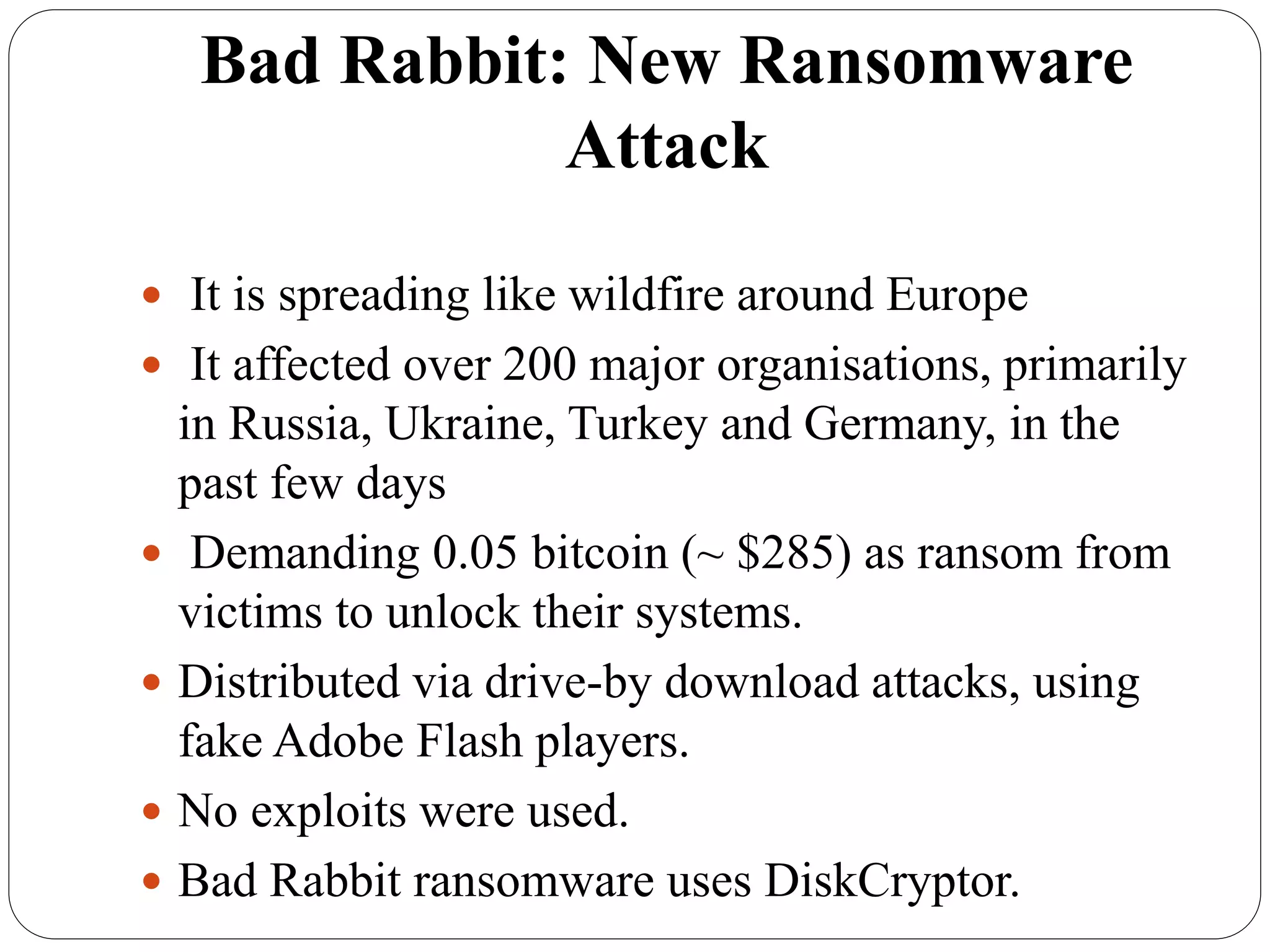
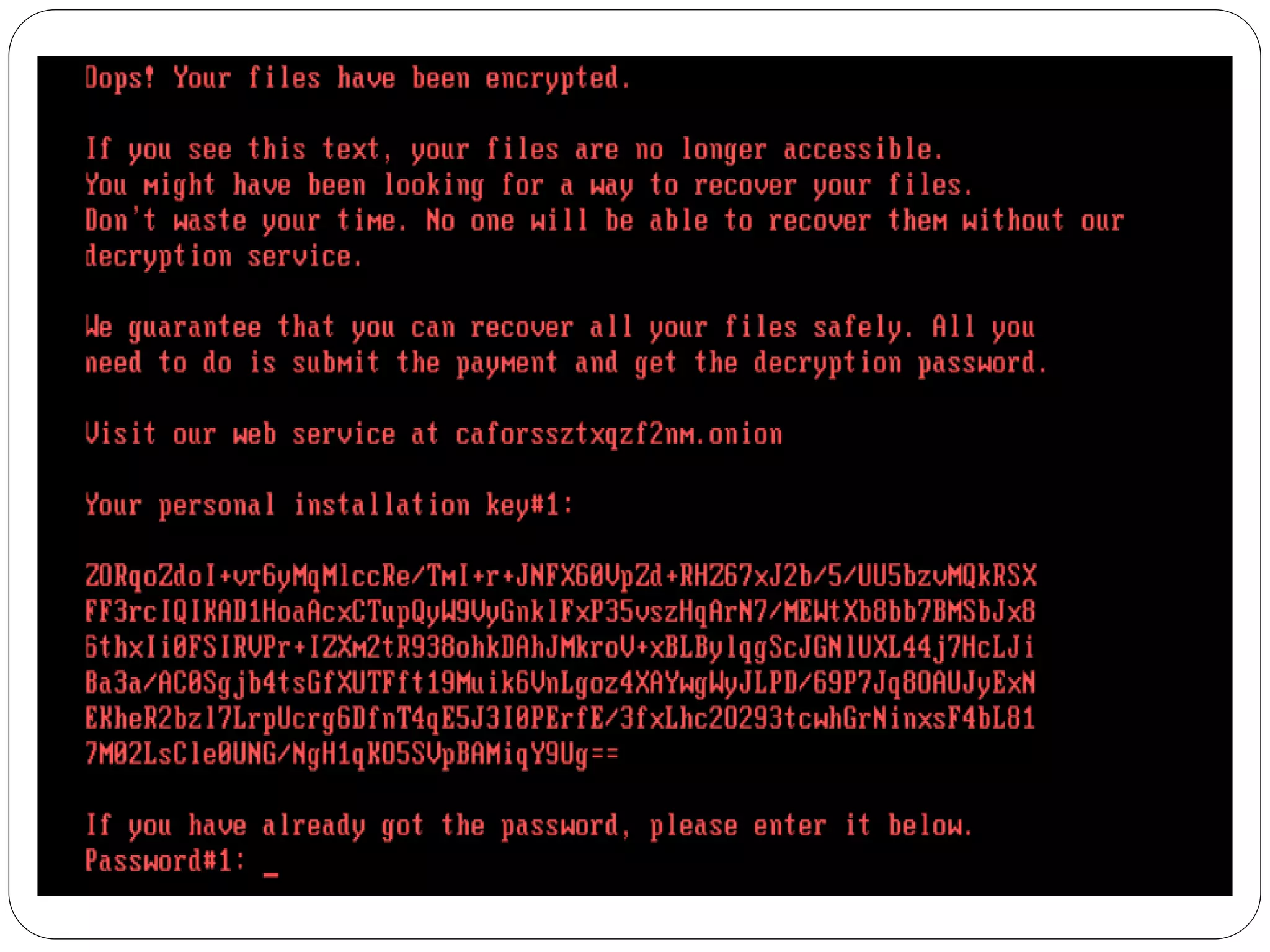
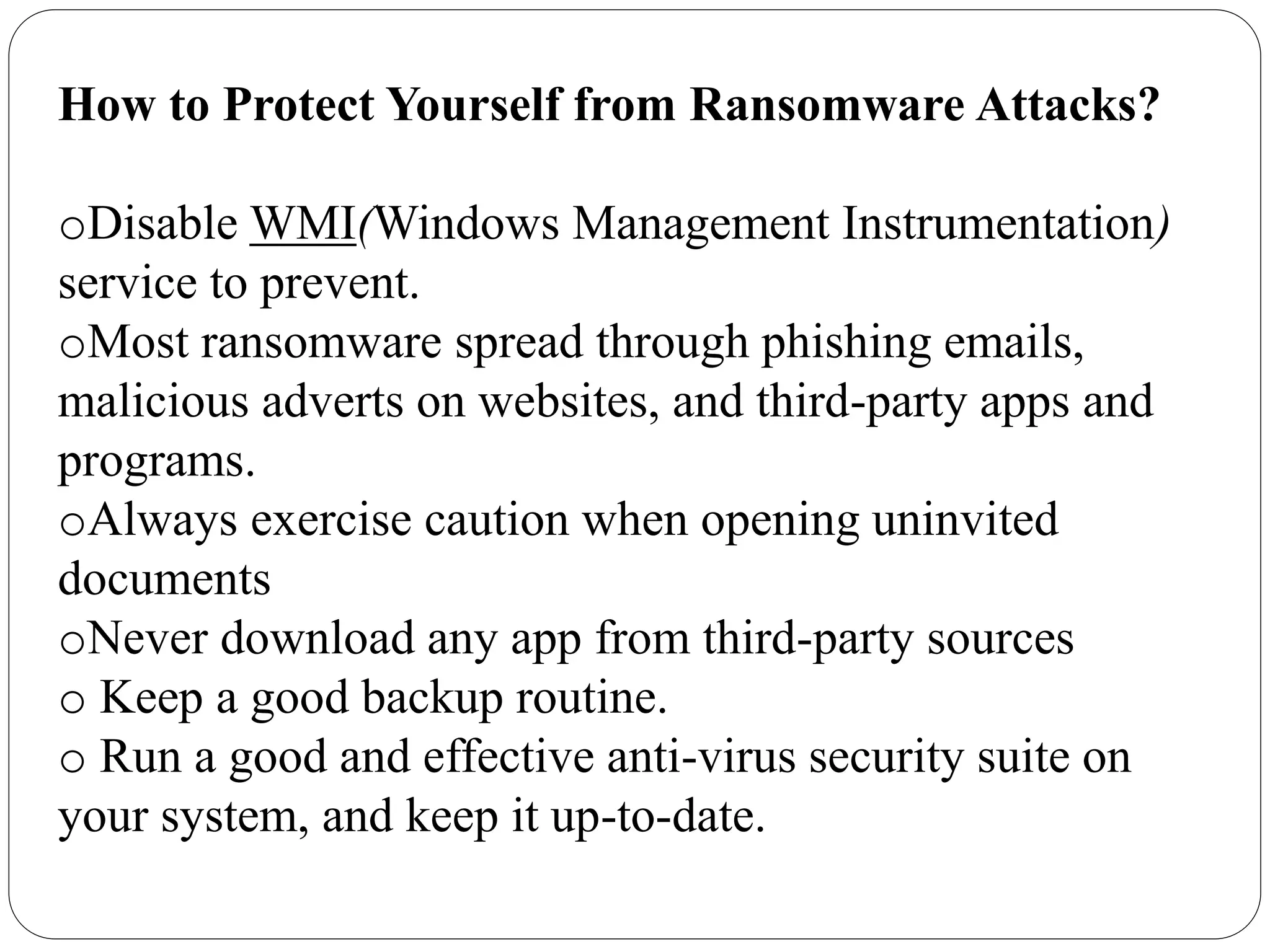
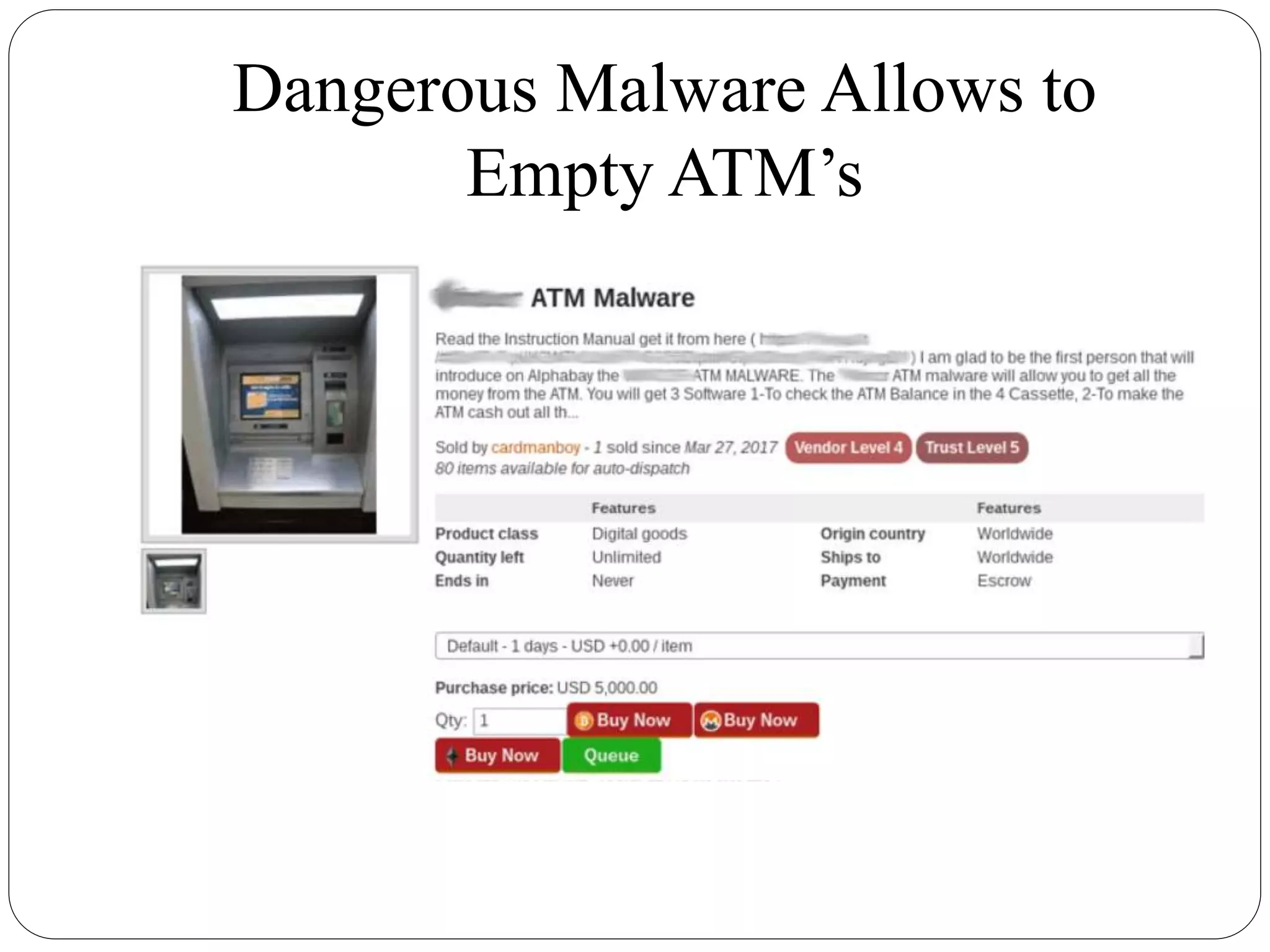
