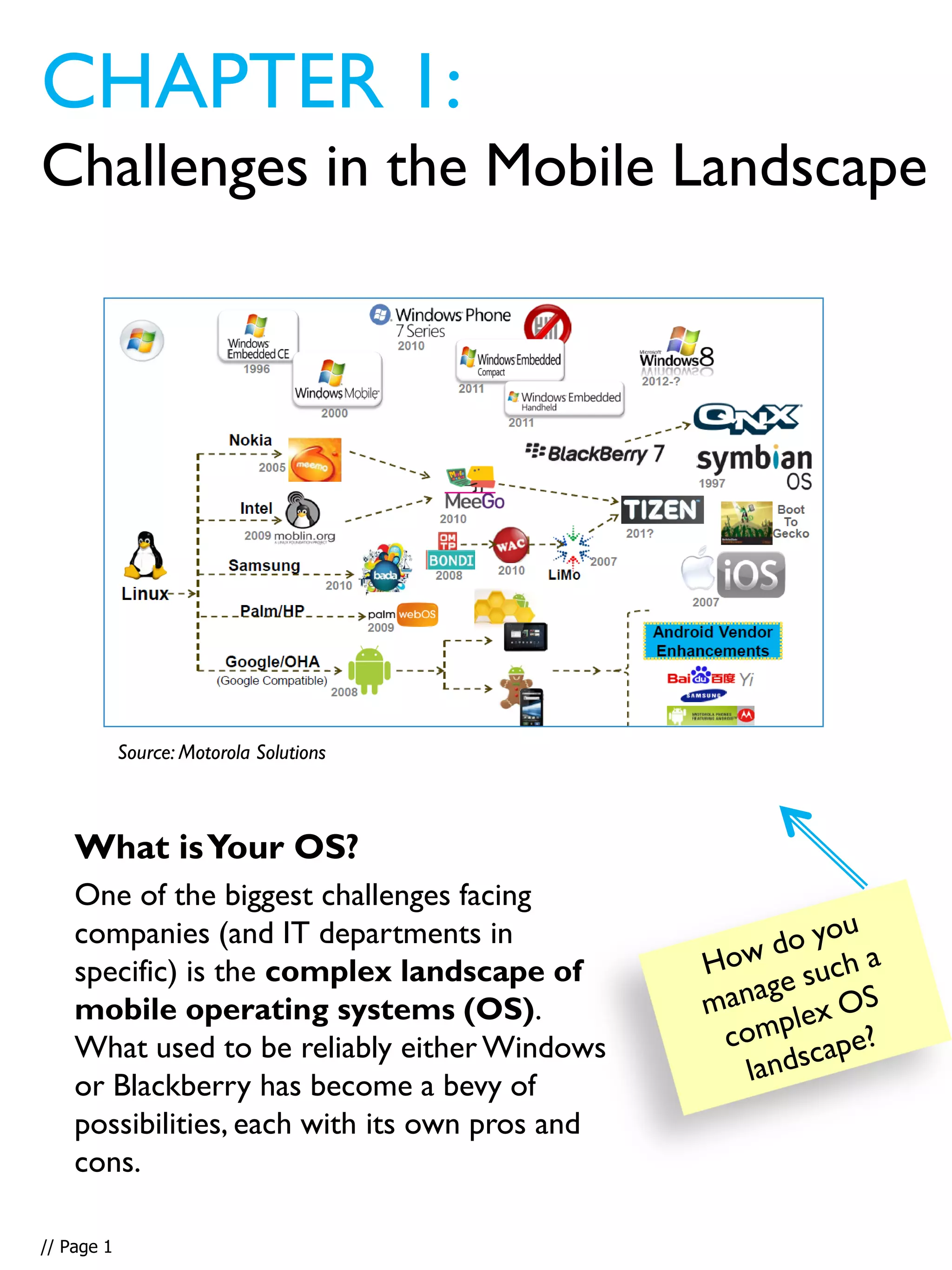
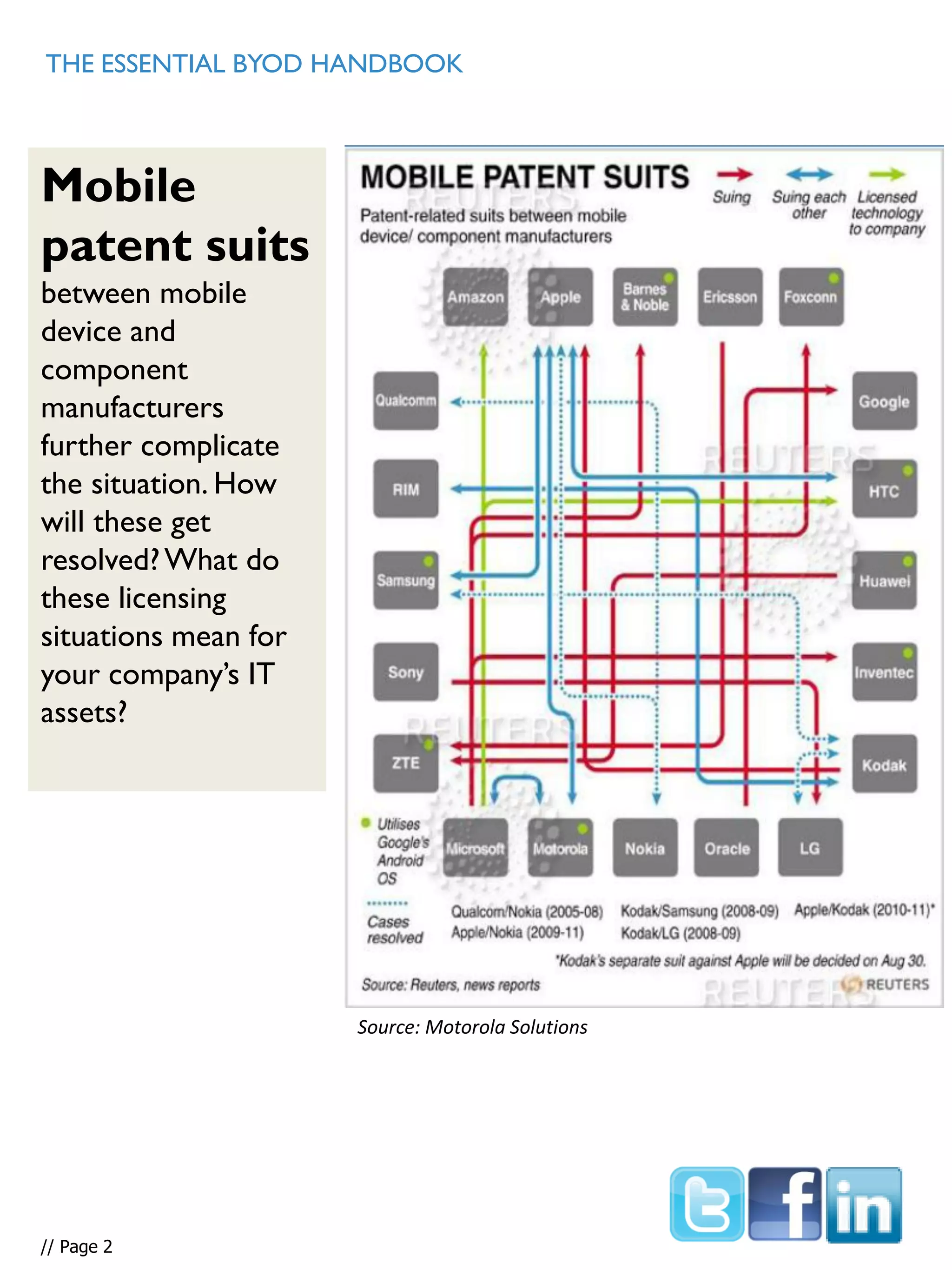
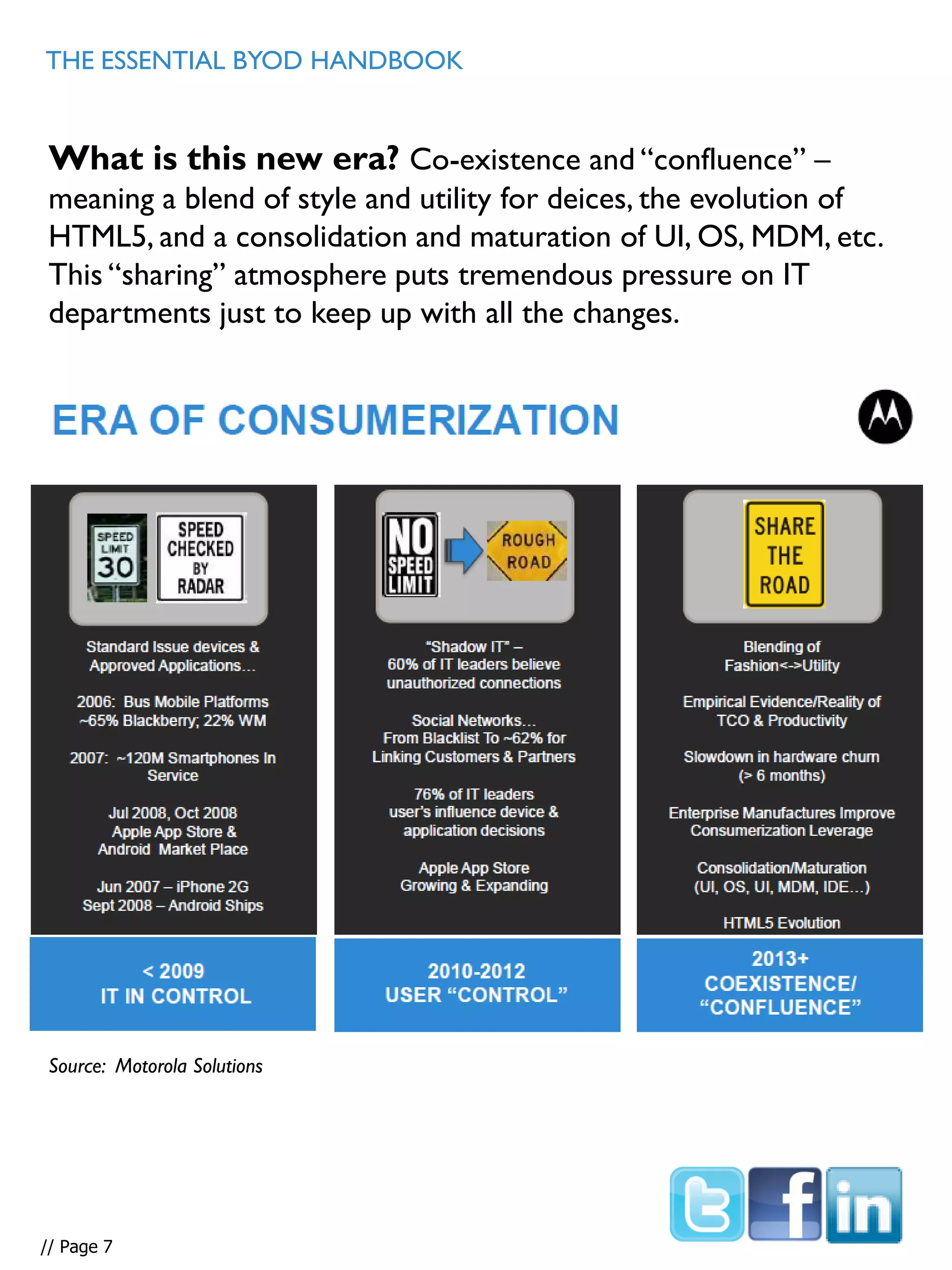
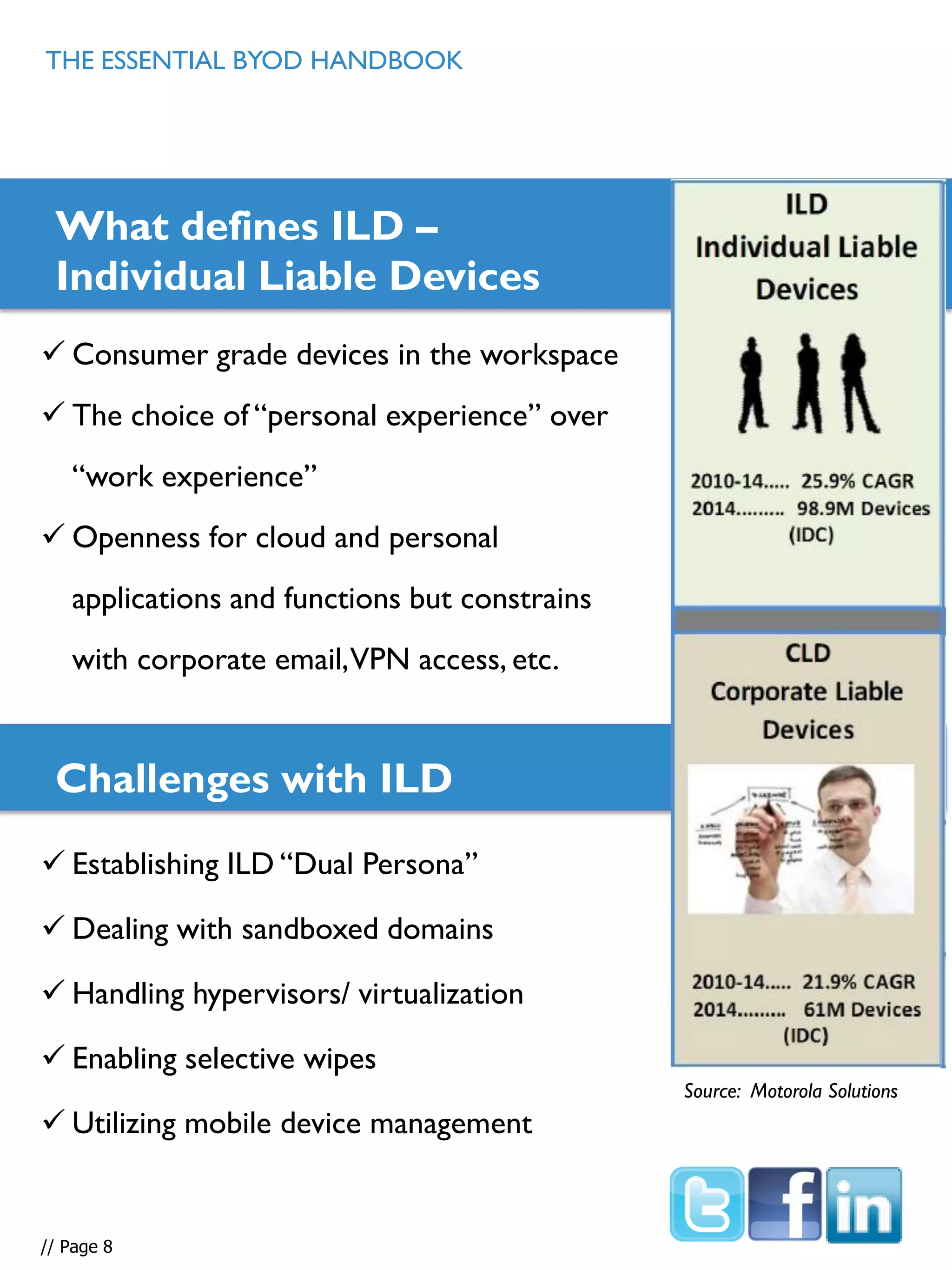
This document provides an overview and guidance on effectively supporting Bring Your Own Device (BYOD) programs. It discusses the challenges of the complex mobile landscape with many operating systems. It also distinguishes between consumer and enterprise mobile devices. The document outlines steps to take to support BYOD, including conducting a device audit, establishing guidelines and policies, using mobile device management software, and ensuring data security. It emphasizes the importance of having a comprehensive BYOD strategy to control costs and effectively manage devices and data.