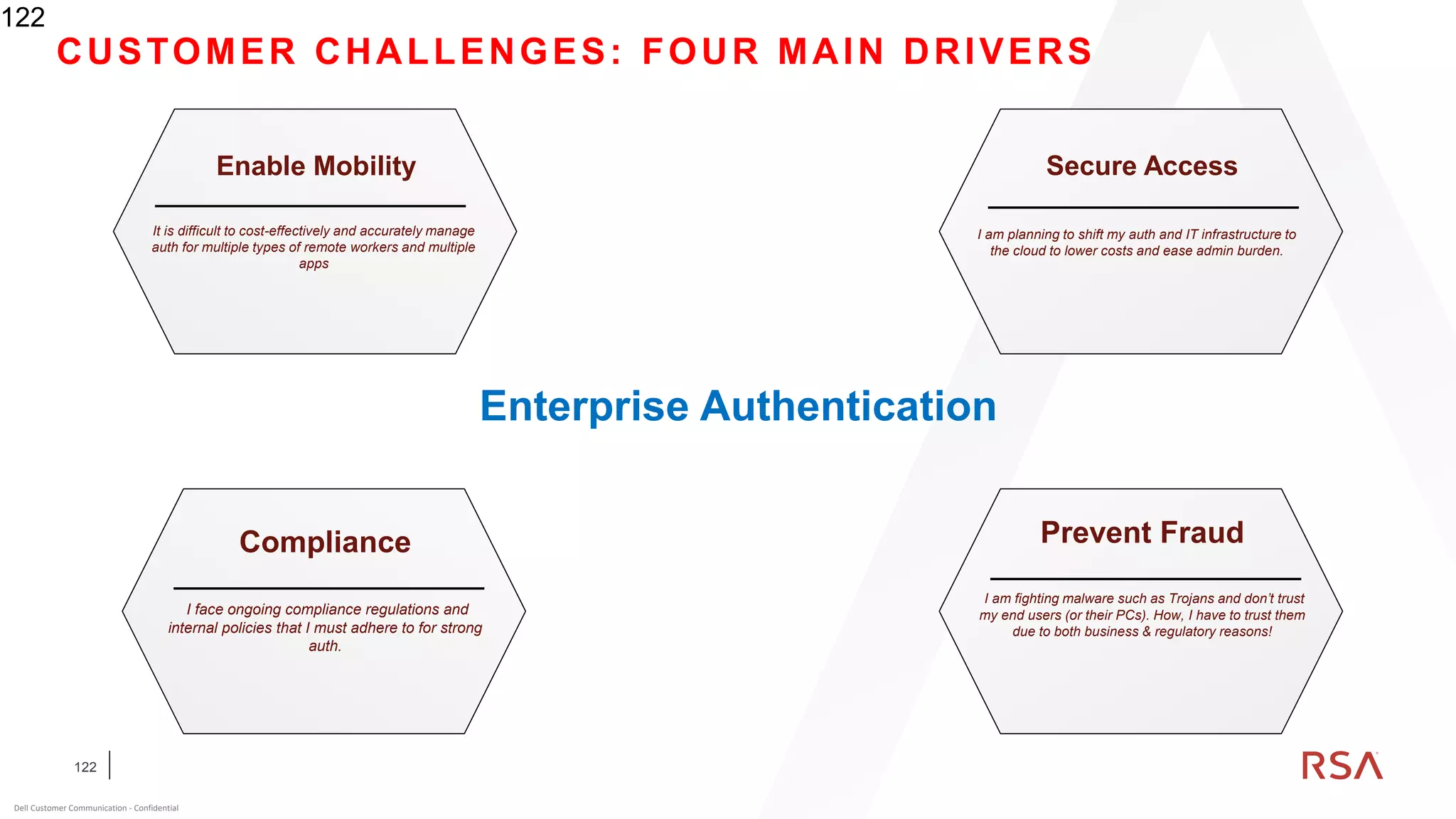
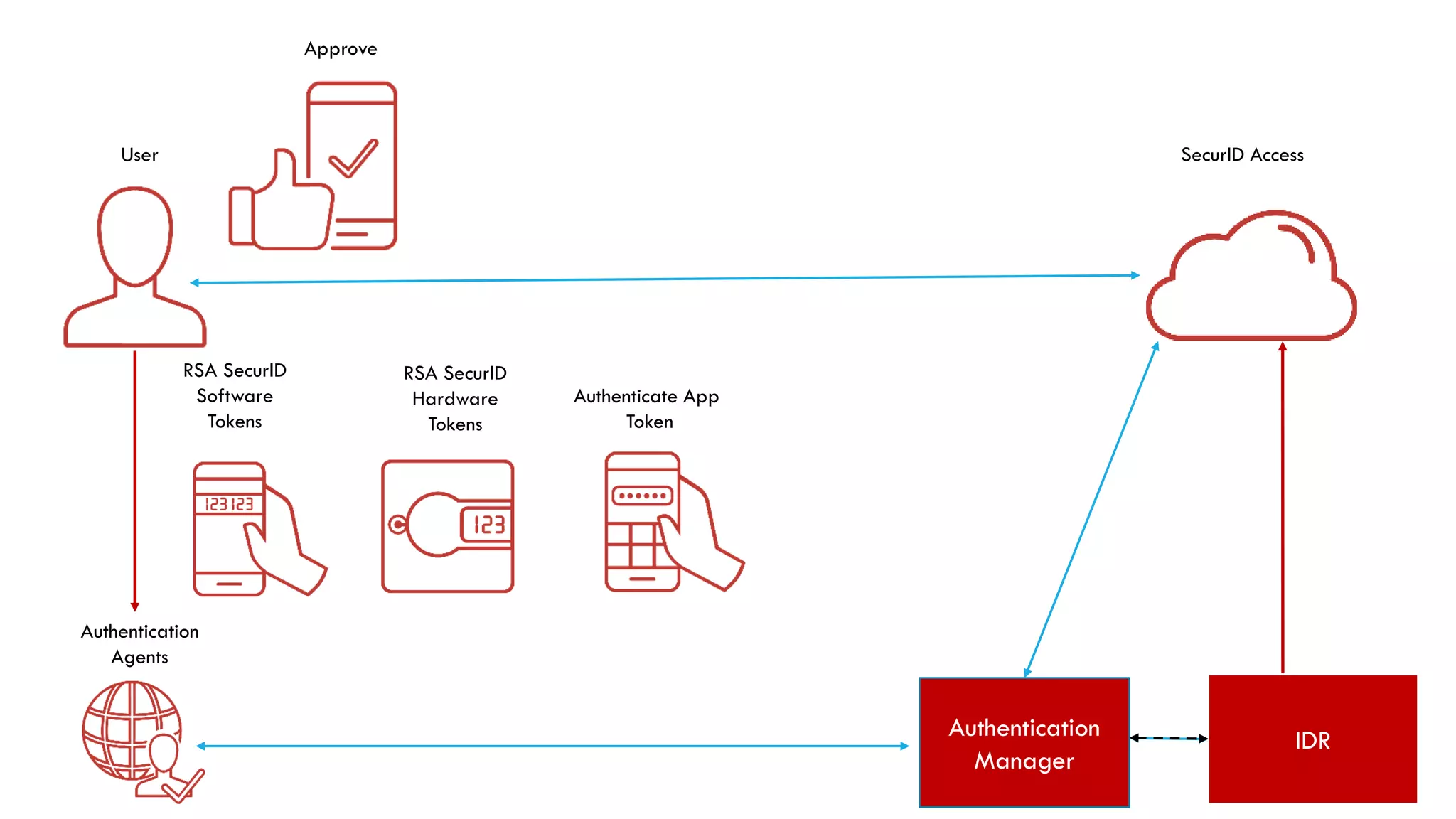
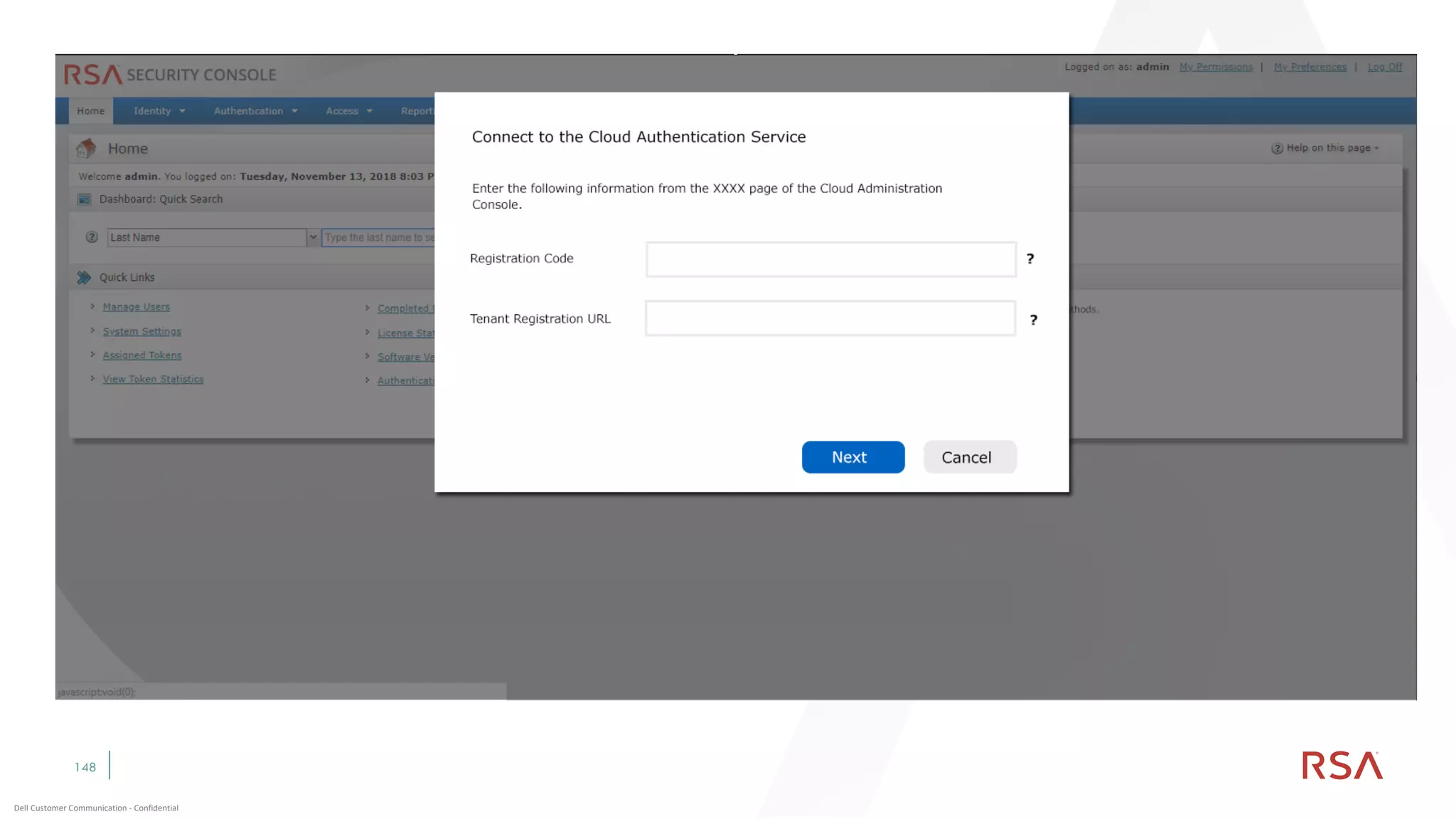
