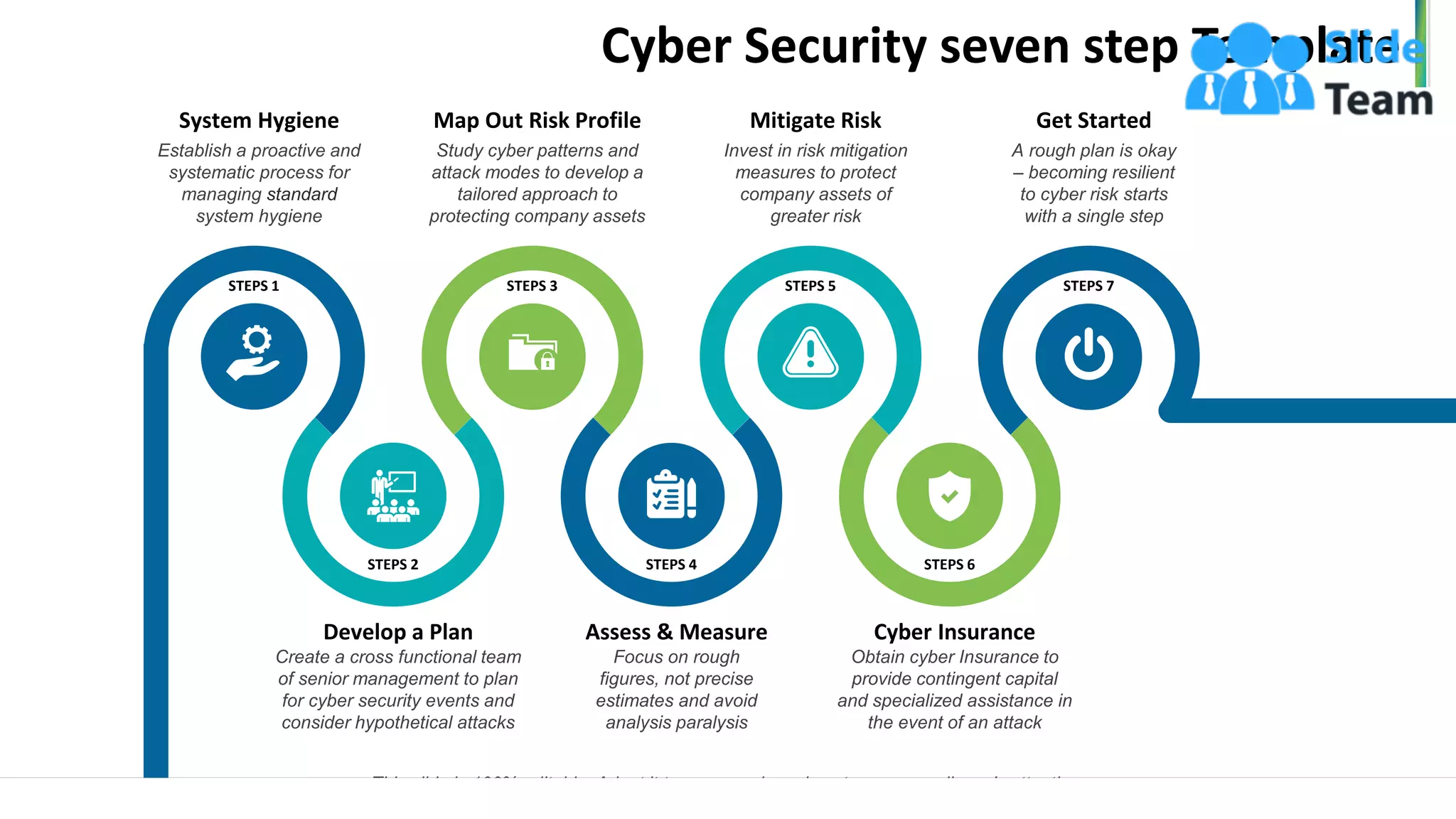
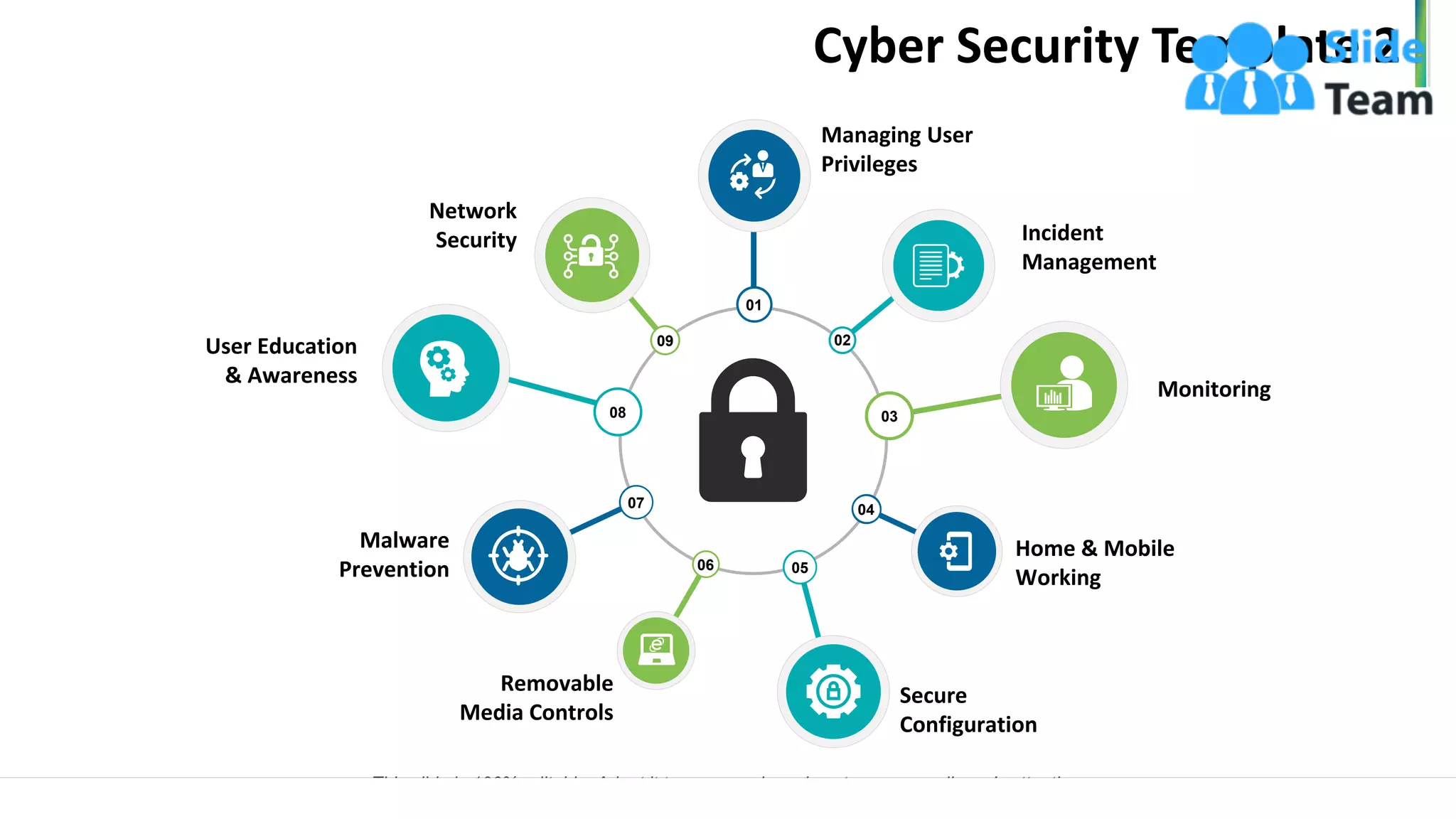
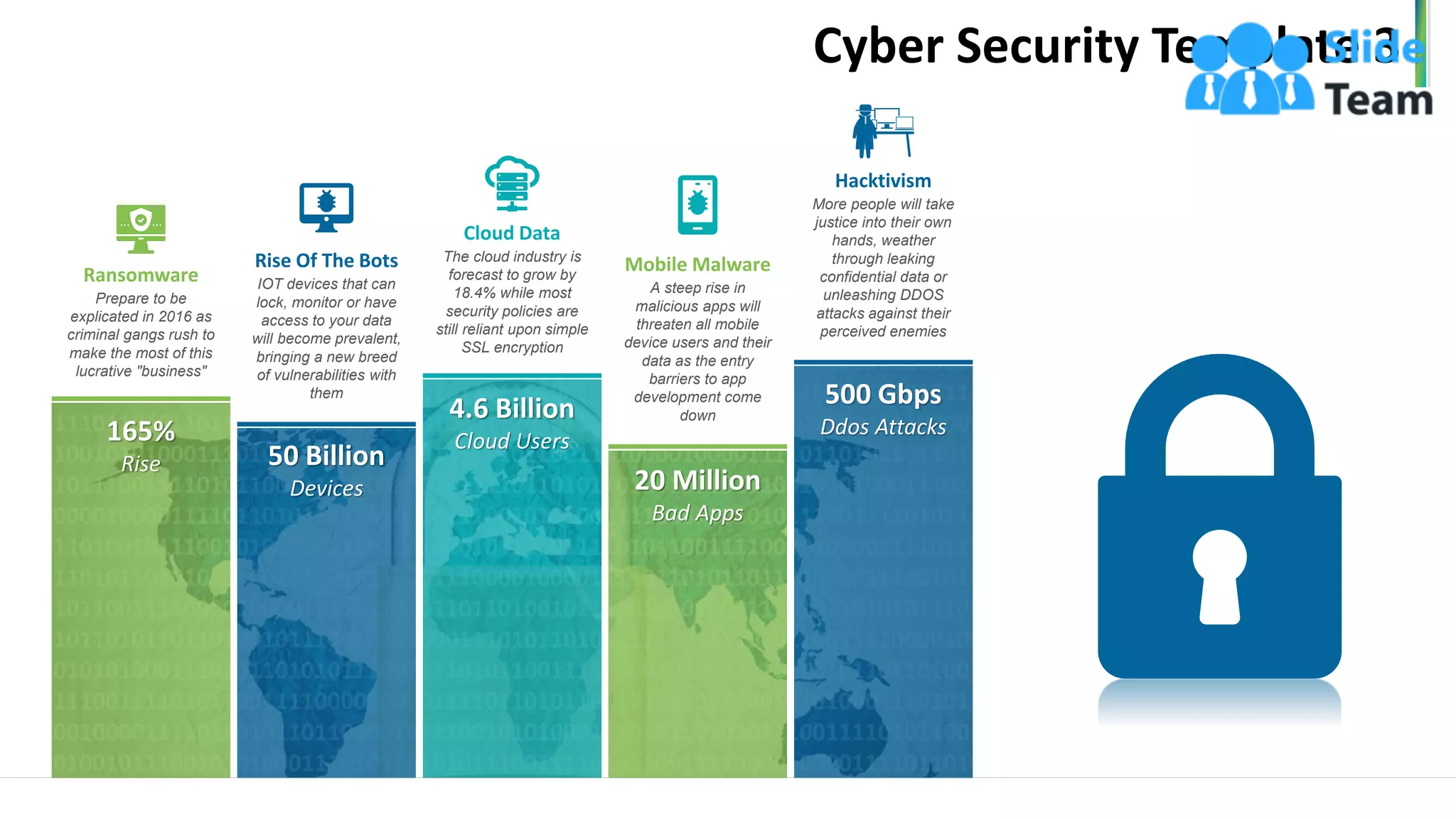
