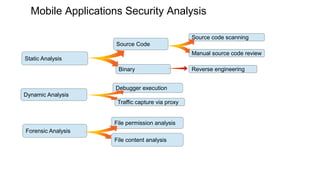
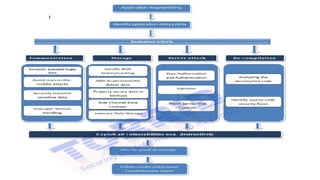
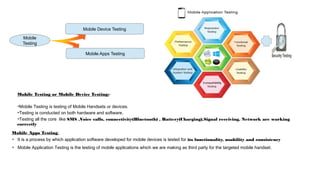
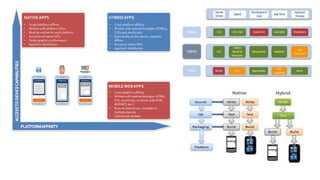
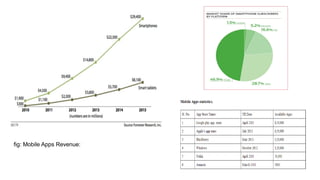
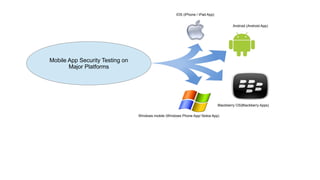
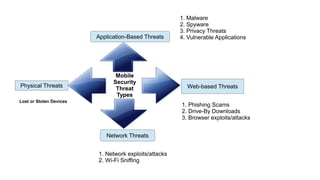
Mobile application security testing is important to identify vulnerabilities and protect sensitive user data. The key concepts of mobile app security testing include authentication, authorization, availability, confidentiality, integrity and non-repudiation. Common mobile security threats include malware, spyware, privacy threats and vulnerable applications. Effective security testing employs strategies like strong authentication, encryption, access control and session management. The testing methodology involves profiling the app, analyzing threats, planning tests, executing tests, and providing daily status reports. Deliverables include management reports, technical vulnerability reports, and best practices documents.





![MALICIOUS SOFTWARE [ VIRUS ] EFFECTS AS FOLLOWS...
❏ It can slow down your computer/mobile device/application/database server/web server
❏ It might corrupt your system files.
❏ It might make some programs faulty or corrupt.
❏ It might damage your boot sector creating problems when you boot into the windows.
❏ It might steal important information from your computer and send to some other person.
❏ It might change the power ratings of your computer and could blast the system.
❏ It can possibly wipe out your hard drive.
❏ It can redirect websites, send spam emails, alter data, destroy data, steal passwords and bank details, format our
hard disk and destroys everything.
❏ It might give you sleepless nights and nightmares [terrifying dreams] if you are able to sleep.](https://image.slidesharecdn.com/19435dad-15f4-4abb-bf0f-b49f76c8ee00-150804094634-lva1-app6892/85/Mobile-Apps-Security-Testing-1-12-320.jpg)





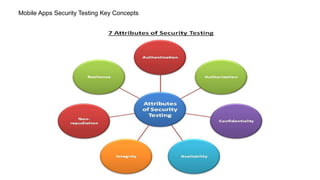
![Authentication:
Authentication is the process of checking credentials [i.e., checking user username or password] to identify the user.
Authorization:
Authorization is the process of giving privileges to the authenticated users. That means all authenticated users can not performs
all operations. Depending on his roles some privileges are given to them in the form authorization. Its like user permissions,
group permissions are an examples of authorization.
For example for a particular bank customers, employees, administrators can login into that websites. But the options available
to these persons are different at customer level, bank employee level, administrators level etc. This is authorization.
Availability
It is a process of checking that information & communications services must be kept available to authorized persons when they
need it. Ex: ATM
Confidentiality
It is a process of checking that information is accessible only for authenticated/authorized users and protecting the information
from any other users.](https://image.slidesharecdn.com/19435dad-15f4-4abb-bf0f-b49f76c8ee00-150804094634-lva1-app6892/85/Mobile-Apps-Security-Testing-1-19-320.jpg)