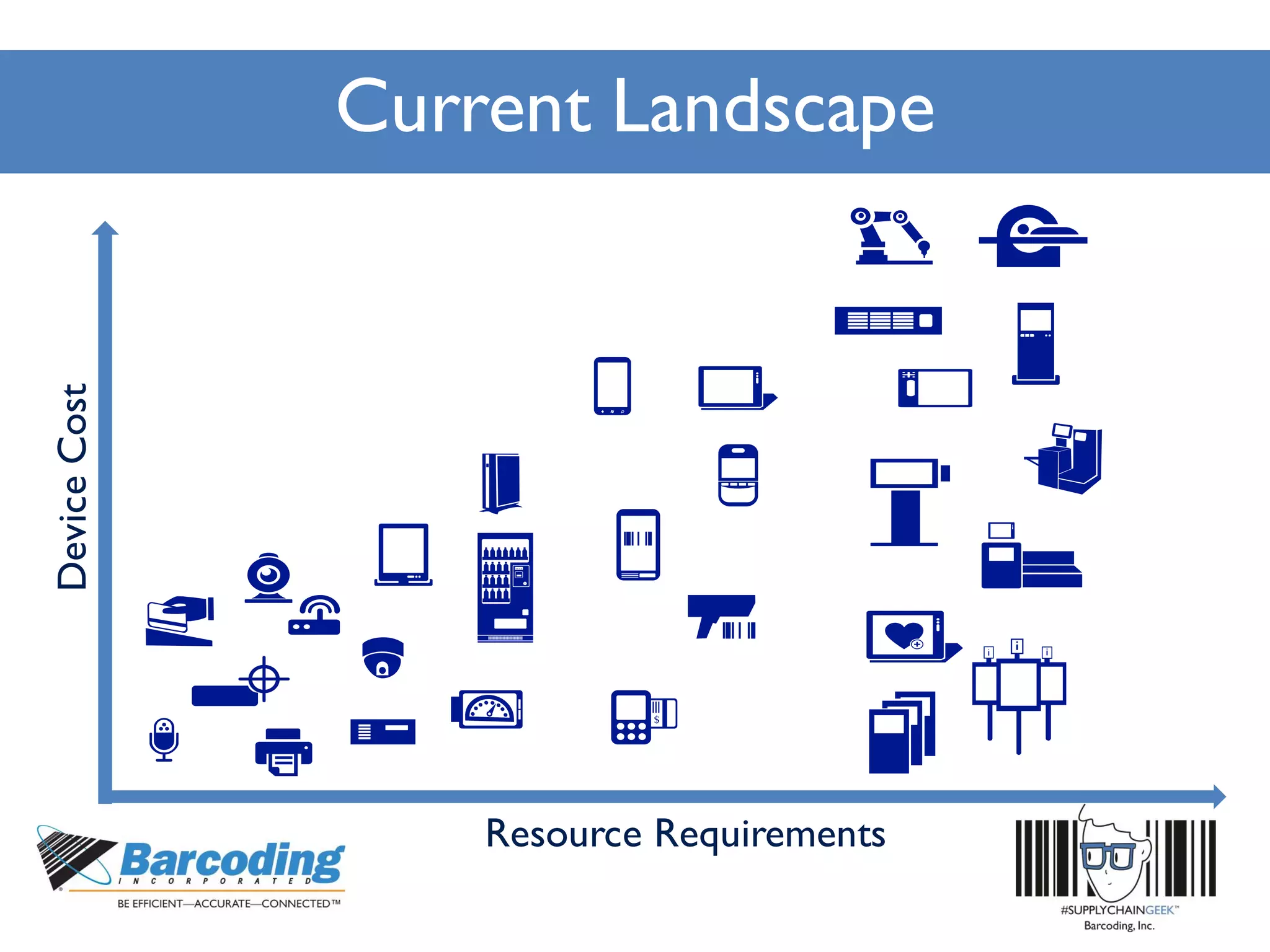
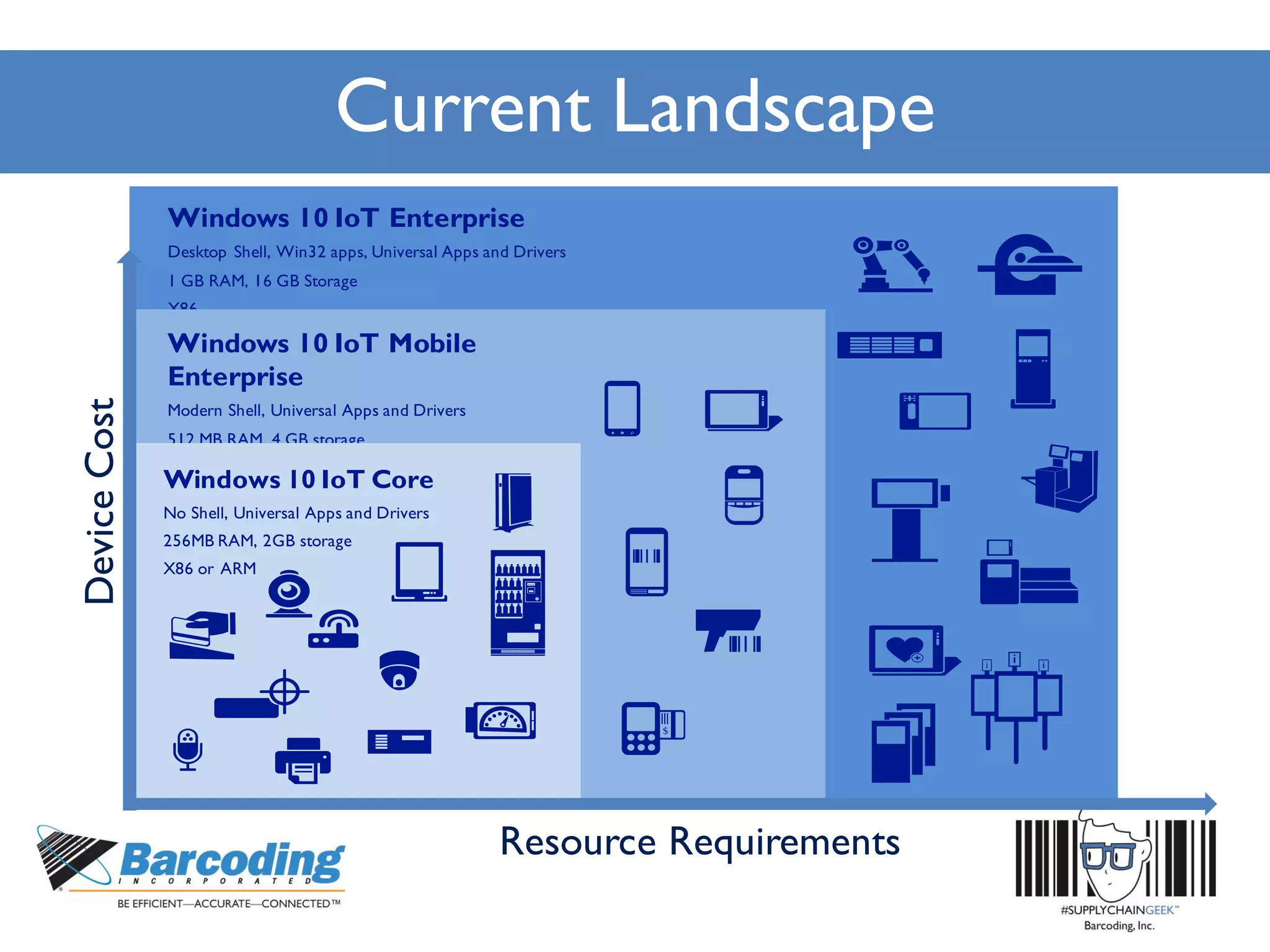
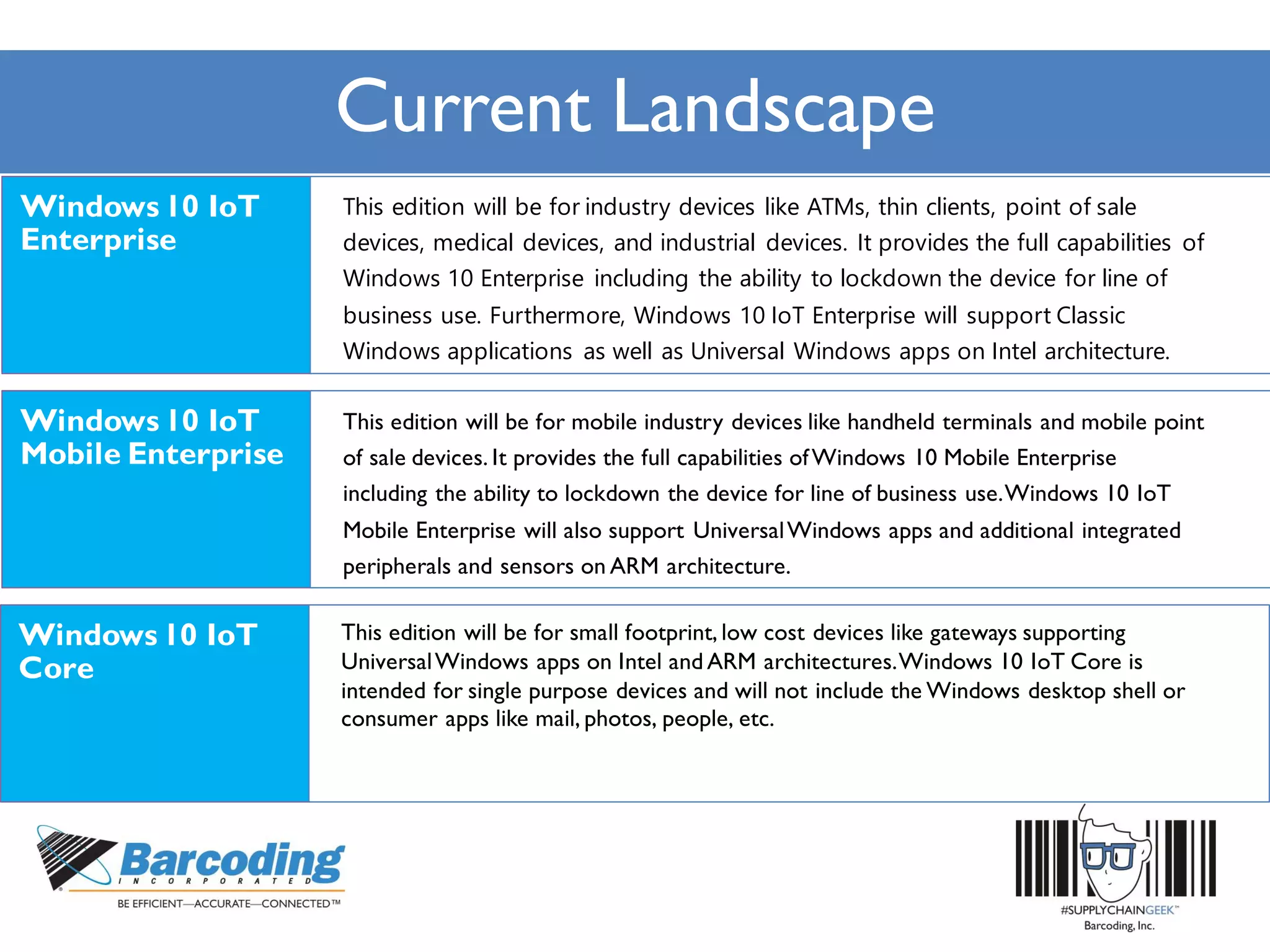
