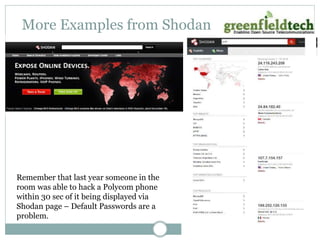
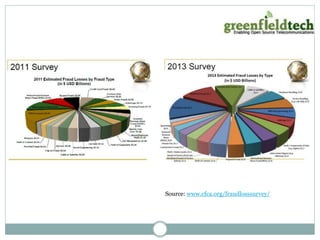
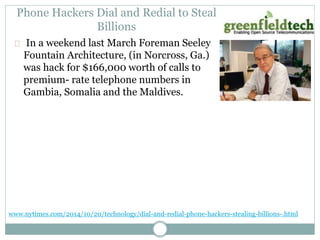
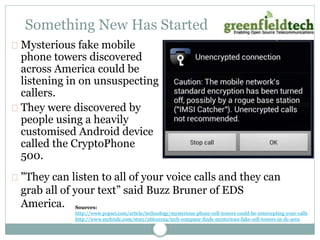
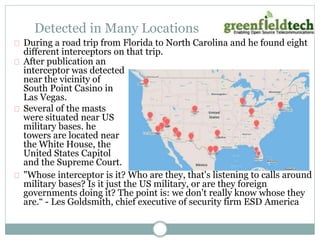
This document discusses how to make an Asterisk system more secure. It begins by explaining that PBX systems are targets for hackers and how they can find unsecured systems. It then provides recommendations for securing the physical device, operating system, network, Asterisk configuration, SIP, and dialplan. Resources discussed include taking Asterisk security courses, reviewing the Asterisk wiki for security articles, keeping systems updated, and using dedicated VoIP security products to monitor for attacks.












![Detection is Hard
“If you've been intercepted, in
some cases it might show at the
top that you've been forced
from 4G down to 2G. But a
decent interceptor won't show
that,” says Goldsmith. “It'll be
set up to show you [falsely] that
you're still on 4G. You'll think
that you're on 4G, but you're
actually being forced back to
2G.”
Some devices can not only capture calls and texts, but even
actively control the phone and send spoof texts.](https://image.slidesharecdn.com/ericklein-makingyourasterisksystemsecure-141110113915-conversion-gate02/85/Making-your-Asterisk-System-Secure-17-320.jpg)