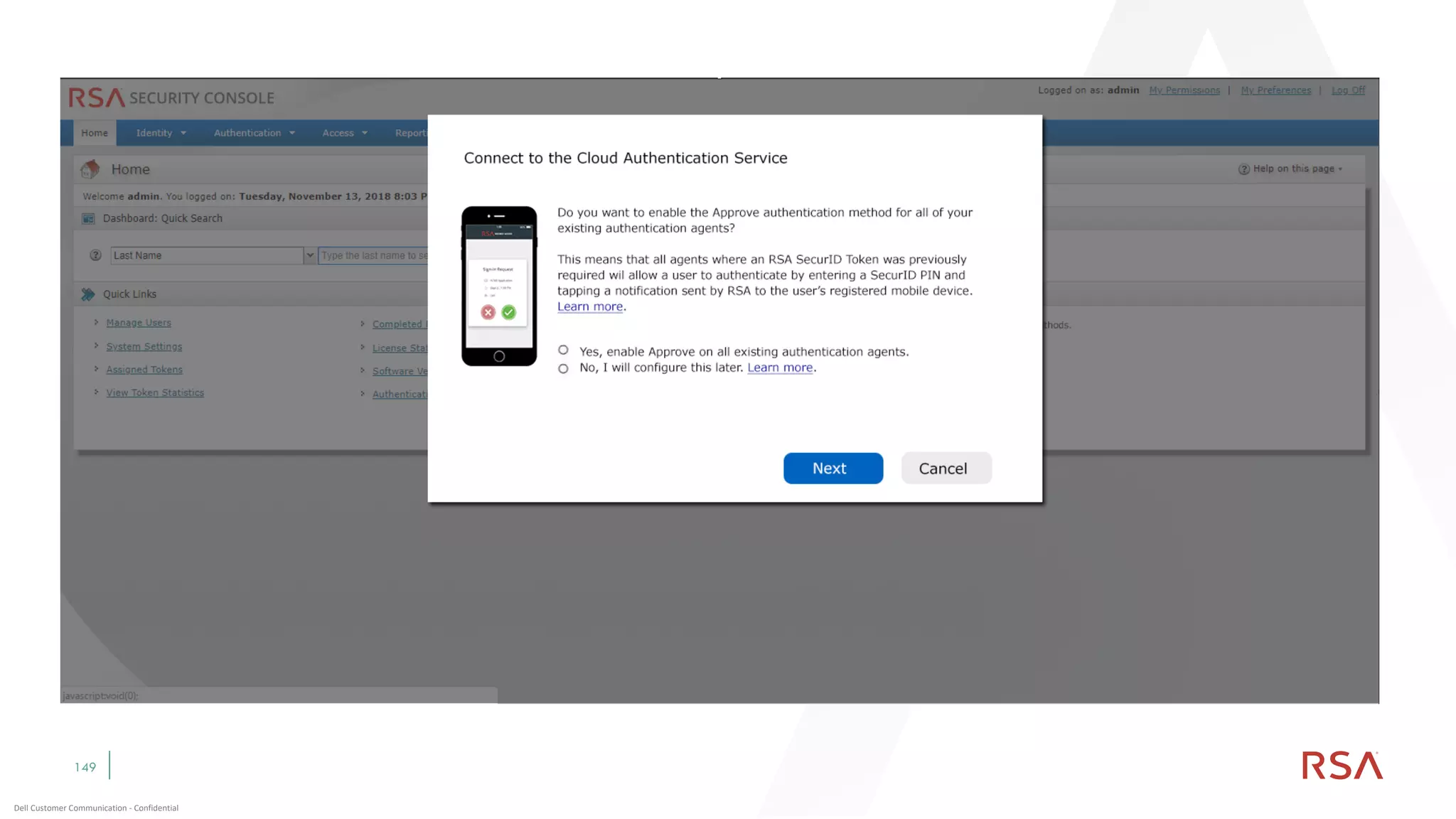
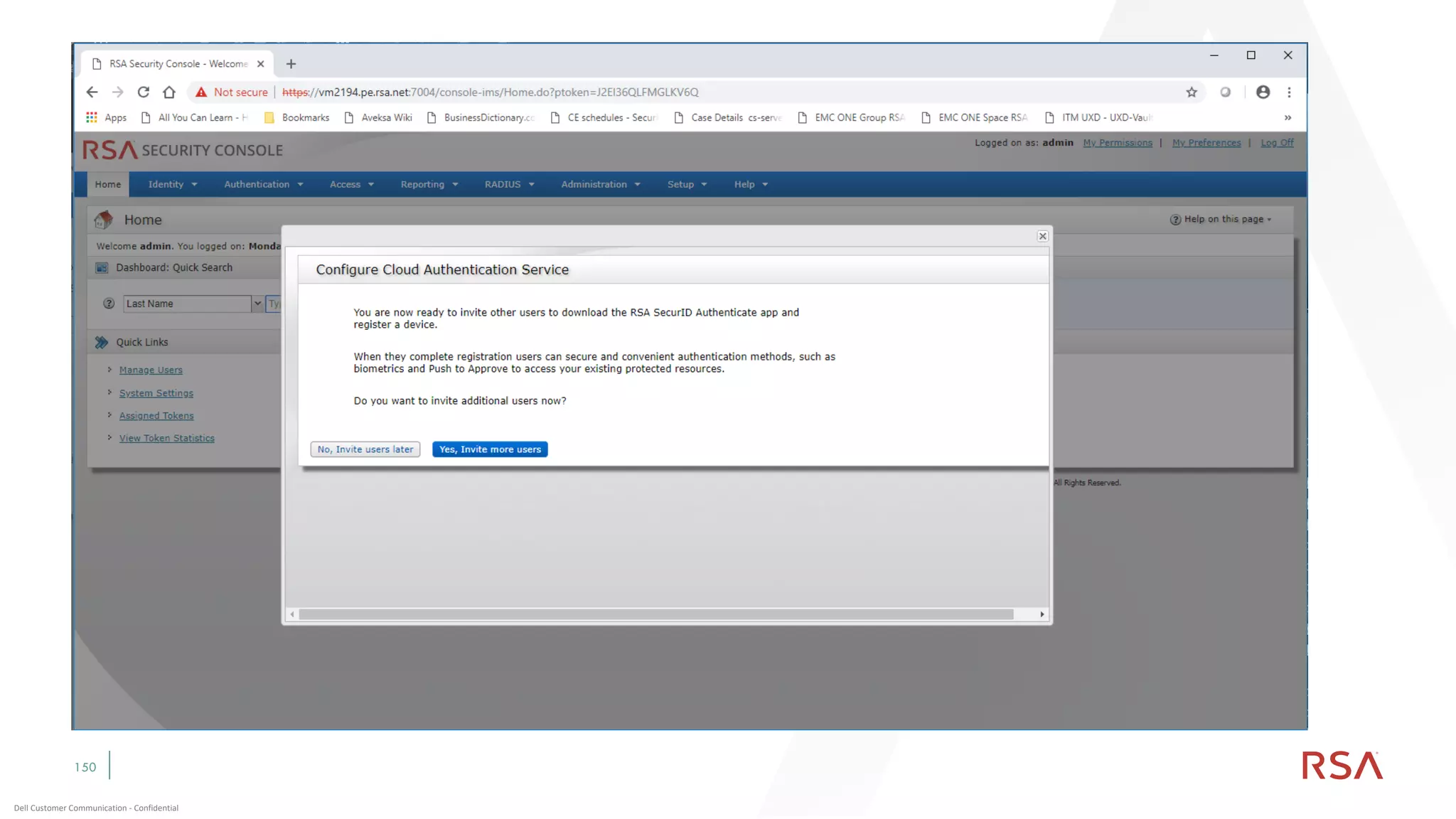
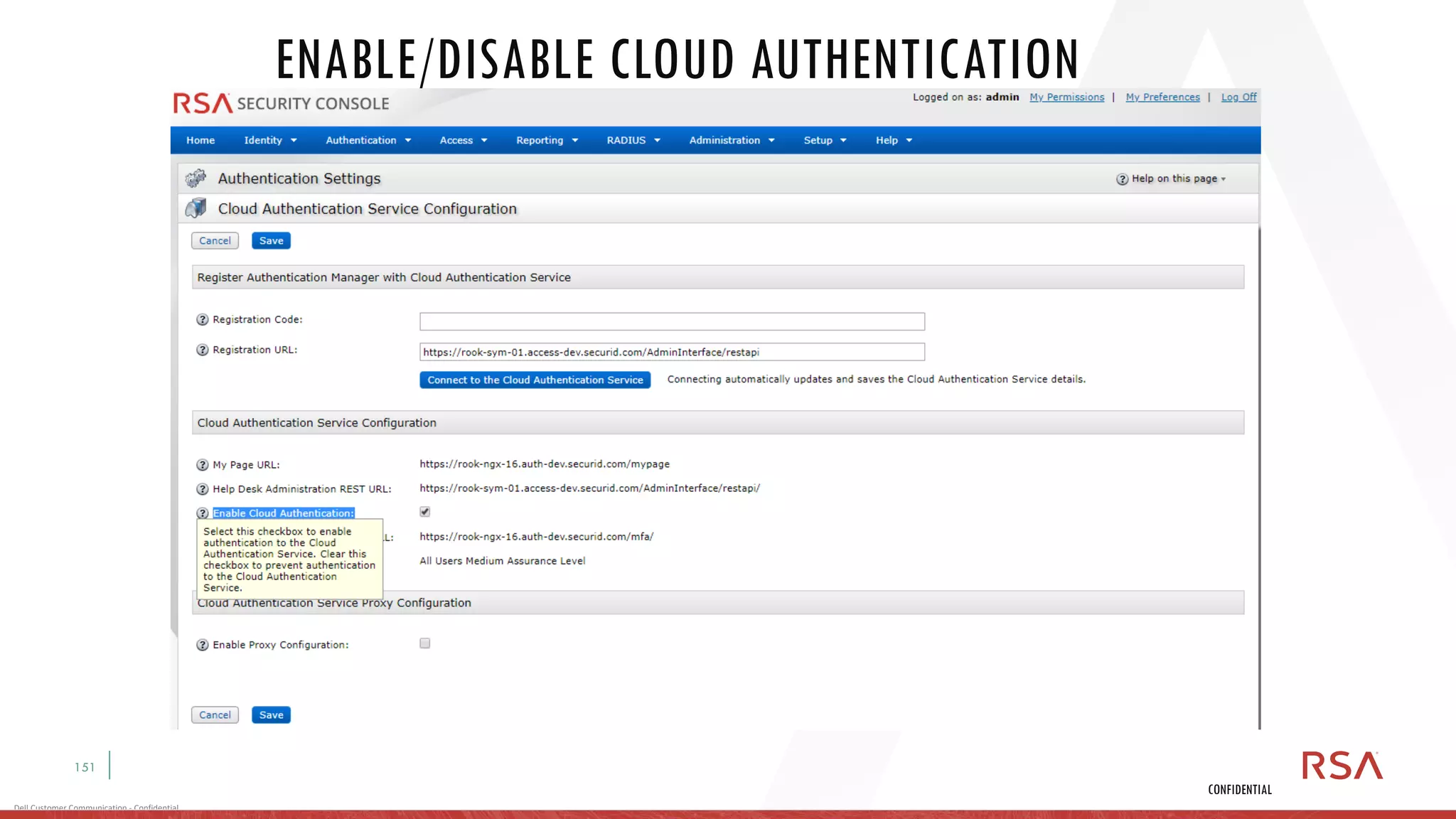
