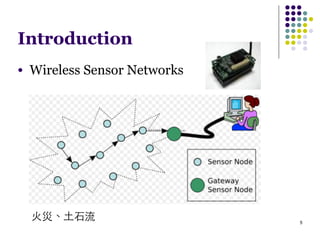
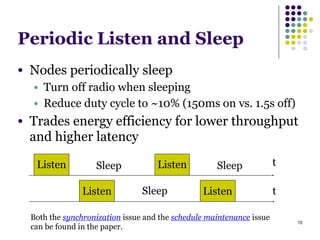
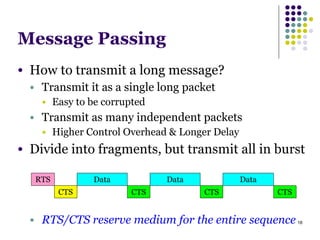
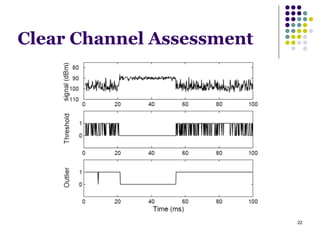
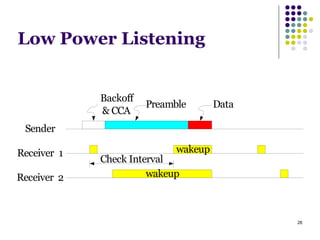
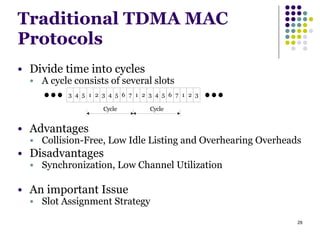
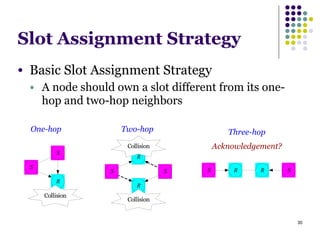
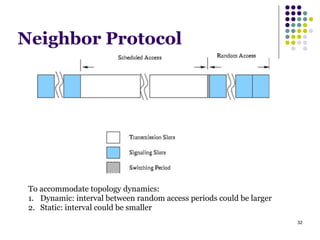
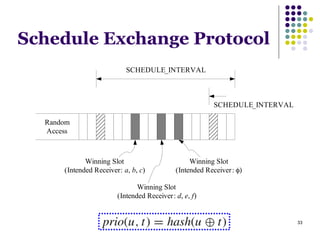
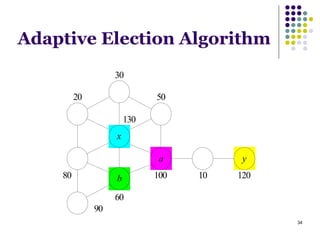
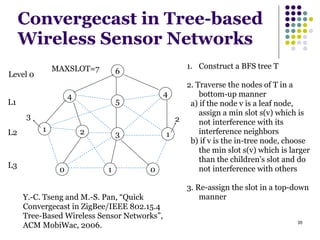
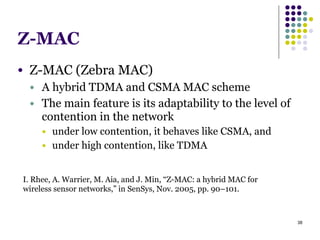
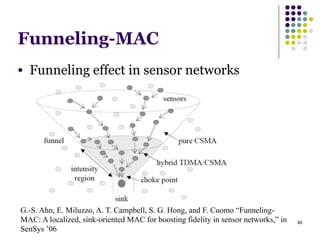
This document summarizes several MAC protocols for wireless sensor networks. It begins by introducing the need for MAC protocols to control medium access in wireless networks and common sources of energy waste. It then categorizes MAC protocols as contention-based (like ALOHA and CSMA), schedule-based (like TDMA), or hybrid. Specific protocols discussed include S-MAC, B-MAC, TRAMA, and hybrid protocols like Z-MAC and Funneling-MAC. The document emphasizes energy efficiency as the primary concern for MAC protocols in wireless sensor networks.