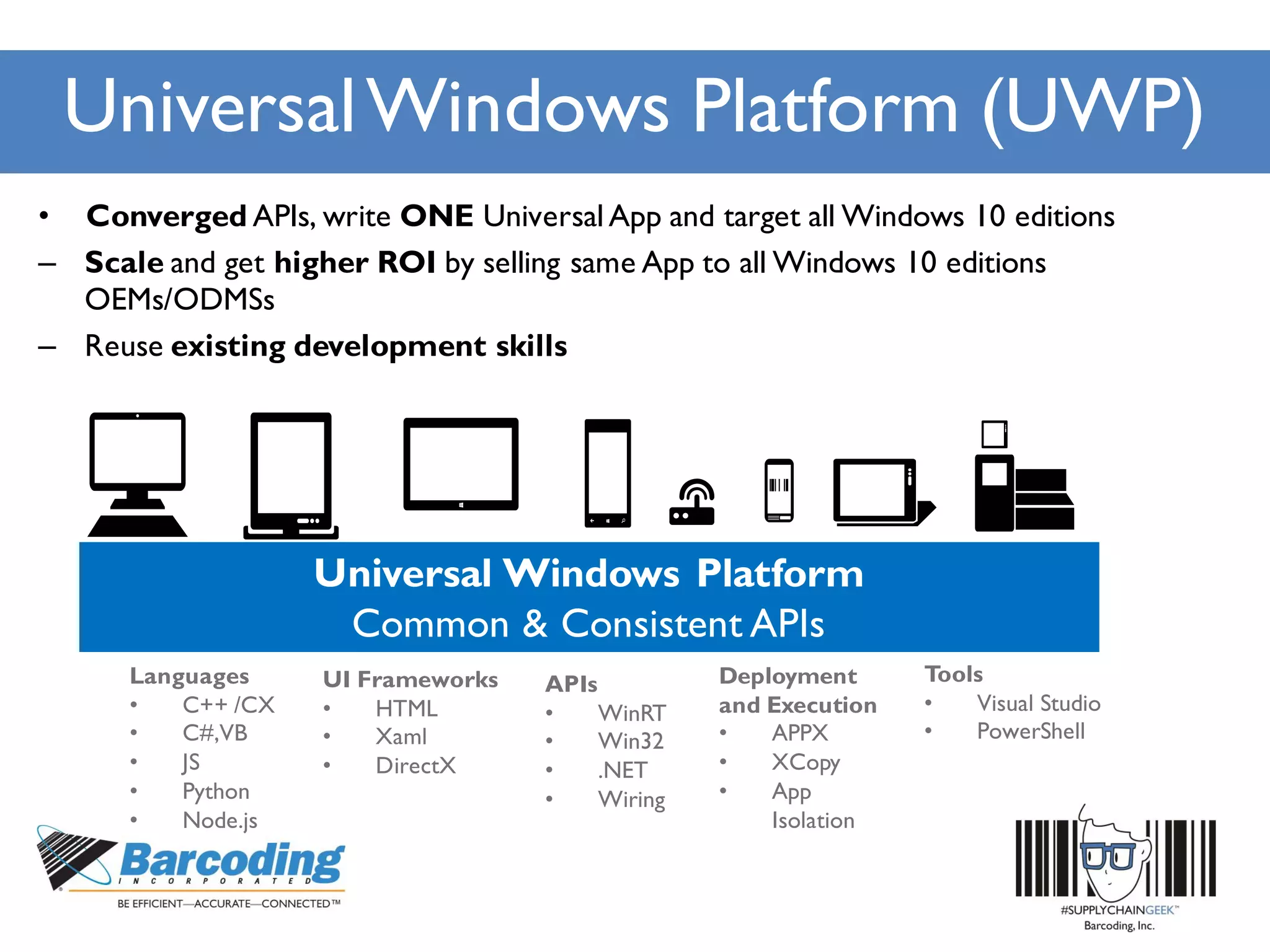
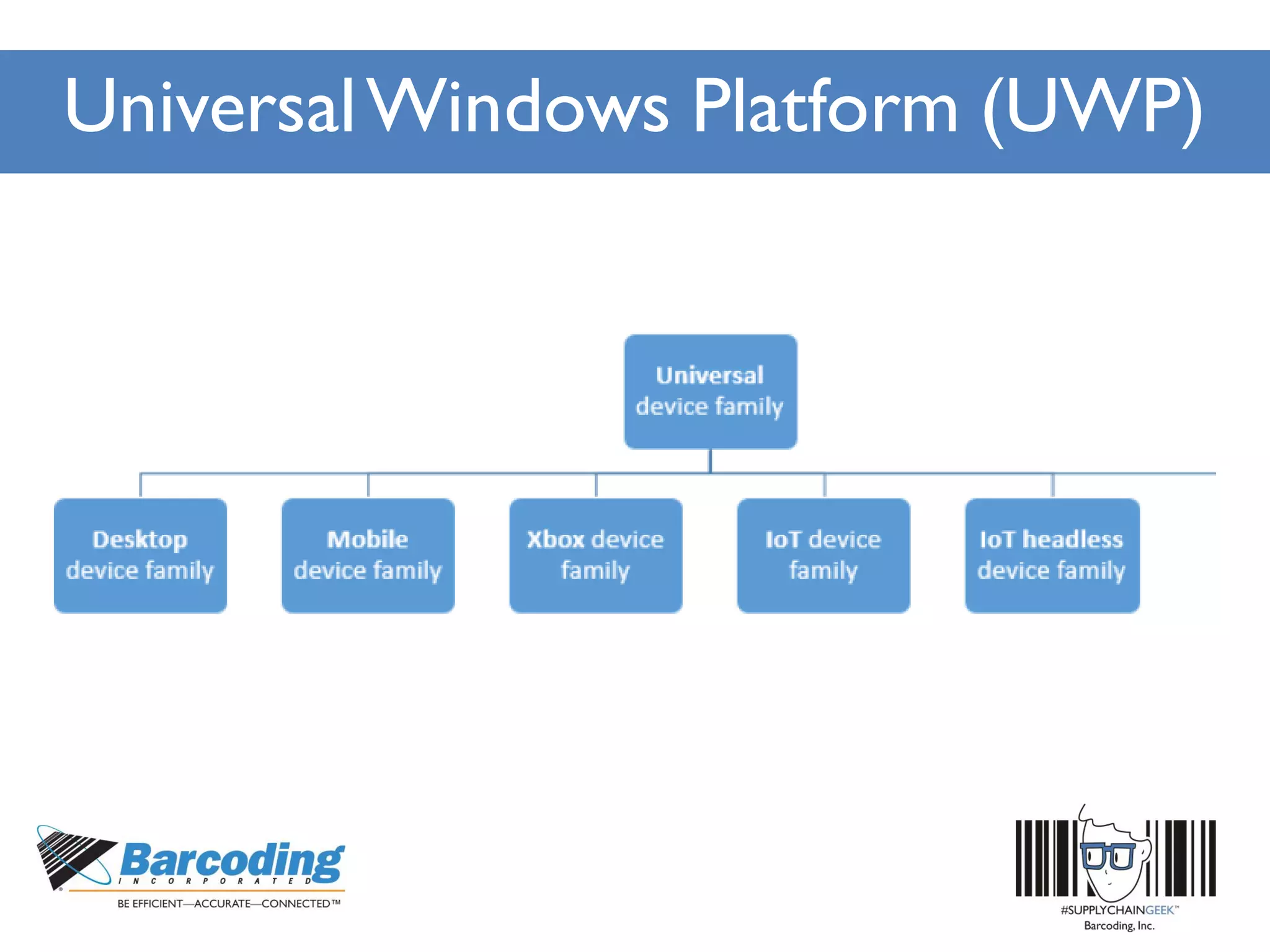
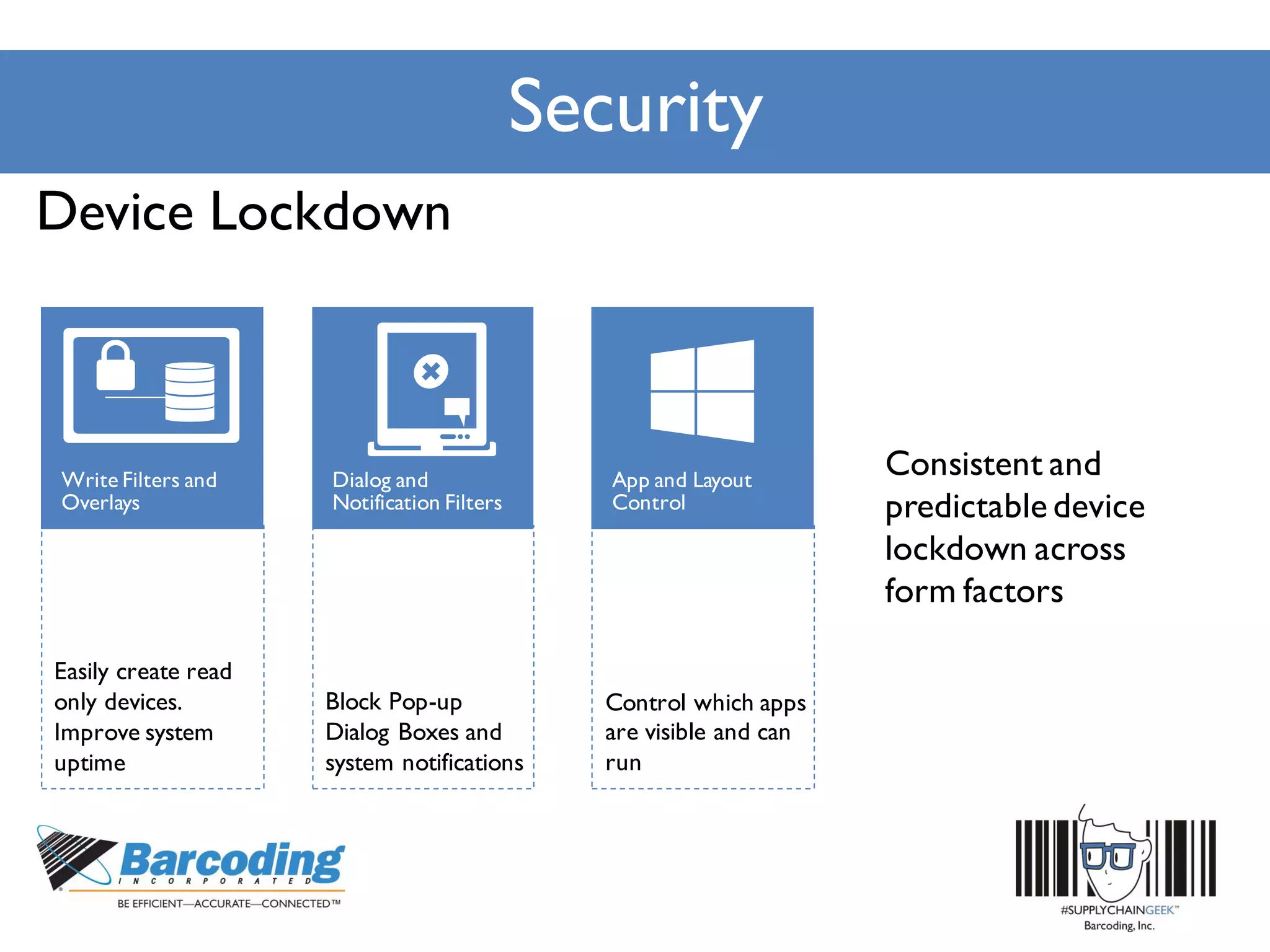
