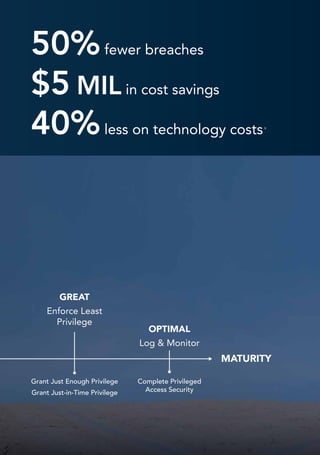
This document discusses the need to rethink security approaches in the modern boundaryless digital landscape. Traditional perimeter-based security relying on firewalls and passwords has proven ineffective with numerous large breaches occurring. The document advocates adopting an identity-centric security model that secures user access and privileges across applications and infrastructure on and off-premises. Centrify is presented as a platform to help organizations implement identity services to better defend against threats in today's complex environment.