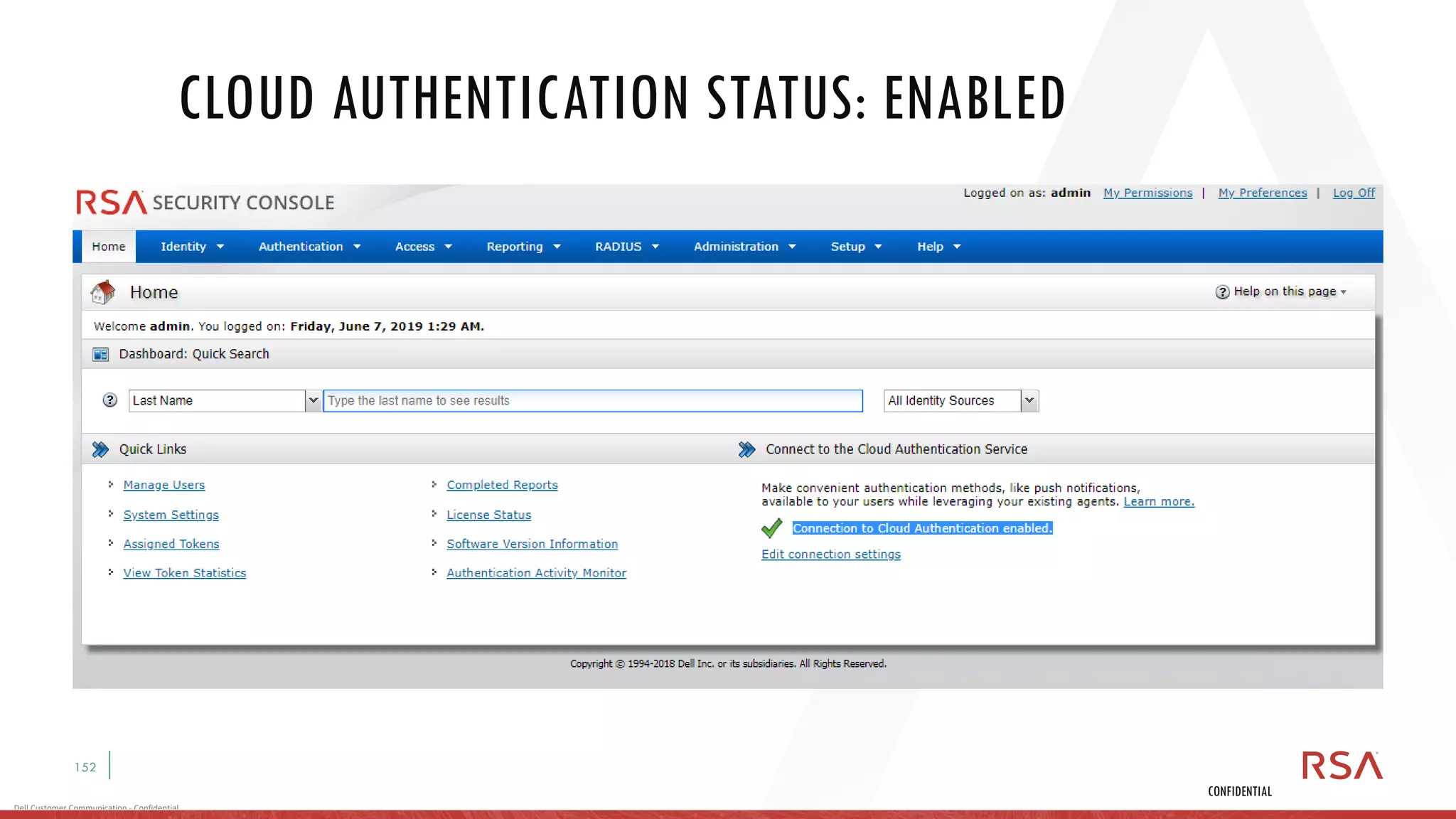
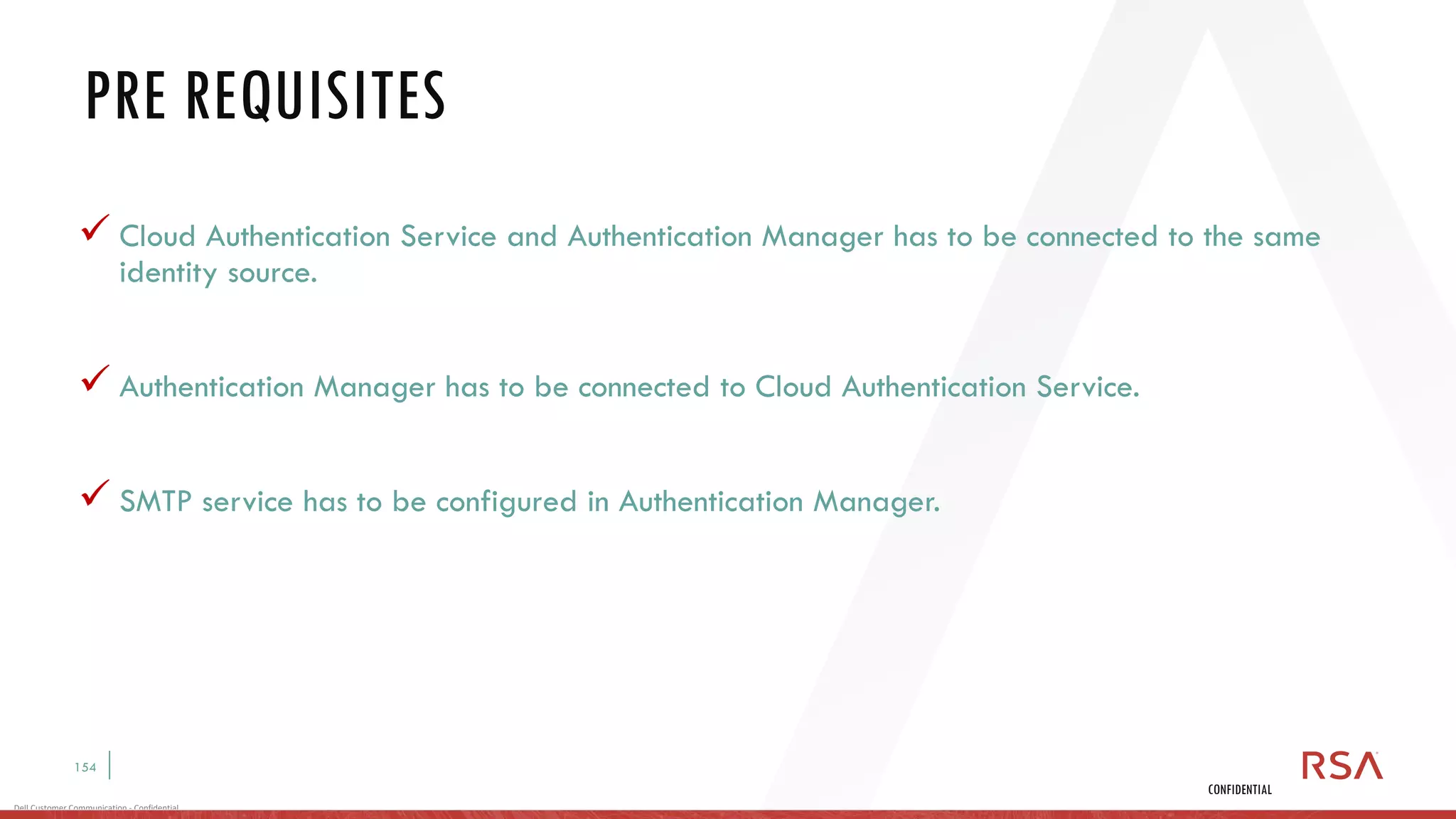
This document discusses two-factor authentication and RSA SecurID software and hardware tokens. It begins with definitions of identification, authentication, and authorization. It then describes two-factor authentication as using two of three factors: something you know, something you have, or something you are. RSA SecurID components include authenticators, agents, and an authentication manager. The document discusses hardware and software SecurID token options and deployment methods. It explains how hardware tokens work and are designed to be secure and long-lasting. Software tokens allow authentication from mobile devices and desktops without hardware.