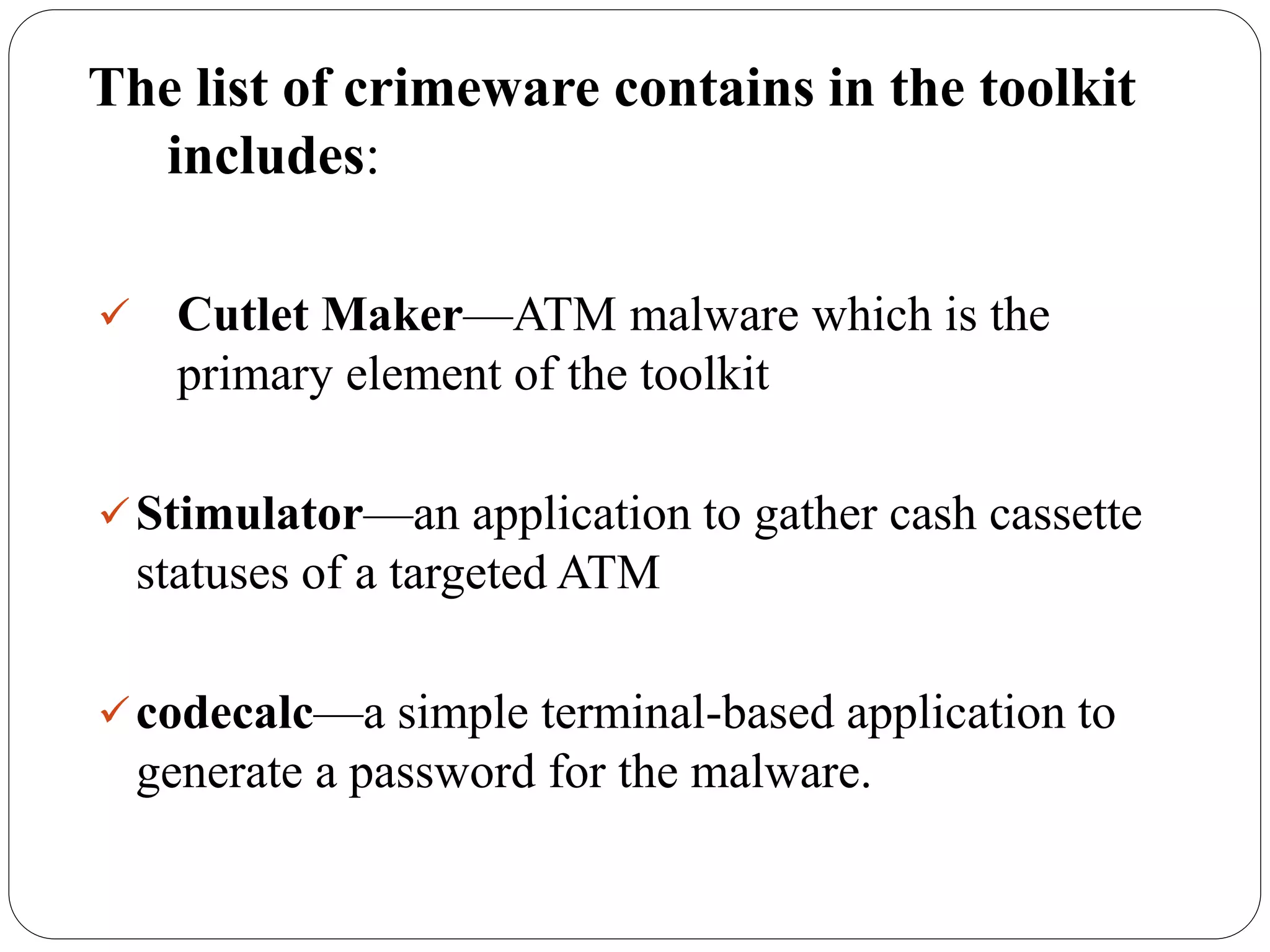
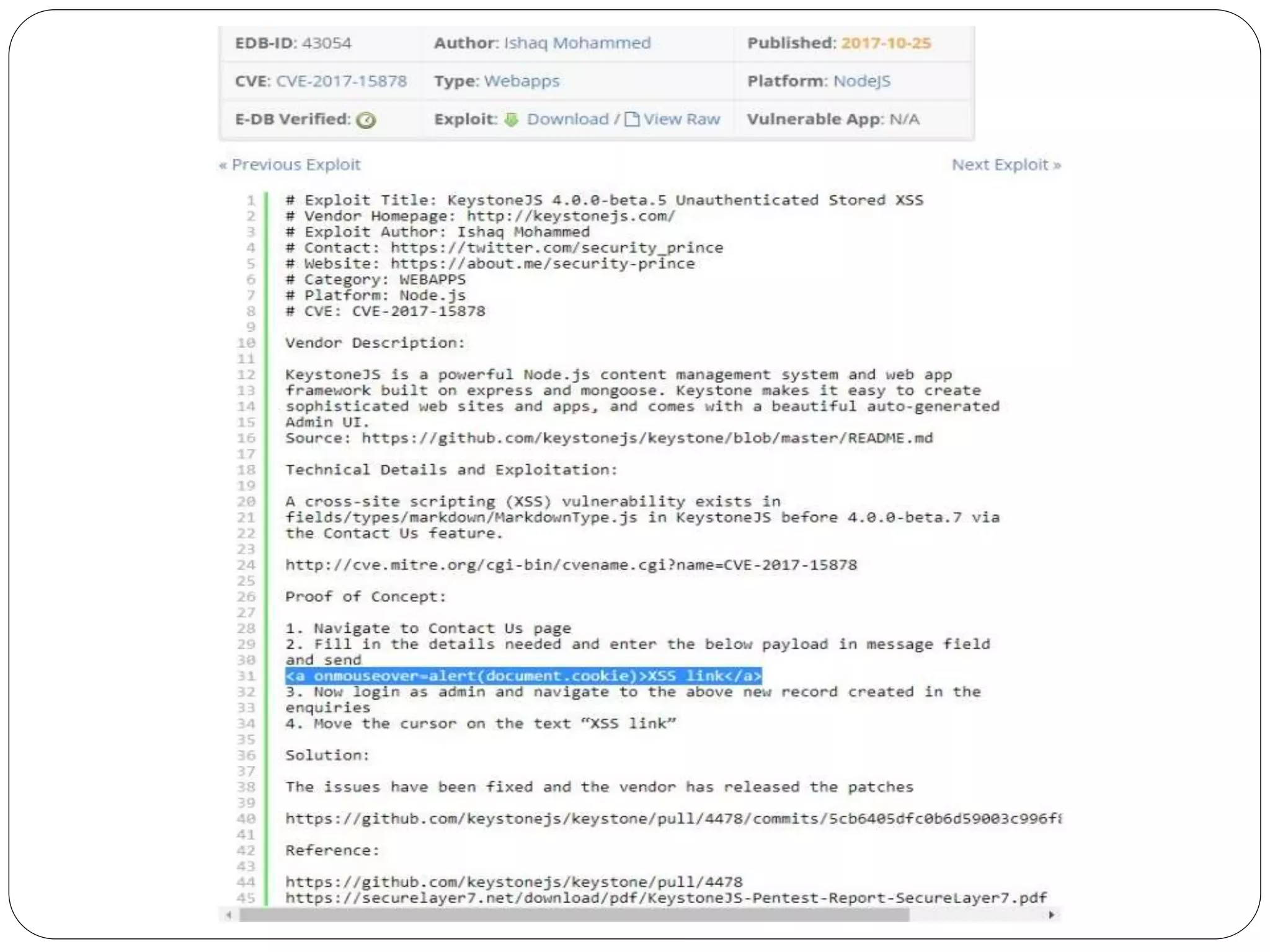
The document discusses several cybersecurity issues: KRACK, a vulnerability that allows hackers to decrypt WiFi network data without knowing the password; Bad Rabbit ransomware that infected over 200 organizations in Europe; malware that exploits the Dynamic Data Exchange feature in Microsoft Office to distribute ransomware and banking trojans; ready-made ATM malware that is being sold online for $5,000 to steal cash from ATMs; and a cross-site scripting vulnerability found in the KeystoneJS web framework. It provides details on how these attacks work and recommendations for preventing or mitigating the risks.