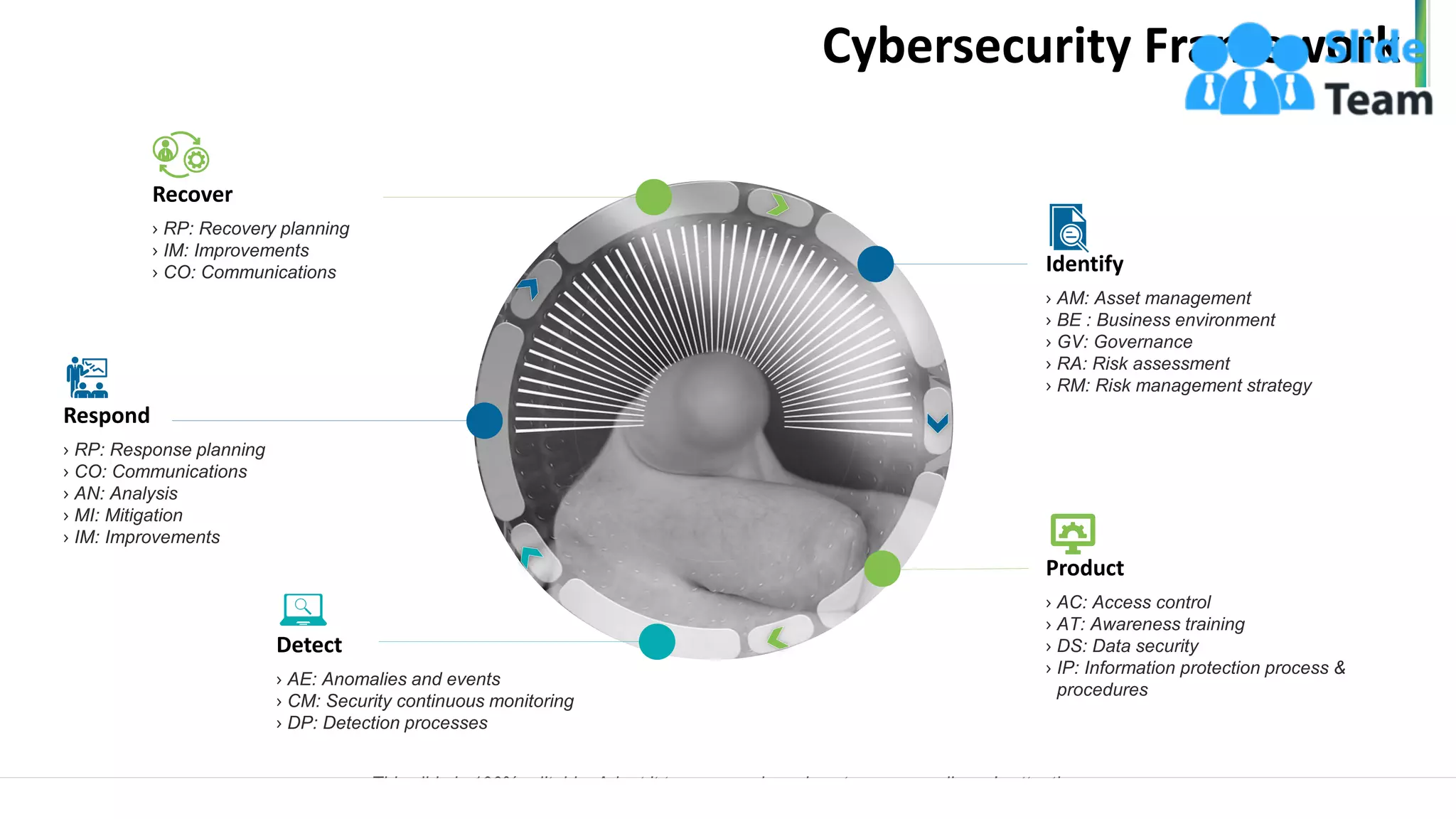
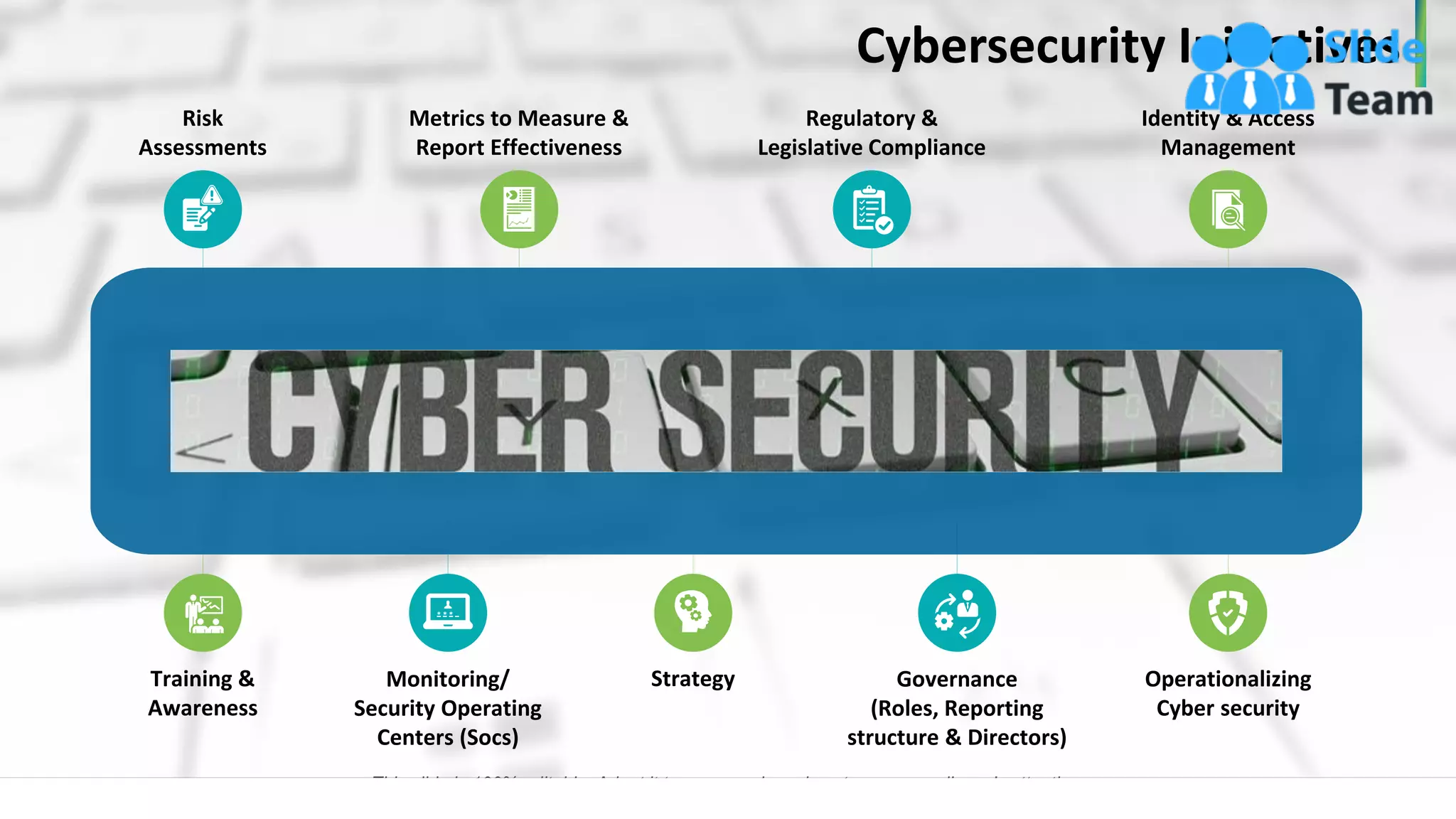
