Embed presentation
Downloaded 18 times



![%##&$^#*!~@&
FINANCE
CONFIDENTIAL
%$^#*@&
Open
Copy
Paste
Edit
aEZQAR]ibr{qU@M]
BXNoHp9nMDAtnBfr
fC;jx+Tg@XL2,Jzu
()&(*7812(*:](https://image.slidesharecdn.com/aipscannertechdays2017shared-171012144153/85/Microsoft-TechDays-Netherlands-2017-Azure-Information-Protection-Scanner-5-320.jpg)
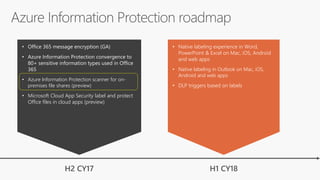




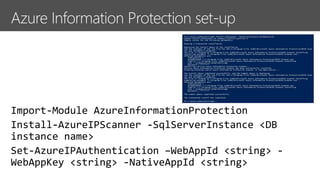



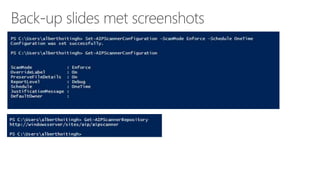
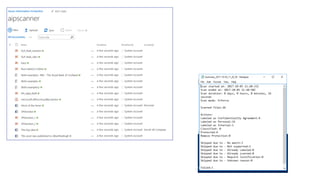
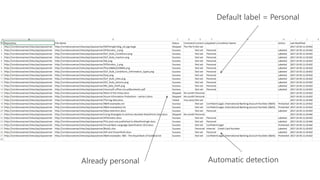

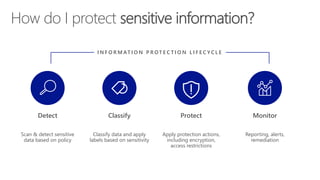
The document outlines procedures for detecting, classifying, and protecting sensitive data based on policies. It highlights features such as native labeling in Microsoft applications, data loss prevention triggers, and the use of Azure Information Protection tools. Additionally, it specifies system requirements and permissions needed for the Azure Information Protection Scanner and its integration with on-premises file shares.




![%##&$^#*!~@&
FINANCE
CONFIDENTIAL
%$^#*@&
Open
Copy
Paste
Edit
aEZQAR]ibr{qU@M]
BXNoHp9nMDAtnBfr
fC;jx+Tg@XL2,Jzu
()&(*7812(*:](https://image.slidesharecdn.com/aipscannertechdays2017shared-171012144153/85/Microsoft-TechDays-Netherlands-2017-Azure-Information-Protection-Scanner-5-320.jpg)