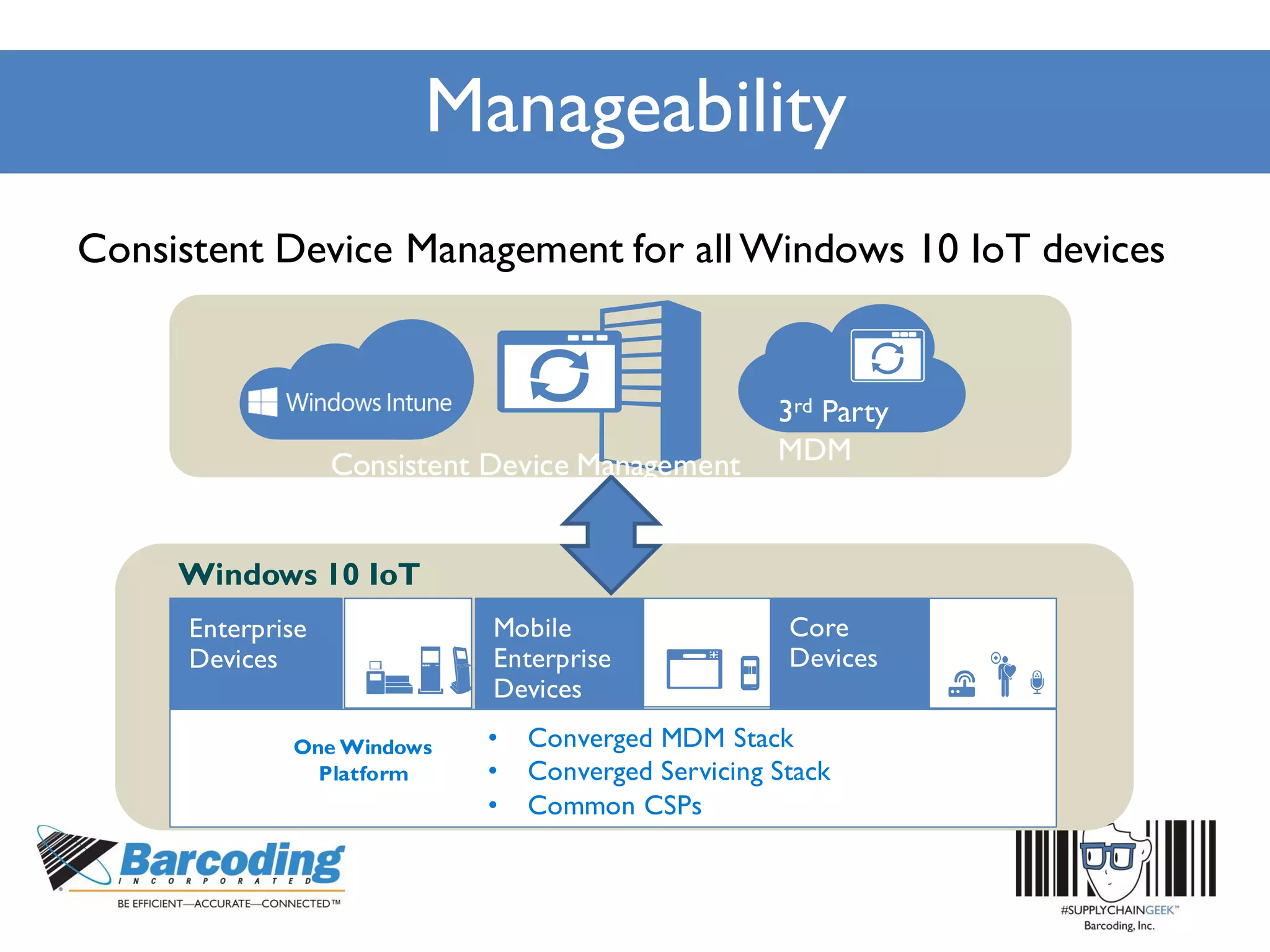
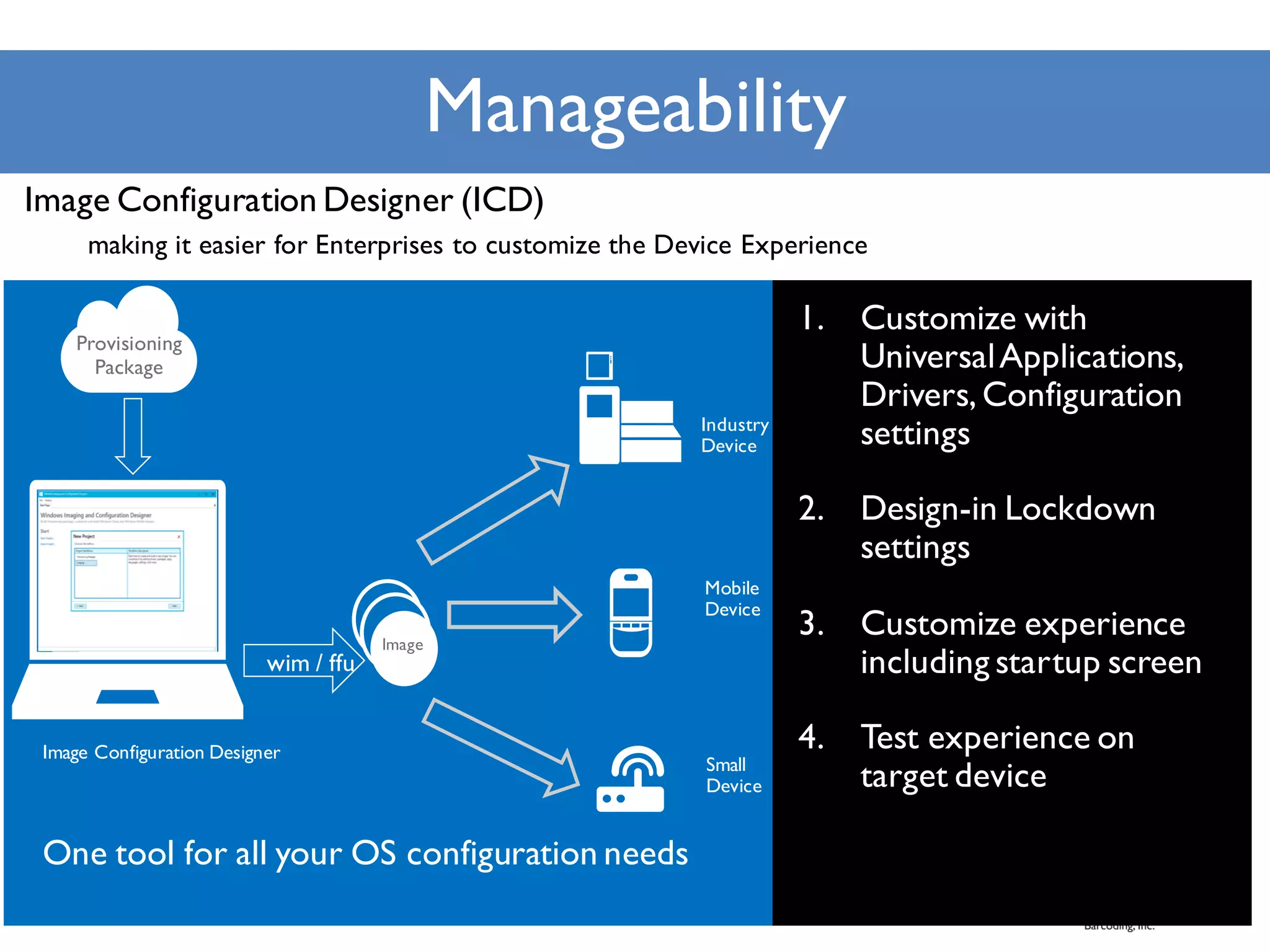
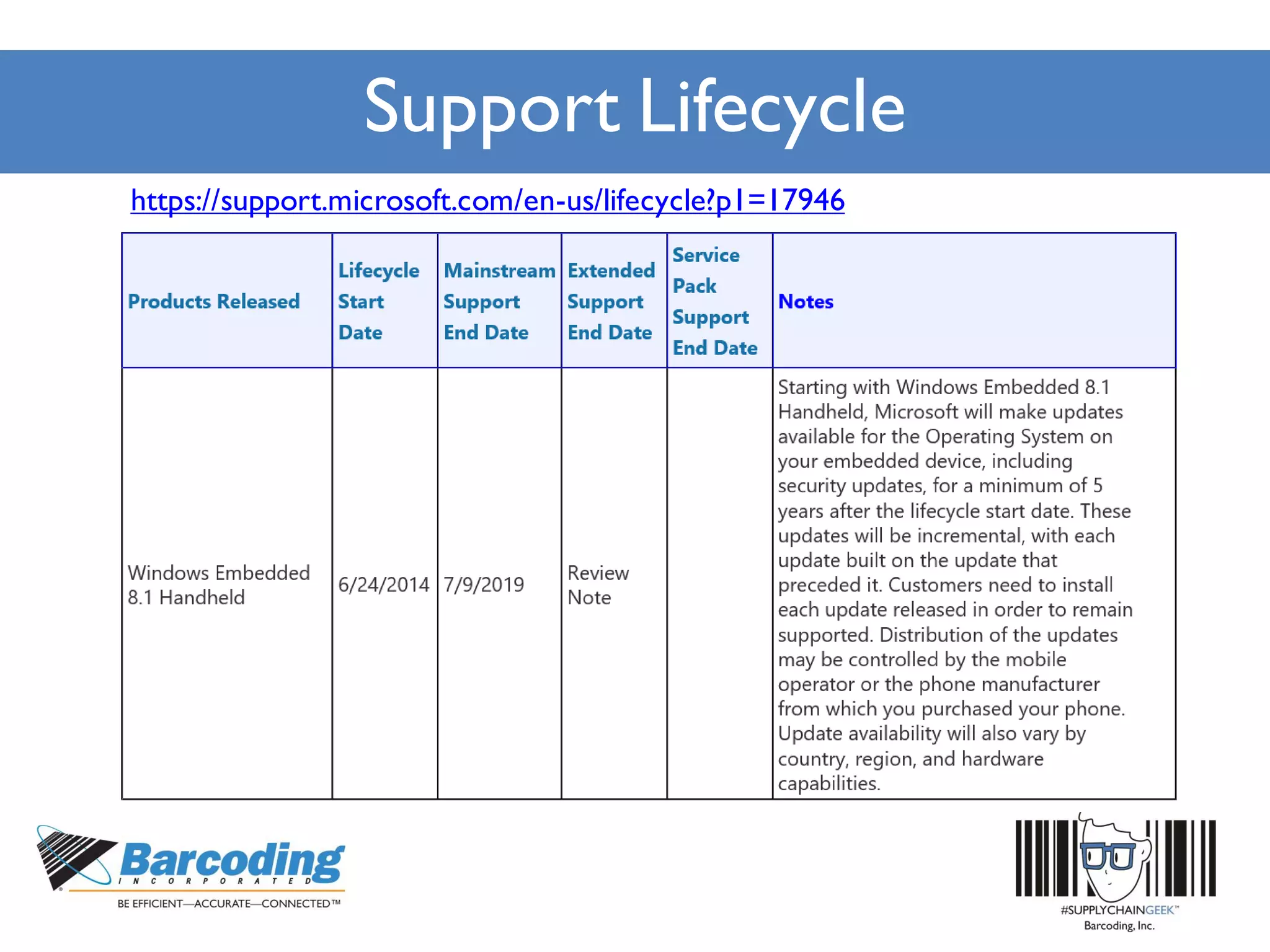
