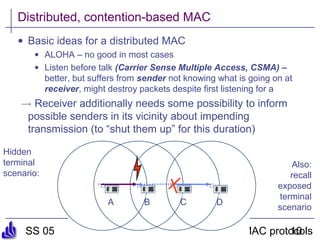
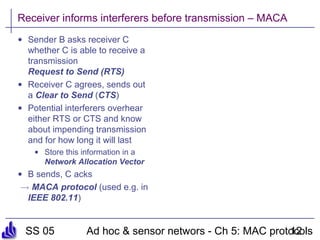
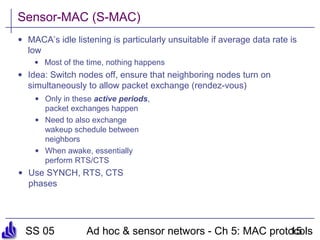
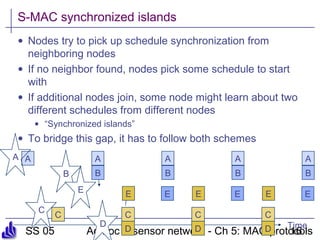
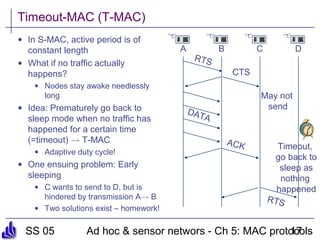
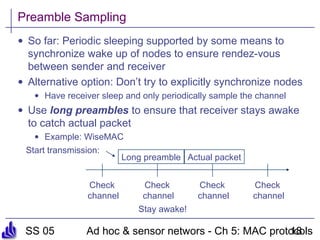
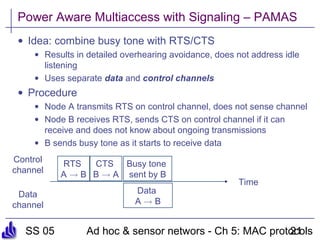
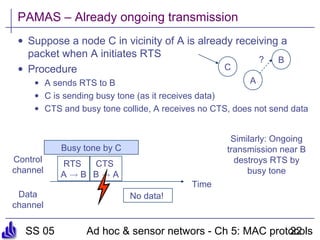
This document summarizes several medium access control (MAC) protocols for wireless networks, focusing on those suitable for mobile and energy-efficient operation. It discusses both contention-based protocols like MACA, S-MAC, and B-MAC, which use carrier sensing and random access, as well as schedule-based protocols like LEACH, SMACS, and TRAMA, which establish schedules to avoid collisions. It also covers the IEEE 802.15.4 standard for low-power wireless personal area networks.