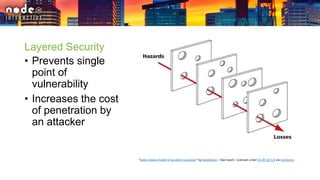
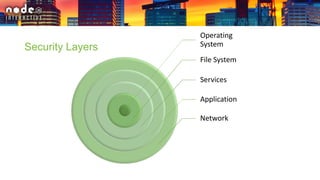
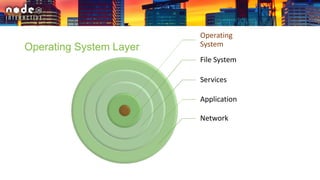
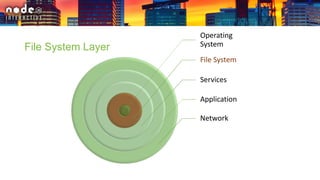
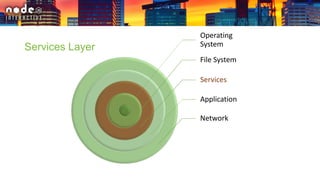
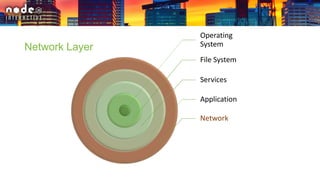
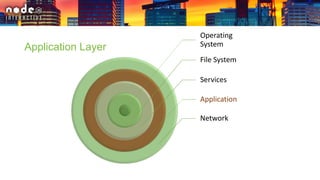
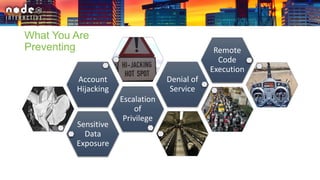
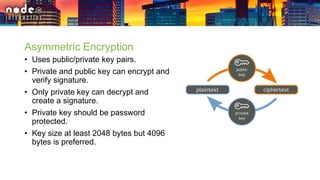
The document outlines various security layers and best practices in IoT and software development, emphasizing that security must be multi-layered to reduce vulnerabilities. It discusses strategies for protecting data in transit and at rest, account hijacking prevention, and measures to avoid remote code execution. Detailed technical recommendations are provided, including encryption techniques, secure session management, and awareness of potential attacks.