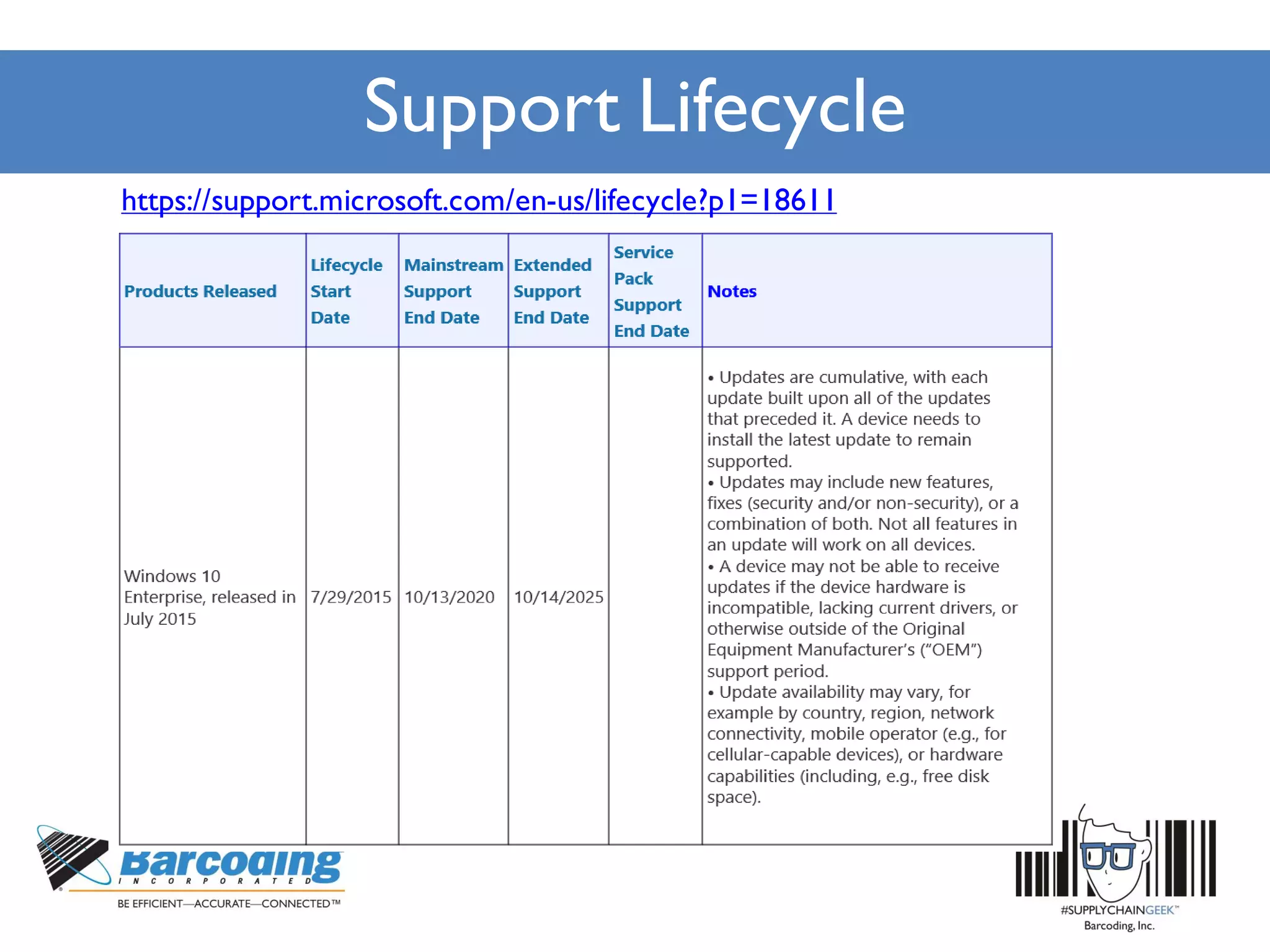
Microsoft's handheld strategy focuses on IoT solutions with Windows 10 by offering various editions like Windows 10 IoT Enterprise, Mobile Enterprise, and Core for different device types, addressing security and manageability aspects. The Universal Windows Platform (UWP) allows developers to create one app for all Windows 10 editions, enhancing ROI and leveraging existing development skills. Microsoft's approach emphasizes advanced security measures, consistent device management through a unified platform, and support lifecycles for enterprise devices.