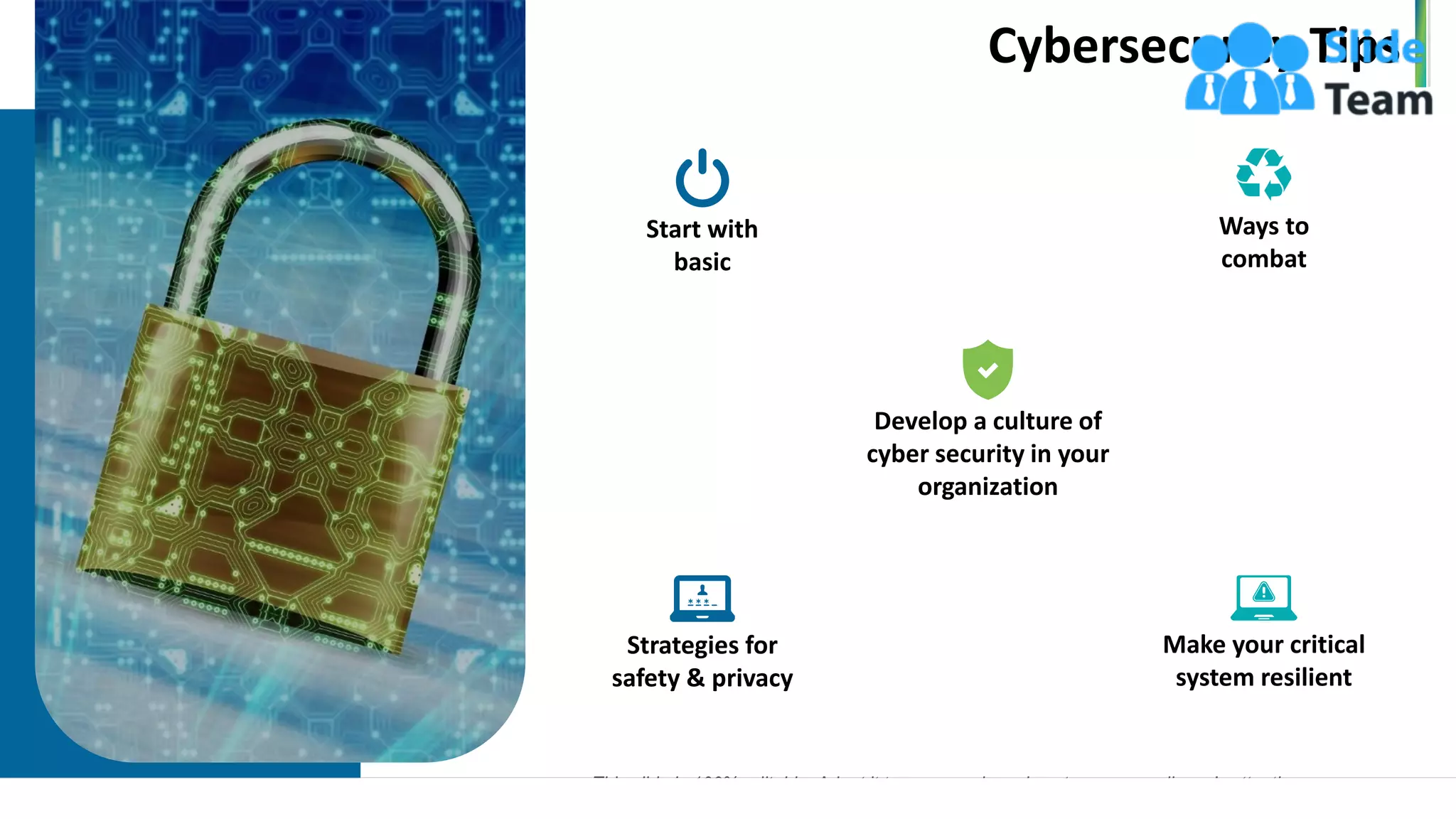
The document outlines a seven-step template for improving cybersecurity within a company, including establishing system hygiene, risk assessment, and investing in cyber insurance. It emphasizes the importance of proactive incident management and developing a culture of cybersecurity among employees. The document also highlights emerging threats such as mobile malware and the rise of IoT vulnerabilities.